Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2, Ver parte 3, Ver parte 4, Ver parte 5, Ver parte 6
Comenzamos con la sección T1033 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1033 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
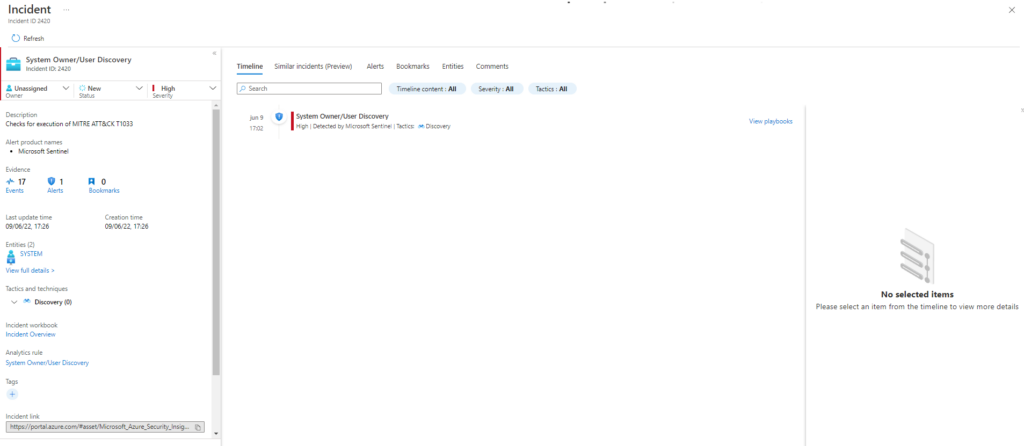
T1033-1 System Owner/User Discovery
T1033-3 Find computers where user has session - Stealth mode (PowerView)
T1033-4 User Discovery With Env Vars PowerShell Script
T1033-5 GetCurrent User with PowerShell ScriptEjecutamos
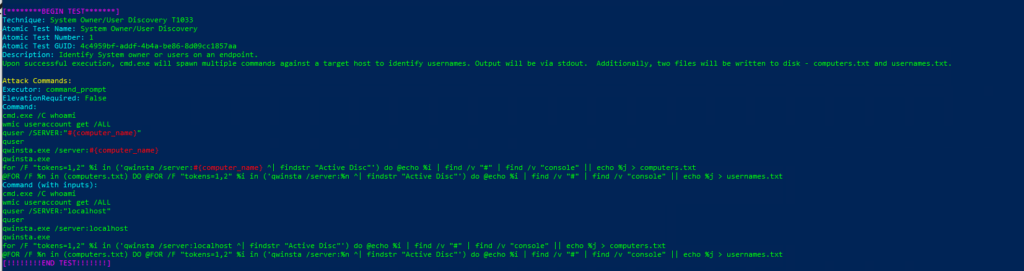
Invoke-AtomicTest T1033Technique: System Owner/User Discovery T1033
Atomic Test Name: System Owner/User Discovery
Atomic Test Number: 1
Atomic Test GUID: 4c4959bf-addf-4b4a-be86-8d09cc1857aa
Description: Identify System owner or users on an endpoint. Upon successful execution, cmd.exe will spawn multiple commands against a target host to identify usernames. Output will be via stdout. Additionally, two files will be written to disk – computers.txt and usernames.txt.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "whoami"
or process_command_line contains "useraccount get /ALL"
or process_command_line contains "qwinsta"
or process_command_line contains "PowerView"
or process_command_line contains "GetCurrent"
or process_command_line contains "[System.Environment]::UserName"
or process_command_line contains "quser"
or process_command_line contains "systeminfo")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer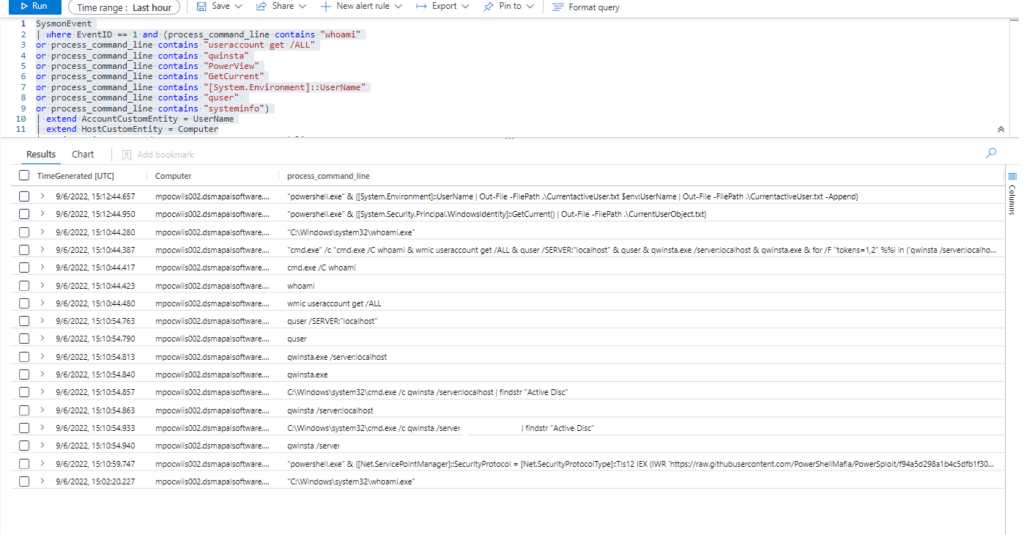
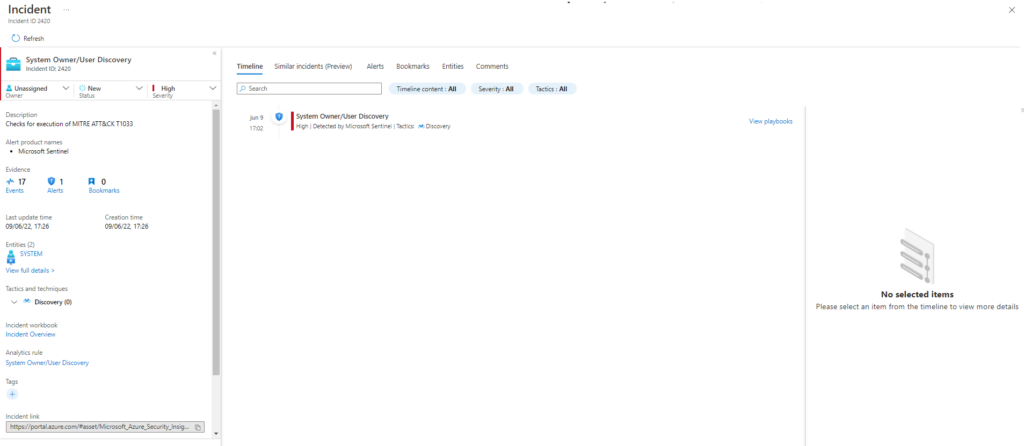
Technique: System Owner/User Discovery T1033
Atomic Test Name: Find computers where user has session – Stealth mode (PowerView)
Atomic Test Number: 3
Atomic Test GUID: 29857f27-a36f-4f7e-8084-4557cd6207ca
Description: Find existing user session on other computers. Upon execution, information about any sessions discovered will be displayed.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "whoami"
or process_command_line contains "useraccount get /ALL"
or process_command_line contains "qwinsta"
or process_command_line contains "PowerView"
or process_command_line contains "GetCurrent"
or process_command_line contains "[System.Environment]::UserName"
or process_command_line contains "quser"
or process_command_line contains "systeminfo")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
