Scenario:
As a member of the Security Blue team, your assignment is to analyze a memory dump using Redline and Volatility tools. Your goal is to trace the steps taken by the attacker on the compromised machine and determine how they managed to bypass the Network Intrusion Detection System «NIDS». Your investigation will involve identifying the specific malware family employed in the attack, along with its characteristics. Additionally, your task is to identify and mitigate any traces or footprints left by the attacker.
Tools:
#1 Respuesta: oneetx.exe
What is the name of the suspicious process?Obtención de la evidencia
Utilizamos el siguiente comando para realizar el análisis inicial de la memoria:
vol -f MemoryDump.mem windows.malfind
El resultado muestra los procesos sospechosos:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
PID Process Start VPN End VPN Tag Protection CommitCharge PrivateMemory File output Notes Hexdump Disasm
5896 oneetx.exe 0x400000 0x437fff VadS PAGE_EXECUTE_READWRITE 56 1 Disabled MZ header
4d 5a 90 00 03 00 00 00 MZ......
04 00 00 00 ff ff 00 00 ........
b8 00 00 00 00 00 00 00 ........
40 00 00 00 00 00 00 00 @.......
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 00 00 00 ........
00 00 00 00 00 01 00 00 ........
0x400000: dec ebp
0x400001: pop edx
0x400002: nop
0x400003: add byte ptr [ebx], al
0x400005: add byte ptr [eax], al
0x400007: add byte ptr [eax + eax], al
0x40000a: add byte ptr [eax], al
7540 smartscreen.ex 0x2505c140000 0x2505c15ffff VadS PAGE_EXECUTE_READWRITE 1 1 Disabled N/A
48 89 54 24 10 48 89 4c H.T$.H.L
24 08 4c 89 44 24 18 4c $.L.D$.L
89 4c 24 20 48 8b 41 28 .L$.H.A(
48 8b 48 08 48 8b 51 50 H.H.H.QP
48 83 e2 f8 48 8b ca 48 H...H..H
b8 60 00 14 5c 50 02 00 .`..\P..
00 48 2b c8 48 81 f9 70 .H+.H..p
0f 00 00 76 09 48 c7 c1 ...v.H..
0x2505c140000: mov qword ptr [rsp + 0x10], rdx
0x2505c140005: mov qword ptr [rsp + 8], rcx
0x2505c14000a: mov qword ptr [rsp + 0x18], r8
0x2505c14000f: mov qword ptr [rsp + 0x20], r9
0x2505c140014: mov rax, qword ptr [rcx + 0x28]
0x2505c140018: mov rcx, qword ptr [rax + 8]
0x2505c14001c: mov rdx, qword ptr [rcx + 0x50]
0x2505c140020: and rdx, 0xfffffffffffffff8
0x2505c140024: mov rcx, rdx
0x2505c140027: movabs rax, 0x2505c140060
0x2505c140031: sub rcx, rax
0x2505c140034: cmp rcx, 0xf70
0x2505c14003b: jbe 0x2505c140046Identificación del Proceso Malicioso
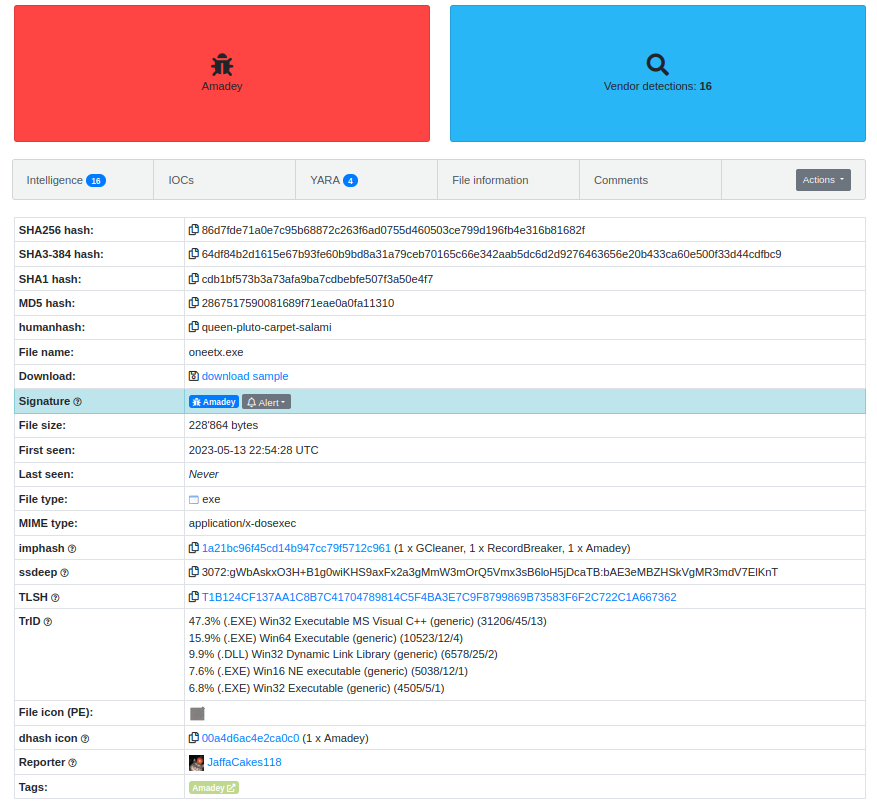
Al buscar en bazaar.abuse.ch, identificamos oneetx.exe como un archivo malicioso potencial.
Listado de Procesos
Para confirmar, listamos los procesos y sus detalles:
vol -f MemoryDump.mem windows.pslist | grep -E "5896|7540"
Output
5896ress884400.0oneetx.exe 0xad8189b41080in5shed - 1 True 2023-05-21 22:30:56.000000 N/A Disabled
7732 5896 rundll32.exe 0xad818d1912c0 1 - 1 True 2023-05-21 22:31:53.000000 N/A Disabled
7540 824 smartscreen.ex 0xad818e893080 14 - 1 False 2023-05-21 23:02:26.000000 N/A DisabledComando utilizado:
vol -f MemoryDump.mem windows.pslistRealización del Dump del Proceso
Procedimos a realizar un dump del proceso oneetx.exe para un análisis más detallado:
vol -f MemoryDump.mem windows.dumpfile --pid 5896
Output:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
ImageSectionObject 0xad818e37b8e0 AcLayers.dll file.0xad818e37b8e0.0xad818ea09d00.ImageSectionObject.AcLayers.dll.img
ImageSectionObject 0xad818da36c30 oneetx.exe file.0xad818da36c30.0xad818ca48660.ImageSectionObject.oneetx.exe.img
ImageSectionObject 0xad818e48a450 sfc.dll Error dumping file
DataSectionObject 0xad81876b7860 R000000000006.clb Error dumping file
DataSectionObject 0xad8187a70b60 cversions.2.db file.0xad8187a70b60.0xad8187ba3070.DataSectionObject.cversions.2.db.dat
ImageSectionObject 0xad8189ce9740 profapi.dll file.0xad8189ce9740.0xad818c027ba0.ImageSectionObject.profapi.dll.img
ImageSectionObject 0xad818d44ca70 IPHLPAPI.DLL file.0xad818d44ca70.0xad818d33fcd0.ImageSectionObject.IPHLPAPI.DLL.img
ImageSectionObject 0xad818f88a770 OnDemandConnRouteHelper.dll file.0xad818f88a770.0xad818e0c8d30.ImageSectionObject.OnDemandConnRouteHelper.dll.img
ImageSectionObject 0xad818c3c0a90 winhttp.dll file.0xad818c3c0a90.0xad818ce43a20.ImageSectionObject.winhttp.dll.img
ImageSectionObject 0xad818d43cee0 HarddiskVolume31.1.mum Error dumping file
ImageSectionObject 0xad818ef21130 edputil.dll Error dumping file
ImageSectionObject 0xad818e4849b0 srvcli.dll Error dumping file
ImageSectionObject 0xad818ef239d0 netutils.dll Error dumping file
ImageSectionObject 0xad818e384bc0 mpr.dll Error dumping file
ImageSectionObject 0xad81861b3ce0 msvcrt.dll file.0xad81861b3ce0.0xad81863d0d60.ImageSectionObject.msvcrt.dll.img
ImageSectionObject 0xad81898a1150 HarddiskVolume3㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀 file.0xad81898a1150.0xad8189706730.ImageSectionObject.HarddiskVolume3㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀.img
ImageSectionObject 0xad818d43f780 uxtheme.dll file.0xad818d43f780.0xad818cf17a20.ImageSectionObject.uxtheme.dll.img
ImageSectionObject 0xad81861b20c0 msvcp_win.dll file.0xad81861b20c0.0xad818618f010.ImageSectionObject.msvcp_win.dll.img
ImageSectionObject 0xad81861b39c0 bcryptprimitives.dll file.0xad81861b39c0.0xad81863d1d60.ImageSectionObject.bcryptprimitives.dll.img
ImageSectionObject 0xad81861b36a0 nsi.dll file.0xad81861b36a0.0xad81863d2d60.ImageSectionObject.nsi.dll.img
ImageSectionObject 0xad81861b3380 clbcatq.dll file.0xad81861b3380.0xad818618e270.ImageSectionObject.clbcatq.dll.img
ImageSectionObject 0xad81861b3830 advapi32.dll file.0xad81861b3830.0xad818618e010.ImageSectionObject.advapi32.dll.img
ImageSectionObject 0xad81861a8570 ws2_32.dll file.0xad81861a8570.0xad818618dc30.ImageSectionObject.ws2_32.dll.img
ImageSectionObject 0xad81861a9510 user32.dll file.0xad81861a9510.0xad81861917b0.ImageSectionObject.user32.dll.img
ImageSectionObject 0xad81861a99c0 shlwapi.dll file.0xad81861a99c0.0xad8186195750.ImageSectionObject.shlwapi.dll.img
ImageSectionObject 0xad81861a9b50 KernelBase.dll file.0xad81861a9b50.0xad818618d010.ImageSectionObject.KernelBase.dll.img
ImageSectionObject 0xad81861a8ed0 setupapi.dll Error dumping file
ImageSectionObject 0xad81861a9e70 sechost.dll file.0xad81861a9e70.0xad8186195c10.ImageSectionObject.sechost.dll.img
ImageSectionObject 0xad81861a96a0 gdi32full.dll file.0xad81861a96a0.0xad8186191c70.ImageSectionObject.gdi32full.dll.img
ImageSectionObject 0xad81861a91f0 ucrtbase.dll file.0xad81861a91f0.0xad81863d4d60.ImageSectionObject.ucrtbase.dll.img
ImageSectionObject 0xad81861a8700 imm32.dll file.0xad81861a8700.0xad8186191a10.ImageSectionObject.imm32.dll.img
