Seguimos configurando nuestra infraestructura SIRP (https://red-orbita.com/?p=8726),En esta entrada veremos como integrar las alertas generadas por rootcheck en wazuh con thehive
Para ello nos vamos al servidor donde tenemos implementado elasalert y creamos las siguientes reglas:
es_host: localhost
es_port: 9200
name: Host-based anomaly detection event
type: frequency
index: wazuh-alerts-3.x-*
num_events: 2
timeframe:
hours: 1
filter:
- term:
rule.id: "516"
alert: hivealerter
hive_connection:
hive_host: http://ip_thehive
hive_port: 9000
hive_apikey: <Paste API key for elastalert user here>
hive_alert_config:
title: '{match[data][title]}'
type: 'external'
source: 'elastalert'
description: '{match[full_log]}'
severity: 2
tags: ['{rule[name]}', '{match[agent][name]}', '{match[rule][groups]}', '{match[_id]}']
tlp: 3
status: 'New'
follow: True
hive_observable_data_mapping:
- ip: "{match[src_ip]}"es_host: localhost
es_port: 9200
name: Host-based anomaly detection event 510
type: frequency
index: wazuh-alerts-3.x-*
num_events: 2
timeframe:
hours: 1
filter:
- term:
rule.id: "510"
alert: hivealerter
hive_connection:
hive_host: http://ip_hive
hive_port: 9000
hive_apikey: <Paste API key for elastalert user here>
hive_alert_config:
title: '{match[data][title]}'
type: 'external'
source: 'elastalert'
description: '{match[full_log]}'
severity: 2
tags: ['{rule[name]}', '{match[agent][name]}', '{match[rule][groups]}', '{match[_id]}']
tlp: 3
status: 'New'
follow: True
hive_observable_data_mapping:
- ip: "{match[src_ip]}"Reiniciamos el servicio
systemctl restart elastalert.service
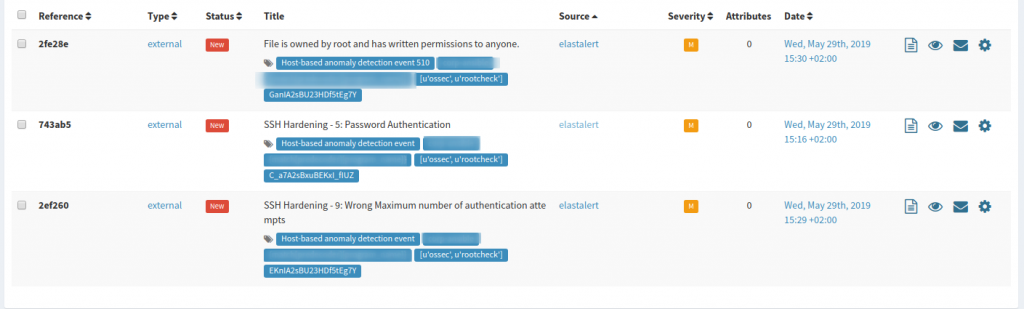
Cuando genere alguna alerta veremos algo similar a lo siguiente:
:wq!