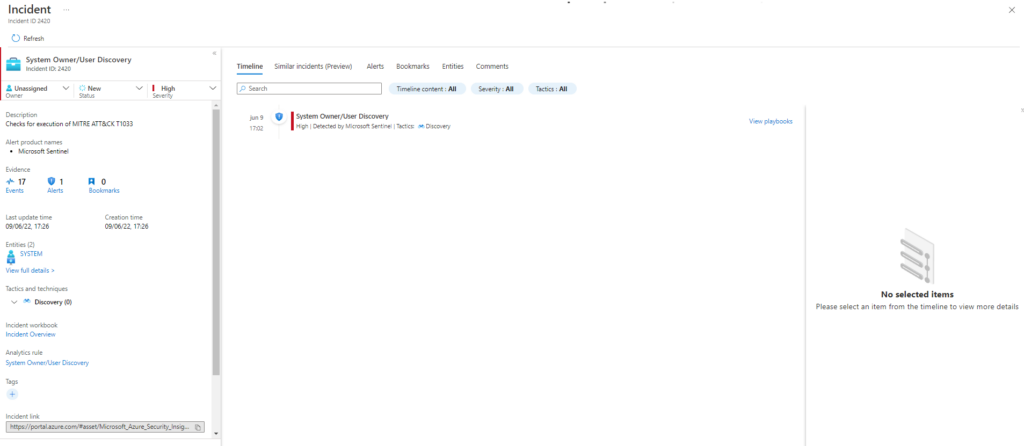
Technique: System Owner/User Discovery T1033
Atomic Test Name: User Discovery With Env Vars PowerShell Script
Atomic Test Number: 4
Atomic Test GUID: dcb6cdee-1fb0-4087-8bf8-88cfd136ba51
Description: Use the PowerShell environment variables to identify the current logged user.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "whoami"
or process_command_line contains "useraccount get /ALL"
or process_command_line contains "qwinsta"
or process_command_line contains "PowerView"
or process_command_line contains "GetCurrent"
or process_command_line contains "[System.Environment]::UserName"
or process_command_line contains "quser"
or process_command_line contains "systeminfo")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
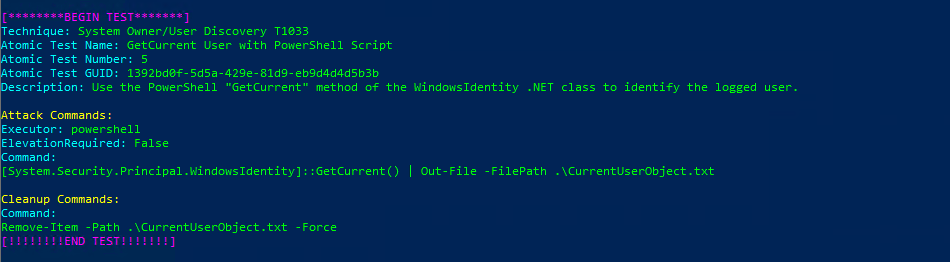
Technique: System Owner/User Discovery T1033
Atomic Test Name: GetCurrent User with PowerShell Script
Atomic Test Number: 5
Atomic Test GUID: 1392bd0f-5d5a-429e-81d9-eb9d4d4d5b3b
Description: Use the PowerShell «GetCurrent» method of the WindowsIdentity .NET class to identify the logged user.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "whoami"
or process_command_line contains "useraccount get /ALL"
or process_command_line contains "qwinsta"
or process_command_line contains "PowerView"
or process_command_line contains "GetCurrent"
or process_command_line contains "[System.Environment]::UserName"
or process_command_line contains "quser"
or process_command_line contains "systeminfo")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
Comenzamos con la sección T1036 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1036 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Executing test: T1036-1 System File Copied to Unusual Location
PS C:\AtomicRedTeam> Invoke-AtomicTest T1036 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1036-1 System File Copied to Unusual Location
T1036-2 Malware Masquerading and Execution from Zip FileEjecutamos
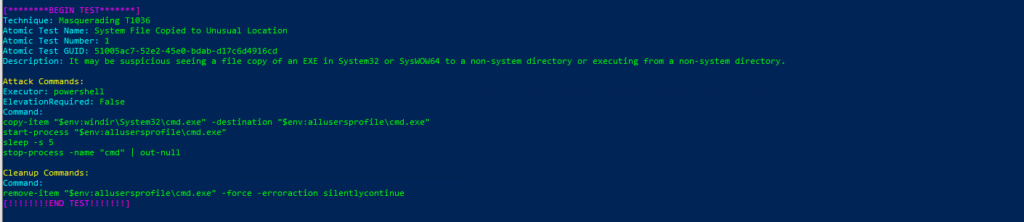
Invoke-AtomicTest T1036Technique: Masquerading T1036
Atomic Test Name: System File Copied to Unusual Location
Atomic Test Number: 1
Atomic Test GUID: 51005ac7-52e2-45e0-bdab-d17c6d4916cd
Description: It may be suspicious seeing a file copy of an EXE in System32 or SysWOW64 to a non-system directory or executing from a non-system directory.
