
Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1
Comenzamos con la sección T1006 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1006 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
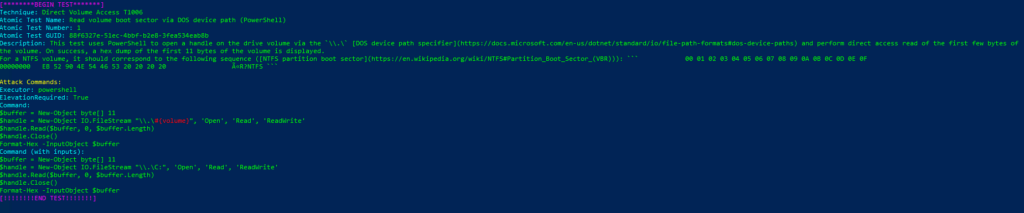
T1006-1 Read volume boot sector via DOS device path (PowerShell)Ejecutamos
Invoke-AtomicTest T1006Technique: Direct Volume Access T1006
Atomic Test Name: Read volume boot sector via DOS device path (PowerShell)
Atomic Test Number: 1
Atomic Test GUID: 88f6327e-51ec-4bbf-b2e8-3fea534eab8b
Description: This test uses PowerShell to open a handle on the drive volume via the \\.\ DOS device path specifier and perform direct access read of the first few bytes of the volume. On success, a hex dump of the first 11 bytes of the volume is displayed. For a NTFS volume, it should correspond to the following sequence (NTFS partition boot sector): 00 01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F 00000000 EB 52 90 4E 54 46 53 20 20 20 20 ëR?NTFS