ImageSectionObject 0xad81863b6250 win32u.dll file.0xad81863b6250.0xad81863d6d60.ImageSectionObject.win32u.dll.img
ImageSectionObject 0xad81861a9ce0 combase.dll file.0xad81861a9ce0.0xad8186191050.ImageSectionObject.combase.dll.img
ImageSectionObject 0xad81861a9380 cfgmgr32.dll file.0xad81861a9380.0xad8186191550.ImageSectionObject.cfgmgr32.dll.img
ImageSectionObject 0xad81863b6890 bcrypt.dll file.0xad81863b6890.0xad8186128be0.ImageSectionObject.bcrypt.dll.img
ImageSectionObject 0xad8186134250 wow64cpu.dll file.0xad8186134250.0xad818618a720.ImageSectionObject.wow64cpu.dll.img
ImageSectionObject 0xad81863b7b50 rpcrt4.dll file.0xad81863b7b50.0xad818619cd30.ImageSectionObject.rpcrt4.dll.img
ImageSectionObject 0xad818604f700 wow64.dll file.0xad818604f700.0xad81862c0740.ImageSectionObject.wow64.dll.img
ImageSectionObject 0xad8186134700 HarddiskVolume3蕵遡驐鹇鵉顐鑕陌陇顀騻鰺鸽齃G file.0xad8186134700.0xad818618bc70.ImageSectionObject.HarddiskVolume3蕵遡驐鹇鵉顐鑕陌陇顀騻鰺鸽齃G.img
DataSectionObject 0xad81860a4780 ntdll.dll Error dumping file
ImageSectionObject 0xad81860a4780 ntdll.dll file.0xad81860a4780.0xad81894692b0.ImageSectionObject.ntdll.dll.imgListado de Hashes MD5
Para asegurar la integridad del análisis, listamos los hashes MD5 de los archivos obtenidos:
md5sum *.img
Output:
f7b7627e4bc86ab94b867b3074e4d097 file.0xad818604f700.0xad81862c0740.ImageSectionObject.wow64.dll.img
51233ee8d0d821892260fe555707838b file.0xad81860a4780.0xad81894692b0.ImageSectionObject.ntdll.dll.img
fb099404aa8e801e45babab26c88ffae file.0xad8186134250.0xad818618a720.ImageSectionObject.wow64cpu.dll.img
217314f299f66f756f902ed70c643ade file.0xad8186134700.0xad818618bc70.ImageSectionObject.HarddiskVolume3蕵遡驐鹇鵉顐鑕陌陇顀騻鰺鸽齃G.img
55163d0601117b88e5fe23794d1ca890 file.0xad81861a8570.0xad818618dc30.ImageSectionObject.ws2_32.dll.img
37ca7704ad0814dc1cf660075e586c8c file.0xad81861a8700.0xad8186191a10.ImageSectionObject.imm32.dll.img
db16aec54e9ad640da3b0ae0681d5588 file.0xad81861a8ed0.0xad818618d270.ImageSectionObject.setupapi.dll.img
d2fc59dcf9a731a1184550c7c94966bf file.0xad81861a91f0.0xad81863d4d60.ImageSectionObject.ucrtbase.dll.img
d65624efb582cdc0bce4e76c0a564881 file.0xad81861a9380.0xad8186191550.ImageSectionObject.cfgmgr32.dll.img
f9930ac766888da536305cceb858ddf3 file.0xad81861a9510.0xad81861917b0.ImageSectionObject.user32.dll.img
7f2015f7ba516bead5f31bddd68d9ab8 file.0xad81861a96a0.0xad8186191c70.ImageSectionObject.gdi32full.dll.img
0fad831b911429824b94133adb3372ec file.0xad81861a99c0.0xad8186195750.ImageSectionObject.shlwapi.dll.img
8ef8e70e1ffd4a95ee52350356c27b58 file.0xad81861a9b50.0xad818618d010.ImageSectionObject.KernelBase.dll.img
78e01ec5aeaa5bca3ea0ef560480b18b file.0xad81861a9ce0.0xad8186191050.ImageSectionObject.combase.dll.img
d595ecae1275619510987d9342878001 file.0xad81861a9e70.0xad8186195c10.ImageSectionObject.sechost.dll.img
149d4d9fcaf4fd928352530973e7a06a file.0xad81861b20c0.0xad818618f010.ImageSectionObject.msvcp_win.dll.img
85b215c96c71421378745094f2d000e8 file.0xad81861b3380.0xad818618e270.ImageSectionObject.clbcatq.dll.img
c5369a9080b41027cd47ab9629dbb9a1 file.0xad81861b36a0.0xad81863d2d60.ImageSectionObject.nsi.dll.img
2ba15995635ace475271c82ced6951fe file.0xad81861b3830.0xad818618e010.ImageSectionObject.advapi32.dll.img
aa192ebb825b148ed75adb1e19fc7a47 file.0xad81861b39c0.0xad81863d1d60.ImageSectionObject.bcryptprimitives.dll.img
7dee0925d700c28d98b29ccd46f47f07 file.0xad81861b3ce0.0xad81863d0d60.ImageSectionObject.msvcrt.dll.img
b3f399674c4904f79a86c4169f5fed00 file.0xad81863b6250.0xad81863d6d60.ImageSectionObject.win32u.dll.img
697deeec83b9da3bd65cbb233f573fc5 file.0xad81863b6890.0xad8186128be0.ImageSectionObject.bcrypt.dll.img
a0b3885b903b23173ddf07d3795d8d6a file.0xad81863b7b50.0xad818619cd30.ImageSectionObject.rpcrt4.dll.img
c3800e6587902cb4def7e5ac9a183029 file.0xad81898a1150.0xad8189706730.ImageSectionObject.HarddiskVolume3㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀.img
21bf33a6bda7f3683ed84d6cd7843398 file.0xad8189ce9740.0xad818c027ba0.ImageSectionObject.profapi.dll.img
97d08dd3eae70aa95534d526edf6bd56 file.0xad818c3c0a90.0xad818ce43a20.ImageSectionObject.winhttp.dll.img
d41d8cd98f00b204e9800998ecf8427e file.0xad818d43cee0.0xad818d328c70.ImageSectionObject.HarddiskVolume31.1.mum.img
cdd15a9c7bb752adedb0c96d673f435e file.0xad818d43f780.0xad818cf17a20.ImageSectionObject.uxtheme.dll.img
1cd1600818a81379a04a33525ca449a1 file.0xad818d44ca70.0xad818d33fcd0.ImageSectionObject.IPHLPAPI.DLL.img
f40168cc10f8cb6fe05322fc391e6947 file.0xad818da36c30.0xad818ca48660.ImageSectionObject.oneetx.exe.img
83d3899af03e52374cc119f1e70172fc file.0xad818e37b8e0.0xad818ea09d00.ImageSectionObject.AcLayers.dll.img
d41d8cd98f00b204e9800998ecf8427e file.0xad818e384bc0.0xad818cd8b010.ImageSectionObject.mpr.dll.img
d41d8cd98f00b204e9800998ecf8427e file.0xad818e4849b0.0xad8189e88d80.ImageSectionObject.srvcli.dll.img
d41d8cd98f00b204e9800998ecf8427e file.0xad818e48a450.0xad818f691c00.ImageSectionObject.sfc.dll.img
d41d8cd98f00b204e9800998ecf8427e file.0xad818ef21130.0xad818d21cab0.ImageSectionObject.edputil.dll.img
d41d8cd98f00b204e9800998ecf8427e file.0xad818ef239d0.0xad8185942de0.ImageSectionObject.netutils.dll.img
9431f9a157ce57c837b1594e50641048 file.0xad818f88a770.0xad818e0c8d30.ImageSectionObject.OnDemandConnRouteHelper.dll.imgVerificación en VirusTotal
Finalmente, comprobamos el hash MD5 f40168cc10f8cb6fe05322fc391e6947 en VirusTotal, confirmando que oneetx.exe es un troyano.
#2 Respuesta: rundll32.exe
What is the child process name of the suspicious process?Obtención de la evidencia
En la pregunta anterior, ya pudimos determinar el nombre del proceso hijo del proceso oneetx.exe. Para verificar esto, utilizamos el plugin windows.pslist de Volatility. Como podemos observar, el proceso hijo es: rundll32.exe.
vol -f MemoryDump.mem windows.pslist | grep -E "5896" Output:
5896ress884400.0oneetx.exe 0xad8189b41080in5shed - 1 True 2023-05-21 22:30:56.000000 N/A Disabled
7732 5896 rundll32.exe 0xad818d1912c0 1 - 1 True 2023-05-21 22:31:53.000000 N/A Disabled
#3 Respuesta: PAGE_EXECUTE_READWRITE
What is the memory protection applied to the suspicious process memory region?Obtención de la evidencia
La memoria del proceso sospechoso tiene varias regiones con diferentes niveles de protección. En el contexto del análisis forense, una de las regiones más críticas está protegida con PAGE_EXECUTE_READWRITE, lo que permite tanto la lectura, escritura como la ejecución de código. Este tipo de protección es especialmente preocupante, ya que puede ser explotado para ejecutar código malicioso inyectado en el proceso.