Azure Sentinel
Query
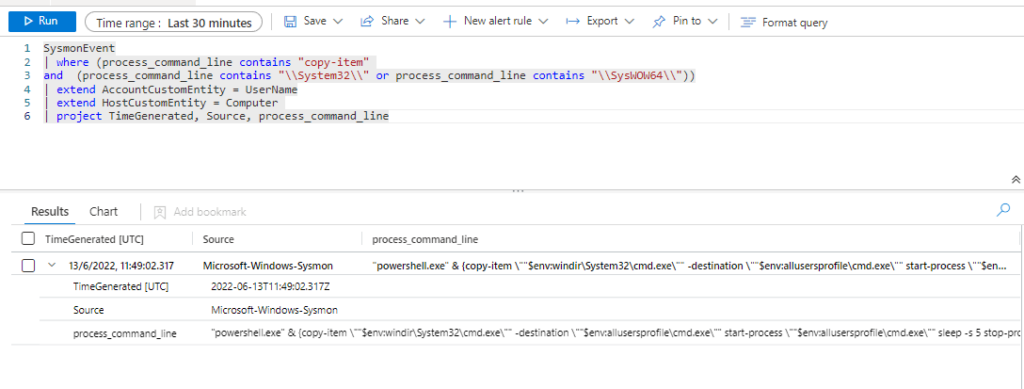
SysmonEvent
| where (process_command_line contains "copy-item"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))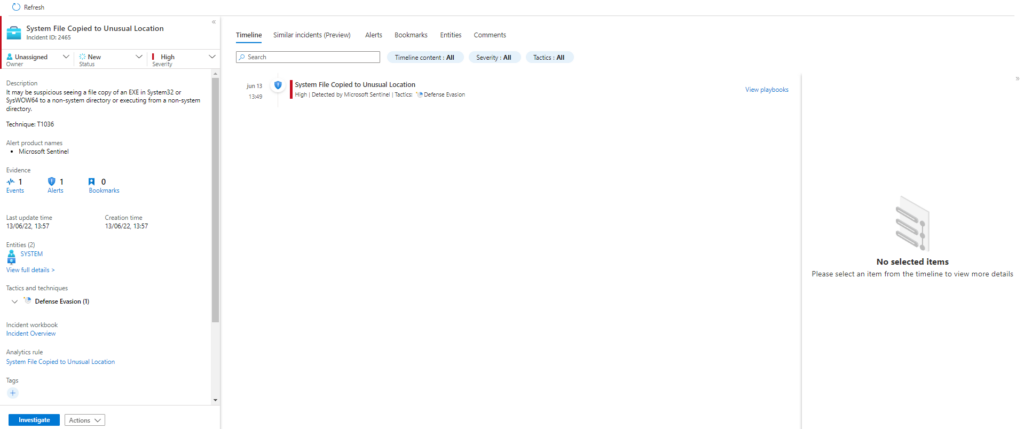
Technique: Masquerading T1036
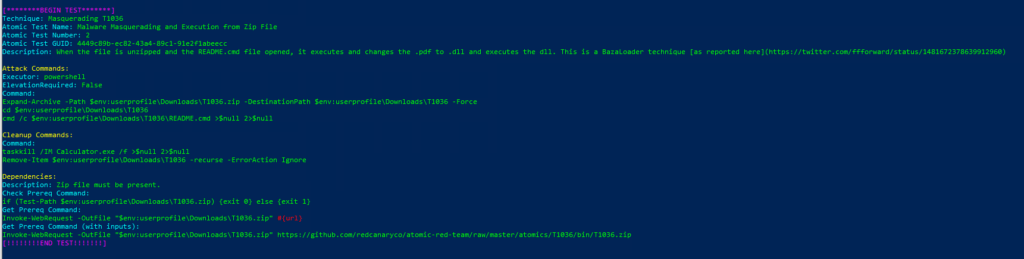
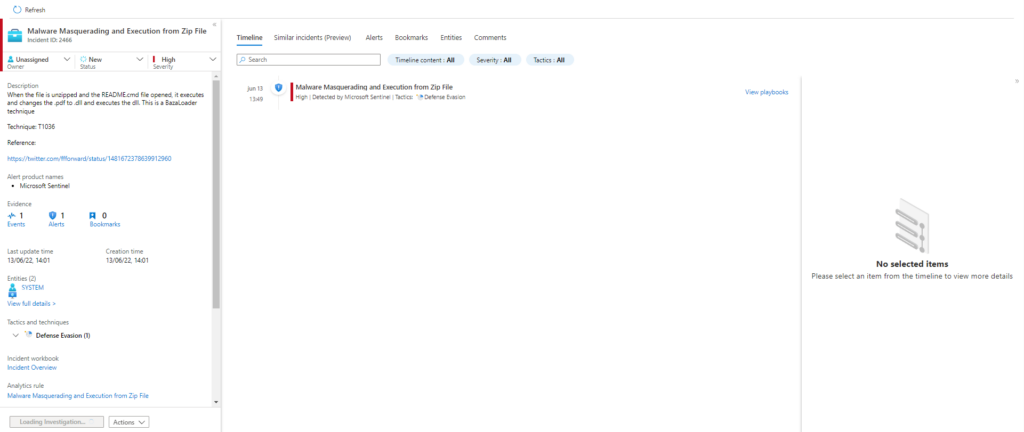
Atomic Test Name: Malware Masquerading and Execution from Zip File
Atomic Test Number: 2
Atomic Test GUID: 4449c89b-ec82-43a4-89c1-91e2f1abeecc
Description: When the file is unzipped and the README.cmd file opened, it executes and changes the .pdf to .dll and executes the dll. This is a BazaLoader technique as reported here
Azure Sentinel
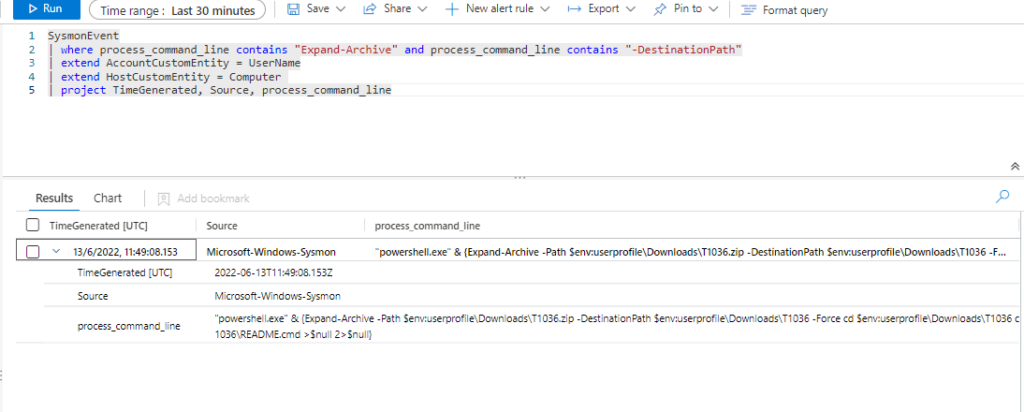
Query
SysmonEvent
| where process_command_line contains "Expand-Archive" and process_command_line contains "-DestinationPath"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
Comenzamos con la sección T1036.003 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1036.003 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1036.003-1 Masquerading as Windows LSASS process
T1036.003-3 Masquerading - cscript.exe running as notepad.exe
T1036.003-4 Masquerading - wscript.exe running as svchost.exe
T1036.003-5 Masquerading - powershell.exe running as taskhostw.exe
T1036.003-6 Masquerading - non-windows exe running as windows exe
T1036.003-7 Masquerading - windows exe running as different windows exe
T1036.003-8 Malicious process Masquerading as LSM.exe
T1036.003-9 File Extension MasqueradingTechnique: Masquerading: Rename System Utilities T1036.003
Atomic Test Name: Masquerading as Windows LSASS process
Atomic Test Number: 1
Atomic Test GUID: 5ba5a3d1-cf3c-4499-968a-a93155d1f717
Description: Copies cmd.exe, renames it, and launches it to masquerade as an instance of lsass.exe.