Azure Sentinel
Query: Sigma Rule
Sysmon
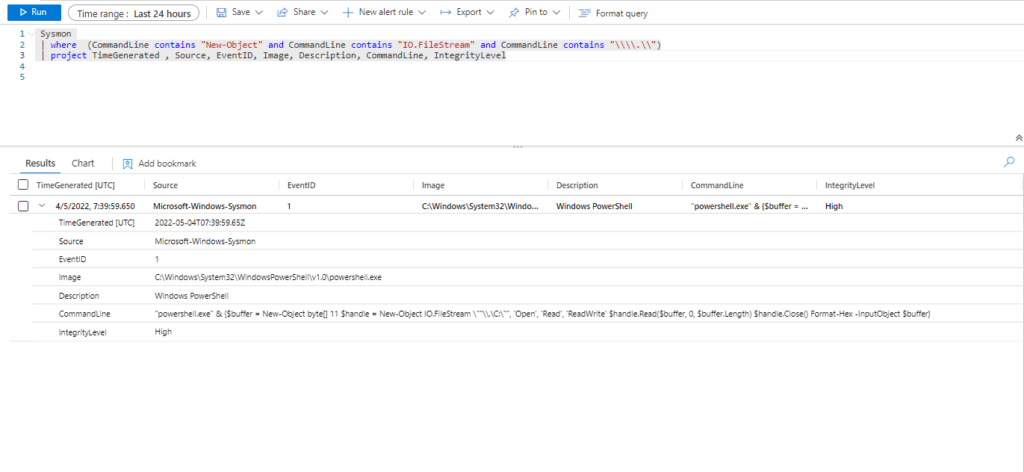
| where (CommandLine contains "New-Object" and CommandLine contains "IO.FileStream" and CommandLine contains "\\\\.\\")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer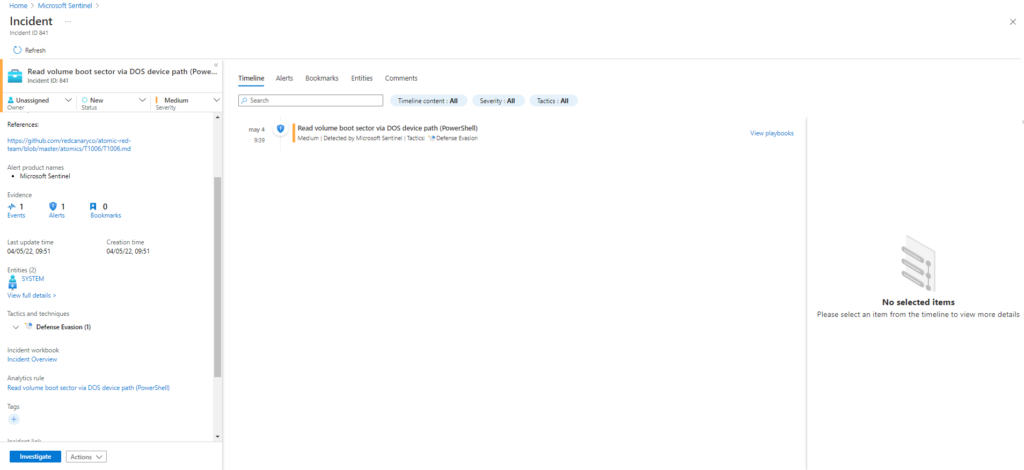
Comenzamos con la sección T1007 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1007 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
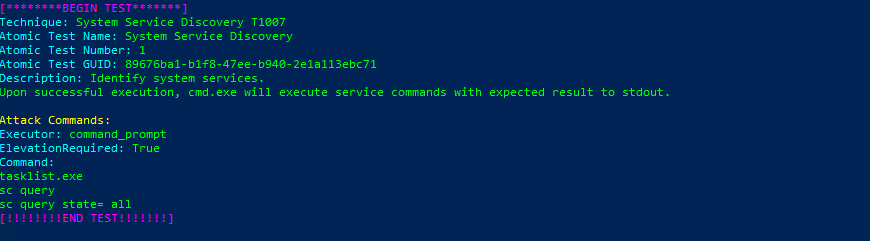
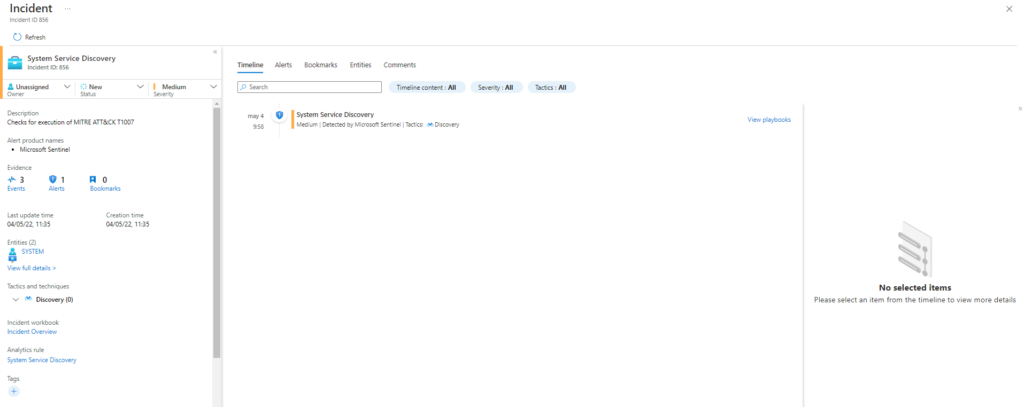
T1007-1 System Service Discovery
T1007-2 System Service Discovery - net.exeEjecutamos
Invoke-AtomicTest T1007Technique: System Service Discovery T1007
Atomic Test Name: System Service Discovery
Atomic Test Number: 1
Atomic Test GUID: 89676ba1-b1f8-47ee-b940-2e1a113ebc71
Description: Identify system services. Upon successful execution, cmd.exe will execute service commands with expected result to stdout.