Al examinar la salida del siguiente comando, se puede observar la siguiente información relevante:
vol -f MemoryDump.mem windows.vadinfo --pid 5896Output relevante:
PID Process Offset Start VPN End VPN Tag Protection CommitCharge PrivateMemory Parent File File output
5896 oneetx.exe 0xffffad818d6d5940 0x400000 0x437fff VadS PAGE_EXECUTE_READWRITE 56 1 0xffffad818d2c7ac0 N/A Disabled
Output:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
PID Process Offset Start VPN End VPN Tag Protection CommitCharge PrivateMemory Parent File File output
5896 oneetx.exe 0xffffad818ddb2c40 0x73da0000 0x74024fff Vad PAGE_EXECUTE_WRITECOPY 554 0 0x0 \Windows\SysWOW64\AcLayers.dll Disabled
5896 oneetx.exe 0xffffad818ddc5200 0x1a60000 0x2e60fff Vad PAGE_READONLY 0 0 0xffffad818ddb2c40 N/A Disabled
5896 oneetx.exe 0xffffad818d6d5b70 0x1390000 0x139ffff VadS PAGE_READWRITE 10 1 0xffffad818ddc5200 N/A Disabled
5896 oneetx.exe 0xffffad818d6bc2b0 0x1000000 0x11fffff VadS PAGE_READWRITE 11 1 0xffffad818d6d5b70 N/A Disabled
5896 oneetx.exe 0xffffad818ddab1c0 0xfc0000 0xfc0fff Vad PAGE_READONLY 0 0 0xffffad818d6bc2b0 N/A Disabled
5896 oneetx.exe 0xffffad818d2c7ac0 0xec0000 0xfb7fff Vad PAGE_EXECUTE_WRITECOPY 0 0 0xffffad818ddab1c0 \Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe Disabled
5896 oneetx.exe 0xffffad818d6d5940 0x400000 0x437fff VadS PAGE_EXECUTE_READWRITE 56 1 0xffffad818d2c7ac0 N/A Disabled
5896 oneetx.exe 0xffffad818ddade20 0xfe0000 0xfe0fff Vad PAGE_READONLY 0 0 0xffffad818ddab1c0 N/A Disabled
5896 oneetx.exe 0xffffad818ddab940 0xfd0000 0xfd0fff Vad PAGE_READONLY 0 0 0xffffad818ddade20 N/A Disabled
5896 oneetx.exe 0xffffad81876f1b30 0xff0000 0xff3fff Vad PAGE_READONLY 0 0 0xffffad818ddade20 N/A Disabled
5896 oneetx.exe 0xffffad818d6cb940 0x1360000 0x1361fff VadS PAGE_READWRITE 2 1 0xffffad818d6bc2b0 N/A Disabled
5896 oneetx.exe 0xffffad818d6c5cc0 0x1220000 0x125ffff VadS PAGE_READWRITE 11 1 0xffffad818d6cb940 N/A Disabled
5896 oneetx.exe 0xffffad818d2cfea0 0x1200000 0x121cfff Vad PAGE_READONLY 0 0 0xffffad818d6c5cc0 N/A Disabled
5896 oneetx.exe 0xffffad818d6c8a10 0x1260000 0x135ffff VadS PAGE_READWRITE 6 1 0xffffad818d6c5cc0 N/A Disabled
5896 oneetx.exe 0xffffad818ddac840 0x1370000 0x1370fff Vad PAGE_READONLY 0 0 0xffffad818d6cb940 N/A Disabled
5896 oneetx.exe 0xffffad818ddae780 0x1380000 0x1380fff Vad PAGE_READONLY 0 0 0xffffad818ddac840 N/A Disabled
5896 oneetx.exe 0xffffad818d6d5c60 0x1510000 0x160ffff VadS PAGE_READWRITE 218 1 0xffffad818d6d5b70 N/A Disabled
5896 oneetx.exe 0xffffad818f029ce0 0x1490000 0x149dfff VadS PAGE_READWRITE 2 1 0xffffad818d6d5c60 N/A Disabled
5896 oneetx.exe 0xffffad818ddaf860 0x13b0000 0x13bffff Vad PAGE_READWRITE 0 0 0xffffad818f029ce0 N/A Disabled
5896 oneetx.exe 0xffffad818ddaebe0 0x13a0000 0x13a0fff Vad PAGE_READONLY 0 0 0xffffad818ddaf860 N/A Disabled
5896 oneetx.exe 0xffffad818ddb24c0 0x13c0000 0x1488fff Vad PAGE_READONLY 0 0 0xffffad818ddaf860 \Windows\System32\locale.nls Disabled
5896 oneetx.exe 0xffffad818e502260 0x14b0000 0x14b7fff Vad PAGE_READONLY 0 0 0xffffad818f029ce0 N/A Disabled
5896 oneetx.exe 0xffffad818ddc3ea0 0x14a0000 0x14a2fff Vad PAGE_EXECUTE_WRITECOPY 0 0 0xffffad818e502260 \Windows\SysWOW64\sfc.dll Disabled
5896 oneetx.exe 0xffffad818ddc62e0 0x1500000 0x1500fff Vad PAGE_READWRITE 0 0 0xffffad818e502260 N/A Disabled
5896 oneetx.exe 0xffffad818c29eaf0 0x14c0000 0x14fffff VadS PAGE_READWRITE 11 1 0xffffad818ddc62e0 N/A Disabled
5896 oneetx.exe 0xffffad818f029600 0x16c0000 0x16cffff VadS PAGE_READWRITE 7 1 0xffffad818d6d5c60 N/A Disabled
5896 oneetx.exe 0xffffad818f02f6e0 0x1690000 0x1696fff VadS PAGE_READWRITE 1 1 0xffffad818f029600 N/A Disabled
5896 oneetx.exe 0xffffad818ddc5d40 0x16b0000 0x16b0fff Vad PAGE_READONLY 0 0 0xffffad818f02f6e0 N/A Disabled
5896 oneetx.exe 0xffffad818e503480 0x16d0000 0x18cffff Vad PAGE_READONLY 0 0 0xffffad818f029600 N/A Disabled
5896 oneetx.exe 0xffffad818ddc5160 0x18d0000 0x1a50fff Vad PAGE_READONLY 0 0 0xffffad818e503480 N/A Disabled
5896 oneetx.exe 0xffffad818f035e50 0x3f00000 0x3f00fff VadS PAGE_READWRITE 1 1 0xffffad818ddc5200 N/A Disabled
5896 oneetx.exe 0xffffad818f02a190 0x3770000 0x377ffff VadS PAGE_READWRITE 1 1 0xffffad818f035e50 N/A Disabled
5896 oneetx.exe 0xffffad818ddc7460 0x35f0000 0x35f6fff Vad PAGE_READONLY 0 0 0xffffad818f02a190 \Windows\Registration\R000000000006.clb Disabled
5896 oneetx.exe 0xffffad818ddc4260 0x3170000 0x34a7fff Vad PAGE_READONLY 0 0 0xffffad818ddc7460 N/A Disabled
5896 oneetx.exe 0xffffad818c2a02b0 0x2e70000 0x2f6ffff VadS PAGE_READWRITE 4 1 0xffffad8190ac5480 N/A Disabled
5896 oneetx.exe 0xffffad818d6c4c30 0x34b0000 0x34effff VadS PAGE_READWRITE 11 1 0xffffad818ddc4260 N/A Disabled
5896 oneetx.exe 0xffffad818d6cd150 0x34f0000 0x35effff VadS PAGE_READWRITE 5 1 0xffffad818d6c4c30 N/A Disabled
5896 oneetx.exe 0xffffad818ddc7a00 0x3750000 0x3753fff Vad PAGE_READONLY 0 0 0xffffad818ddc7460 \ProgramData\Microsoft\Windows\Caches\cversions.2.db Disabled
5896 oneetx.exe 0xffffad818f02b310 0x3600000 0x360ffff VadS PAGE_NOACCESS 1 1 0xffffad818ddc7a00 N/A Disabled
5896 oneetx.exe 0xffffad818ddc75a0 0x3760000 0x3763fff Vad PAGE_READONLY 0 0 0xffffad818ddc7a00 \ProgramData\Microsoft\Windows\Caches\cversions.2.db Disabled
5896 oneetx.exe 0xffffad818ddc7640 0x39b0000 0x39bffff Vad PAGE_READONLY 0 0 0xffffad818f02a190 \Windows\System32\en-GB\propsys.dll.mui Disabled
5896 oneetx.exe 0xffffad818ddc7500 0x38c0000 0x3908fff Vad PAGE_READONLY 0 0 0xffffad818ddc7640 翀ß챓̠
쀀དᵓ큌㱐ೀ Disabled
5896 oneetx.exe 0xffffad818ddc6c40 0x3910000 0x39abfff Vad PAGE_READONLY 0 0 0xffffad818ddc7500 \ProgramData\Microsoft\Windows\Caches\{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000001.db Disabled
5896 oneetx.exe 0xffffad818ddc7b40 0x39d0000 0x39e9fff Vad PAGE_READONLY 0 0 0xffffad818ddc7640 \Users\Tammam\AppData\Local\Microsoft\Windows\Caches\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000001.db Disabled
5896 oneetx.exe 0xffffad818ddcfd40 0x39c0000 0x39c0fff Vad PAGE_READWRITE 0 0 0xffffad818ddc7b40 N/A Disabled
5896 oneetx.exe 0xffffad818ddc8f40 0x39f0000 0x39f0fff Vad PAGE_READWRITE 0 0 0xffffad818ddc7b40 N/A Disabled
5896 oneetx.exe 0xffffad818ddd4160 0x4090000 0x4090fff Vad PAGE_READONLY 0 0 0xffffad818f035e50 N/A Disabled
5896 oneetx.exe 0xffffad818ddd29a0 0x4070000 0x4070fff Vad PAGE_READONLY 0 0 0xffffad818ddd4160 N/A Disabled
5896 oneetx.exe 0xffffad818f035ea0 0x3f10000 0x3f10fff VadS PAGE_READWRITE 1 1 0xffffad818ddd29a0 N/A Disabled
5896 oneetx.exe 0xffffad818ddae140 0x4060000 0x4060fff Vad PAGE_READWRITE 0 0 0xffffad818f035ea0 N/A Disabled
5896 oneetx.exe 0xffffad818ddd3c60 0x4080000 0x408ffff Vad PAGE_READONLY 0 0 0xffffad818ddd29a0 N/A Disabled
5896 oneetx.exe 0xffffad8189d257b0 0x4220000 0x4223fff Vad PAGE_READONLY 0 0 0xffffad818ddd4160 \ProgramData\Microsoft\Windows\Caches\cversions.2.db Disabled
5896 oneetx.exe 0xffffad818ddd4340 0x40b0000 0x40b2fff Vad PAGE_READONLY 0 0 0xffffad8189d257b0 \Windows\System32\en-US\mswsock.dll.mui Disabled
5896 oneetx.exe 0xffffad818ddd34e0 0x40a0000 0x40a0fff Vad PAGE_READWRITE 0 0 0xffffad818ddd4340 N/A Disabled