Upon execution, cmd will be launched by powershell. If using Invoke-AtomicTest, The test will hang until the 120 second timeout cancels the session
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "copy"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))
or (process_command_line contains "copy" and process_command_line contains "\\svchost.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
|project TimeGenerated, Source, process_command_line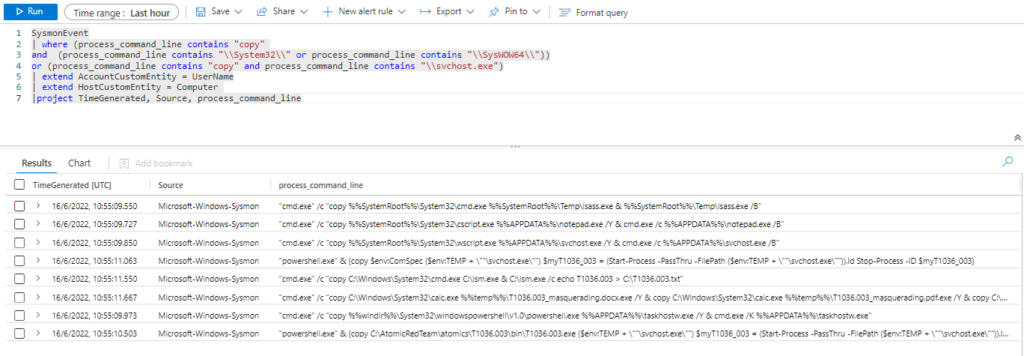
Technique: Masquerading: Rename System Utilities T1036.003
Atomic Test Name: Masquerading – cscript.exe running as notepad.exe
Atomic Test Number: 3
Atomic Test GUID: 3a2a578b-0a01-46e4-92e3-62e2859b42f0
Description: Copies cscript.exe, renames it, and launches it to masquerade as an instance of notepad.exe.
Upon successful execution, cscript.exe is renamed as notepad.exe and executed from non-standard path.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "copy"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))
or (process_command_line contains "copy" and process_command_line contains "\\svchost.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
|project TimeGenerated, Source, process_command_line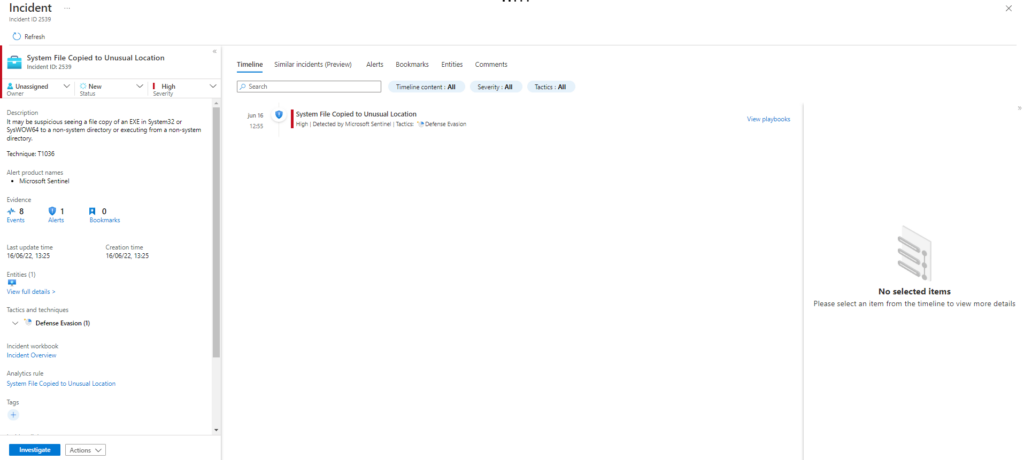

Technique: Masquerading: Rename System Utilities T1036.003
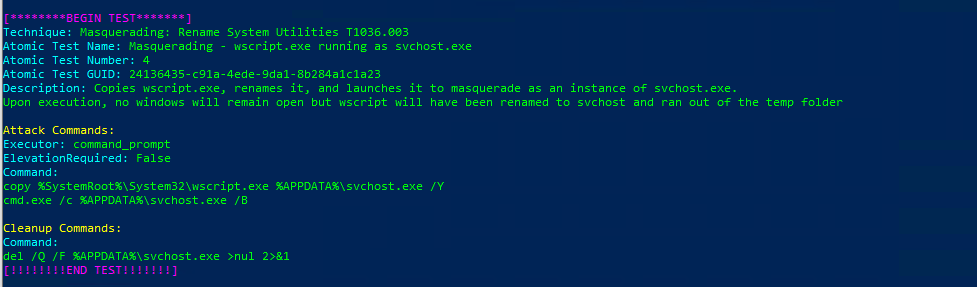
Atomic Test Name: Masquerading – wscript.exe running as svchost.exe
Atomic Test Number: 4
Atomic Test GUID: 24136435-c91a-4ede-9da1-8b284a1c1a23
Description: Copies wscript.exe, renames it, and launches it to masquerade as an instance of svchost.exe.
