
Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2
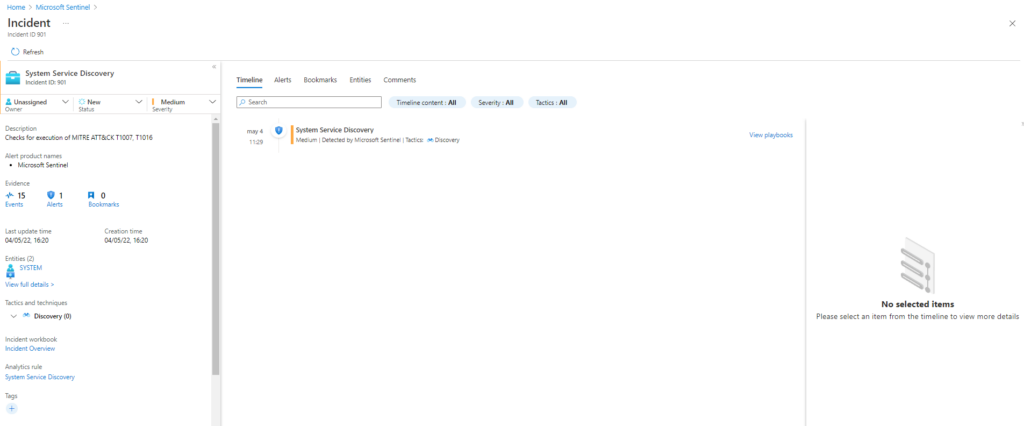
Comenzamos con la sección T1016 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1016 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1016-1 System Network Configuration Discovery on Windows
T1016-2 List Windows Firewall Rules
T1016-4 System Network Configuration Discovery (TrickBot Style)
T1016-5 List Open Egress Ports
T1016-6 Adfind - Enumerate Active Directory Subnet Objects
T1016-7 Qakbot ReconTechnique: System Network Configuration Discovery T1016
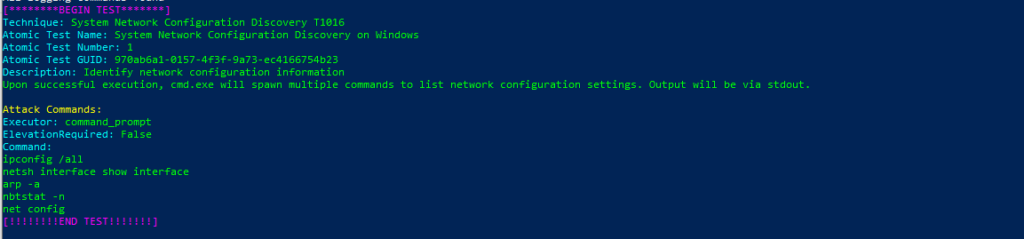
Atomic Test Name: System Network Configuration Discovery on Windows
Atomic Test Number: 1
Atomic Test GUID: 970ab6a1-0157-4f3f-9a73-ec4166754b23
Description: Identify network configuration information Upon successful execution, cmd.exe will spawn multiple commands to list network configuration settings. Output will be via stdout.
Azure Sentinel
Query:
Esta query puede dar muchos fallos positivos debido a software o script que se ejecuten como por ejemplo: WaAppAgent.exe.
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer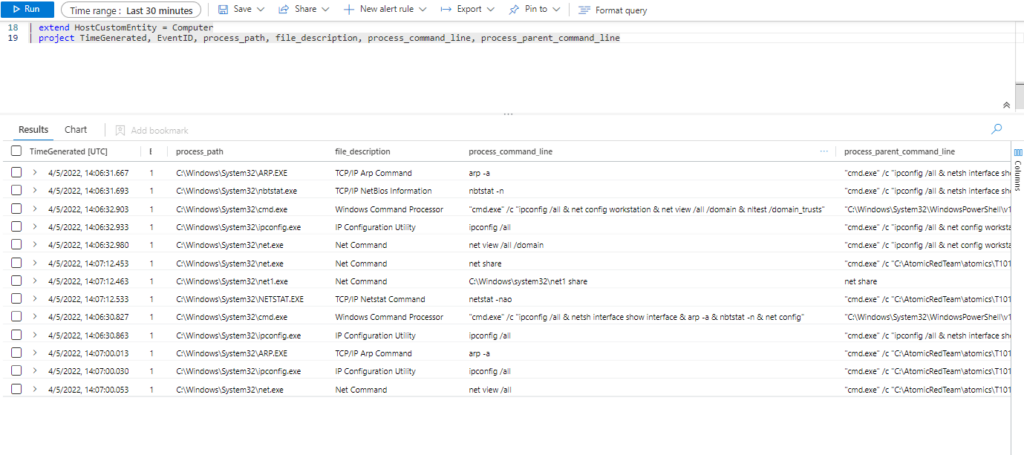
Technique: System Network Configuration Discovery T1016
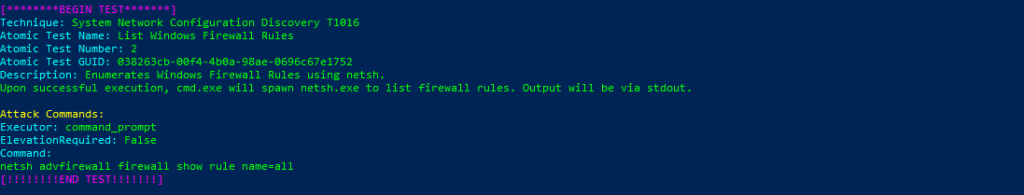
Atomic Test Name: List Windows Firewall Rules
Atomic Test Number: 2
Atomic Test GUID: 038263cb-00f4-4b0a-98ae-0696c67e1752
Description: Enumerates Windows Firewall Rules using netsh. Upon successful execution, cmd.exe will spawn netsh.exe to list firewall rules. Output will be via stdout.
Azure Sentinel
Query:
Esta query puede dar muchos fallos positivos debido a software o script que se ejecuten como por ejemplo: WaAppAgent.exe.
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

