
Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2, Ver parte 3, Ver parte 4
Comenzamos con la sección T1021.001 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1021.001 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1021.001-1 RDP to DomainController
T1021.001-2 RDP to Server
T1021.001-3 Changing RDP Port to Non Standard Port via Powershell
T1021.001-4 Changing RDP Port to Non Standard Port via Command_PromptEjecutamos
Invoke-AtomicTest T1021.001Technique: Remote Services: Remote Desktop Protocol T1021.001
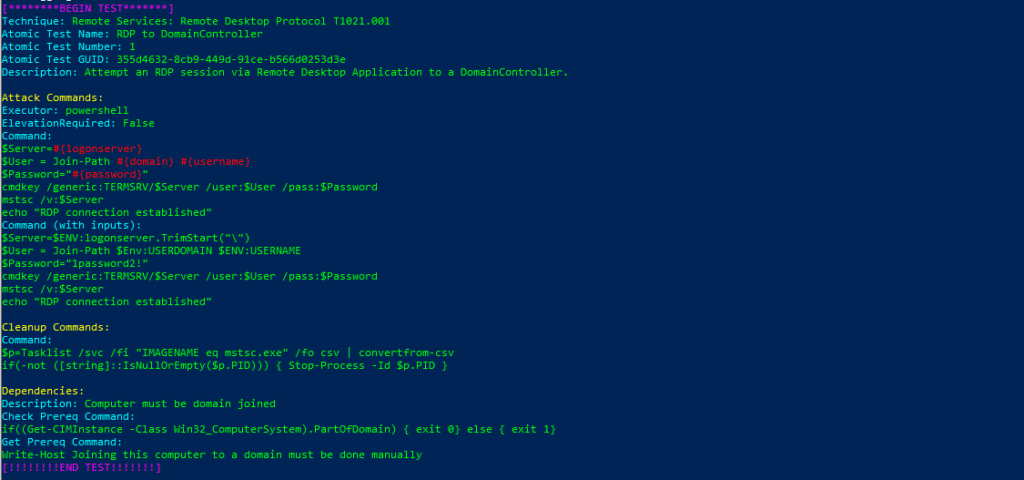
Atomic Test Name: RDP to DomainController
Atomic Test Number: 1
Atomic Test GUID: 355d4632-8cb9-449d-91ce-b566d0253d3e
Description: Attempt an RDP session via Remote Desktop Application to a DomainController.
Azurre Sentinel
Query:
SysmonEvent
| where process_command_line contains "cmdkey" and process_command_line contains "mstsc"
or (process_command_line contains "HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal Server\\WinStations\\RDP-Tcp"
or (process_command_line contains "New-NetFirewallRule" and process_command_line contains "-Action Allow"
or process_command_line contains "netsh advfirewall" and process_command_line contains "action=allow" ))
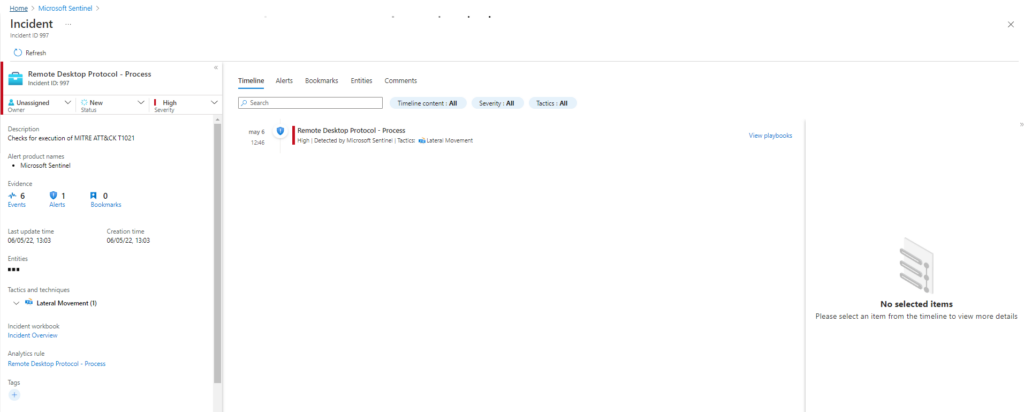
| extend AccountCustomEntity = UserName | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer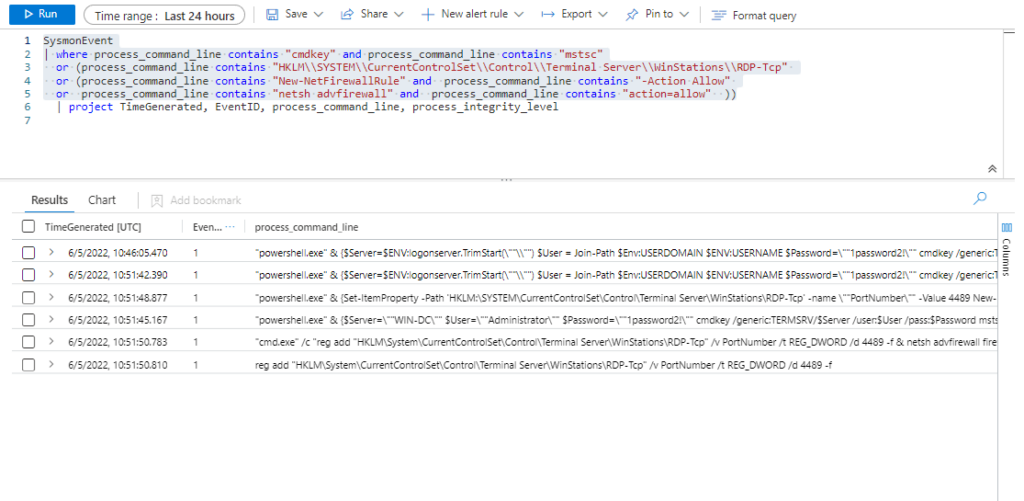
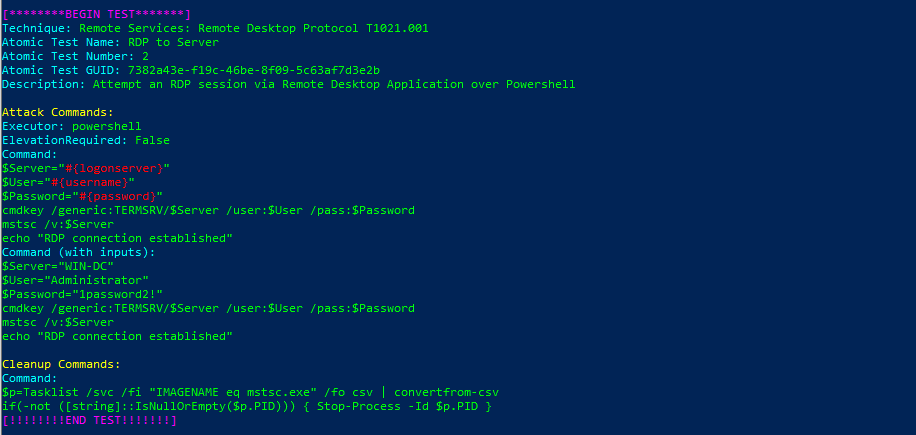
Technique: Remote Services: Remote Desktop Protocol T1021.001
Atomic Test Name: RDP to Server
Atomic Test Number: 2
Atomic Test GUID: 7382a43e-f19c-46be-8f09-5c63af7d3e2b
Description: Attempt an RDP session via Remote Desktop Application over Powershell
Azurre Sentinel
Query:
SysmonEvent
| where process_command_line contains "cmdkey" and process_command_line contains "mstsc"
or (process_command_line contains "HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal Server\\WinStations\\RDP-Tcp"
or (process_command_line contains "New-NetFirewallRule" and process_command_line contains "-Action Allow"
or process_command_line contains "netsh advfirewall" and process_command_line contains "action=allow" ))
