Instructions:
- Uncompress the lab (pass: cyberdefenders.org)
Scenario:
Our intrusion detection system has alerted us to suspicious behavior on a workstation, pointing to a likely malware intrusion. A memory dump of this system has been taken for analysis. Your task is to analyze this dump, trace the malware’s actions, and report key findings. This analysis is critical in understanding the breach and preventing further compromise.
Tools:
- Volatility 3
#1 Respuesta: ChromeSetup.exe
We need to identify the process responsible for this suspicious behavior. What is the name of the suspicious process?Obtención de la evidencia
Utilizamos el siguiente comando para realizar el análisis inicial de la memoria:
vol -f memory.dmp windows.malfind El resultado muestra los procesos sospechosos:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
PID Process Start VPN End VPN Tag Protection CommitCharge PrivateMemory File output Notes Hexdump Disasm
2128 SearchApp.exe 0x25942230000 0x2594224ffff VadS PAGE_EXECUTE_READWRITE 4 1 Disabled N/A
48 89 54 24 10 48 89 4c H.T$.H.L
24 08 4c 89 44 24 18 4c $.L.D$.L
89 4c 24 20 48 8b 41 28 .L$.H.A(
48 8b 48 08 48 8b 51 50 H.H.H.QP
48 83 e2 f8 48 8b ca 48 H...H..H
b8 60 00 23 42 59 02 00 .`.#BY..
00 48 2b c8 48 81 f9 70 .H+.H..p
0f 00 00 76 09 48 c7 c1 ...v.H..
0x25942230000: mov qword ptr [rsp + 0x10], rdx
0x25942230005: mov qword ptr [rsp + 8], rcx
0x2594223000a: mov qword ptr [rsp + 0x18], r8
0x2594223000f: mov qword ptr [rsp + 0x20], r9
0x25942230014: mov rax, qword ptr [rcx + 0x28]
0x25942230018: mov rcx, qword ptr [rax + 8]
0x2594223001c: mov rdx, qword ptr [rcx + 0x50]
0x25942230020: and rdx, 0xfffffffffffffff8
0x25942230024: mov rcx, rdx
0x25942230027: movabs rax, 0x25942230060
0x25942230031: sub rcx, rax
0x25942230034: cmp rcx, 0xf70
0x2594223003b: jbe 0x25942230046
2128 SearchApp.exe 0x259535c0000 0x25953623fff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
e9 fb ff fd ef ff ff ff ........
ff cc cc cc cc cc cc cc ........
e9 eb 03 fe ef ff ff ff ........
ff cc cc cc cc cc cc cc ........
e9 db 0f fe ef ff ff ff ........
ff cc cc cc cc cc cc cc ........
e9 cb 17 fe ef ff ff ff ........
ff cc cc cc cc cc cc cc ........
0x259535c0000: jmp 0x259435a0000
7068 RuntimeBroker. 0x1db7d360000 0x1db7d360fff Vad PAGE_EXECUTE_READWRITE 0 0 Disabled N/A
00 00 00 00 00 00 00 00 ........
fe ff ff ff f7 2f 00 00 ...../..
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
0x1db7d360000: add byte ptr [rax], al
0x1db7d360002: add byte ptr [rax], al
0x1db7d360004: add byte ptr [rax], al
0x1db7d360006: add byte ptr [rax], al
7484 smartscreen.ex 0x1f413fe0000 0x1f413ffffff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
48 89 54 24 10 48 89 4c H.T$.H.L
24 08 4c 89 44 24 18 4c $.L.D$.L
89 4c 24 20 48 8b 41 28 .L$.H.A(
48 8b 48 08 48 8b 51 50 H.H.H.QP
48 83 e2 f8 48 8b ca 48 H...H..H
b8 60 00 fe 13 f4 01 00 .`......
00 48 2b c8 48 81 f9 70 .H+.H..p
0f 00 00 76 09 48 c7 c1 ...v.H..
0x1f413fe0000: mov qword ptr [rsp + 0x10], rdx
0x1f413fe0005: mov qword ptr [rsp + 8], rcx
0x1f413fe000a: mov qword ptr [rsp + 0x18], r8
0x1f413fe000f: mov qword ptr [rsp + 0x20], r9
0x1f413fe0014: mov rax, qword ptr [rcx + 0x28]
0x1f413fe0018: mov rcx, qword ptr [rax + 8]
0x1f413fe001c: mov rdx, qword ptr [rcx + 0x50]
0x1f413fe0020: and rdx, 0xfffffffffffffff8
0x1f413fe0024: mov rcx, rdx
0x1f413fe0027: movabs rax, 0x1f413fe0060
0x1f413fe0031: sub rcx, rax
0x1f413fe0034: cmp rcx, 0xf70
0x1f413fe003b: jbe 0x1f413fe0046
7484 smartscreen.ex 0x1f414320000 0x1f414383fff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
e9 fb 07 07 00 00 00 00 ........
00 cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
0x1f414320000: jmp 0x1f414390800
0x1f414320005: add byte ptr [rax], al
0x1f414320007: add byte ptr [rax], al
0x1f414320009: int3
0x1f41432000a: int3
0x1f41432000b: int3
0x1f41432000c: int3
0x1f41432000d: int3
0x1f41432000e: int3
0x1f41432000f: int3
0x1f414320010: int3
0x1f414320011: int3
0x1f414320012: int3
0x1f414320013: int3
0x1f414320014: int3
0x1f414320015: int3
0x1f414320016: int3
0x1f414320017: int3
0x1f414320018: int3
0x1f414320019: int3
0x1f41432001a: int3
0x1f41432001b: int3
0x1f41432001c: int3
0x1f41432001d: int3
0x1f41432001e: int3
0x1f41432001f: int3
0x1f414320020: int3
0x1f414320021: int3
0x1f414320022: int3
0x1f414320023: int3
0x1f414320024: int3
0x1f414320025: int3
0x1f414320026: int3
0x1f414320027: int3
0x1f414320028: int3
0x1f414320029: int3
0x1f41432002a: int3
0x1f41432002b: int3
0x1f41432002c: int3
0x1f41432002d: int3
0x1f41432002e: int3
0x1f41432002f: int3
0x1f414320030: int3
0x1f414320031: int3
0x1f414320032: int3
0x1f414320033: int3
0x1f414320034: int3
0x1f414320035: int3
0x1f414320036: int3
0x1f414320037: int3
0x1f414320038: int3
0x1f414320039: int3
0x1f41432003a: int3
0x1f41432003b: int3
0x1f41432003c: int3
0x1f41432003d: int3
0x1f41432003e: int3
0x1f41432003f: int3
7484 smartscreen.ex 0x1f4247d0000 0x1f4247effff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
48 89 54 24 10 48 89 4c H.T$.H.L
24 08 4c 89 44 24 18 4c $.L.D$.L
89 4c 24 20 48 8b 41 28 .L$.H.A(
48 8b 48 08 48 8b 51 50 H.H.H.QP
48 83 e2 f8 48 8b ca 48 H...H..H
b8 60 00 7d 24 f4 01 00 .`.}$...
00 48 2b c8 48 81 f9 70 .H+.H..p
0f 00 00 76 09 48 c7 c1 ...v.H..
0x1f4247d0000: mov qword ptr [rsp + 0x10], rdx
0x1f4247d0005: mov qword ptr [rsp + 8], rcx
0x1f4247d000a: mov qword ptr [rsp + 0x18], r8
0x1f4247d000f: mov qword ptr [rsp + 0x20], r9
0x1f4247d0014: mov rax, qword ptr [rcx + 0x28]
0x1f4247d0018: mov rcx, qword ptr [rax + 8]
0x1f4247d001c: mov rdx, qword ptr [rcx + 0x50]
0x1f4247d0020: and rdx, 0xfffffffffffffff8
0x1f4247d0024: mov rcx, rdx
0x1f4247d0027: movabs rax, 0x1f4247d0060
0x1f4247d0031: sub rcx, rax
0x1f4247d0034: cmp rcx, 0xf70
0x1f4247d003b: jbe 0x1f4247d0046
7484 smartscreen.ex 0x1f424860000 0x1f4248c3fff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
e9 fb ff 06 00 00 00 00 ........
00 cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
cc cc cc cc cc cc cc cc ........
0x1f424860000: jmp 0x1f4248d0000
0x1f424860005: add byte ptr [rax], al
0x1f424860007: add byte ptr [rax], al
0x1f424860009: int3
0x1f42486000a: int3
0x1f42486000b: int3
0x1f42486000c: int3
0x1f42486000d: int3
0x1f42486000e: int3
0x1f42486000f: int3
0x1f424860010: int3
0x1f424860011: int3
0x1f424860012: int3
0x1f424860013: int3
0x1f424860014: int3
0x1f424860015: int3
0x1f424860016: int3
0x1f424860017: int3
0x1f424860018: int3
0x1f424860019: int3
0x1f42486001a: int3
0x1f42486001b: int3
0x1f42486001c: int3
0x1f42486001d: int3
0x1f42486001e: int3
0x1f42486001f: int3
0x1f424860020: int3
0x1f424860021: int3
0x1f424860022: int3
0x1f424860023: int3
0x1f424860024: int3
0x1f424860025: int3
0x1f424860026: int3
0x1f424860027: int3
0x1f424860028: int3
0x1f424860029: int3
0x1f42486002a: int3
0x1f42486002b: int3
0x1f42486002c: int3
0x1f42486002d: int3
0x1f42486002e: int3
0x1f42486002f: int3
0x1f424860030: int3
0x1f424860031: int3
0x1f424860032: int3
0x1f424860033: int3
0x1f424860034: int3
0x1f424860035: int3
0x1f424860036: int3
0x1f424860037: int3
0x1f424860038: int3
0x1f424860039: int3
0x1f42486003a: int3
0x1f42486003b: int3
0x1f42486003c: int3
0x1f42486003d: int3
0x1f42486003e: int3
0x1f42486003f: int3
7484 smartscreen.ex 0x1f4351d0000 0x1f4351effff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
48 89 54 24 10 48 89 4c H.T$.H.L
24 08 4c 89 44 24 18 4c $.L.D$.L
89 4c 24 20 48 8b 41 28 .L$.H.A(
48 8b 48 08 48 8b 51 50 H.H.H.QP
48 83 e2 f8 48 8b ca 48 H...H..H
b8 60 00 1d 35 f4 01 00 .`..5...