5896 oneetx.exe 0xffffad818ddd3940 0x40c0000 0x40d0fff Vad PAGE_READONLY 0 0 0xffffad818ddd4340 N/A Disabled
5896 oneetx.exe 0xffffad818ddc46c0 0x73050000 0x730c2fff Vad PAGE_EXECUTE_WRITECOPY 4 0 0xffffad8189d257b0 \Windows\SysWOW64\winspool.drv Disabled
5896 oneetx.exe 0xffffad818ddc43a0 0x6c5a0000 0x6c9f3fff Vad PAGE_EXECUTE_WRITECOPY 6 0 0xffffad818ddc46c0 菨ル護Ǚ菨ル護Ǚ菨ル護Ǚ菨ル護Ǚ Disabled
5896 oneetx.exe 0xffffad818ddae460 0x76390000 0x7647ffff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818ddb2c40 N/A Disabled
5896 oneetx.exe 0xffffad818ddc4b20 0x754e0000 0x754eefff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddae460 N/A Disabled
5896 oneetx.exe 0xffffad818ddc7820 0x750c0000 0x750d7fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddc4b20 \Windows\SysWOW64\profapi.dll Disabled
5896 oneetx.exe 0xffffad818ddd1a00 0x74bb0000 0x74be1fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddc7820 \Windows\SysWOW64\IPHLPAPI.DLL Disabled
5896 oneetx.exe 0xffffad818ddd01a0 0x74550000 0x74561fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddd1a00 \Windows\SysWOW64\OnDemandConnRouteHelper.dll Disabled
5896 oneetx.exe 0xffffad818ddc5a20 0x743b0000 0x74471fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddd01a0 \Windows\SysWOW64\propsys.dll Disabled
5896 oneetx.exe 0xffffad818ddcdae0 0x740e0000 0x74287fff Vad PAGE_EXECUTE_WRITECOPY 14 0 0xffffad818ddc5a20 \Windows\SysWOW64\urlmon.dll Disabled
5896 oneetx.exe 0xffffad818ddd1960 0x74490000 0x744e1fff Vad PAGE_EXECUTE_WRITECOPY 4 0 0xffffad818ddc5a20 \Windows\SysWOW64\mswsock.dll Disabled
5896 oneetx.exe 0xffffad818ddd0240 0x74a50000 0x74b18fff Vad PAGE_EXECUTE_WRITECOPY 4 0 0xffffad818ddd01a0 \Windows\SysWOW64\winhttp.dll Disabled
5896 oneetx.exe 0xffffad818ddce580 0x74e30000 0x74e50fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddd1a00 1.1.mum Disabled
5896 oneetx.exe 0xffffad818ddcdcc0 0x74e90000 0x750bcfff Vad PAGE_EXECUTE_WRITECOPY 10 0 0xffffad818ddce580 \Windows\SysWOW64\iertutil.dll Disabled
5896 oneetx.exe 0xffffad818ddcbf60 0x752d0000 0x752eafff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddc7820 \Windows\SysWOW64\edputil.dll Disabled
5896 oneetx.exe 0xffffad818ddccf00 0x751f0000 0x7520cfff Vad PAGE_EXECUTE_WRITECOPY 11 0 0xffffad818ddcbf60 \Windows\SysWOW64\srvcli.dll Disabled
5896 oneetx.exe 0xffffad818ddce940 0x751e0000 0x751eafff Vad PAGE_EXECUTE_WRITECOPY 2 0 0xffffad818ddccf00 \Windows\SysWOW64\netutils.dll Disabled
5896 oneetx.exe 0xffffad818ddd2040 0x752f0000 0x752f7fff Vad PAGE_EXECUTE_WRITECOPY 2 0 0xffffad818ddcbf60 \Windows\SysWOW64\winnsi.dll Disabled
5896 oneetx.exe 0xffffad818ddbe9a0 0x76090000 0x76125fff Vad PAGE_EXECUTE_WRITECOPY 4 0 0xffffad818ddc4b20 N/A Disabled
5896 oneetx.exe 0xffffad818ddb3b40 0x75b50000 0x75beefff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddbe9a0 \Windows\SysWOW64\apphelp.dll Disabled
5896 oneetx.exe 0xffffad818ddc57a0 0x75510000 0x75536fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb3b40 \Windows\SysWOW64\wldp.dll Disabled
5896 oneetx.exe 0xffffad818ddc2f00 0x754f0000 0x75508fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddc57a0 \Windows\SysWOW64\mpr.dll Disabled
5896 oneetx.exe 0xffffad818ddc66a0 0x75540000 0x75b4cfff Vad PAGE_EXECUTE_WRITECOPY 9 0 0xffffad818ddc57a0 \Windows\SysWOW64\windows.storage.dll Disabled
5896 oneetx.exe 0xffffad818ddb4180 0x75d90000 0x75e4efff Vad PAGE_EXECUTE_WRITECOPY 7 0 0xffffad818ddb3b40 \Windows\SysWOW64\msvcrt.dll Disabled
5896 oneetx.exe 0xffffad818ddc5980 0x75ca0000 0x75caefff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb4180 㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀㙎倀 Disabled
5896 oneetx.exe 0xffffad818ddac700 0x75c20000 0x75c93fff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818ddc5980 \Windows\SysWOW64\uxtheme.dll Disabled
5896 oneetx.exe 0xffffad818ddb56c0 0x75cb0000 0x75d2afff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818ddc5980 \Windows\SysWOW64\msvcp_win.dll Disabled
5896 oneetx.exe 0xffffad818ddc4d00 0x75eb0000 0x75f0efff Vad PAGE_EXECUTE_WRITECOPY 2 0 0xffffad818ddb4180 \Windows\SysWOW64\bcryptprimitives.dll Disabled
5896 oneetx.exe 0xffffad818ddd2860 0x75f10000 0x75f16fff Vad PAGE_EXECUTE_WRITECOPY 2 0 0xffffad818ddc4d00 \Windows\SysWOW64\nsi.dll Disabled
5896 oneetx.exe 0xffffad818ddc6380 0x76220000 0x7629dfff Vad PAGE_EXECUTE_WRITECOPY 6 0 0xffffad818ddbe9a0 \Windows\SysWOW64\clbcatq.dll Disabled
5896 oneetx.exe 0xffffad818ddc5660 0x76130000 0x76212fff Vad PAGE_EXECUTE_WRITECOPY 4 0 0xffffad818ddc6380 N/A Disabled
5896 oneetx.exe 0xffffad818ddc5520 0x762a0000 0x7631afff Vad PAGE_EXECUTE_WRITECOPY 6 0 0xffffad818ddc6380 \Windows\SysWOW64\advapi32.dll Disabled
5896 oneetx.exe 0xffffad818ddc4a80 0x76320000 0x76382fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddc5520 \Windows\SysWOW64\ws2_32.dll Disabled
5896 oneetx.exe 0xffffad818d2ca2c0 0x77de0000 0x77f83fff Vad PAGE_EXECUTE_WRITECOPY 9 0 0xffffad818ddae460 \Windows\SysWOW64\ntdll.dll Disabled
5896 oneetx.exe 0xffffad818ddb62a0 0x77620000 0x777bafff Vad PAGE_EXECUTE_WRITECOPY 8 0 0xffffad818d2ca2c0 \Windows\SysWOW64\user32.dll Disabled
5896 oneetx.exe 0xffffad818ddbe540 0x76d00000 0x76d44fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb62a0 \Windows\SysWOW64\shlwapi.dll Disabled
5896 oneetx.exe 0xffffad818ddadf60 0x76a50000 0x76c68fff Vad PAGE_EXECUTE_WRITECOPY 6 0 0xffffad818ddbe540 \Windows\SysWOW64\KernelBase.dll Disabled
5896 oneetx.exe 0xffffad818ddbf760 0x76610000 0x76a48fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddadf60 \Windows\SysWOW64\setupapi.dll Disabled
5896 oneetx.exe 0xffffad818ddc4bc0 0x76c70000 0x76ce5fff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818ddadf60 \Windows\SysWOW64\sechost.dll Disabled
5896 oneetx.exe 0xffffad818ddb54e0 0x773f0000 0x774ccfff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818ddbe540 \Windows\SysWOW64\gdi32full.dll Disabled
5896 oneetx.exe 0xffffad818ddb7920 0x76e30000 0x773e4fff Vad PAGE_EXECUTE_WRITECOPY 11 0 0xffffad818ddb54e0 N/A Disabled
5896 oneetx.exe 0xffffad818ddc4440 0x76da0000 0x76e26fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb7920 N/A Disabled
5896 oneetx.exe 0xffffad818ddb5800 0x774d0000 0x775effff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb54e0 \Windows\SysWOW64\ucrtbase.dll Disabled
5896 oneetx.exe 0xffffad818ddc5480 0x775f0000 0x77614fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb5800 \Windows\SysWOW64\imm32.dll Disabled
5896 oneetx.exe 0xffffad818ddb65c0 0x77c90000 0x77ca7fff Vad PAGE_EXECUTE_WRITECOPY 2 0 0xffffad818ddb62a0 \Windows\SysWOW64\win32u.dll Disabled
5896 oneetx.exe 0xffffad818ddbeea0 0x77900000 0x77b7ffff Vad PAGE_EXECUTE_WRITECOPY 6 0 0xffffad818ddb65c0 \Windows\SysWOW64\combase.dll Disabled
5896 oneetx.exe 0xffffad818ddc12e0 0x777c0000 0x777fafff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddbeea0 \Windows\SysWOW64\cfgmgr32.dll Disabled
5896 oneetx.exe 0xffffad818ddb5da0 0x77c60000 0x77c82fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddbeea0 N/A Disabled