| extend AccountCustomEntity = UserName | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer

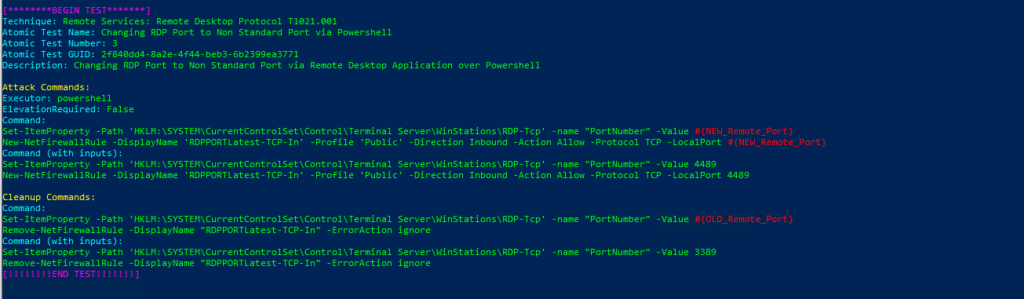
Technique: Remote Services: Remote Desktop Protocol T1021.001
Atomic Test Name: Changing RDP Port to Non Standard Port via Powershell
Atomic Test Number: 3
Atomic Test GUID: 2f840dd4-8a2e-4f44-beb3-6b2399ea3771
Description: Changing RDP Port to Non Standard Port via Remote Desktop Application over Powershell
Azurre Sentinel
Query:
SysmonEvent
| where process_command_line contains "cmdkey" and process_command_line contains "mstsc"
or (process_command_line contains "HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal Server\\WinStations\\RDP-Tcp"
or (process_command_line contains "New-NetFirewallRule" and process_command_line contains "-Action Allow"
or process_command_line contains "netsh advfirewall" and process_command_line contains "action=allow" ))
| extend AccountCustomEntity = UserName | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer

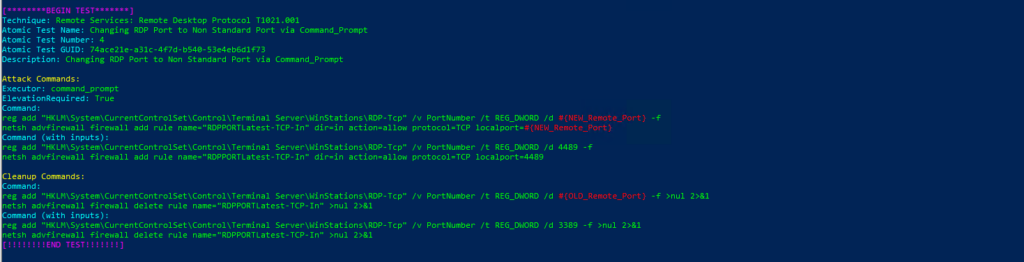
Technique: Remote Services: Remote Desktop Protocol T1021.001
Atomic Test Name: Changing RDP Port to Non Standard Port via Command_Prompt
Atomic Test Number: 4
Atomic Test GUID: 74ace21e-a31c-4f7d-b540-53e4eb6d1f73
Description: Changing RDP Port to Non Standard Port via Command_Prompt
Azurre Sentinel
Query:
SysmonEvent
| where process_command_line contains "cmdkey" and process_command_line contains "mstsc"
or (process_command_line contains "HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal Server\\WinStations\\RDP-Tcp"
or (process_command_line contains "New-NetFirewallRule" and process_command_line contains "-Action Allow"
or process_command_line contains "netsh advfirewall" and process_command_line contains "action=allow" ))
| extend AccountCustomEntity = UserName | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer

Comenzamos con la sección T1021.002 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1021.002 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1021.002-1 Map admin share
T1021.002-2 Map Admin Share PowerShell
T1021.002-3 Copy and Execute File with PsExec