00 48 2b c8 48 81 f9 70 .H+.H..p
0f 00 00 76 09 48 c7 c1 ...v.H..
0x1f4351d0000: mov qword ptr [rsp + 0x10], rdx
0x1f4351d0005: mov qword ptr [rsp + 8], rcx
0x1f4351d000a: mov qword ptr [rsp + 0x18], r8
0x1f4351d000f: mov qword ptr [rsp + 0x20], r9
0x1f4351d0014: mov rax, qword ptr [rcx + 0x28]
0x1f4351d0018: mov rcx, qword ptr [rax + 8]
0x1f4351d001c: mov rdx, qword ptr [rcx + 0x50]
0x1f4351d0020: and rdx, 0xfffffffffffffff8
0x1f4351d0024: mov rcx, rdx
0x1f4351d0027: movabs rax, 0x1f4351d0060
0x1f4351d0031: sub rcx, rax
0x1f4351d0034: cmp rcx, 0xf70
0x1f4351d003b: jbe 0x1f4351d0046
7780 OneDrive.exe 0x76b0000 0x76bffff VadS PAGE_EXECUTE_READWRITE 16 1 Disabled N/A
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
f8 ff 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
0x76b0000: add byte ptr [eax], al
0x76b0002: add byte ptr [eax], al
0x76b0004: add byte ptr [eax], al
0x76b0006: add byte ptr [eax], al
0x76b0008: add byte ptr [eax], al
0x76b000a: add byte ptr [eax], al
0x76b000c: add byte ptr [eax], al
0x76b000e: add byte ptr [eax], al
0x76b0010: clc
0x76b0011: inc dword ptr [eax]
0x76b0013: add byte ptr [eax], al
0x76b0015: add byte ptr [eax], al
0x76b0017: add byte ptr [eax], al
0x76b0019: add byte ptr [eax], al
0x76b001b: add byte ptr [eax], al
0x76b001d: add byte ptr [eax], al
0x76b001f: add byte ptr [eax], al
0x76b0021: add byte ptr [eax], al
0x76b0023: add byte ptr [eax], al
0x76b0025: add byte ptr [eax], al
0x76b0027: add byte ptr [eax], al
0x76b0029: add byte ptr [eax], al
0x76b002b: add byte ptr [eax], al
0x76b002d: add byte ptr [eax], al
0x76b002f: add byte ptr [eax], al
0x76b0031: add byte ptr [eax], al
0x76b0033: add byte ptr [eax], al
0x76b0035: add byte ptr [eax], al
0x76b0037: add byte ptr [eax], al
0x76b0039: add byte ptr [eax], al
0x76b003b: add byte ptr [eax], al
0x76b003d: add byte ptr [eax], al
5912 WWAHost.exe 0x18909a60000 0x18909a7ffff VadS PAGE_EXECUTE_READWRITE 2 1 Disabled N/A
48 89 54 24 10 48 89 4c H.T$.H.L
24 08 4c 89 44 24 18 4c $.L.D$.L
89 4c 24 20 48 8b 41 28 .L$.H.A(
48 8b 48 08 48 8b 51 50 H.H.H.QP
48 83 e2 f8 48 8b ca 48 H...H..H
b8 60 00 a6 09 89 01 00 .`......
00 48 2b c8 48 81 f9 70 .H+.H..p
0f 00 00 76 09 48 c7 c1 ...v.H..
0x18909a60000: mov qword ptr [rsp + 0x10], rdx
0x18909a60005: mov qword ptr [rsp + 8], rcx
0x18909a6000a: mov qword ptr [rsp + 0x18], r8
0x18909a6000f: mov qword ptr [rsp + 0x20], r9
0x18909a60014: mov rax, qword ptr [rcx + 0x28]
0x18909a60018: mov rcx, qword ptr [rax + 8]
0x18909a6001c: mov rdx, qword ptr [rcx + 0x50]
0x18909a60020: and rdx, 0xfffffffffffffff8
0x18909a60024: mov rcx, rdx
0x18909a60027: movabs rax, 0x18909a60060
0x18909a60031: sub rcx, rax
0x18909a60034: cmp rcx, 0xf70
0x18909a6003b: jbe 0x18909a60046
5912 WWAHost.exe 0x1890a380000 0x1890a3e3fff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
e9 fb ff 08 00 00 00 00 ........
00 cc cc cc cc cc cc cc ........
e9 eb 07 09 00 00 00 00 ........
00 cc cc cc cc cc cc cc ........
e9 db 0f 09 00 00 00 00 ........
00 cc cc cc cc cc cc cc ........
e9 cb 0b 09 00 00 00 00 ........
00 cc cc cc cc cc cc cc ........
0x1890a380000: jmp 0x1890a410000
0x1890a380005: add byte ptr [rax], al
0x1890a380007: add byte ptr [rax], al
0x1890a380009: int3
0x1890a38000a: int3
0x1890a38000b: int3
0x1890a38000c: int3
0x1890a38000d: int3
0x1890a38000e: int3
0x1890a38000f: int3
0x1890a380010: jmp 0x1890a410800
0x1890a380015: add byte ptr [rax], al
0x1890a380017: add byte ptr [rax], al
0x1890a380019: int3
0x1890a38001a: int3
0x1890a38001b: int3
0x1890a38001c: int3
0x1890a38001d: int3
0x1890a38001e: int3
0x1890a38001f: int3
0x1890a380020: jmp 0x1890a411000
0x1890a380025: add byte ptr [rax], al
0x1890a380027: add byte ptr [rax], al
0x1890a380029: int3
0x1890a38002a: int3
0x1890a38002b: int3
0x1890a38002c: int3
0x1890a38002d: int3
0x1890a38002e: int3
0x1890a38002f: int3
0x1890a380030: jmp 0x1890a410c00
0x1890a380035: add byte ptr [rax], al
0x1890a380037: add byte ptr [rax], al
0x1890a380039: int3
0x1890a38003a: int3
0x1890a38003b: int3
0x1890a38003c: int3
0x1890a38003d: int3
0x1890a38003e: int3
0x1890a38003f: int3 Al analizar losprocesos identificamos el proceso OneDrive.exe con PID 7780 utilizando windows.pstree para visualizar la estructura de directorios.