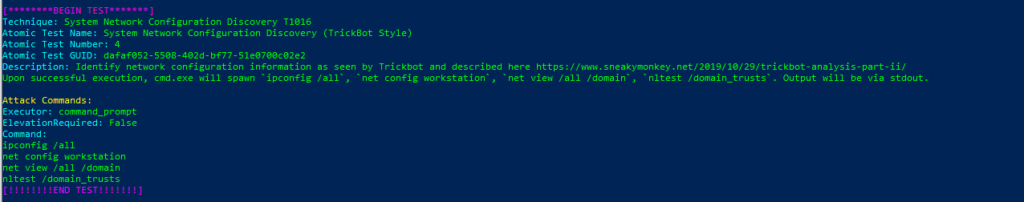
Technique: System Network Configuration Discovery T1016
Atomic Test Name: System Network Configuration Discovery (TrickBot Style)
Atomic Test Number: 4
Atomic Test GUID: dafaf052-5508-402d-bf77-51e0700c02e2
Description: Identify network configuration information as seen by Trickbot and described here https://www.sneakymonkey.net/2019/10/29/trickbot-analysis-part-ii/
Upon successful execution, cmd.exe will spawn ipconfig /all, net config workstation, net view /all /domain, nltest /domain_trusts. Output will be via stdout.
Azure Sentinel
Query:
Esta query puede dar muchos fallos positivos debido a software o script que se ejecuten como por ejemplo: WaAppAgent.exe.
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