T1021.002-4 Execute command writing output to local Admin ShareEjecutamos
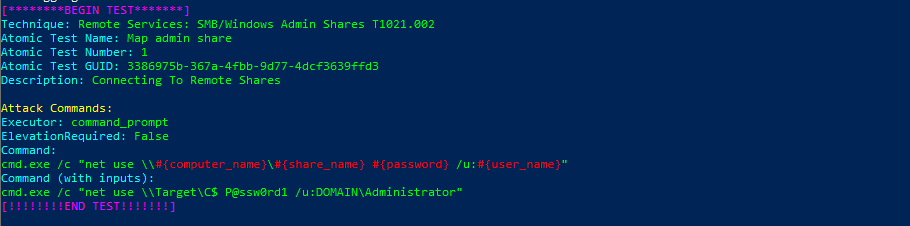
Invoke-AtomicTest T1021.002Technique: Remote Services: SMB/Windows Admin Shares T1021.002
Atomic Test Name: Map admin share
Atomic Test Number: 1
Atomic Test GUID: 3386975b-367a-4fbb-9d77-4dcf3639ffd3
Description: Connecting To Remote Shares
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or (process_command_line contains "csc.exe" and (process_command_line contains "-out"))
or (process_command_line contains "netstat" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "WindowsAzureGuestAgent.exe"))
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net view"
or (process_command_line contains "net share" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "net start" and not(process_command_line contains "RDAgentBootLoader"))
or process_command_line contains "net sessions"
or (process_command_line contains "net config" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "net file" and not(process_path contains "\\Windows\\Microsoft.NET\\Framework64" or file_name contains "csc.exe"))
or (process_command_line contains "ipconfig" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs" or file_directory contains "CabFolder" or process_parent_command_line contains "WindowsAzureGuestAgent.exe"))
or process_command_line contains "netsh interface show interface"
or (process_command_line contains "arp /a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "arp -a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "arp.exe /a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "arp.exe -a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "nbtstat" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs" or file_directory contains "CabFolder"))
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w") and not(process_parent_command_line contains "gatherNetworkInfo.vbs"))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
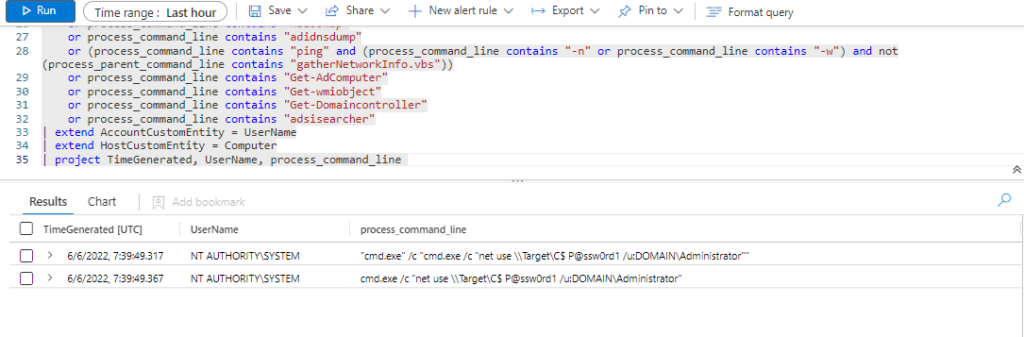
Technique: Remote Services: SMB/Windows Admin Shares T1021.002
Atomic Test Name: Map Admin Share PowerShell
Atomic Test Number: 2
Atomic Test GUID: 514e9cd7-9207-4882-98b1-c8f791bae3c5