vol -f memory.dmp windows.pstree
Output
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
4 0 System 0xca82b0e88040 165 - N/A False 2024-02-01 19:48:22.000000 N/A - - -
* 320 4 smss.exe 0xca82b1a95040 2 - N/A False 2024-02-01 19:48:22.000000 N/A \Device\HarddiskVolume3\Windows\System32\smss.exe \SystemRoot\System32\smss.exe \SystemRoot\System32\smss.exe
* 108 4 Registry 0xca82b0eeb080 4 - N/A False 2024-02-01 19:48:15.000000 N/A Registry - -
* 1828 4 MemCompression 0xca82b39b9040 34 - N/A False 2024-02-01 19:48:24.000000 N/A MemCompression - -
448 440 csrss.exe 0xca82b1f68080 11 - 0 False 2024-02-01 19:48:23.000000 N/A \Device\HarddiskVolume3\Windows\System32\csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 C:\Windows\system32\csrss.exe
524 440 wininit.exe 0xca82b2843080 2 - 0 False 2024-02-01 19:48:23.000000 N/A \Device\HarddiskVolume3\Windows\System32\wininit.exe wininit.exe C:\Windows\system32\wininit.exe
* 676 524 lsass.exe 0xca82b2923080 10 - 0 False 2024-02-01 19:48:23.000000 N/A \Device\HarddiskVolume3\Windows\System32\lsass.exe C:\Windows\system32\lsass.exe C:\Windows\system32\lsass.exe
* 660 524 services.exe 0xca82b28e9080 8 - 0 False 2024-02-01 19:48:23.000000 N/A \Device\HarddiskVolume3\Windows\System32\services.exe C:\Windows\system32\services.exe C:\Windows\system32\services.exe
** 2564 660 spoolsv.exe 0xca82b3c5b200 8 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\spoolsv.exe C:\Windows\System32\spoolsv.exe C:\Windows\System32\spoolsv.exe
** 5132 660 svchost.exe 0xca82b7752280 9 - 0 False 2024-02-01 19:48:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s PcaSvc C:\Windows\system32\svchost.exe
** 3104 660 svchost.exe 0xca82b7229080 12 - 0 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s CDPSvc C:\Windows\system32\svchost.exe
** 1068 660 svchost.exe 0xca82b3115300 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s lmhosts C:\Windows\System32\svchost.exe
** 2092 660 svchost.exe 0xca82b0f38080 13 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
*** 7272 2092 audiodg.exe 0xca82b8308080 5 - 0 False 2024-02-01 19:48:49.000000 N/A \Device\HarddiskVolume3\Windows\System32\audiodg.exe C:\Windows\system32\AUDIODG.EXE 0x4b8 C:\Windows\system32\AUDIODG.EXE
** 2612 660 svchost.exe 0xca82b3ca22c0 5 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p C:\Windows\system32\svchost.exe
** 3128 660 svchost.exe 0xca82b3e6b080 7 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s LanmanServer C:\Windows\system32\svchost.exe
** 3160 660 svchost.exe 0xca82b3e9f2c0 2 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s SstpSvc C:\Windows\system32\svchost.exe
** 5220 660 svchost.exe 0xca82b77792c0 5 - 1 False 2024-02-01 19:48:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k ClipboardSvcGroup -p -s cbdhsvc C:\Windows\system32\svchost.exe
** 1644 660 svchost.exe 0xca82b38c7300 3 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s DispBrokerDesktopSvc C:\Windows\system32\svchost.exe
** 3692 660 svchost.exe 0xca82b7061280 6 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s TabletInputService C:\Windows\System32\svchost.exe
*** 3936 3692 ctfmon.exe 0xca82b7107240 11 - 1 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\ctfmon.exe "ctfmon.exe" C:\Windows\system32\ctfmon.exe
** 6252 660 SearchIndexer. 0xca82b7daa0c0 16 - 0 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\System32\SearchIndexer.exe C:\Windows\system32\SearchIndexer.exe /Embedding C:\Windows\system32\SearchIndexer.exe
*** 8696 6252 SearchProtocol 0xca82b8c08300 9 - 0 False 2024-02-01 19:53:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\SearchProtocolHost.exe "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" C:\Windows\system32\SearchProtocolHost.exe
*** 3004 6252 SearchFilterHo 0xca82b1c74300 4 - 0 False 2024-02-01 19:53:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\SearchFilterHost.exe "C:\Windows\system32\SearchFilterHost.exe" 0 812 816 824 8192 820 796 C:\Windows\system32\SearchFilterHost.exe
** 1136 660 svchost.exe 0xca82b313e300 8 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s EventLog C:\Windows\System32\svchost.exe
** 1144 660 svchost.exe 0xca82b313f300 12 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s Schedule C:\Windows\system32\svchost.exe
*** 3152 1144 taskhostw.exe 0xca82b7681280 7 - 1 False 2024-02-01 19:48:27.000000 N/A \Device\HarddiskVolume3\Windows\System32\taskhostw.exe taskhostw.exe C:\Windows\system32\taskhostw.exe
*** 3116 1144 taskhostw.exe 0xca82b3e6a300 8 - 1 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\taskhostw.exe taskhostw.exe {222A245B-E637-4AE9-A93F-A59CA119A75E} C:\Windows\system32\taskhostw.exe
*** 7500 1144 MicrosoftEdgeU 0xca82b79e5080 3 - 0 True 2024-02-01 19:51:24.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /c C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe
** 1156 660 svchost.exe 0xca82b3140080 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s ProfSvc C:\Windows\system32\svchost.exe
** 3208 660 svchost.exe 0xca82b3ed6280 3 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s TrkWks C:\Windows\System32\svchost.exe
** 1164 660 svchost.exe 0xca82b3153280 3 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s NcbService C:\Windows\System32\svchost.exe
** 2704 660 svchost.exe 0xca82b3cbb300 5 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p -s LanmanWorkstation C:\Windows\System32\svchost.exe
** 1172 660 svchost.exe 0xca82b3152080 4 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s TimeBrokerSvc C:\Windows\system32\svchost.exe
** 1684 660 svchost.exe 0xca82b390c300 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p -s NlaSvc C:\Windows\System32\svchost.exe
** 4760 660 svchost.exe 0xca82b7757280 4 - 0 False 2024-02-01 19:48:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost C:\Windows\System32\svchost.exe
** 3228 660 svchost.exe 0xca82b7682080 3 - 0 False 2024-02-01 19:48:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k wsappx -p -s ClipSVC C:\Windows\System32\svchost.exe
** 3248 660 VGAuthService. 0xca82b3edd300 3 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe "C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe" C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe
** 4276 660 dllhost.exe 0xca82b7320280 15 - 0 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\dllhost.exe C:\Windows\system32\dllhost.exe /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235} C:\Windows\system32\dllhost.exe
** 1716 660 svchost.exe 0xca82b39042c0 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s EventSystem C:\Windows\system32\svchost.exe
** 3256 660 vm3dservice.ex 0xca82b3edb0c0 5 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\vm3dservice.exe C:\Windows\system32\vm3dservice.exe C:\Windows\system32\vm3dservice.exe
*** 3544 3256 vm3dservice.ex 0xca82b3fce200 6 - 1 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\vm3dservice.exe vm3dservice.exe -n C:\Windows\system32\vm3dservice.exe
** 1724 660 svchost.exe 0xca82b3920080 6 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s SysMain C:\Windows\system32\svchost.exe
** 4796 660 svchost.exe 0xca82b758d300 7 - 0 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -s RmSvc C:\Windows\System32\svchost.exe
** 2244 660 svchost.exe 0xca82b0e970c0 10 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k NetworkService -p -s Dnscache C:\Windows\system32\svchost.exe
** 1740 660 svchost.exe 0xca82b3907080 4 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k netsvcs -p -s Themes C:\Windows\System32\svchost.exe
** 7380 660 svchost.exe 0xca82b79841c0 5 - 0 False 2024-02-01 19:49:00.