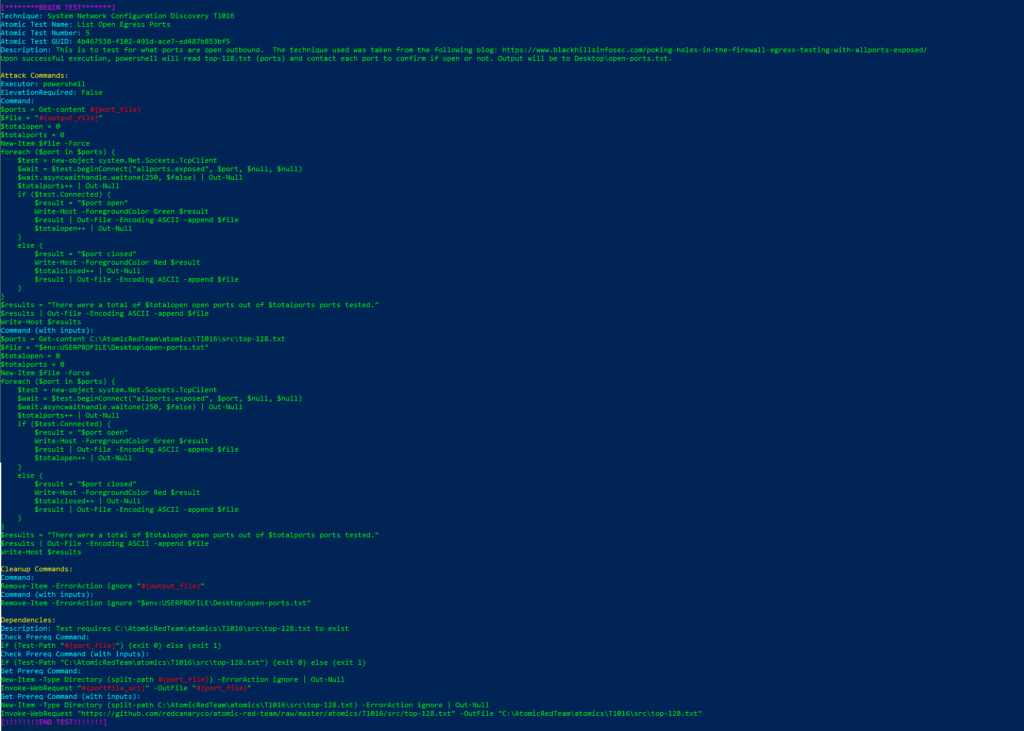
Technique: System Network Configuration Discovery T1016
Atomic Test Name: List Open Egress Ports
Atomic Test Number: 5
Atomic Test GUID: 4b467538-f102-491d-ace7-ed487b853bf5
Description: This is to test for what ports are open outbound. The technique used was taken from the following blog: https://www.blackhillsinfosec.com/poking-holes-in-the-firewall-egress-testing-with-allports-exposed/ Upon successful execution, powershell will read top-128.txt (ports) and contact each port to confirm if open or not. Output will be to Desktop\open-ports.txt.
Azure Sentinel
Query:
Esta query puede dar muchos fallos positivos debido a software o script que se ejecuten como por ejemplo: WaAppAgent.exe.
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

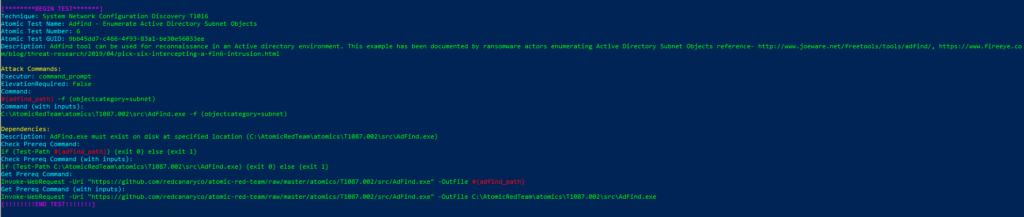
Technique: System Network Configuration Discovery T1016
Atomic Test Name: Adfind – Enumerate Active Directory Subnet Objects
Atomic Test Number: 6
Atomic Test GUID: 9bb45dd7-c466-4f93-83a1-be30e56033ee
Description: Adfind tool can be used for reconnaissance in an Active directory environment. This example has been documented by ransomware actors enumerating Active Directory Subnet Objects reference- http://www.joeware.net/freetools/tools/adfind/, https://www.fireeye.com/blog/threat-research/2019/04/pick-six-intercepting-a-fin6-intrusion.html
Azure Sentinel
Query:
Esta query puede dar muchos fallos positivos debido a software o script que se ejecuten como por ejemplo: WaAppAgent.exe.
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: System Network Configuration Discovery T1016
Atomic Test Name: Qakbot Recon
Atomic Test Number: 7
Atomic Test GUID: 121de5c6-5818-4868-b8a7-8fd07c455c1b
Description: A list of commands known to be performed by Qakbot for recon purposes

Azure Sentinel
Query:
Esta query puede dar muchos fallos positivos debido a software o script que se ejecuten como por ejemplo: WaAppAgent.exe.
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

:wq!