Upon execution, no windows will remain open but wscript will have been renamed to svchost and ran out of the temp folder
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "copy"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))
or (process_command_line contains "copy" and process_command_line contains "\\svchost.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
|project TimeGenerated, Source, process_command_line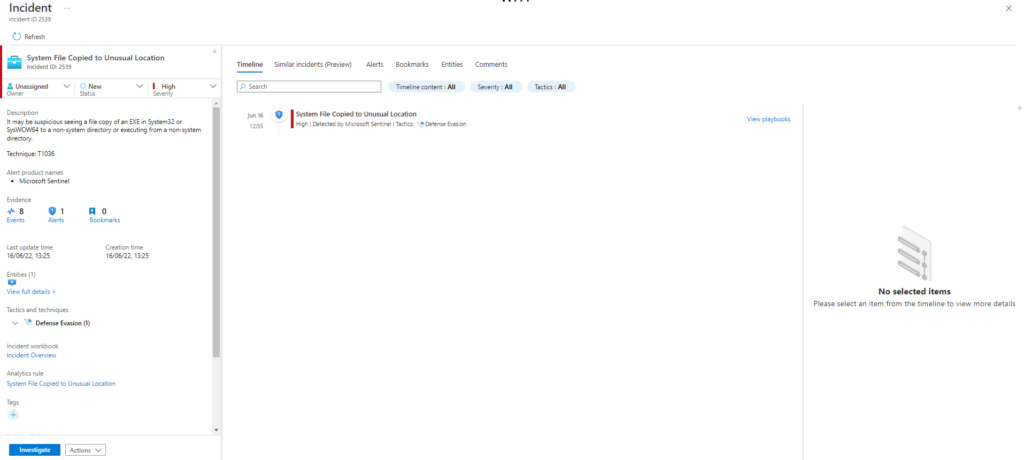

Technique: Masquerading: Rename System Utilities T1036.003
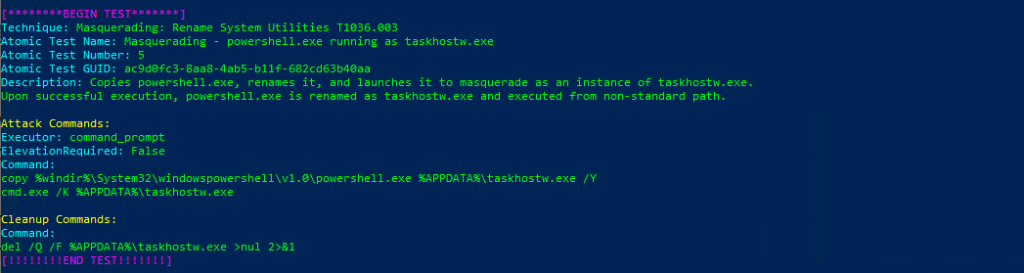
Atomic Test Name: Masquerading – powershell.exe running as taskhostw.exe
Atomic Test Number: 5
Atomic Test GUID: ac9d0fc3-8aa8-4ab5-b11f-682cd63b40aa
Description: Copies powershell.exe, renames it, and launches it to masquerade as an instance of taskhostw.exe. Upon successful execution, powershell.exe is renamed as taskhostw.exe and executed from non-standard path.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "copy"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))
or (process_command_line contains "copy" and process_command_line contains "\\svchost.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
|project TimeGenerated, Source, process_command_line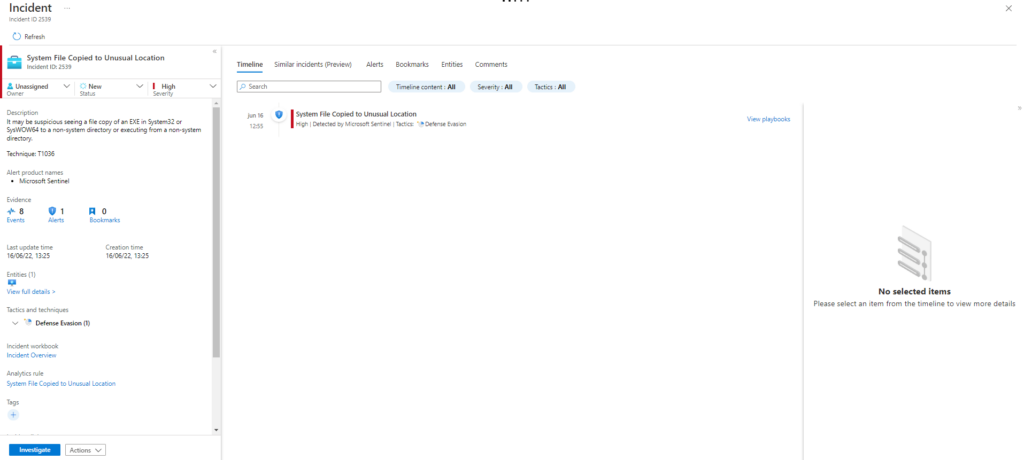

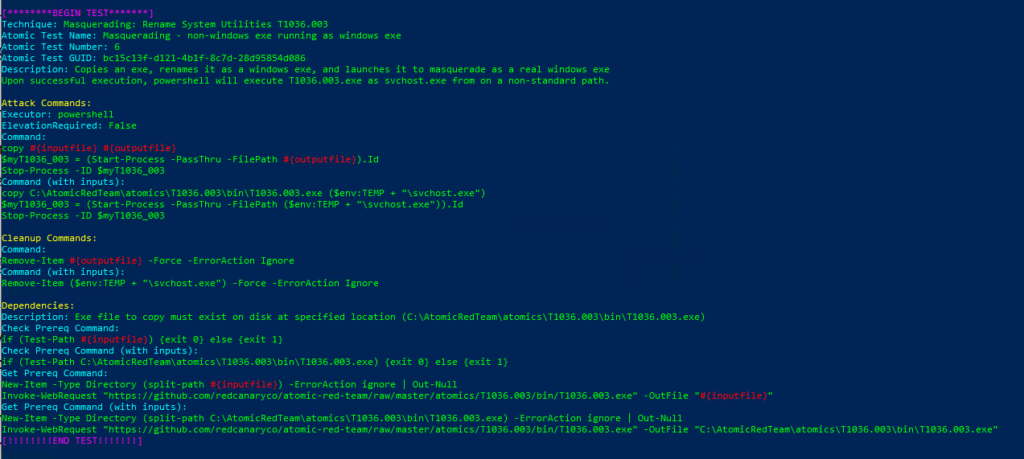
Technique: Masquerading: Rename System Utilities T1036.003
Atomic Test Name: Masquerading – non-windows exe running as windows exe
Atomic Test Number: 6
Atomic Test GUID: bc15c13f-d121-4b1f-8c7d-28d95854d086
Description: Copies an exe, renames it as a windows exe, and launches it to masquerade as a real windows exe Upon successful execution, powershell will execute T1036.003.exe as svchost.exe from on a non-standard path.