5896 oneetx.exe 0xffffad818ddc2e60 0x77b80000 0x77b98fff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddb5da0 \Windows\SysWOW64\bcrypt.dll Disabled
5896 oneetx.exe 0xffffad818ddacca0 0x77dd0000 0x77dd9fff Vad PAGE_EXECUTE_WRITECOPY 2 0 0xffffad818ddb65c0 \Windows\System32\wow64cpu.dll Disabled
5896 oneetx.exe 0xffffad818ddc0020 0x77cb0000 0x77d6dfff Vad PAGE_EXECUTE_WRITECOPY 3 0 0xffffad818ddacca0 \Windows\SysWOW64\rpcrt4.dll Disabled
5896 oneetx.exe 0xffffad818d6b9290 0x7ffed000 0x7ffedfff VadS PAGE_READONLY 1 1 0xffffad818d2ca2c0 N/A Disabled
5896 oneetx.exe 0xffffad818d6d5990 0x7fb20000 0x7fb21fff VadS PAGE_READWRITE 1 1 0xffffad818d6b9290 N/A Disabled
5896 oneetx.exe 0xffffad818d6bfb90 0x7faf0000 0x7faf1fff VadS PAGE_READWRITE 1 1 0xffffad818d6d5990 N/A Disabled
5896 oneetx.exe 0xffffad818ddb2100 0x7f9e0000 0x7fadffff Vad PAGE_READONLY 0 0 0xffffad818d6bfb90 N/A Disabled
5896 oneetx.exe 0xffffad818d6d56c0 0x7fae0000 0x7fae8fff VadS PAGE_READWRITE 1 1 0xffffad818ddb2100 N/A Disabled
5896 oneetx.exe 0xffffad818d6d5b20 0x7fb00000 0x7fb10fff VadS PAGE_READWRITE 1 1 0xffffad818d6bfb90 N/A Disabled
5896 oneetx.exe 0xffffad818d2ce780 0x7fb40000 0x7fb62fff Vad PAGE_READONLY 0 0 0xffffad818d6d5990 N/A Disabled
5896 oneetx.exe 0xffffad818d2cde20 0x7fb30000 0x7fb30fff Vad PAGE_READONLY 0 0 0xffffad818d2ce780 N/A Disabled
5896 oneetx.exe 0xffffad818d6b6ea0 0x7ffe0000 0x7ffe0fff VadS PAGE_READONLY 1 1 0xffffad818d2ce780 N/A Disabled
5896 oneetx.exe 0xffffad818ddacde0 0x7ffa69860000 0x7ffa698b8fff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818d6b9290 \Windows\System32\wow64.dll Disabled
5896 oneetx.exe 0xffffad818d6baeb0 0x7fff0000 0xffffffff VadS PAGE_READONLY 2147483647 1 0xffffad818ddacde0 N/A Disabled
5896 oneetx.exe 0xffffad818ddacac0 0x7ffa68810000 0x7ffa68892fff Vad PAGE_EXECUTE_WRITECOPY 5 0 0xffffad818d6baeb0 蕵遡驐鹇鵉顐鑕陌陇顀騻鰺鸽齃G Disabled
5896 oneetx.exe 0xffffad818d2c7f20 0x7ffa69c70000 0x7ffa69e67fff Vad PAGE_EXECUTE_WRITECOPY 16 0 0xffffad818ddacde0 \Windows\System32\ntdll.dll Disabled
La línea anterior indica que hay una región de memoria en el proceso oneetx.exe con protección PAGE_EXECUTE_READWRITE. Esta región empieza en 0x400000 y termina en 0x437fff. La combinación de permisos de lectura, escritura y ejecución en una región de memoria es inusual y puede ser indicativa de actividades sospechosas, como la inyección de código malicioso que podría ser ejecutado.
Importancia de PAGE_EXECUTE_READWRITE
La protección PAGE_EXECUTE_READWRITE es significativa porque:
- Permite la ejecución de código, lo cual es un requisito para que un programa malicioso o un exploit puedan ser ejecutados.
- Permite la escritura, lo que facilita la modificación del contenido de la memoria, incluyendo la posibilidad de alterar el comportamiento del código legítimo del proceso.
- Permite la lectura, lo que es necesario para que el proceso acceda y lea instrucciones o datos almacenados en esa región de memoria.
En resumen, la presencia de una región de memoria con PAGE_EXECUTE_READWRITE en el proceso oneetx.exe es un indicador claro de una posible actividad maliciosa.
#4 Respuesta: outline.exe
What is the name of the process responsible for the VPN connection?Obtención de la evidencia
Listamos las conexiones empleando windows.netscan.NetScan en busca de alguna conexión sospechosa y encontramos el proceso: tun2socks.exe.
vol -f MemoryDump.mem windows.netscan.NetScanOutput
olatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
Offset Proto LocalAddr LocalPort ForeignAddr ForeignPort State PID Owner Created
0xad81861e2310 TCPv4 0.0.0.0 49668 0.0.0.0 0 LISTENING 1840 spoolsv.exe 2023-05-21 22:28:09.000000
0xad81861e2310 TCPv6 :: 49668 :: 0 LISTENING 1840 spoolsv.exe 2023-05-21 22:28:09.000000
0xad81861e2470 TCPv4 0.0.0.0 5040 0.0.0.0 0 LISTENING 1196 svchost.exe 2023-05-21 22:30:31.000000
0xad81861e2730 TCPv4 0.0.0.0 135 0.0.0.0 0 LISTENING 952 svchost.exe 2023-05-21 22:27:36.000000
0xad81861e2b50 TCPv4 0.0.0.0 49665 0.0.0.0 0 LISTENING 552 wininit.exe 2023-05-21 22:27:36.000000
0xad81861e2b50 TCPv6 :: 49665 :: 0 LISTENING 552 wininit.exe 2023-05-21 22:27:36.000000
0xad81861e2e10 TCPv4 0.0.0.0 49665 0.0.0.0 0 LISTENING 552 wininit.exe 2023-05-21 22:27:36.000000
0xad81861e3230 TCPv4 0.0.0.0 49664 0.0.0.0 0 LISTENING 696 lsass.exe 2023-05-21 22:27:36.000000
0xad81861e3390 TCPv4 0.0.0.0 135 0.0.0.0 0 LISTENING 952 svchost.exe 2023-05-21 22:27:36.000000
0xad81861e3390 TCPv6 :: 135 :: 0 LISTENING 952 svchost.exe 2023-05-21 22:27:36.000000
0xad81861e34f0 TCPv4 0.0.0.0 49664 0.0.0.0 0 LISTENING 696 lsass.exe 2023-05-21 22:27:36.000000
0xad81861e34f0 TCPv6 :: 49664 :: 0 LISTENING 696 lsass.exe 2023-05-21 22:27:36.000000
0xad81861e37b0 TCPv4 0.0.0.0 49666 0.0.0.0 0 LISTENING 1012 svchost.exe 2023-05-21 22:27:49.000000
0xad81861e37b0 TCPv6 :: 49666 :: 0 LISTENING 1012 svchost.exe 2023-05-21 22:27:49.000000
0xad81861e3910 TCPv4 0.0.0.0 49667 0.0.0.0 0 LISTENING 448 svchost.exe 2023-05-21 22:27:58.000000
0xad81861e3910 TCPv6 :: 49667 :: 0 LISTENING 448 svchost.exe 2023-05-21 22:27:58.000000
0xad81861e3a70 TCPv4 0.0.0.0 49668 0.0.0.0 0 LISTENING 1840 spoolsv.exe 2023-05-21 22:28:09.000000
0xad81861e3bd0 TCPv4 0.0.0.0 49666 0.0.0.0 0 LISTENING 1012 svchost.exe 2023-05-21 22:27:49.000000
0xad81861e3e90 TCPv4 0.0.0.0 49667 0.0.0.0 0 LISTENING 448 svchost.exe 2023-05-21 22:27:58.000000
0xad818662ecb0 TCPv4 0.0.0.0 445 0.0.0.0 0 LISTENING 4 System 2023-05-21 22:29:04.000000
0xad818662ecb0 TCPv6 :: 445 :: 0 LISTENING 4 System 2023-05-21 22:29:04.000000
0xad818662f390 TCPv4 0.0.0.0 7680 0.0.0.0 0 LISTENING 5476 svchost.exe 2023-05-21 22:58:09.000000
0xad818662f390 TCPv6 :: 7680 :: 0 LISTENING 5476 svchost.exe 2023-05-21 22:58:09.000000
0xad81878518f0 UDPv4 192.168.190.141 138 * 0 4 System 2023-05-21 22:27:56.000000
0xad8187852250 UDPv4 192.168.190.141 137 * 0 4 System 2023-05-21 22:27:56.000000
0xad818902a5d0 TCPv4 192.168.190.141 139 0.0.0.0 0 LISTENING 4 System 2023-05-21 22:27:56.000000
0xad818971f870 UDPv4 0.0.0.0 56250 * 0 6644 SkypeApp.exe 2023-05-21 22:58:07.000000
0xad818971f870 UDPv6 :: 56250 * 0 6644 SkypeApp.exe 2023-05-21 22:58:07.000000
0xad81897eb010 TCPv4 10.0.85.2 55439 20.22.207.36 443 CLOSED 448 svchost.exe 2023-05-21 23:00:40.000000
0xad81898a6d10 UDPv4 127.0.0.1 57787 * 0 448 svchost.exe 2023-05-21 22:28:54.000000
0xad81898bc7f0 UDPv4 0.0.0.0 5355 * 0 1448 svchost.exe 2023-05-21 22:57:37.000000
0xad81898bc7f0 UDPv6 :: 5355 * 0 1448 svchost.exe 2023-05-21 22:57:37.000000
0xad8189a291b0 TCPv4 0.0.0.0 55972 0.0.0.0 0 LISTENING 5964 svchost.exe 2023-05-21 22:27:57.000000
0xad8189a291b0 TCPv6 :: 55972 :: 0 LISTENING 5964 svchost.exe 2023-05-21 22:27:57.000000
0xad8189a29470 TCPv4 0.0.0.0 55972 0.0.0.0 0 LISTENING 5964 svchost.exe 2023-05-21 22:27:57.000000
0xad8189a2a7b0 TCPv4 0.0.0.0 49669 0.0.0.0 0 LISTENING 676 services.exe 2023-05-21 22:29:08.000000
0xad8189a2a910 TCPv4 0.0.0.0 49669 0.0.0.0 0 LISTENING 676 services.exe 2023-05-21 22:29:08.000000
0xad8189a2a910 TCPv6 :: 49669 :: 0 LISTENING 676 services.exe 2023-05-21 22:29:08.000000
0xad8189a30a20 TCPv4 192.168.190.141 53660 38.121.43.65 443 CLOSED 4628 tun2socks.exe 2023-05-21 22:00:25.000000