Azure Sentinel
Query:
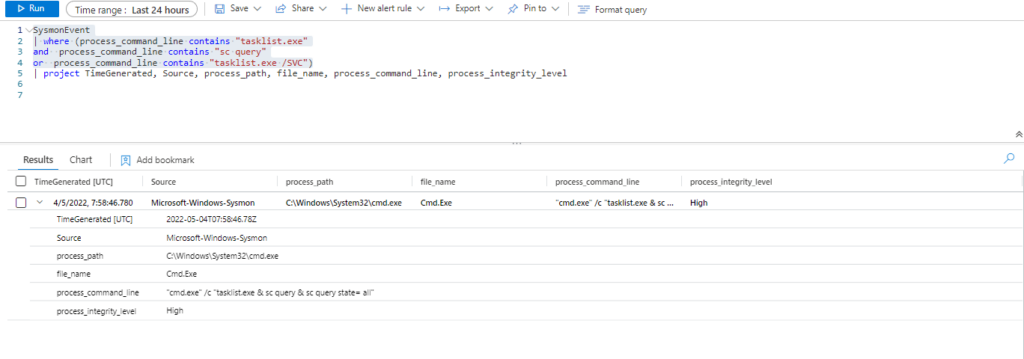
SysmonEvent
| where (process_command_line contains "tasklist.exe"
and process_command_line contains "sc query"
or process_command_line contains "tasklist.exe /SVC")
or process_command_line contains "csc.exe" and process_command_line contains "-out"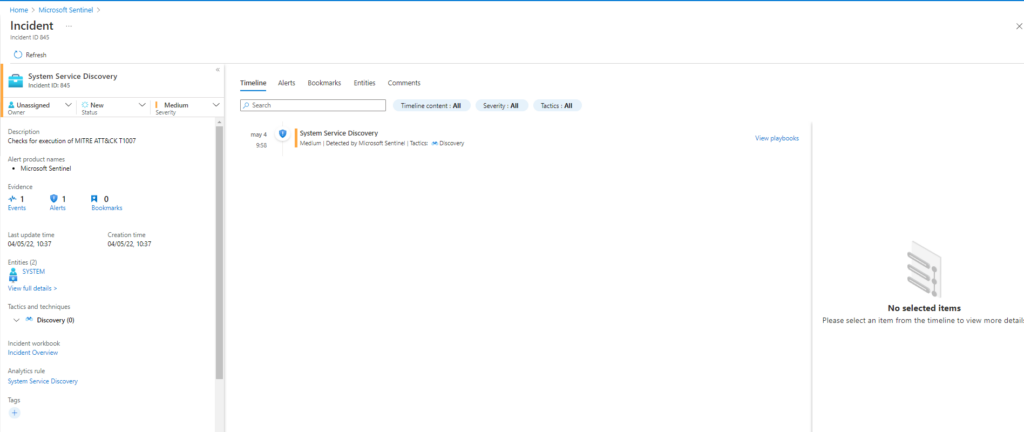
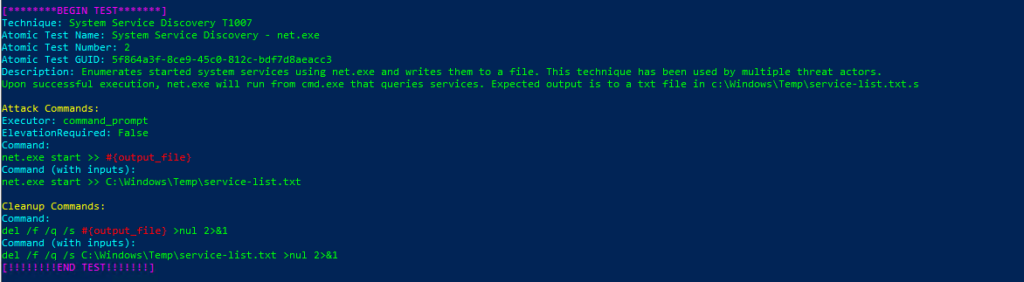
Technique: System Service Discovery T1007
Atomic Test Name: System Service Discovery – net.exe
Atomic Test Number: 2
Atomic Test GUID: 5f864a3f-8ce9-45c0-812c-bdf7d8aeacc3
Description: Enumerates started system services using net.exe and writes them to a file. This technique has been used by multiple threat actors.