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s lfsvc C:\Windows\system32\svchost.exe
** 2776 660 svchost.exe 0xca82b3d1c2c0 7 - 1 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc C:\Windows\system32\svchost.exe
** 3288 660 wlms.exe 0xca82b3ef1240 3 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\wlms\wlms.exe C:\Windows\system32\wlms\wlms.exe C:\Windows\system32\wlms\wlms.exe
** 3296 660 vmtoolsd.exe 0xca82b3ef4280 12 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\vmtoolsd.exe "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
** 740 660 svchost.exe 0xca82b30c7240 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s gpsvc C:\Windows\system32\svchost.exe
** 4836 660 msdtc.exe 0xca82b75a7280 12 - 0 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\msdtc.exe C:\Windows\System32\msdtc.exe C:\Windows\System32\msdtc.exe
** 2280 660 svchost.exe 0xca82b0fc0080 3 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
** 1260 660 svchost.exe 0xca82b318f2c0 4 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork -p C:\Windows\system32\svchost.exe
** 2288 660 svchost.exe 0xca82b0fbe080 5 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\system32\svchost.exe
** 3832 660 svchost.exe 0xca82b8b352c0 6 - 1 False 2024-02-01 19:50:05.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k UnistackSvcGroup C:\Windows\System32\svchost.exe
** 3852 660 svchost.exe 0xca82b1c90240 13 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k netsvcs C:\Windows\System32\svchost.exe
** 2328 660 svchost.exe 0xca82b0fb1080 9 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k appmodel -p -s StateRepository C:\Windows\system32\svchost.exe
** 3356 660 svchost.exe 0xca82b3efa240 8 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s WpnService C:\Windows\system32\svchost.exe
** 7968 660 svchost.exe 0xca82b8ba72c0 4 - 0 False 2024-02-01 19:50:05.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc C:\Windows\System32\svchost.exe
** 808 660 svchost.exe 0xca82b299a240 15 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch -p C:\Windows\system32\svchost.exe
*** 4492 808 WmiPrvSE.exe 0xca82b7424280 13 - 0 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\wbem\WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe C:\Windows\system32\wbem\wmiprvse.exe
*** 7948 808 RuntimeBroker. 0xca82b87e5200 3 - 1 False 2024-02-01 19:49:08.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 8848 808 RuntimeBroker. 0xca82b8bd5080 1 - 1 False 2024-02-01 19:49:36.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 5912 808 WWAHost.exe 0xca82b8b86080 34 - 1 False 2024-02-01 19:49:19.000000 N/A \Device\HarddiskVolume3\Windows\System32\WWAHost.exe "C:\Windows\system32\wwahost.exe" -ServerName:Microsoft.MicrosoftOfficeHub.wwa C:\Windows\system32\wwahost.exe
*** 8728 808 WinStore.App.e 0xca82b7df4080 11 - 1 False 2024-02-01 19:49:34.000000 N/A \Device\HarddiskVolume3\Program Files\WindowsApps\Microsoft.WindowsStore_11910.1002.5.0_x64__8wekyb3d8bbwe\WinStore.App.exe "C:\Program Files\WindowsApps\Microsoft.WindowsStore_11910.1002.5.0_x64__8wekyb3d8bbwe\WinStore.App.exe" -ServerName:App.AppXc75wvwned5vhz4xyxxecvgdjhdkgsdza.mca C:\Program Files\WindowsApps\Microsoft.WindowsStore_11910.1002.5.0_x64__8wekyb3d8bbwe\WinStore.App.exe
*** 7068 808 RuntimeBroker. 0xca82b81d42c0 7 - 1 False 2024-02-01 19:48:31.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 5676 808 StartMenuExper 0xca82b78c4080 12 - 1 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe "C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe
*** 2220 808 RuntimeBroker. 0xca82b896d340 6 - 1 False 2024-02-01 19:52:27.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 2608 808 ShellExperienc 0xca82b880b340 18 - 1 False 2024-02-01 19:52:26.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe "C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe
*** 6964 808 LockApp.exe 0xca82b7dca080 12 - 1 False 2024-02-01 19:48:31.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\Microsoft.LockApp_cw5n1h2txyewy\LockApp.exe "C:\Windows\SystemApps\Microsoft.LockApp_cw5n1h2txyewy\LockApp.exe" -ServerName:WindowsDefaultLockScreen.AppX7y4nbzq37zn4ks9k7amqjywdat7d3j2z.mca C:\Windows\SystemApps\Microsoft.LockApp_cw5n1h2txyewy\LockApp.exe
*** 4792 808 SkypeApp.exe 0xca82b88020c0 13 - 1 False 2024-02-01 19:49:06.000000 N/A \Device\HarddiskVolume3\Program Files\WindowsApps\Microsoft.SkypeApp_14.53.77.0_x64__kzf8qxf38zg5c\SkypeApp.exe "C:\Program Files\WindowsApps\Microsoft.SkypeApp_14.53.77.0_x64__kzf8qxf38zg5c\SkypeApp.exe" -ServerName:App.AppXffn3yxqvgawq9fpmnhy90fr3y01d1t5b.mca C:\Program Files\WindowsApps\Microsoft.SkypeApp_14.53.77.0_x64__kzf8qxf38zg5c\SkypeApp.exe
*** 7484 808 smartscreen.ex 0xca82b82d0340 17 - 1 False 2024-02-01 19:48:41.000000 N/A \Device\HarddiskVolume3\Windows\System32\smartscreen.exe C:\Windows\System32\smartscreen.exe -Embedding C:\Windows\System32\smartscreen.exe
*** 5948 808 RuntimeBroker. 0xca82b7a9b080 7 - 1 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 6216 808 RuntimeBroker. 0xca82b7b14240 15 - 1 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 6984 808 WmiPrvSE.exe 0xca82b8046080 7 - 0 False 2024-02-01 19:48:46.000000 N/A \Device\HarddiskVolume3\Windows\System32\wbem\WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe C:\Windows\system32\wbem\wmiprvse.exe
*** 7112 808 ApplicationFra 0xca82b8ba2080 3 - 1 False 2024-02-01 19:49:19.000000 N/A \Device\HarddiskVolume3\Windows\System32\ApplicationFrameHost.exe C:\Windows\system32\ApplicationFrameHost.exe -Embedding C:\Windows\system32\ApplicationFrameHost.exe
*** 2128 808 SearchApp.exe 0xca82b7b10080 35 - 1 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe "C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe
*** 8420 808 dllhost.exe 0xca82b8e7b300 6 - 1 False 2024-02-01 19:49:21.000000 N/A \Device\HarddiskVolume3\Windows\System32\dllhost.exe C:\Windows\system32\DllHost.exe /Processid:{973D20D7-562D-44B9-B70B-5A0F49CCDF3F} C:\Windows\system32\DllHost.exe
*** 2928 808 RuntimeBroker. 0xca82b82d80c0 6 - 1 False 2024-02-01 19:48:32.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 5624 808 RuntimeBroker. 0xca82b8b182c0 1 - 1 False 2024-02-01 19:49:19.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
** 5932 660 svchost.exe 0xca82b7b0a0c0 10 - 0 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s UsoSvc C:\Windows\system32\svchost.exe
** 2864 660 svchost.exe 0xca82b3d432c0 6 - 1 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k UnistackSvcGroup -s WpnUserService C:\Windows\system32\svchost.exe
** 1844 660 svchost.exe 0xca82b39bb240 3 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s SENS C:\Windows\system32\svchost.exe
** 2872 660 svchost.exe 0xca82b3e68240 7 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s TokenBroker C:\Windows\system32\svchost.exe
** 2876 660 svchost.exe 0xca82b3d55240 22 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s Winmgmt C:\Windows\system32\svchost.exe
*** 2964 2876 WMIADAP.exe 0xca82b8b0f340 4 - 0 False 2024-02-01 19:52:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\wbem\WMIADAP.exe wmiadap.exe /F /T /R \\?\C:\Windows\system32\wbem\WMIADAP.EXE
** 4416 660 svchost.exe 0xca82b7406240 34 - 0 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k wsappx -p -s AppXSvc C:\Windows\system32\svchost.exe
** 2384 660 svchost.exe 0xca82b0f69080 4 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k netsvcs -p -s ShellHWDetection C:\Windows\System32\svchost.exe
** 3420 660 svchost.exe 0xca82b3f8f2c0 4 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalService -p -s WdiServiceHost C:\Windows\System32\svchost.exe
** 2912 660 svchost.exe 0xca82b3d8e240 5 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s IKEEXT C:\Windows\system32\svchost.exe
** 6500 660 svchost.exe 0xca82b84cc080 3 - 0 False 2024-02-01 19:48:49.