0xad8189a844e0 UDPv4 10.0.85.2 58844 * 0 5328 msedge.exe 2023-05-21 22:51:53.000000
0xad8189cea350 UDPv4 0.0.0.0 5050 * 0 1196 svchost.exe 2023-05-21 22:30:27.000000
0xad818c17ada0 UDPv4 0.0.0.0 52051 * 0 4628 tun2socks.exe 2023-05-21 22:24:14.000000
0xad818c367b30 TCPv4 192.168.190.141 49710 204.79.197.203 443 CLOSE_WAIT 1916 SearchApp.exe 2023-05-21 22:33:09.000000
0xad818c3b22e0 UDPv4 0.0.0.0 63218 * 0 1448 svchost.exe 2023-05-21 22:39:15.000000
0xad818c3b22e0 UDPv6 :: 63218 * 0 1448 svchost.exe 2023-05-21 22:39:15.000000
0xad818d004ba0 UDPv4 0.0.0.0 63917 * 0 1448 svchost.exe 2023-05-21 23:02:48.000000
0xad818d004ba0 UDPv6 :: 63917 * 0 1448 svchost.exe 2023-05-21 23:02:48.000000
0xad818d1bc010 TCPv4 10.0.85.2 55424 52.182.143.208 443 CLOSE_WAIT 6644 SkypeApp.exe 2023-05-21 22:57:59.000000
0xad818d2f7b00 TCPv4 10.0.85.2 55460 52.159.127.243 443 CLOSED 448 svchost.exe 2023-05-21 23:01:08.000000
0xad818d5352b0 TCPv4 10.0.85.2 53659 204.79.197.237 443 CLOSED 3580 explorer.exe 2023-05-21 22:00:25.000000
0xad818da19700 UDPv4 0.0.0.0 500 * 0 448 svchost.exe 2023-05-21 22:27:56.000000
0xad818da1ab50 UDPv4 0.0.0.0 4500 * 0 448 svchost.exe 2023-05-21 22:27:56.000000
0xad818da1d8a0 UDPv4 0.0.0.0 4500 * 0 448 svchost.exe 2023-05-21 22:27:56.000000
0xad818da1d8a0 UDPv6 :: 4500 * 0 448 svchost.exe 2023-05-21 22:27:56.000000
0xad818da1dbc0 UDPv4 0.0.0.0 0 * 0 448 svchost.exe 2023-05-21 22:27:57.000000
0xad818da1dbc0 UDPv6 :: 0 * 0 448 svchost.exe 2023-05-21 22:27:57.000000
0xad818da1e520 UDPv4 0.0.0.0 0 * 0 448 svchost.exe 2023-05-21 22:27:57.000000
0xad818da1f010 UDPv4 0.0.0.0 500 * 0 448 svchost.exe 2023-05-21 22:27:56.000000
0xad818da1f010 UDPv6 :: 500 * 0 448 svchost.exe 2023-05-21 22:27:56.000000
0xad818da202d0 UDPv4 0.0.0.0 0 * 0 5964 svchost.exe 2023-05-21 22:27:57.000000
0xad818da202d0 UDPv6 :: 0 * 0 5964 svchost.exe 2023-05-21 22:27:57.000000
0xad818da21bd0 UDPv4 0.0.0.0 0 * 0 5964 svchost.exe 2023-05-21 22:27:57.000000
0xad818dbc1a60 TCPv4 192.168.190.141 49713 104.119.188.96 443 CLOSE_WAIT 1916 SearchApp.exe 2023-05-21 22:33:11.000000
0xad818dd05370 UDPv4 0.0.0.0 5353 * 0 5328 msedge.exe 2023-05-21 23:01:32.000000
0xad818dd07440 UDPv4 0.0.0.0 5353 * 0 5328 msedge.exe 2023-05-21 23:01:32.000000
0xad818dd07440 UDPv6 :: 5353 * 0 5328 msedge.exe 2023-05-21 23:01:32.000000
0xad818de4aa20 TCPv4 10.0.85.2 55462 77.91.124.20 80 CLOSED 5896 oneetx.exe 2023-05-21 23:01:22.000000
0xad818df1d920 TCPv4 192.168.190.141 55433 38.121.43.65 443 CLOSED 4628 tun2socks.exe 2023-05-21 23:00:02.000000
0xad818e3698f0 UDPv4 0.0.0.0 5353 * 0 5328 msedge.exe 2023-05-21 22:05:24.000000
0xad818e3701a0 UDPv4 0.0.0.0 5353 * 0 5328 msedge.exe 2023-05-21 22:05:24.000000
0xad818e3701a0 UDPv6 :: 5353 * 0 5328 msedge.exe 2023-05-21 22:05:24.000000
0xad818e370b00 UDPv4 0.0.0.0 5353 * 0 5328 msedge.exe 2023-05-21 22:05:24.000000
0xad818e371dc0 UDPv4 0.0.0.0 5353 * 0 5328 msedge.exe 2023-05-21 22:05:24.000000
0xad818e371dc0 UDPv6 :: 5353 * 0 5328 msedge.exe 2023-05-21 22:05:24.000000
0xad818e3a1200 UDPv4 0.0.0.0 5355 * 0 1448 svchost.exe 2023-05-21 22:57:37.000000
0xad818e4a6900 UDPv4 0.0.0.0 0 * 0 5480 oneetx.exe 2023-05-21 22:39:47.000000
0xad818e4a6900 UDPv6 :: 0 * 0 5480 oneetx.exe 2023-05-21 22:39:47.000000
0xad818e4a9650 UDPv4 0.0.0.0 0 * 0 5480 oneetx.exe 2023-05-21 22:39:47.000000
0xad818e77da20 TCPv4 192.168.190.141 52434 204.79.197.200 443 CLOSED - - 2023-05-21 23:02:20.000000
0xad818ef06c70 UDPv6 fe80::a406:8c42:43a9:413 1900 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef09b50 UDPv6 fe80::4577:874:81a:78cd 1900 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef0b5e0 UDPv6 ::1 1900 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef0ec90 UDPv6 fe80::a406:8c42:43a9:413 55910 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef0f140 UDPv6 fe80::4577:874:81a:78cd 55911 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef0f2d0 UDPv6 ::1 55912 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef0fdc0 UDPv4 192.168.190.141 55913 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef10270 UDPv4 10.0.85.2 137 * 0 4 System 2023-05-21 22:40:16.000000
0xad818ef11530 UDPv4 192.168.190.141 1900 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef116c0 UDPv4 10.0.85.2 1900 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef11850 UDPv4 10.0.85.2 138 * 0 4 System 2023-05-21 22:40:16.000000
0xad818ef119e0 UDPv4 127.0.0.1 1900 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef13150 UDPv4 10.0.85.2 55914 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef132e0 UDPv4 127.0.0.1 55915 * 0 3004 svchost.exe 2023-05-21 22:40:16.000000
0xad818ef77b40 TCPv4 192.168.190.141 55176 192.168.190.2 53 CLOSED 1448 svchost.exe 2023-05-21 23:01:39.000000
0xad818f88cc80 UDPv4 0.0.0.0 5355 * 0 1448 svchost.exe 2023-05-21 23:01:26.000000
0xad818f88cc80 UDPv6 :: 5355 * 0 1448 svchost.exe 2023-05-21 23:01:26.000000
0xad818f894340 UDPv4 0.0.0.0 5355 * 0 1448 svchost.exe 2023-05-21 23:01:26.000000
0xad8190dd8800 UDPv4 0.0.0.0 5353 * 0 1448 svchost.exe 2023-05-21 23:01:25.000000
0xad8190dd8800 UDPv6 :: 5353 * 0 1448 svchost.exe 2023-05-21 23:01:25.000000
0xad8190dd8990 UDPv4 0.0.0.0 5353 * 0 1448 svchost.exe 2023-05-21 23:01:25.000000
0xad8190dd97a0 UDPv4 0.0.0.0 0 * 0 1448 svchost.exe 2023-05-21 23:01:25.000000
0xad8190dd97a0 UDPv6 :: 0 * 0 1448 svchost.exe 2023-05-21 23:01:25.000000
0xad8190e12b10 UDPv6 fe80::a406:8c42:43a9:413 1900 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e161c0 UDPv6 ::1 1900 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e16e40 UDPv4 192.168.190.141 1900 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e19230 UDPv6 ::1 57094 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e1a1d0 UDPv4 192.168.190.141 57095 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e1a360 UDPv4 127.0.0.1 57096 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e1a680 UDPv4 127.0.0.1 1900 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e1acc0 UDPv6 fe80::a406:8c42:43a9:413 57093 * 0 3004 svchost.exe 2023-05-21 23:01:29.000000
0xad8190e59a60 UDPv4 0.0.0.0 55536 * 0 4628 tun2socks.exe 2023-05-21 23:00:47.000000
0xad8190e59d80 UDPv4 0.0.0.0 56228 * 0 4628 tun2socks.exe 2023-05-21 23:00:38.000000
0xad8190e5b040 UDPv4 0.0.0.0 49734 * 0 4628 tun2socks.exe 2023-05-21 23:00:41.000000
Descripción del proceso tun2socks.exe y su uso
El proceso tun2socks.exe es una utilidad utilizada principalmente en entornos VPN y proxy. Su función principal es redirigir el tráfico de red desde una interfaz TUN/TAP a través de un proxy SOCKS. A continuación, se detalla más información sobre su funcionamiento y usos:
¿Qué es tun2socks.exe?
tun2socks.exe es una herramienta que permite redirigir el tráfico de red de una interfaz de red virtual (TUN/TAP) a través de un proxy SOCKS. Es parte del proyecto «The SoftEther VPN Project» y es utilizado comúnmente para encapsular el tráfico de red de una VPN a través de un proxy SOCKS5, lo cual puede ser útil en situaciones donde se necesita ocultar la conexión VPN detrás de un proxy o cuando se requiere superar restricciones de red impuestas por cortafuegos.