Description: Map Admin share utilizing PowerShell
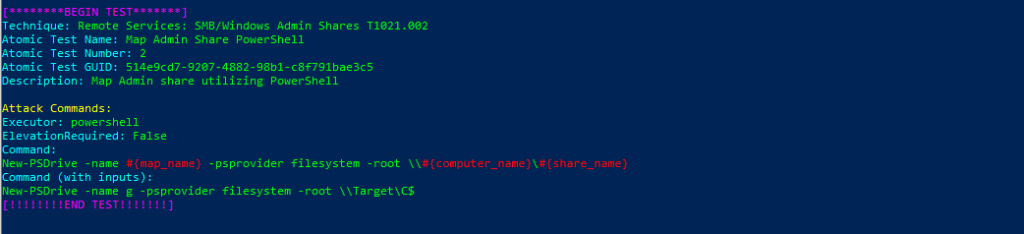
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or (process_command_line contains "csc.exe" and (process_command_line contains "-out"))
or (process_command_line contains "netstat" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "WindowsAzureGuestAgent.exe"))
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net view"
or (process_command_line contains "net share" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "net start" and not(process_command_line contains "RDAgentBootLoader"))
or process_command_line contains "net sessions"
or (process_command_line contains "net config" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "net file" and not(process_path contains "\\Windows\\Microsoft.NET\\Framework64" or file_name contains "csc.exe"))
or (process_command_line contains "ipconfig" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs" or file_directory contains "CabFolder" or process_parent_command_line contains "WindowsAzureGuestAgent.exe"))
or process_command_line contains "netsh interface show interface"
or (process_command_line contains "arp /a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "arp -a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "arp.exe /a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "arp.exe -a" and not(process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs"))
or (process_command_line contains "nbtstat" and not(process_parent_path contains "WaAppAgent.exe" or process_parent_command_line contains "\\Windows\\system32\\gatherNetworkInfo.vbs" or file_directory contains "CabFolder"))
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w") and not(process_parent_command_line contains "gatherNetworkInfo.vbs"))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote Services: SMB/Windows Admin Shares T1021.002
Atomic Test Name: Copy and Execute File with PsExec
Atomic Test Number: 3
Atomic Test GUID: 0eb03d41-79e4-4393-8e57-6344856be1cf
Description: Copies a file to a remote host and executes it using PsExec. Requires the download of PsExec from https://docs.microsoft.com/en-us/sysinternals/downloads/psexec.