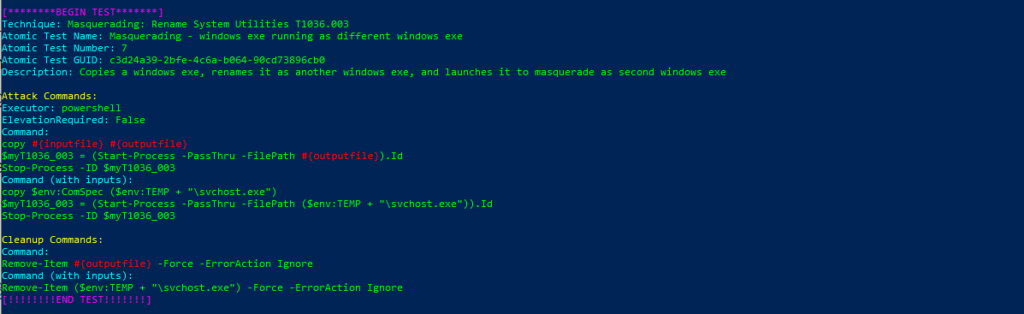
Technique: Masquerading: Rename System Utilities T1036.003
Atomic Test Name: Masquerading – windows exe running as different windows exe
Atomic Test Number: 7
Atomic Test GUID: c3d24a39-2bfe-4c6a-b064-90cd73896cb0
Description: Copies a windows exe, renames it as another windows exe, and launches it to masquerade as second windows exe
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "copy"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))
or (process_command_line contains "copy" and process_command_line contains "\\svchost.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
|project TimeGenerated, Source, process_command_line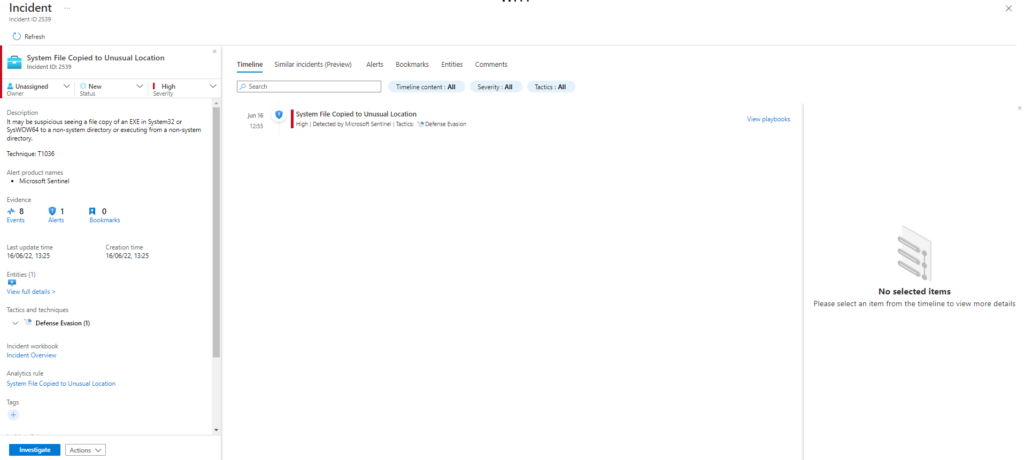

Technique: Masquerading: Rename System Utilities T1036.003
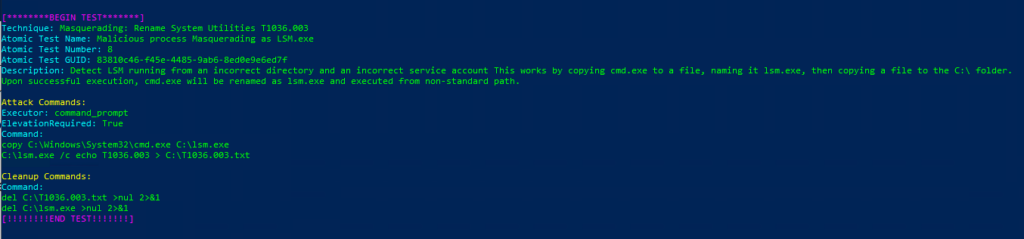
Atomic Test Name: Malicious process Masquerading as LSM.exe
Atomic Test Number: 8
Atomic Test GUID: 83810c46-f45e-4485-9ab6-8ed0e9e6ed7f
Description: Detect LSM running from an incorrect directory and an incorrect service account This works by copying cmd.exe to a file, naming it lsm.exe, then copying a file to the C:\ folder.
Upon successful execution, cmd.exe will be renamed as lsm.exe and executed from non-standard path.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "copy"
and (process_command_line contains "\\System32\\" or process_command_line contains "\\SysWOW64\\"))