¿Para qué se usa tun2socks.exe?
- Encapsulación de tráfico VPN:
tun2socks.exese usa para redirigir el tráfico de una conexión VPN a través de un proxy SOCKS. Esto es útil en situaciones donde se necesita superar restricciones de red o se desea añadir una capa adicional de anonimato. - Superar restricciones de red: Al encapsular el tráfico VPN a través de un proxy SOCKS, es posible evitar cortafuegos o restricciones de red que bloquean las conexiones VPN directas.
- Anonimato y privacidad: Redirigir el tráfico a través de un proxy SOCKS puede proporcionar una capa adicional de anonimato, ya que la dirección IP real del usuario queda oculta detrás del proxy.
- Compatibilidad con aplicaciones: Algunas aplicaciones pueden no soportar directamente conexiones VPN, pero sí pueden configurarse para usar un proxy SOCKS.
tun2socks.exepermite que estas aplicaciones se beneficien de la protección de una VPN redirigiendo su tráfico a través del proxy.
Tras conseguir el proceso tun2socks.exe, ejecutamos el comando windows.pstree para obtener el árbol de procesos y determinar el proceso padre. El comando es el siguiente:
vol -f MemoryDump.mem windows.pstree Output:
Volatility 3 Framework 2.7.1
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
4 0 System 0xad8185883180 157 - N/A False 2023-05-21 22:27:10.000000 N/A - - -
* 1280 4 MemCompression 0xad8187835080 62 - N/A False 2023-05-21 22:27:49.000000 N/A MemCompression - -
* 108 4 Registry 0xad81858f2080 4 - N/A False 2023-05-21 22:26:54.000000 N/A Registry - -
* 332 4 smss.exe 0xad81860dc040 2 - N/A False 2023-05-21 22:27:10.000000 N/A \Device\HarddiskVolume3\Windows\System32\smss.exe - -
452 444 csrss.exe 0xad81861cd080 12 - 0 False 2023-05-21 22:27:22.000000 N/A \Device\HarddiskVolume3\Windows\System32\csrss.exe - -
528 520 csrss.exe 0xad8186f1b140 14 - 1 False 2023-05-21 22:27:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\csrss.exe
552 444 wininit.exe 0xad8186f2b080 1 - 0 False 2023-05-21 22:27:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\wininit.exe - -
* 696 552 lsass.exe 0xad8186fc6080 10 - 0 False 2023-05-21 22:27:29.000000 N/A \Device\HarddiskVolume3\Windows\System32\lsass.exe C:\Windows\system32\lsass.exe C:\Windows\system32\lsass.exe
* 676 552 services.exe 0xad8186f4d080 7 - 0 False 2023-05-21 22:27:29.000000 N/A \Device\HarddiskVolume3\Windows\System32\services.exe C:\Windows\system32\services.exe C:\Windows\system32\services.exe
** 4228 676 SearchIndexer. 0xad818ce06240 15 - 0 False 2023-05-21 22:31:27.000000 N/A \Device\HarddiskVolume3\Windows\System32\SearchIndexer.exe C:\Windows\system32\SearchIndexer.exe /Embedding C:\Windows\system32\SearchIndexer.exe
** 8708 676 svchost.exe 0xad818d431080 5 - 0 False 2023-05-21 22:57:33.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 5136 676 SecurityHealth 0xad818d374280 7 - 0 False 2023-05-21 22:32:01.000000 N/A \Device\HarddiskVolume3\Windows\System32\SecurityHealthService.exe - -
** 2200 676 VGAuthService. 0xad81896b3300 2 - 0 False 2023-05-21 22:28:19.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe - -
** 3608 676 svchost.exe 0xad818d07a080 3 - 0 False 2023-05-21 22:41:28.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 2076 676 svchost.exe 0xad8187b94080 10 - 0 False 2023-05-21 22:28:19.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k utcsvc -p C:\Windows\System32\svchost.exe
** 1448 676 svchost.exe 0xad818796c2c0 30 - 0 False 2023-05-21 22:27:52.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p C:\Windows\System32\svchost.exe
** 1064 676 svchost.exe 0xad8189d7c2c0 15 - 1 False 2023-05-21 22:30:09.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k UnistackSvcGroup C:\Windows\system32\svchost.exe
** 6696 676 svchost.exe 0xad818c532080 8 - 0 False 2023-05-21 22:34:07.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 1196 676 svchost.exe 0xad81877972c0 34 - 0 False 2023-05-21 22:27:46.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p C:\Windows\system32\svchost.exe
** 1840 676 spoolsv.exe 0xad8187acb200 10 - 0 False 2023-05-21 22:28:03.000000 N/A \Device\HarddiskVolume3\Windows\System32\spoolsv.exe - -
** 952 676 svchost.exe 0xad81876802c0 12 - 0 False 2023-05-21 22:27:36.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k RPCSS -p C:\Windows\system32\svchost.exe
** 824 676 svchost.exe 0xad818761d240 22 - 0 False 2023-05-21 22:27:32.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch -p C:\Windows\system32\svchost.exe
*** 7312 824 ApplicationFra 0xad818e84f300 10 - 1 False 2023-05-21 22:35:44.000000 N/A \Device\HarddiskVolume3\Windows\System32\ApplicationFrameHost.exe C:\Windows\system32\ApplicationFrameHost.exe -Embedding C:\Windows\system32\ApplicationFrameHost.exe
*** 4116 824 RuntimeBroker. 0xad818cd93300 3 - 1 False 2023-05-21 22:31:24.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe - -
*** 5656 824 RuntimeBroker. 0xad81876e8080 0 - 1 False 2023-05-21 21:58:19.000000 2023-05-21 22:02:01.000000 \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe - -
*** 2332 824 TiWorker.exe 0xad818e780080 4 - 0 False 2023-05-21 22:58:13.000000 N/A \Device\HarddiskVolume3\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.1940_none_7dd80d767cb5c7b0\TiWorker.exe --
*** 7336 824 RuntimeBroker. 0xad818e8bb080 2 - 1 False 2023-05-21 22:11:39.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe - -
*** 5808 824 HxTsr.exe 0xad818de5d080 0 - 1 False 2023-05-21 21:59:58.000000 2023-05-21 22:07:45.000000 \Device\HarddiskVolume3\Program Files\WindowsApps\microsoft.windowscommunicationsapps_16005.11629.20316.0_x64__8wekyb3d8bbwe\HxTsr.exe - -
*** 7160 824 SearchApp.exe 0xad818ccc4080 57 - 1 False 2023-05-21 22:39:13.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe - -
*** 6076 824 ShellExperienc 0xad818eb18080 14 - 1 False 2023-05-21 22:11:36.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe - -
*** 5704 824 RuntimeBroker. 0xad8185962080 5 - 1 False 2023-05-21 22:32:44.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 8264 824 RuntimeBroker. 0xad818eec8080 4 - 1 False 2023-05-21 22:40:33.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe - -
*** 3160 824 StartMenuExper 0xad818cad3240 14 - 1 False 2023-05-21 22:31:21.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe "C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe
*** 4448 824 RuntimeBroker. 0xad818c09a080 9 - 1 False 2023-05-21 22:31:33.000000 N/A \Device\HarddiskVolume3\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 1764 824 dllhost.exe 0xad818d176080 7 - 1 False 2023-05-21 22:32:48.000000 N/A \Device\HarddiskVolume3\Windows\System32\dllhost.exe
*** 3944 824 WmiPrvSE.exe 0xad818c054080 13 - 0 False 2023-05-21 22:30:44.000000 N/A \Device\HarddiskVolume3\Windows\System32\wbem\WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe C:\Windows\system32\wbem\wmiprvse.exe
*** 6644 824 SkypeApp.exe 0xad818d3ac080 49 - 1 False 2023-05-21 22:41:52.000000 N/A \Device\HarddiskVolume3\Program Files\WindowsApps\Microsoft.SkypeApp_14.53.77.0_x64__kzf8qxf38zg5c\SkypeApp.exe - -
*** 372 824 SkypeBackgroun 0xad8186f49080 3 - 1 False 2023-05-21 22:10:00.000000 N/A \Device\HarddiskVolume3\Program Files\WindowsApps\Microsoft.SkypeApp_14.53.77.0_x64__kzf8qxf38zg5c\SkypeBackgroundHost.exe - -
*** 7540 824 smartscreen.ex 0xad818e893080 14 - 1 False 2023-05-21 23:02:26.000000 N/A \Device\HarddiskVolume3\Windows\System32\smartscreen.exe C:\Windows\System32\smartscreen.exe -Embedding C:\Windows\System32\smartscreen.exe
*** 8952 824 TextInputHost. 0xad818e6db080 10 - 1 False 2023-05-21 21:59:11.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe "C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe
*** 1916 824 SearchApp.exe 0xad818d099080 24 - 1 False 2023-05-21 22:33:05.000000 N/A \Device\HarddiskVolume3\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe - -
** 6200 676 SgrmBroker.exe 0xad818d09f080 7 - 0 False 2023-05-21 22:33:42.000000 N/A \Device\HarddiskVolume3\Windows\System32\SgrmBroker.exe - -
** 3004 676 svchost.exe 0xad818c4212c0 7 - 0 False 2023-05-21 22:30:55.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation -p C:\Windows\system32\svchost.exe
** 448 676 svchost.exe 0xad8187721240 54 - 0 False 2023-05-21 22:27:41.