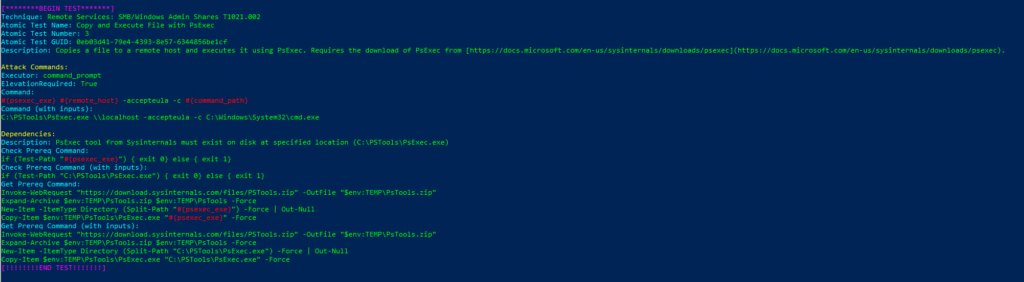
Azure Sentinel
Query: Sigma Rule
SysmonEvent
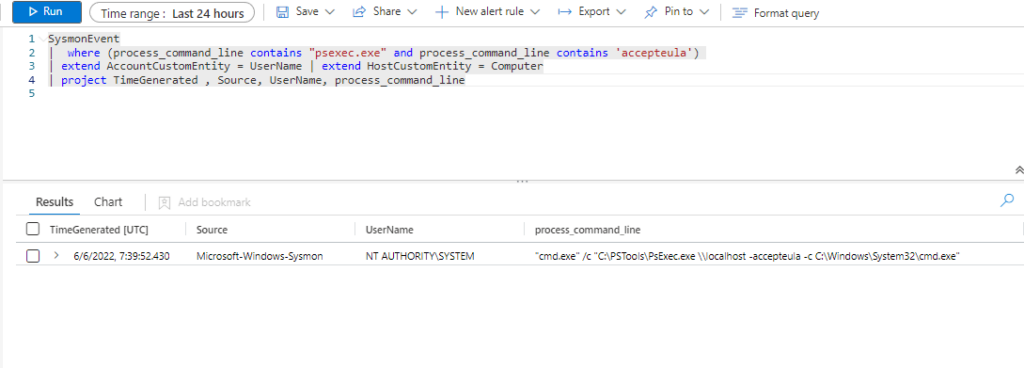
| where (process_command_line contains "psexec.exe" and process_command_line contains 'accepteula')
or (process_command_line contains "\\127.0.0" and process_command_line contains "\\ADMIN$\\")
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer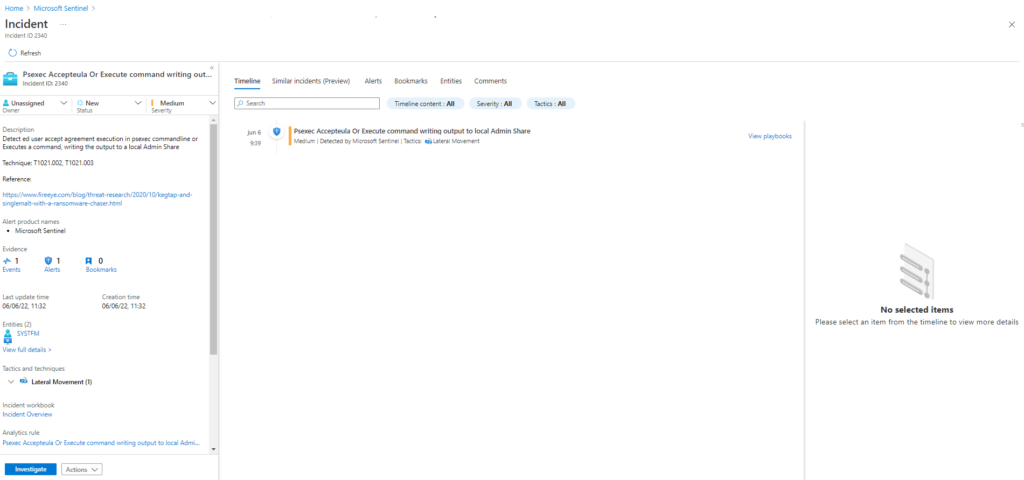
Technique: Remote Services: SMB/Windows Admin Shares T1021.002
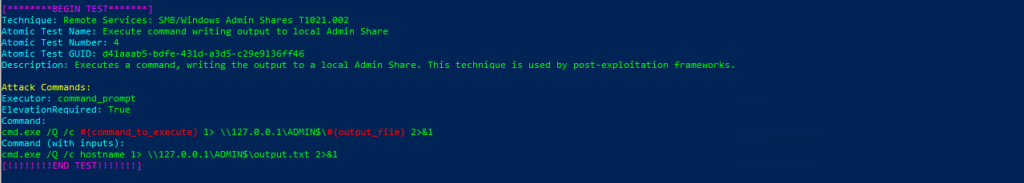
Atomic Test Name: Execute command writing output to local Admin Share
Atomic Test Number: 4
Atomic Test GUID: d41aaab5-bdfe-431d-a3d5-c29e9136ff46
Description: Executes a command, writing the output to a local Admin Share. This technique is used by post-exploitation frameworks.