or (process_command_line contains "copy" and process_command_line contains "\\svchost.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
|project TimeGenerated, Source, process_command_line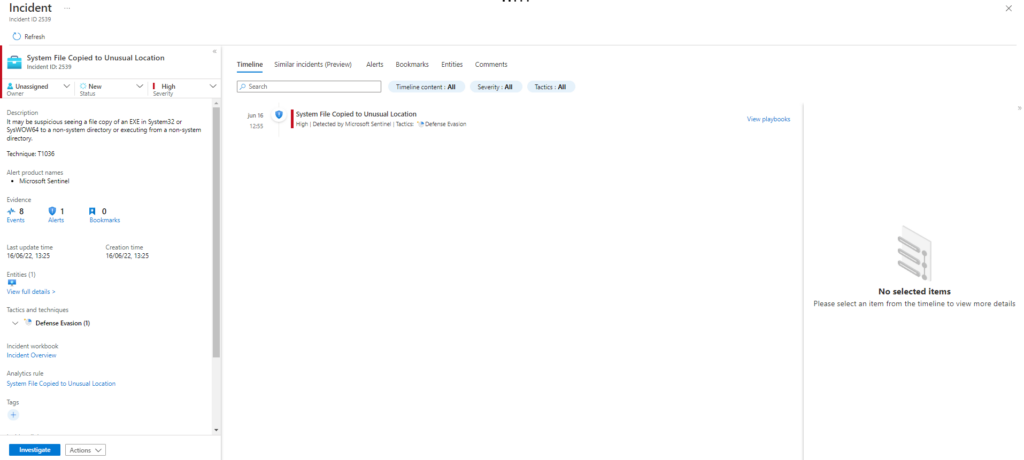

Technique: Masquerading: Rename System Utilities T1036.003
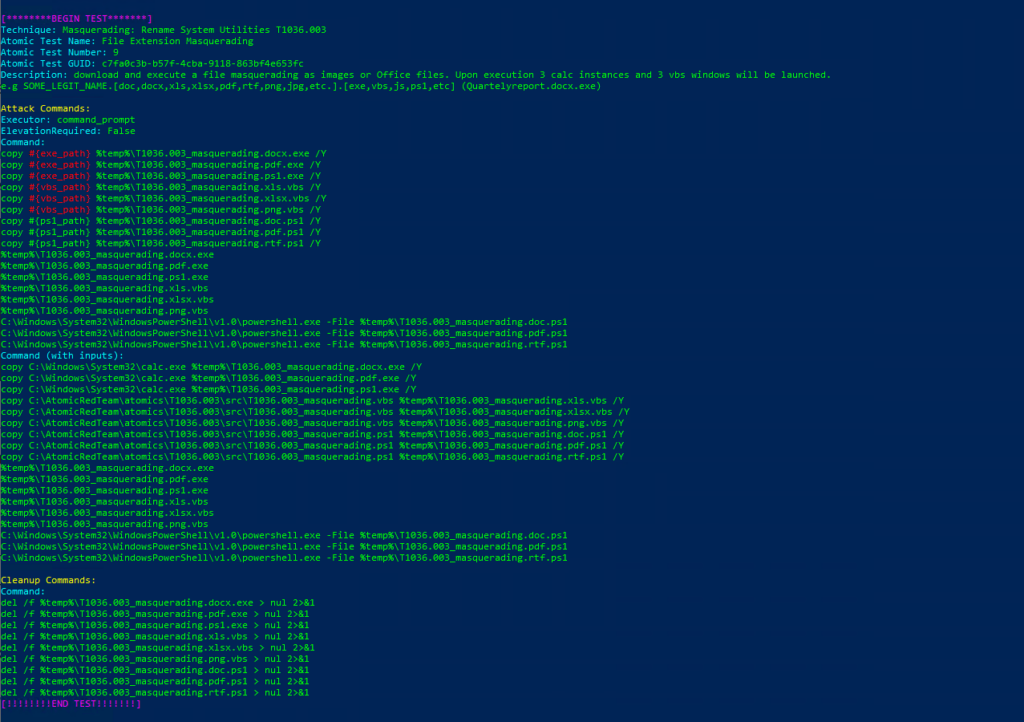
Atomic Test Name: File Extension Masquerading
Atomic Test Number: 9
Atomic Test GUID: c7fa0c3b-b57f-4cba-9118-863bf4e653fc
Description: download and execute a file masquerading as images or Office files. Upon execution 3 calc instances and 3 vbs windows will be launched. e.g SOME_LEGIT_NAME.[doc,docx,xls,xlsx,pdf,rtf,png,jpg,etc.].exe,vbs,js,ps1,etc
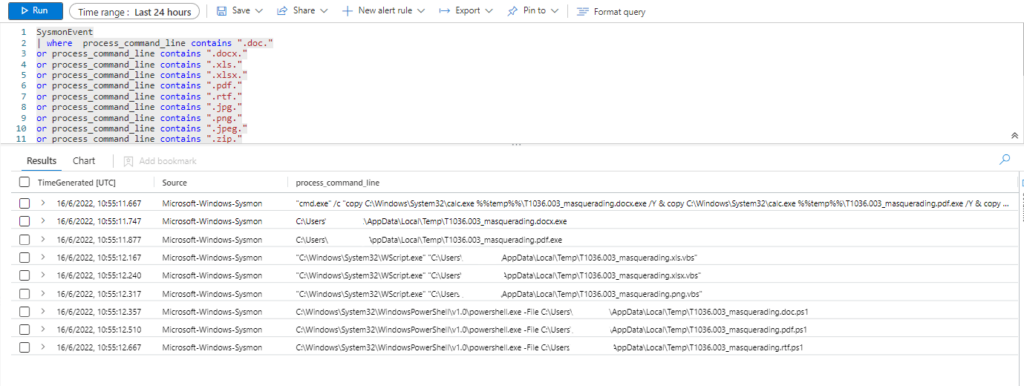
Azure Sentinel
Query: Alert Rule
SysmonEvent
| where process_command_line contains ".doc."
or process_command_line contains ".docx."
or process_command_line contains ".xls."
or process_command_line contains ".xlsx."
or process_command_line contains ".pdf."
or process_command_line contains ".rtf."
or process_command_line contains ".jpg."
or process_command_line contains ".png."
or process_command_line contains ".jpeg."
or process_command_line contains ".zip."
or process_command_line contains ".rar."
or process_command_line contains ".ppt."
or process_command_line contains ".pptx."