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s Appinfo C:\Windows\system32\svchost.exe
** 1384 660 svchost.exe 0xca82b38042c0 4 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s nsi C:\Windows\system32\svchost.exe
** 2920 660 svchost.exe 0xca82b3d90300 5 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k NetworkServiceNetworkRestricted -p -s PolicyAgent C:\Windows\system32\svchost.exe
** 6504 660 svchost.exe 0xca82b7b16240 4 - 0 False 2024-02-01 19:48:30.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k appmodel -p -s camsvc C:\Windows\system32\svchost.exe
** 1916 660 svchost.exe 0xca82b3a30280 4 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s AudioEndpointBuilder C:\Windows\System32\svchost.exe
** 7040 660 SgrmBroker.exe 0xca82b8f85340 8 - 0 False 2024-02-01 19:50:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\SgrmBroker.exe C:\Windows\system32\SgrmBroker.exe C:\Windows\system32\SgrmBroker.exe
** 1420 660 svchost.exe 0xca82b3817240 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p -s UserManager C:\Windows\system32\svchost.exe
*** 2760 1420 sihost.exe 0xca82b3d1a280 11 - 1 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\sihost.exe sihost.exe C:\Windows\system32\sihost.exe
** 1932 660 svchost.exe 0xca82b3a322c0 7 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s FontCache C:\Windows\system32\svchost.exe
** 1944 660 svchost.exe 0xca82b3a362c0 8 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalService -p -s netprofm C:\Windows\System32\svchost.exe
** 2972 660 svchost.exe 0xca82b3dae300 7 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k NetworkService -p -s CryptSvc C:\Windows\system32\svchost.exe
** 7580 660 SecurityHealth 0xca82b8586240 14 - 0 False 2024-02-01 19:48:41.000000 N/A \Device\HarddiskVolume3\Windows\System32\SecurityHealthService.exe C:\Windows\system32\SecurityHealthService.exe C:\Windows\system32\SecurityHealthService.exe
** 928 660 svchost.exe 0xca82b29be2c0 7 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k RPCSS -p C:\Windows\system32\svchost.exe
** 1452 660 svchost.exe 0xca82b3855300 6 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s Dhcp C:\Windows\system32\svchost.exe
** 2988 660 svchost.exe 0xca82b3dd8240 11 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k utcsvc -p C:\Windows\System32\svchost.exe
** 2484 660 svchost.exe 0xca82b3b382c0 17 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetworkFirewall -p C:\Windows\system32\svchost.exe
** 2996 660 svchost.exe 0xca82b3dda2c0 15 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNoNetwork -p -s DPS C:\Windows\System32\svchost.exe
** 6080 660 svchost.exe 0xca82b742b340 0 - 0 False 2024-02-01 19:51:24.000000 2024-02-01 19:51:30.000000 \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 2500 660 svchost.exe 0xca82b3be80c0 12 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p -s DoSvc C:\Windows\System32\svchost.exe
** 2004 660 svchost.exe 0xca82b3b2c300 3 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s WinHttpAutoProxySvc C:\Windows\system32\svchost.exe
** 984 660 svchost.exe 0xca82b3038240 5 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch -p -s LSM C:\Windows\system32\svchost.exe
** 5592 660 svchost.exe 0xca82b81ef2c0 4 - 0 False 2024-02-01 19:48:31.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p -s BthAvctpSvc C:\Windows\system32\svchost.exe
** 3040 660 svchost.exe 0xca82b3df5080 6 - 0 False 2024-02-01 19:48:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetSvcs -p -s iphlpsvc C:\Windows\System32\svchost.exe
** 2544 660 svchost.exe 0xca82b8e84340 9 - 0 False 2024-02-01 19:50:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s wscsvc C:\Windows\System32\svchost.exe
* 844 524 fontdrvhost.ex 0xca82b299d080 6 - 0 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\fontdrvhost.exe "fontdrvhost.exe" C:\Windows\system32\fontdrvhost.exe
532 516 csrss.exe 0xca82b287f140 13 - 1 False 2024-02-01 19:48:23.000000 N/A \Device\HarddiskVolume3\Windows\System32\csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 C:\Windows\system32\csrss.exe
624 516 winlogon.exe 0xca82b28cb080 4 - 1 False 2024-02-01 19:48:23.000000 N/A \Device\HarddiskVolume3\Windows\System32\winlogon.exe winlogon.exe C:\Windows\system32\winlogon.exe
* 364 624 LogonUI.exe 0xca82b30a2080 0 - 1 False 2024-02-01 19:48:24.000000 2024-02-01 19:48:37.000000 \Device\HarddiskVolume3\Windows\System32\LogonUI.exe - -
* 372 624 dwm.exe 0xca82b30a3080 14 - 1 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\dwm.exe "dwm.exe" C:\Windows\system32\dwm.exe
* 4508 624 userinit.exe 0xca82b7426340 0 - 1 False 2024-02-01 19:48:26.000000 2024-02-01 19:48:52.000000 \Device\HarddiskVolume3\Windows\System32\userinit.exe - -
** 4568 4508 explorer.exe 0xca82b7440340 55 - 1 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\explorer.exe C:\Windows\Explorer.EXE C:\Windows\Explorer.EXE
*** 7780 4568 OneDrive.exe 0xca82b814a0c0 21 - 1 True 2024-02-01 19:48:42.000000 N/A \Device\HarddiskVolume3\Users\alex\AppData\Local\Microsoft\OneDrive\OneDrive.exe "C:\Users\alex\AppData\Local\Microsoft\OneDrive\OneDrive.exe" /background C:\Users\alex\AppData\Local\Microsoft\OneDrive\OneDrive.exe
*** 7540 4568 SecurityHealth 0xca82b7858080 3 - 1 False 2024-02-01 19:48:41.000000 N/A \Device\HarddiskVolume3\Windows\System32\SecurityHealthSystray.exe "C:\Windows\System32\SecurityHealthSystray.exe" C:\Windows\System32\SecurityHealthSystray.exe
*** 7684 4568 vmtoolsd.exe 0xca82b7dbe080 8 - 1 False 2024-02-01 19:48:41.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\vmtoolsd.exe "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
*** 4628 4568 ChromeSetup.ex 0xca82b830a300 4 - 1 True 2024-02-01 19:48:50.000000 N/A \Device\HarddiskVolume3\Users\alex\Downloads\ChromeSetup.exe "C:\Users\alex\Downloads\ChromeSetup.exe" C:\Users\alex\Downloads\ChromeSetup.exe
* 836 624 fontdrvhost.ex 0xca82b299c140 6 - 1 False 2024-02-01 19:48:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\fontdrvhost.exe "fontdrvhost.exe" C:\Windows\system32\fontdrvhost.exeEl resultado reveló varios procesos de interés:
** 4568 4508 explorer.exe 0xca82b7440340 55 - 1 False 2024-02-01 19:48:26.000000 N/A \Device\HarddiskVolume3\Windows\explorer.exe C:\Windows\Explorer.EXE C:\Windows\Explorer.EXE
*** 7780 4568 OneDrive.exe 0xca82b814a0c0 21 - 1 True 2024-02-01 19:48:42.000000 N/A \Device\HarddiskVolume3\Users\alex\AppData\Local\Microsoft\OneDrive\OneDrive.exe "C:\Users\alex\AppData\Local\Microsoft\OneDrive\OneDrive.exe" /background C:\Users\alex\AppData\Local\Microsoft\OneDrive\OneDrive.exe
*** 7540 4568 SecurityHealth 0xca82b7858080 3 - 1 False 2024-02-01 19:48:41.000000 N/A \Device\HarddiskVolume3\Windows\System32\SecurityHealthSystray.exe "C:\Windows\System32\SecurityHealthSystray.exe" C:\Windows\System32\SecurityHealthSystray.exe
*** 7684 4568 vmtoolsd.exe 0xca82b7dbe080 8 - 1 False 2024-02-01 19:48:41.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\vmtoolsd.exe "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
*** 4628 4568 ChromeSetup.ex 0xca82b830a300 4 - 1 True 2024-02-01 19:48:50.000000 N/A \Device\HarddiskVolume3\Users\alex\Downloads\ChromeSetup.exe "C:\Users\alex\Downloads\ChromeSetup.exe" C:\Users\alex\Downloads\ChromeSetup.exe
Para explorar posibles conexiones entre estos procesos, ejecutamos windows.netstat:
vol -f memory.dmp windows.netstat
Output:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
Offset Proto LocalAddr LocalPort ForeignAddr ForeignPort State PID Owner Created