Azure Sentinel
Query: Sigma Rule
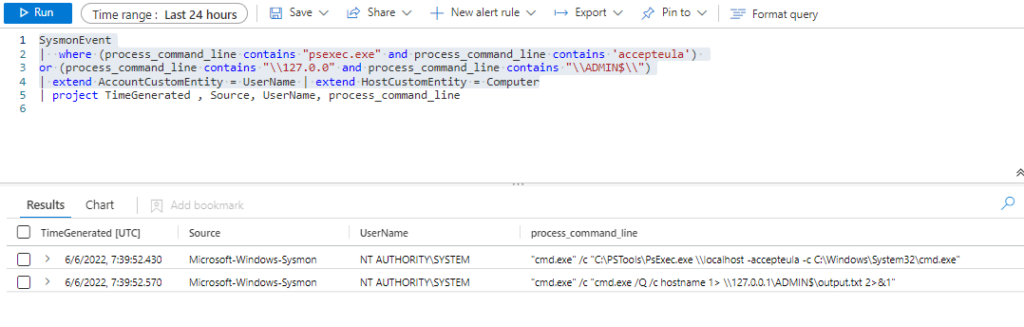
SysmonEvent
| where (process_command_line contains "psexec.exe" and process_command_line contains 'accepteula')
or (process_command_line contains "\\127.0.0" and process_command_line contains "\\ADMIN$\\")
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer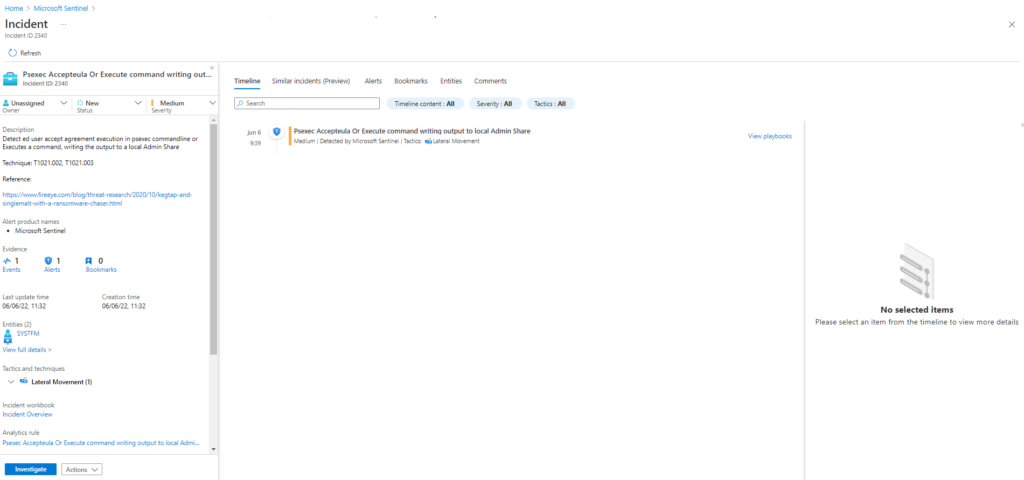
Comenzamos con la sección T1021.003 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1021.003 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1021.003-1 PowerShell Lateral Movement using MMC20Ejecutamos
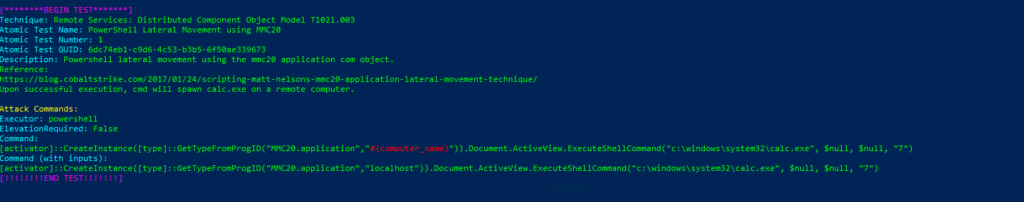
Invoke-AtomicTest T1021.003 Technique: Remote Services: Distributed Component Object Model T1021.003
Atomic Test Name: PowerShell Lateral Movement using MMC20
Atomic Test Number: 1
Atomic Test GUID: 6dc74eb1-c9d6-4c53-b3b5-6f50ae339673
Description: Powershell lateral movement using the mmc20 application com object.