Upon successful execution, net.exe will run from cmd.exe that queries services. Expected output is to a txt file in c:\Windows\Temp\service-list.txt.s
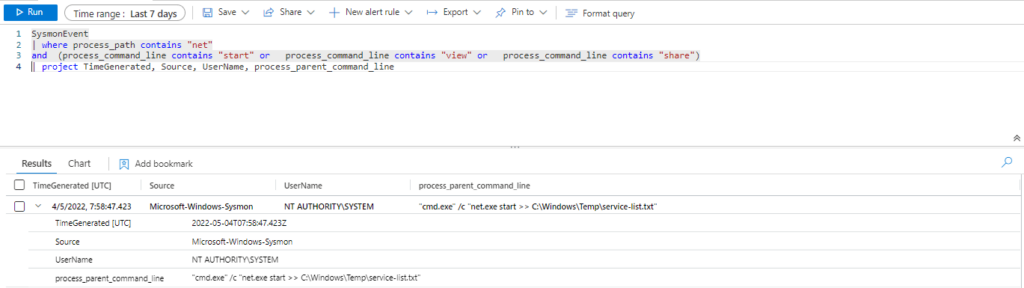
SysmonEvent
| where process_path contains "net"
and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer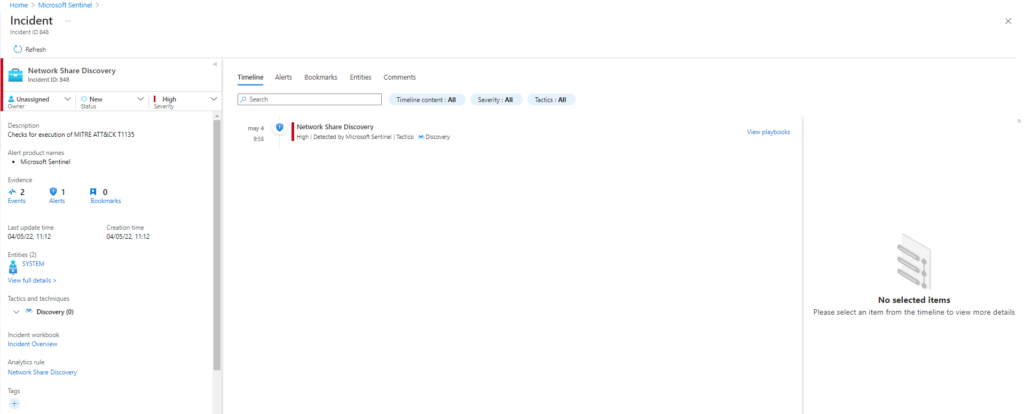
Comenzamos con la sección T1010 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1010 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1010-1 List Process Main Windows - C# .NETTechnique: Application Window Discovery T1010
Atomic Test Name: List Process Main Windows – C# .NET
Atomic Test Number: 1
Atomic Test GUID: fe94a1c3-3e22-4dc9-9fdf-3a8bdbc10dc4
Description: Compiles and executes C# code to list main window titles associated with each process.
Upon successful execution, powershell will download the .cs from the Atomic Red Team repo, and cmd.exe will compile and execute T1010.exe. Upon T1010.exe execution, expected output will be via stdout.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe"
and process_command_line contains "sc query"
or process_command_line contains "tasklist.exe /SVC")
or process_command_line contains "csc.exe" and process_command_line contains "-out"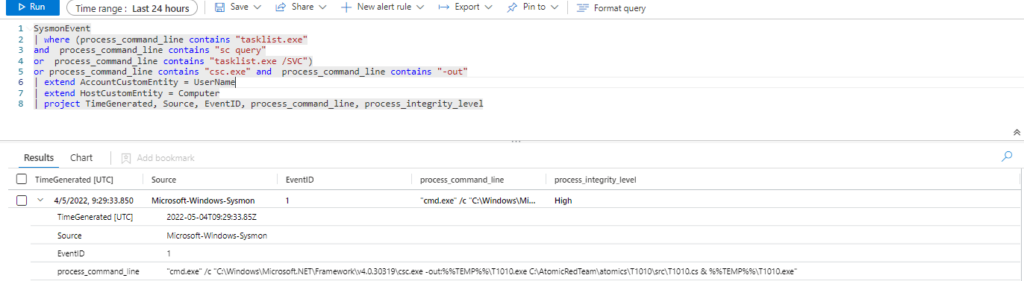
Comenzamos con la sección T1012 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1012 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
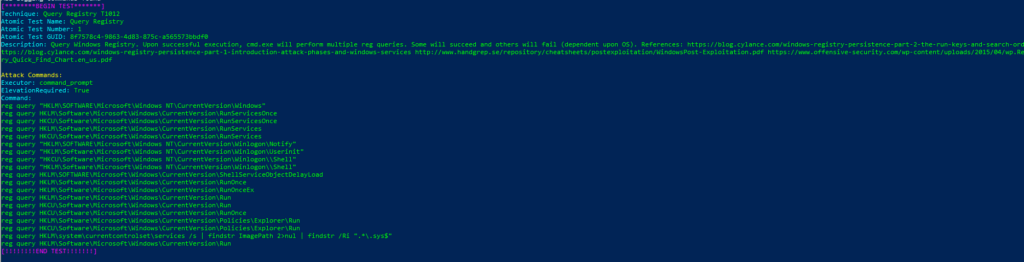
T1012-1 Query RegistryTechnique: Query Registry T1012
Atomic Test Name: Query Registry
Atomic Test Number: 1
Atomic Test GUID: 8f7578c4-9863-4d83-875c-a565573bbdf0
Description: Query Windows Registry. Upon successful execution, cmd.exe will perform multiple reg queries. Some will succeed and others will fail (dependent upon OS). References:
https://blog.cylance.com/windows-registry-persistence-part-2-the-run-keys-and-search-order https://blog.cylance.com/windows-registry-persistence-part-1-introduction-attack-phases-and-windows-services http://www.handgrep.se/repository/cheatsheets/postexploitation/WindowsPost-Exploitation.pdf https://www.offensive-security.com/wp-content/uploads/2015/04/wp.Registry_Quick_Find_Chart.en_us.pdf
Azure Sentinel
Query:
SysmonEvent
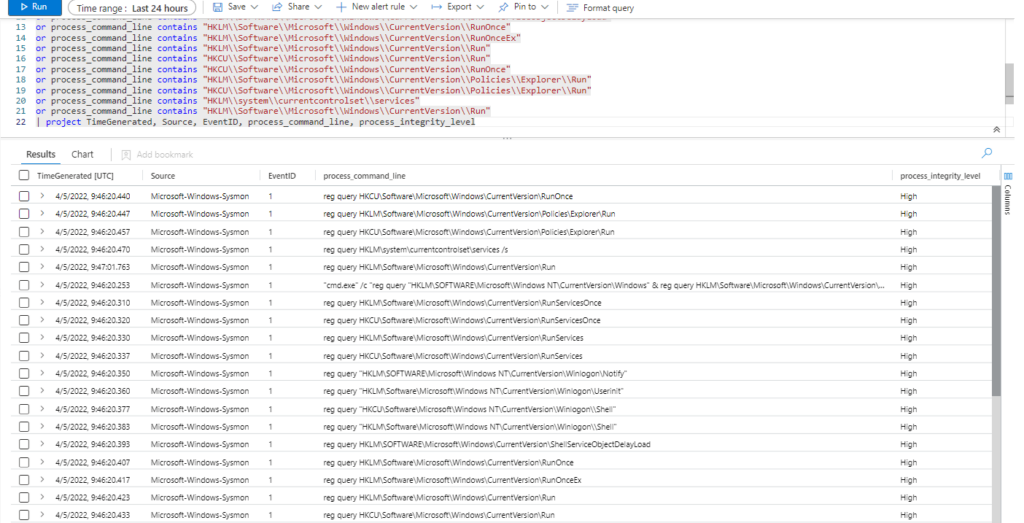
| where process_command_line contains "reg query"
and process_command_line contains "HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Windows"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\RunServicesOnce"
or process_command_line contains "HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\RunServicesOnce"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\RunServices"
or process_command_line contains "HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\RunServices"
or process_command_line contains "HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\Notify"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\Userinit"
or process_command_line contains "HKCU\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\\\Shell"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\\\Shell"
or process_command_line contains "HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellServiceObjectDelayLoad"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnceEx"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Run"
or process_command_line contains "HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run"
or process_command_line contains "HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\Run"
or process_command_line contains "HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\Run"
or process_command_line contains "HKLM\\system\\currentcontrolset\\services"
or process_command_line contains "HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Run"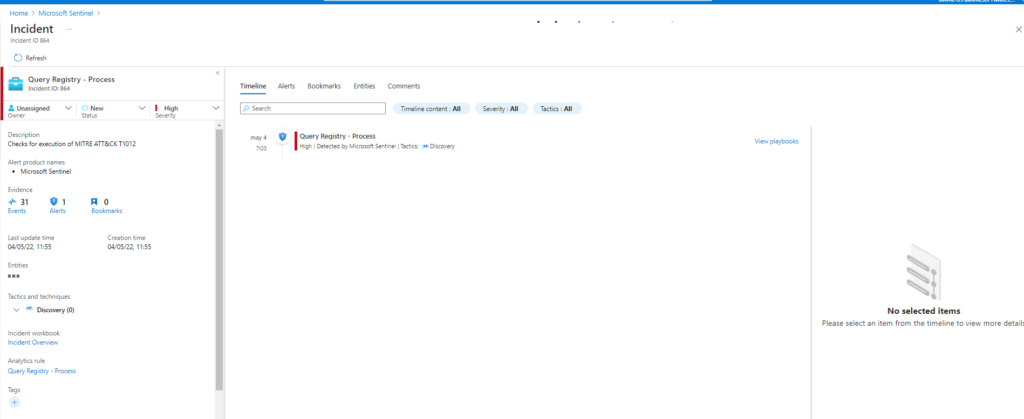
:wq!