0xca82b7deeb20 TCPv4 192.168.19.133 49763 2.18.162.9 443 ESTABLISHED 2500 svchost.exe 2024-02-01 19:52:57.000000
0xca82b7abdaf0 TCPv4 192.168.19.133 49739 40.115.3.253 443 ESTABLISHED 3356 svchost.exe 2024-02-01 19:51:25.000000
0xca82b87e8a20 TCPv4 192.168.19.133 49697 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b8bd7a20 TCPv4 192.168.19.133 49695 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b7861a20 TCPv4 192.168.19.133 49761 2.16.149.135 80 ESTABLISHED 2500 svchost.exe 2024-02-01 19:52:57.000000
0xca82b87f3010 TCPv4 192.168.19.133 49691 192.229.221.95 80 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b8005a20 TCPv4 192.168.19.133 49693 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b3fc74d0 TCPv4 192.168.19.133 49759 2.18.162.9 443 ESTABLISHED 2500 svchost.exe 2024-02-01 19:52:56.000000
0xca82b8ba9a20 TCPv4 192.168.19.133 49699 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b8b98a20 TCPv4 192.168.19.133 49760 2.18.162.9 443 ESTABLISHED 2500 svchost.exe 2024-02-01 19:52:57.000000
0xca82b7f1fa20 TCPv4 192.168.19.133 49692 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b8564050 TCPv4 192.168.19.133 49755 20.199.120.85 443 ESTABLISHED 3356 svchost.exe 2024-02-01 19:52:25.000000
0xca82b38b0730 TCPv4 192.168.19.133 49765 52.179.219.14 443 ESTABLISHED 2500 svchost.exe 2024-02-01 19:52:58.000000
0xca82b78cba20 TCPv4 192.168.19.133 49694 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b7e5a700 TCPv4 192.168.19.133 49700 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b8bc2b30 TCPv4 192.168.19.133 49682 58.64.204.181 5202 SYN_SENT 4628 ChromeSetup.ex 2024-02-01 19:48:51.000000
0xca82b8baea20 TCPv4 192.168.19.133 49696 95.100.200.202 443 CLOSE_WAIT 5912 WWAHost.exe 2024-02-01 19:49:20.000000
0xca82b1c2ed30 TCPv4 0.0.0.0 135 0.0.0.0 0 LISTENING 928 svchost.exe 2024-02-01 19:48:24.000000
0xca82b1c2ed30 TCPv6 :: 135 :: 0 LISTENING 928 svchost.exe 2024-02-01 19:48:24.000000
0xca82b1c2e0d0 TCPv4 0.0.0.0 135 0.0.0.0 0 LISTENING 928 svchost.exe 2024-02-01 19:48:24.000000
0xca82b3fe2a70 TCPv4 192.168.19.133 139 0.0.0.0 0 LISTENING 4 System 2024-02-01 19:48:26.000000
0xca82b0eadb50 TCPv4 0.0.0.0 445 0.0.0.0 0 LISTENING 4 System 2024-02-01 19:48:25.000000
0xca82b0eadb50 TCPv6 :: 445 :: 0 LISTENING 4 System 2024-02-01 19:48:25.000000
0xca82b3fe19f0 TCPv4 0.0.0.0 5040 0.0.0.0 0 LISTENING 3104 svchost.exe 2024-02-01 19:48:31.000000
0xca82b0ead9f0 TCPv4 0.0.0.0 7680 0.0.0.0 0 LISTENING 2500 svchost.exe 2024-02-01 19:48:25.000000
0xca82b0ead9f0 TCPv6 :: 7680 :: 0 LISTENING 2500 svchost.exe 2024-02-01 19:48:25.000000
0xca82b1c2ebd0 TCPv4 0.0.0.0 49664 0.0.0.0 0 LISTENING 676 lsass.exe 2024-02-01 19:48:24.000000
0xca82b1c2ebd0 TCPv6 :: 49664 :: 0 LISTENING 676 lsass.exe 2024-02-01 19:48:24.000000
0xca82b1c2e910 TCPv4 0.0.0.0 49664 0.0.0.0 0 LISTENING 676 lsass.exe 2024-02-01 19:48:24.000000
0xca82b1c2ee90 TCPv4 0.0.0.0 49665 0.0.0.0 0 LISTENING 524 wininit.exe 2024-02-01 19:48:24.000000
0xca82b1c2ee90 TCPv6 :: 49665 :: 0 LISTENING 524 wininit.exe 2024-02-01 19:48:24.000000
0xca82b1c2d470 TCPv4 0.0.0.0 49665 0.0.0.0 0 LISTENING 524 wininit.exe 2024-02-01 19:48:24.000000
0xca82b1c2e230 TCPv4 0.0.0.0 49666 0.0.0.0 0 LISTENING 1136 svchost.exe 2024-02-01 19:48:24.000000
0xca82b1c2e230 TCPv6 :: 49666 :: 0 LISTENING 1136 svchost.exe 2024-02-01 19:48:24.000000
0xca82b1c2d5d0 TCPv4 0.0.0.0 49666 0.0.0.0 0 LISTENING 1136 svchost.exe 2024-02-01 19:48:24.000000
0xca82b37e9a70 TCPv4 0.0.0.0 49667 0.0.0.0 0 LISTENING 1144 svchost.exe 2024-02-01 19:48:24.000000
0xca82b37e9a70 TCPv6 :: 49667 :: 0 LISTENING 1144 svchost.exe 2024-02-01 19:48:24.000000
0xca82b1c2e7b0 TCPv4 0.0.0.0 49667 0.0.0.0 0 LISTENING 1144 svchost.exe 2024-02-01 19:48:24.000000
0xca82b0eadcb0 TCPv4 0.0.0.0 49668 0.0.0.0 0 LISTENING 2564 spoolsv.exe 2024-02-01 19:48:25.000000
0xca82b0eadcb0 TCPv6 :: 49668 :: 0 LISTENING 2564 spoolsv.exe 2024-02-01 19:48:25.000000
0xca82b0ead5d0 TCPv4 0.0.0.0 49668 0.0.0.0 0 LISTENING 2564 spoolsv.exe 2024-02-01 19:48:25.000000
0xca82b3fe11b0 TCPv4 0.0.0.0 49669 0.0.0.0 0 LISTENING 660 services.exe 2024-02-01 19:48:25.000000
0xca82b3fe11b0 TCPv6 :: 49669 :: 0 LISTENING 660 services.exe 2024-02-01 19:48:25.000000
0xca82b3fe2390 TCPv4 0.0.0.0 49669 0.0.0.0 0 LISTENING 660 services.exe 2024-02-01 19:48:25.000000
0xca82b711f470 TCPv4 0.0.0.0 49670 0.0.0.0 0 LISTENING 2920 svchost.exe 2024-02-01 19:48:26.000000
0xca82b711f470 TCPv6 :: 49670 :: 0 LISTENING 2920 svchost.exe 2024-02-01 19:48:26.000000
0xca82b711f050 TCPv4 0.0.0.0 49670 0.0.0.0 0 LISTENING 2920 svchost.exe 2024-02-01 19:48:26.000000
0xca82b748db00 UDPv4 192.168.19.133 137 * 0 4 System 2024-02-01 19:48:26.000000
0xca82b748d650 UDPv4 192.168.19.133 138 * 0 4 System 2024-02-01 19:48:26.000000
0xca82b3d5f6f0 UDPv4 0.0.0.0 500 * 0 2912 svchost.exe 2024-02-01 19:48:25.000000
0xca82b3d5f6f0 UDPv6 :: 500 * 0 2912 svchost.exe 2024-02-01 19:48:25.000000
0xca82b3d5e750 UDPv4 0.0.0.0 500 * 0 2912 svchost.exe 2024-02-01 19:48:25.000000
0xca82b3d5fba0 UDPv4 0.0.0.0 4500 * 0 2912 svchost.exe 2024-02-01 19:48:25.000000
0xca82b3d5fba0 UDPv6 :: 4500 * 0 2912 svchost.exe 2024-02-01 19:48:25.000000
0xca82b3d5f560 UDPv4 0.0.0.0 4500 * 0 2912 svchost.exe 2024-02-01 19:48:25.000000
0xca82b748e460 UDPv4 0.0.0.0 5353 * 0 2244 svchost.exe 2024-02-01 19:48:26.000000
0xca82b748e460 UDPv6 :: 5353 * 0 2244 svchost.exe 2024-02-01 19:48:26.000000
0xca82b748e780 UDPv4 0.0.0.0 5353 * 0 2244 svchost.exe 2024-02-01 19:48:26.000000
0xca82b7492150 UDPv4 0.0.0.0 5355 * 0 2244 svchost.exe 2024-02-01 19:48:26.000000
0xca82b7492150 UDPv6 :: 5355 * 0 2244 svchost.exe 2024-02-01 19:48:26.000000
0xca82b748fd60 UDPv4 0.0.0.0 5355 * 0 2244 svchost.exe 2024-02-01 19:48:26.000000
0xca82b3f676a0 UDPv4 127.0.0.1 60166 * 0 3040 svchost.exe 2024-02-01 19:48:25.000000Descubrimos una conexión relevante:
"0xca82b8bc2b30 TCPv4 192.168.19.133 49682 58.64.204.181 5202 SYN_SENT 4628 ChromeSetup.ex 2024-02-01 19:48:51.000000"
Para profundizar, realizamos un volcado del archivo asociado al PID 4628:
vol -f memory.dmp windows.dumpfile --pid 4628Output:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
ImageSectionObject 0xca82b8202cd0 winmm.dll file.0xca82b8202cd0.0xca82b79ab4b0.ImageSectionObject.winmm.dll.img
DataSectionObject 0xca82b85325a0 ChromeSetup.exe Error dumping file
ImageSectionObject 0xca82b85325a0 ChromeSetup.exe file.0xca82b85325a0.0xca82b7e06c80.ImageSectionObject.ChromeSetup.exe.img
ImageSectionObject 0xca82b8215100 AcLayers.dll file.0xca82b8215100.0xca82b7ae1d60.ImageSectionObject.AcLayers.dll.img
ImageSectionObject 0xca82b8218300 sfc.dll file.0xca82b8218300.0xca82b8490050.ImageSectionObject.sfc.dll.img
ImageSectionObject 0xca82b821c950 winrnr.dll file.0xca82b821c950.0xca82b7de9c80.ImageSectionObject.winrnr.dll.img
ImageSectionObject 0xca82b8217810 msacm32.dll file.0xca82b8217810.0xca82b7dd6c80.ImageSectionObject.msacm32.dll.img
ImageSectionObject 0xca82b8536420 wsock32.dll file.0xca82b8536420.0xca82b7a69db0.ImageSectionObject.wsock32.dll.img
ImageSectionObject 0xca82b8218490 pnrpnsp.dll file.0xca82b8218490.0xca82b7e31ca0.ImageSectionObject.pnrpnsp.dll.img
ImageSectionObject 0xca82b82198e0 wshbth.dll file.0xca82b82198e0.0xca82b7bfac20.ImageSectionObject.wshbth.dll.img
ImageSectionObject 0xca82b821d8f0 nlaapi.dll file.0xca82b821d8f0.0xca82b7abbcc0.ImageSectionObject.nlaapi.dll.img
ImageSectionObject 0xca82b8539df0 NapiNSP.dll file.0xca82b8539df0.0xca82b7e4fc80.ImageSectionObject.NapiNSP.dll.img
ImageSectionObject 0xca82b8217cc0 winmmbase.dll file.0xca82b8217cc0.0xca82b7ae1b00.ImageSectionObject.winmmbase.dll.img
ImageSectionObject 0xca82b82187b0 sfc_os.dll file.0xca82b82187b0.0xca82b78b6a20.ImageSectionObject.sfc_os.dll.img