Azure Sentinel
Query:
| where ParentImage contains "svchost.exe" and Image contains "mmc.exe" and CommandLine contains "-Embedding"
or (CommandLine contains "MMC20.Application" and CommandLine contains "ExecuteShellCommand")
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer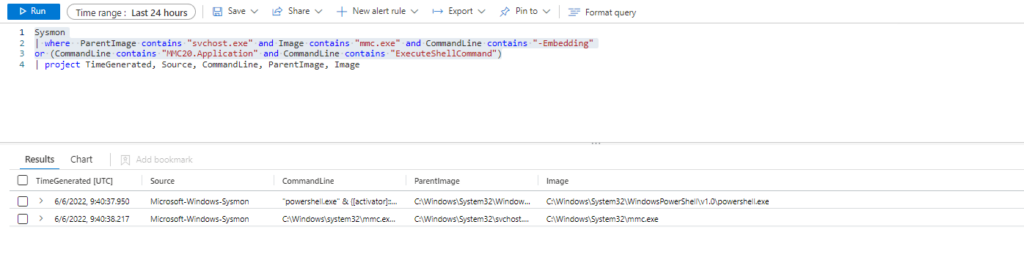
Comenzamos con la sección T1021.001 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1021.006 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1021.006-1 Enable Windows Remote Management
T1021.006-2 Invoke-Command
T1021.006-3 WinRM Access with Evil-WinRMEjecutamos
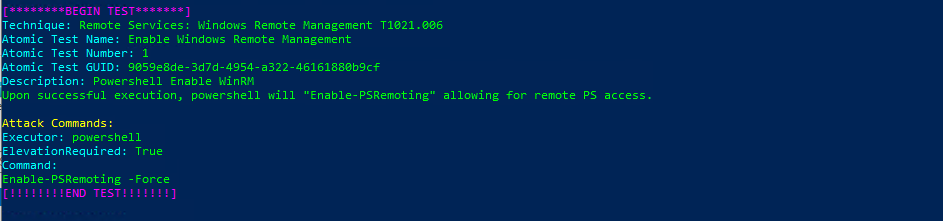
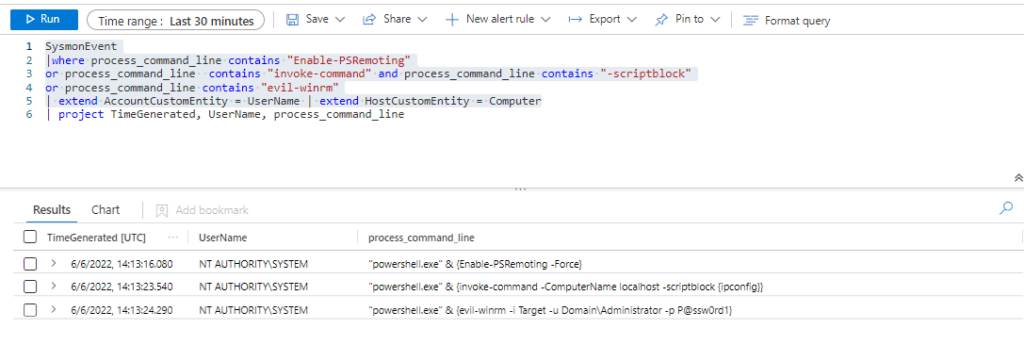
Invoke-AtomicTest T1021.006Technique: Remote Services: Windows Remote Management T1021.006
Atomic Test Name: Enable Windows Remote Management
Atomic Test Number: 1
Atomic Test GUID: 9059e8de-3d7d-4954-a322-46161880b9cf
Description: Powershell Enable WinRM
Upon successful execution, powershell will «Enable-PSRemoting» allowing for remote PS access.