|project TimeGenerated, Source, process_command_line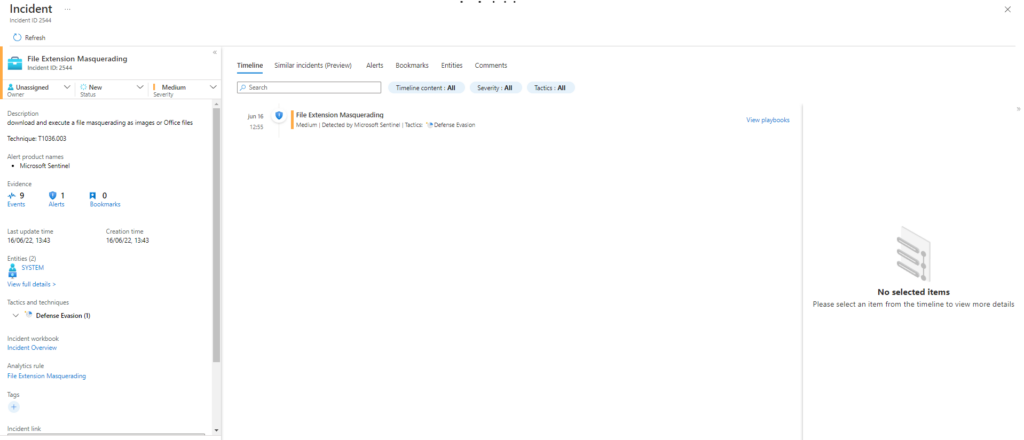
Comenzamos con la sección T1036.004 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1036.004 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1036.004-1 Creating W32Time similar named service using schtasks
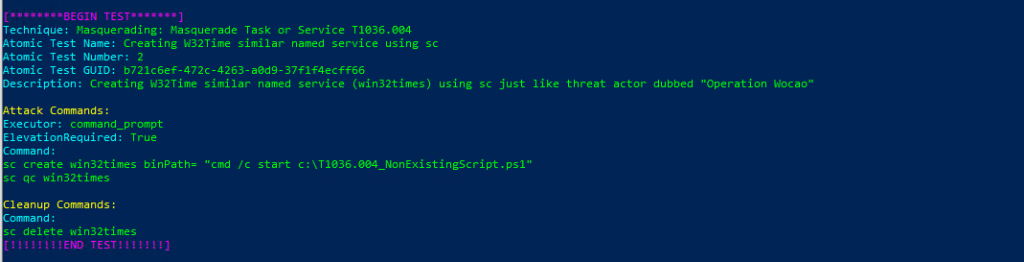
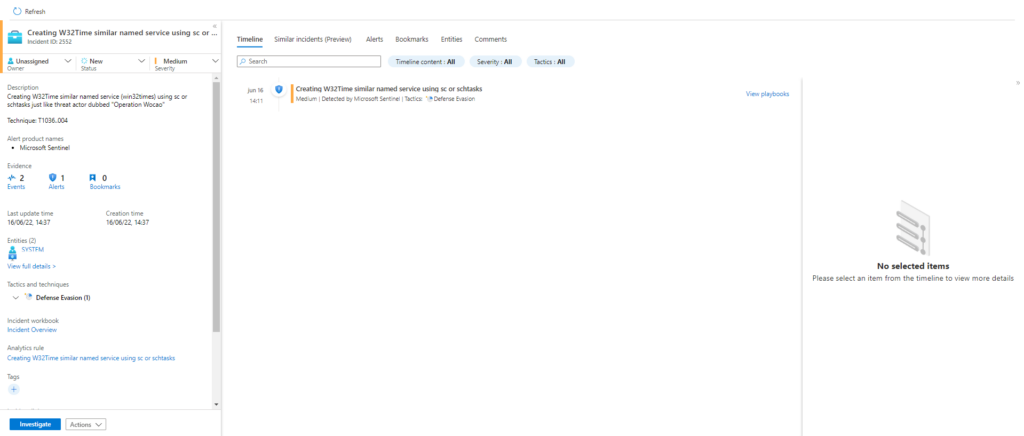
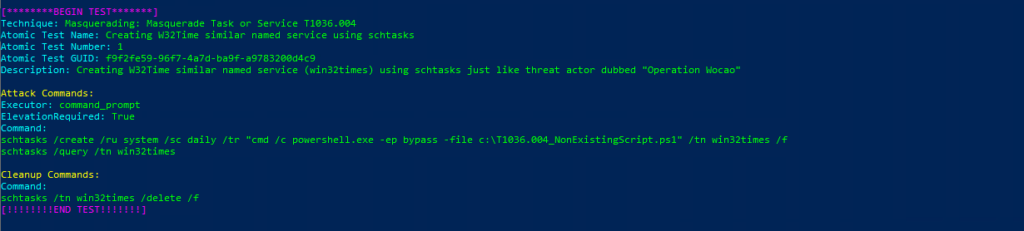
T1036.004-2 Creating W32Time similar named service using scTechnique: Masquerading: Masquerade Task or Service T1036.004
Atomic Test Name: Creating W32Time similar named service using schtasks
Atomic Test Number: 1
Atomic Test GUID: f9f2fe59-96f7-4a7d-ba9f-a9783200d4c9
Description: Creating W32Time similar named service (win32times) using schtasks just like threat actor dubbed «Operation Wocao»
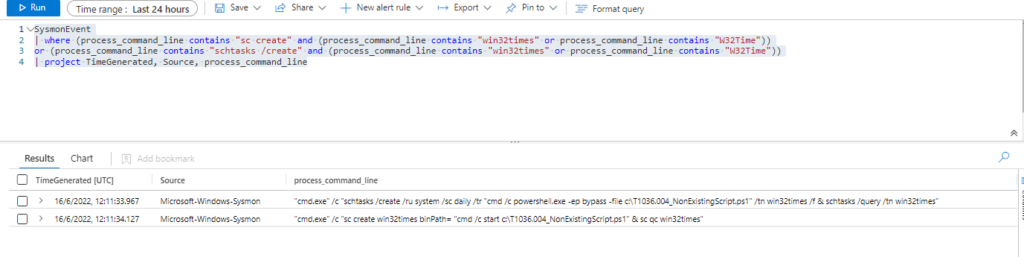
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "sc create" and (process_command_line contains "win32times" or process_command_line contains "W32Time"))
or (process_command_line contains "schtasks /create" and (process_command_line contains "win32times" or process_command_line contains "W32Time"))
| project TimeGenerated, Source, process_command_line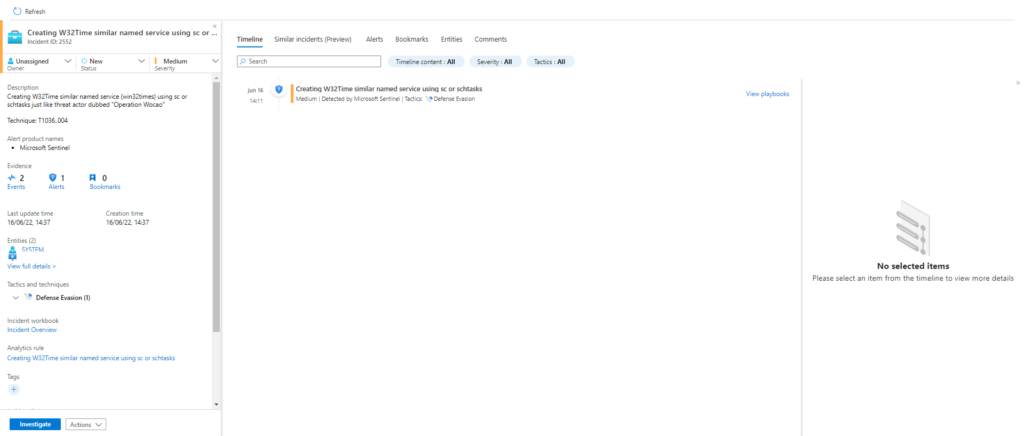
Technique: Masquerading: Masquerade Task or Service T1036.004
Atomic Test Name: Creating W32Time similar named service using sc
Atomic Test Number: 2
Atomic Test GUID: b721c6ef-472c-4263-a0d9-37f1f4ecff66
Description: Creating W32Time similar named service (win32times) using sc just like threat actor dubbed «Operation Wocao»