ImageSectionObject 0xca82b82179a0 winspool.drv file.0xca82b82179a0.0xca82b7e4cc80.ImageSectionObject.winspool.drv.img
ImageSectionObject 0xca82b8525a80 mswsock.dll file.0xca82b8525a80.0xca82b7640cc0.ImageSectionObject.mswsock.dll.img
ImageSectionObject 0xca82b8527380 apphelp.dll file.0xca82b8527380.0xca82b7105dc0.ImageSectionObject.apphelp.dll.img
ImageSectionObject 0xca82b82174f0 AcGenral.dll file.0xca82b82174f0.0xca82b7a8cb80.ImageSectionObject.AcGenral.dll.img
ImageSectionObject 0xca82b8523370 FWPUCLNT.DLL file.0xca82b8523370.0xca82b858ac80.ImageSectionObject.FWPUCLNT.DLL.img
ImageSectionObject 0xca82b8523820 rasadhlp.dll file.0xca82b8523820.0xca82b78cca20.ImageSectionObject.rasadhlp.dll.img
ImageSectionObject 0xca82b820b1a0 samcli.dll file.0xca82b820b1a0.0xca82b1c14c80.ImageSectionObject.samcli.dll.img
ImageSectionObject 0xca82b82021e0 dnsapi.dll file.0xca82b82021e0.0xca82b79ab750.ImageSectionObject.dnsapi.dll.img
ImageSectionObject 0xca82b1b70700 sechost.dll file.0xca82b1b70700.0xca82b1ba12b0.ImageSectionObject.sechost.dll.img
DataSectionObject 0xca82b81330b0 uxtheme.dll file.0xca82b81330b0.0xca82b84a4eb0.DataSectionObject.uxtheme.dll.dat
ImageSectionObject 0xca82b81330b0 uxtheme.dll file.0xca82b81330b0.0xca82b78e0c80.ImageSectionObject.uxtheme.dll.img
ImageSectionObject 0xca82b82050c0 srvcli.dll file.0xca82b82050c0.0xca82b78f1a20.ImageSectionObject.srvcli.dll.img
ImageSectionObject 0xca82b8203180 mpr.dll file.0xca82b8203180.0xca82b78f0c80.ImageSectionObject.mpr.dll.img
ImageSectionObject 0xca82b296a410 netutils.dll file.0xca82b296a410.0xca82b73a8b80.ImageSectionObject.netutils.dll.img
ImageSectionObject 0xca82b7c7b660 urlmon.dll file.0xca82b7c7b660.0xca82b7e4dc80.ImageSectionObject.urlmon.dll.img
ImageSectionObject 0xca82b8204a80 iertutil.dll file.0xca82b8204a80.0xca82b37c68a0.ImageSectionObject.iertutil.dll.img
ImageSectionObject 0xca82b3f72610 comctl32.dll file.0xca82b3f72610.0xca82b8056c80.ImageSectionObject.comctl32.dll.img
ImageSectionObject 0xca82b8139960 dwmapi.dll file.0xca82b8139960.0xca82b75f2c80.ImageSectionObject.dwmapi.dll.img
ImageSectionObject 0xca82b81362b0 IPHLPAPI.DLL file.0xca82b81362b0.0xca82b8052a20.ImageSectionObject.IPHLPAPI.DLL.img
ImageSectionObject 0xca82b1bb9700 win32u.dll file.0xca82b1bb9700.0xca82b1ba9820.ImageSectionObject.win32u.dll.img
ImageSectionObject 0xca82b7254090 version.dll file.0xca82b7254090.0xca82b73a8db0.ImageSectionObject.version.dll.img
ImageSectionObject 0xca82b772bdf0 sspicli.dll file.0xca82b772bdf0.0xca82b7663a20.ImageSectionObject.sspicli.dll.img
ImageSectionObject 0xca82b7726800 kernel.appcore.dll file.0xca82b7726800.0xca82b763dc80.ImageSectionObject.kernel.appcore.dll.img
ImageSectionObject 0xca82b8131620 userenv.dll file.0xca82b8131620.0xca82b78dfa20.ImageSectionObject.userenv.dll.img
ImageSectionObject 0xca82b1bba380 gdi32.dll file.0xca82b1bba380.0xca82b1ba9a50.ImageSectionObject.gdi32.dll.img
ImageSectionObject 0xca82b1bb9ed0 msctf.dll file.0xca82b1bb9ed0.0xca82b1baa390.ImageSectionObject.msctf.dll.img
ImageSectionObject 0xca82b1bb9890 ole32.dll file.0xca82b1bb9890.0xca82b1ba2010.ImageSectionObject.ole32.dll.img
ImageSectionObject 0xca82b1bbace0 ws2_32.dll file.0xca82b1bbace0.0xca82b1ba29a0.ImageSectionObject.ws2_32.dll.img
ImageSectionObject 0xca82b1b70890 msvcrt.dll file.0xca82b1b70890.0xca82b1ba1510.ImageSectionObject.msvcrt.dll.img
ImageSectionObject 0xca82b1bbab50 bcryptprimitives.dll file.0xca82b1bbab50.0xca82b1ba1970.ImageSectionObject.bcryptprimitives.dll.img
ImageSectionObject 0xca82b19355e0 ntdll.dll file.0xca82b19355e0.0xca82b193f050.ImageSectionObject.ntdll.dll.img
ImageSectionObject 0xca82b1b703e0 KernelBase.dll file.0xca82b1b703e0.0xca82b1b5ec20.ImageSectionObject.KernelBase.dll.img
ImageSectionObject 0xca82b1b711f0 rpcrt4.dll file.0xca82b1b711f0.0xca82b1b9f4e0.ImageSectionObject.rpcrt4.dll.img
ImageSectionObject 0xca82b1b700c0 gdi32full.dll file.0xca82b1b700c0.0xca82b1ba1050.ImageSectionObject.gdi32full.dll.img
ImageSectionObject 0xca82b1b70250 SHCore.dll file.0xca82b1b70250.0xca82b1b9f970.ImageSectionObject.SHCore.dll.img
ImageSectionObject 0xca82b1b719c0 ucrtbase.dll file.0xca82b1b719c0.0xca82b1b9f050.ImageSectionObject.ucrtbase.dll.img
ImageSectionObject 0xca82b1b71510 shlwapi.dll file.0xca82b1b71510.0xca82b1b9f280.ImageSectionObject.shlwapi.dll.img
ImageSectionObject 0xca82b1b716a0 advapi32.dll file.0xca82b1b716a0.0xca82b1b5f740.ImageSectionObject.advapi32.dll.img
ImageSectionObject 0xca82b1b71380 imm32.dll file.0xca82b1b71380.0xca82b1b5fc00.ImageSectionObject.imm32.dll.img
ImageSectionObject 0xca82b1b38bb0 kernel32.dll file.0xca82b1b38bb0.0xca82b1b54cd0.ImageSectionObject.kernel32.dll.img
ImageSectionObject 0xca82b1b39ce0 msvcp_win.dll file.0xca82b1b39ce0.0xca82b1b5a930.ImageSectionObject.msvcp_win.dll.img
ImageSectionObject 0xca82b1b70bb0 oleaut32.dll file.0xca82b1b70bb0.0xca82b1b5c470.ImageSectionObject.oleaut32.dll.img
ImageSectionObject 0xca82b1b70ed0 setupapi.dll file.0xca82b1b70ed0.0xca82b1b5e9c0.ImageSectionObject.setupapi.dll.img
ImageSectionObject 0xca82b1b38d40 shell32.dll file.0xca82b1b38d40.0xca82b1b57ac0.ImageSectionObject.shell32.dll.img
ImageSectionObject 0xca82b1b39380 comdlg32.dll file.0xca82b1b39380.0xca82b1b59cf0.ImageSectionObject.comdlg32.dll.img
ImageSectionObject 0xca82b1b38570 cfgmgr32.dll file.0xca82b1b38570.0xca82b1b2d010.ImageSectionObject.cfgmgr32.dll.img
ImageSectionObject 0xca82b1b391f0 user32.dll file.0xca82b1b391f0.0xca82b1b2d270.ImageSectionObject.user32.dll.img
ImageSectionObject 0xca82b1b38700 combase.dll file.0xca82b1b38700.0xca82b1b2d8f0.ImageSectionObject.combase.dll.img
ImageSectionObject 0xca82b1b383e0 bcrypt.dll file.0xca82b1b383e0.0xca82b379a010.ImageSectionObject.bcrypt.dll.img
ImageSectionObject 0xca82b1b38a20 nsi.dll file.0xca82b1b38a20.0xca82b3799d00.ImageSectionObject.nsi.dll.img
ImageSectionObject 0xca82b1ace6a0 wow64cpu.dll file.0xca82b1ace6a0.0xca82b1b0a320.ImageSectionObject.wow64cpu.dll.img
ImageSectionObject 0xca82b1acdd40 wow64.dll file.0xca82b1acdd40.0xca82b1b0a5f0.ImageSectionObject.wow64.dll.img
ImageSectionObject 0xca82b1933ee0 ntdll.dll file.0xca82b1933ee0.0xca82b1922c70.ImageSectionObject.ntdll.dll.img
ImageSectionObject 0xca82b1aefbb0 wow64win.dll file.0xca82b1aefbb0.0xca82b1ab7d30.ImageSectionObject.wow64win.dll.img
Y obtuvimos el MD5 del proceso:
md5sum *ChromeSetup.exe*
11318cc3a3613fb679e25973a0a701fc file.0xca82b85325a0.0xca82b7e06c80.ImageSectionObject.ChromeSetup.exe.img
14f6b75515df5eee396d961e161148c5 file.0xca82b85325a0.0xca82b83c7770.DataSectionObject.ChromeSetup.exe.dat
Al verificar en VirusTotal, confirmamos que se trata de un troyano identificado como «virus.nimnul/vjadtre».
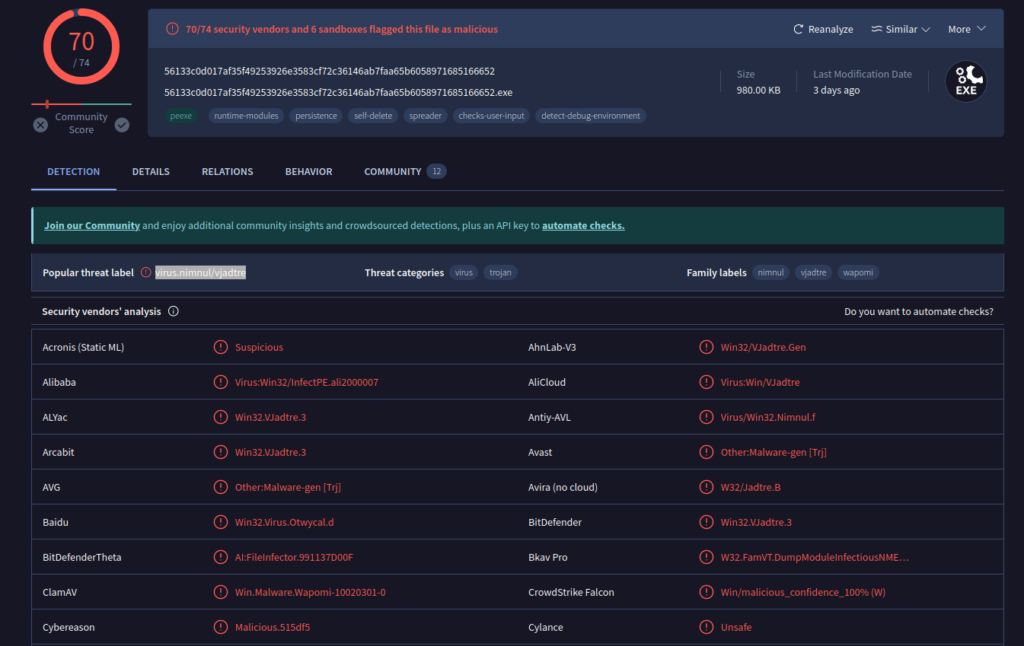
#2 Respuesta: C:\Users\alex\Downloads\ChromeSetup.exe
To eradicate the malware, what is the exact file path of the process executable?Obtención de la evidencia
En la pregunta anterior, identificamos la ubicación del archivo utilizando el comando «windows.pstree»:
vol -f memory.dmp windows.pstree | grep ChromeSetup.exe
*** 4628: 100.04568 ChromeSetup.exan0xca82b830a300 4 - 1 True 2024-02-01 19:48:50.000000 N/A \Device\HarddiskVolume3\Users\alex\Downloads\ChromeSetup.exe "C:\Users\alex\Downloads\ChromeSetup.exe" C:\Users\alex\Downloads\ChromeSetup.exe
La ruta del archivo ejecutable del proceso ChromeSetup.exe es:
C:\Users\alex\Downloads\ChromeSetup.exe
#3 Respuesta: 58.64.204.181
Identifying network connections is crucial for understanding the malware's communication strategy. What is the IP address it attempted to connect to?Obtención de la evidencia
En la pregunta #1, identificamos la dirección IP del atacante utilizando el comando windows.netstat.