Azure Sentinel
Query:
SysmonEvent
|where process_command_line contains "Enable-PSRemoting"
or process_command_line contains "invoke-command" and process_command_line contains "-scriptblock"
or process_command_line contains "evil-winrm"
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer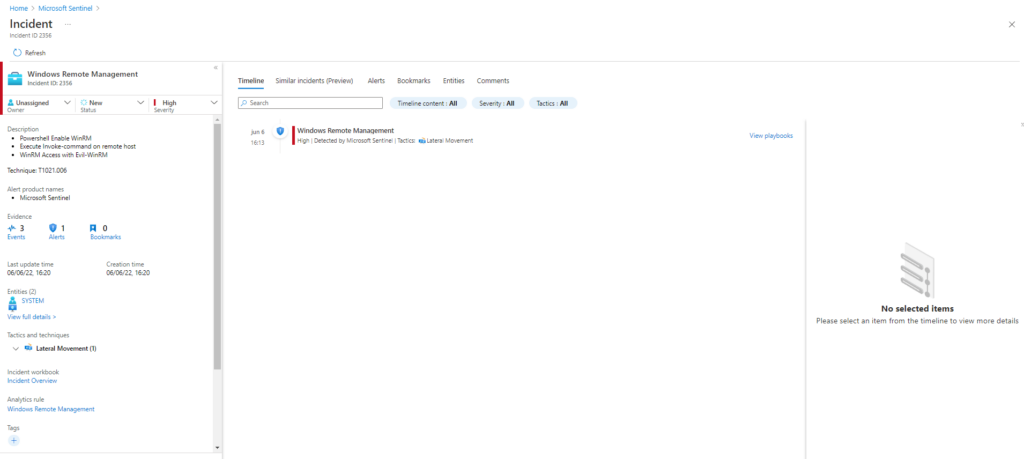
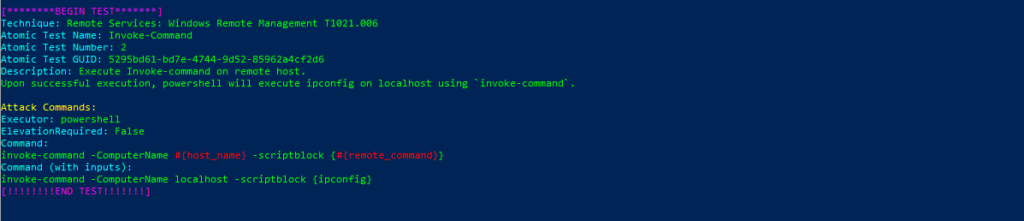
Technique: Remote Services: Windows Remote Management T1021.006
Atomic Test Name: Invoke-Command
Atomic Test Number: 2
Atomic Test GUID: 5295bd61-bd7e-4744-9d52-85962a4cf2d6
Description: Execute Invoke-command on remote host. Upon successful execution, powershell will execute ipconfig on localhost using invoke-command.
Azure Sentinel
Query:
SysmonEvent
|where process_command_line contains "Enable-PSRemoting"
or process_command_line contains "invoke-command" and process_command_line contains "-scriptblock"
or process_command_line contains "evil-winrm"
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer

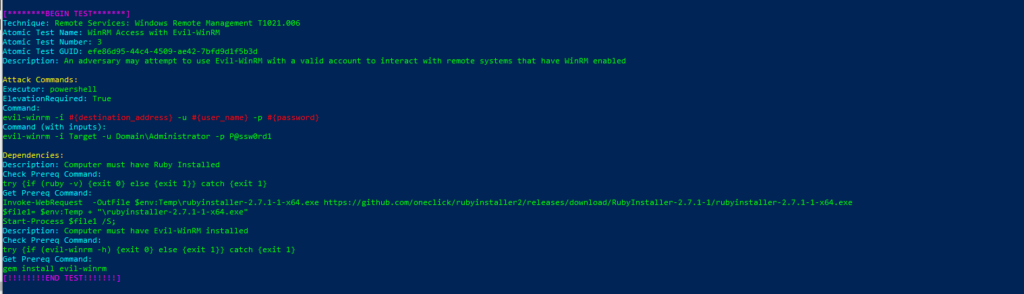
Technique: Remote Services: Windows Remote Management T1021.006
Atomic Test Name: WinRM Access with Evil-WinRM
Atomic Test Number: 3
Atomic Test GUID: efe86d95-44c4-4509-ae42-7bfd9d1f5b3d
Description: An adversary may attempt to use Evil-WinRM with a valid account to interact with remote systems that have WinRM enabled
:wq!
Una respuesta a “Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte 5 (ATT&CK T1021)”