vol -f memory.dmp windows.netstat | grep ChromeSetup.ex
0xca82b8bc2b30.0TCPv4 192.168.19.133an49682fin58.64.204.181 5202 SYN_SENT 4628 ChromeSetup.ex 2024-02-01 19:48:51.000000#4 Respuesta: Hong Kong
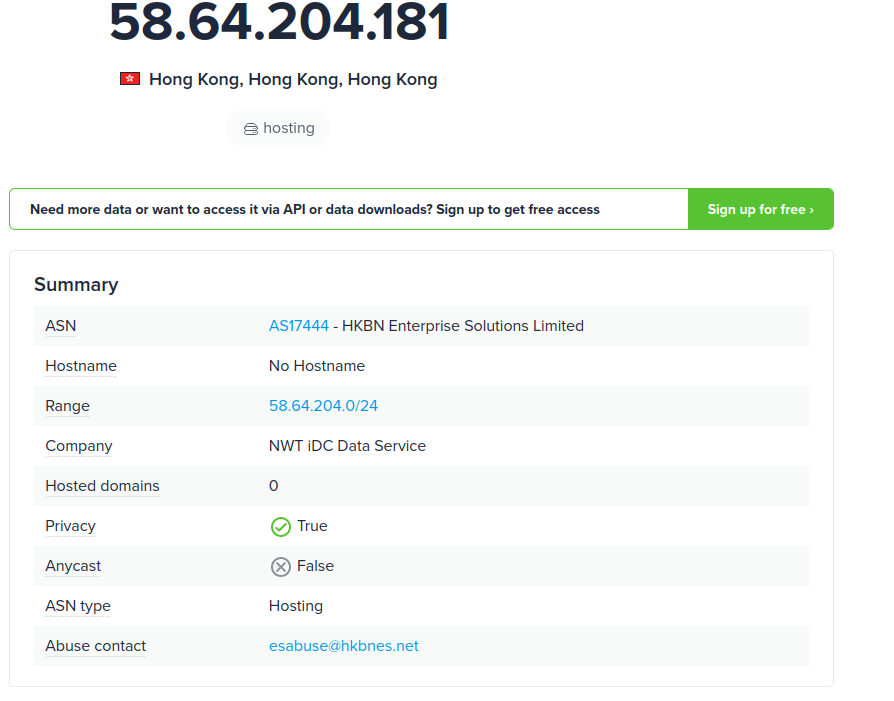
To pinpoint the geographical origin of the attack, which city is associated with the IP address the malware communicated with?Obtención de la evidencia
Para obtener la ubicación de la dirección IP, utilicé el servicio https://ipinfo.io/58.64.204.181:
curl https://ipinfo.io/58.64.204.181
{
"ip": "58.64.204.181",
"city": "Hong Kong",
"region": "Hong Kong",
"country": "HK",
"loc": "22.2783,114.1747",
"org": "AS17444 HKBN Enterprise Solutions Limited",
"timezone": "Asia/Hong_Kong",
"readme": "https://ipinfo.io/missingauth"
}
#5 Respuesta: 280c9d36039f9432433893dee6126d72b9112ad2
Hashes provide a unique identifier for files, aiding in detecting similar threats across machines. What is the SHA1 hash of the malware's executable?Obtención de la evidencia
En la pregunta #1 realizamos un volcado del proceso para un análisis detallado y confirmamos que se trataba del malware utilizando el comando «windows.dumpfile –pid 4628». A continuación, obtenemos el hash SHA1 del archivo:
sha1sum file.0xca82b85325a0.0xca82b7e06c80.ImageSectionObject.ChromeSetup.exe.img
280c9d36039f9432433893dee6126d72b9112ad2 file.0xca82b85325a0.0xca82b7e06c80.ImageSectionObject.ChromeSetup.exe.img
#6 Respuesta: 2019-12-01 08:36:04
Understanding the malware's development timeline can offer insights into its deployment. What is the compilation UTC timestamp of the malware?Obtención de la evidencia
Para obtener la timestamp de compilación en formato UTC del malware, utilizamos exiftool para extraer los metadatos del archivo:
exiftool file.0xca82b85325a0.0xca82b7e06c80.ImageSectionObject.ChromeSetup.exe.imgOutput:
ExifTool Version Number : 12.57
File Name : file.0xca82b85325a0.0xca82b7e06c80.ImageSectionObject.ChromeSetup.exe.img
Directory : .
File Size : 1004 kB
File Modification Date/Time : 2024:07:09 10:07:24+02:00
File Access Date/Time : 2024:07:09 10:08:36+02:00
File Inode Change Date/Time : 2024:07:09 10:07:24+02:00
File Permissions : -rw-------
File Type : Win32 EXE
File Type Extension : exe
MIME Type : application/octet-stream
Machine Type : Intel 386 or later, and compatibles
Time Stamp : 2019:12:01 09:36:04+01:00
Image File Characteristics : No relocs, Executable, No line numbers, No symbols, 32-bit
PE Type : PE32
Linker Version : 6.0
Code Size : 782336
Initialized Data Size : 372736
Uninitialized Data Size : 0
Entry Point : 0x116000
OS Version : 4.0
Image Version : 0.0
Subsystem Version : 4.0
Subsystem : Windows GUI
Para convertir el tiempo local a UTC, simplemente ajustamos la hora restando el desplazamiento horario. En este caso:
- La Time Stamp local es
2019-12-01 09:36:04+01:00. - El desplazamiento horario es
+01:00(Central European Time, CET).
Paso a paso para convertir a UTC:
- Identifica el desplazamiento horario: El
+01:00indica que la hora local está una hora adelantada con respecto a UTC. - Resta el desplazamiento horario: Para obtener el tiempo en UTC, resta una hora a la marca de tiempo local.Por lo tanto:
Tiempo UTC = Tiempo local - Desplazamiento horario
= 2019-12-01 09:36:04 +01:00 - 01:00
= 2019-12-01 08:36:04 UTC
Así, la marca de tiempo de compilación del malware en formato UTC es 2019-12-01 08:36:04.
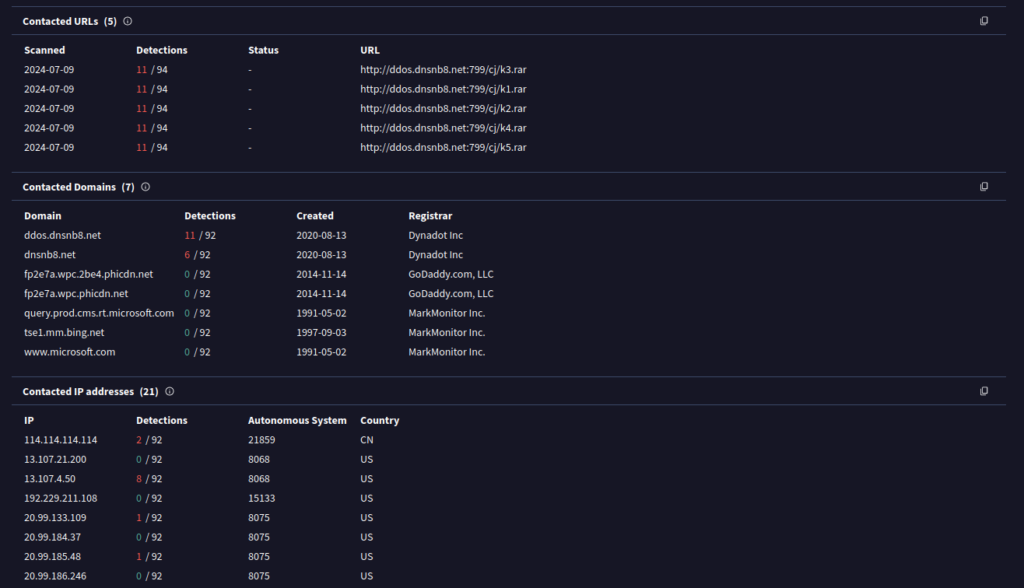
#7 Respuesta: dnsnb8.net
Identifying domains involved with this malware helps in blocking future malicious communications and identifying current possible communications with that domain in our network. Can you provide the domain related to the malware?Obtención de la evidencia
Buscando en VirusTotal los IOC, encontramos los siguientes dominios asociados a este malware.
:wq!