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p C:\Windows\system32\svchost.exe
*** 1600 448 taskhostw.exe 0xad8189d07300 10 - 1 False 2023-05-21 22:30:09.000000 N/A \Device\HarddiskVolume3\Windows\System32\taskhostw.exe - -
*** 6048 448 taskhostw.exe 0xad818dc5d080 5 - 1 False 2023-05-21 22:40:20.000000 N/A \Device\HarddiskVolume3\Windows\System32\taskhostw.exe - -
*** 3876 448 taskhostw.exe 0xad8189b30080 8 - 1 False 2023-05-21 22:08:02.000000 N/A \Device\HarddiskVolume3\Windows\System32\taskhostw.exe - -
*** 5480 448 oneetx.exe 0xad818d3d6080 6 - 1 True 2023-05-21 23:03:00.000000 N/A \Device\HarddiskVolume3\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe - -
*** 1392 448 sihost.exe 0xad8189e94280 11 - 1 False 2023-05-21 22:30:08.000000 N/A \Device\HarddiskVolume3\Windows\System32\sihost.exe sihost.exe C:\Windows\system32\sihost.exe
** 832 676 msdtc.exe 0xad8185861280 9 - 0 False 2023-05-21 22:29:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\msdtc.exe - -
** 6596 676 TrustedInstall 0xad818dc88080 4 - 0 False 2023-05-21 22:58:13.000000 N/A \Device\HarddiskVolume3\Windows\servicing\TrustedInstaller.exe - -
** 5964 676 svchost.exe 0xad818ef86080 5 - 0 False 2023-05-21 22:27:56.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 1232 676 svchost.exe 0xad8186f4a2c0 7 - 0 False 2023-05-21 22:29:39.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 3028 676 dllhost.exe 0xad8185907080 12 - 0 False 2023-05-21 22:29:20.000000 N/A \Device\HarddiskVolume3\Windows\System32\dllhost.exe C:\Windows\system32\dllhost.exe /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235} C:\Windows\system32\dllhost.exe
** 1496 676 svchost.exe 0xad81879752c0 12 - 0 False 2023-05-21 22:27:52.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
*** 6324 1496 audiodg.exe 0xad818df2e080 4 - 0 False 2023-05-21 22:42:56.000000 N/A \Device\HarddiskVolume3\Windows\System32\audiodg.exe - -
** 1116 676 svchost.exe 0xad818c426080 6 - 1 False 2023-05-21 22:31:00.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k ClipboardSvcGroup -p C:\Windows\system32\svchost.exe
** 7772 676 svchost.exe 0xad818e88e140 3 - 0 False 2023-05-21 22:36:03.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 1376 676 svchost.exe 0xad81878020c0 15 - 0 False 2023-05-21 22:27:49.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork -p C:\Windows\system32\svchost.exe
** 2144 676 vmtoolsd.exe 0xad81896ab080 11 - 0 False 2023-05-21 22:28:19.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\vmtoolsd.exe "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
** 1120 676 MsMpEng.exe 0xad818945c080 12 - 0 False 2023-05-21 22:10:01.000000 N/A \Device\HarddiskVolume3\ProgramData\Microsoft\Windows Defender\Platform\4.18.2304.8-0\MsMpEng.exe
** 1892 676 svchost.exe 0xad8187b34080 14 - 0 False 2023-05-21 22:28:05.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetworkFirewall -p C:\Windows\system32\svchost.exe
** 5476 676 svchost.exe 0xad818e752080 9 - 0 False 2023-05-21 22:58:08.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p C:\Windows\System32\svchost.exe
** 2024 676 svchost.exe 0xad8187b65240 7 - 0 False 2023-05-21 22:28:11.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 2152 676 vm3dservice.ex 0xad81896ae240 2 - 0 False 2023-05-21 22:28:19.000000 N/A \Device\HarddiskVolume3\Windows\System32\vm3dservice.exe - -
*** 2404 2152 vm3dservice.ex 0xad8186619200 2 - 1 False 2023-05-21 22:28:32.000000 N/A \Device\HarddiskVolume3\Windows\System32\vm3dservice.exe - -
** 1644 676 svchost.exe 0xad8187a112c0 6 - 0 False 2023-05-21 22:27:58.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe - -
** 752 676 svchost.exe 0xad8187758280 21 - 0 False 2023-05-21 22:27:43.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p C:\Windows\System32\svchost.exe
*** 3204 752 ctfmon.exe 0xad8189c8b280 12 - 1 False 2023-05-21 22:30:11.000000 N/A \Device\HarddiskVolume3\Windows\System32\ctfmon.exe "ctfmon.exe" C:\Windows\system32\ctfmon.exe
** 1012 676 svchost.exe 0xad818774c080 19 - 0 False 2023-05-21 22:27:43.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
** 1652 676 svchost.exe 0xad8187a2d2c0 10 - 0 False 2023-05-21 22:27:58.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\system32\svchost.exe
** 4340 676 VSSVC.exe 0xad818e888080 3 - 0 False 2023-05-21 23:01:06.000000 N/A \Device\HarddiskVolume3\Windows\System32\VSSVC.exe C:\Windows\system32\vssvc.exe C:\Windows\system32\vssvc.exe
** 2044 676 svchost.exe 0xad8189b27080 28 - 0 False 2023-05-21 22:49:29.000000 N/A \Device\HarddiskVolume3\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k wsappx -p C:\Windows\system32\svchost.exe
* 852 552 fontdrvhost.ex 0xad818761b0c0 5 - 0 False 2023-05-21 22:27:33.000000 N/A \Device\HarddiskVolume3\Windows\System32\fontdrvhost.exe - -
588 520 winlogon.exe 0xad8186f450c0 5 - 1 False 2023-05-21 22:27:25.000000 N/A \Device\HarddiskVolume3\Windows\System32\winlogon.exe - -
* 1016 588 dwm.exe 0xad81876e4340 15 - 1 False 2023-05-21 22:27:38.000000 N/A \Device\HarddiskVolume3\Windows\System32\dwm.exe "dwm.exe" C:\Windows\system32\dwm.exe
* 3556 588 userinit.exe 0xad818c02f340 0 - 1 False 2023-05-21 22:30:28.000000 2023-05-21 22:30:43.000000 \Device\HarddiskVolume3\Windows\System32\userinit.exe - -
** 3580 3556 explorer.exe 0xad818c047340 76 - 1 False 2023-05-21 22:30:28.000000 N/A \Device\HarddiskVolume3\Windows\explorer.exe C:\Windows\Explorer.EXE C:\Windows\Explorer.EXE
*** 6724 3580 Outline.exe 0xad818e578080 0 - 1 True 2023-05-21 22:36:09.000000 2023-05-21 23:01:24.000000 \Device\HarddiskVolume3\Program Files (x86)\Outline\Outline.exe - -
**** 4224 6724 Outline.exe 0xad818e88b080 0 - 1 True 2023-05-21 22:36:23.000000 2023-05-21 23:01:24.000000 \Device\HarddiskVolume3\Program Files (x86)\Outline\Outline.exe - -
**** 4628 6724 tun2socks.exe 0xad818de82340 0 - 1 True 2023-05-21 22:40:10.000000 2023-05-21 23:01:24.000000 \Device\HarddiskVolume3\Program Files (x86)\Outline\resources\app.asar.unpacked\third_party\outline-go-tun2socks\win32\tun2socks.exe - -
*** 5636 3580 notepad.exe 0xad818db45080 1 - 1 False 2023-05-21 22:46:50.000000 N/A \Device\HarddiskVolume3\Windows\System32\notepad.exe - -
*** 464 3580 SecurityHealth 0xad818979d080 3 - 1 False 2023-05-21 22:31:59.000000 N/A \Device\HarddiskVolume3\Windows\System32\SecurityHealthSystray.exe - -
*** 5328 3580 msedge.exe 0xad818d0980c0 54 - 1 False 2023-05-21 22:32:02.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start /prefetch:5 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 4544 5328 msedge.exe 0xad818d75b080 14 - 1 False 2023-05-21 22:32:39.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 8896 5328 msedge.exe 0xad8187a39080 18 - 1 False 2023-05-21 22:28:21.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 5156 5328 msedge.exe 0xad818c553080 14 - 1 False 2023-05-21 22:28:22.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 7964 5328 msedge.exe 0xad818dee5080 19 - 1 False 2023-05-21 22:22:09.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 4396 5328 msedge.exe 0xad818d515080 7 - 1 False 2023-05-21 22:32:19.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 6544 5328 msedge.exe 0xad818c0ea080 18 - 1 False 2023-05-21 22:22:35.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 2388 5328 msedge.exe 0xad818e54c340 18 - 1 False 2023-05-21 22:05:35.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 6292 5328 msedge.exe 0xad818d7a1080 20 - 1 False 2023-05-21 22:06:15.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 1144 5328 msedge.exe 0xad818d75f080 18 - 1 False 2023-05-21 22:32:38.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
**** 5340 5328 msedge.exe 0xad818d7b3080 10 - 1 False 2023-05-21 22:32:39.000000 N/A \Device\HarddiskVolume3\Program Files (x86)\Microsoft\Edge\Application\msedge.exe - -
*** 3252 3580 vmtoolsd.exe 0xad8189796300 8 - 1 False 2023-05-21 22:31:59.000000 N/A \Device\HarddiskVolume3\Program Files\VMware\VMware Tools\vmtoolsd.exe "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
*** 2228 3580 FTK Imager.exe 0xad818d143080 10 - 1 False 2023-05-21 22:43:56.000000 N/A \Device\HarddiskVolume3\Program Files\AccessData\FTK Imager\FTK Imager.exe - -
*** 8920 3580 FTK Imager.exe 0xad818ef81080 20 - 1 False 2023-05-21 23:02:28.000000 N/A \Device\HarddiskVolume3\Program Files\AccessData\FTK Imager\FTK Imager.exe "C:\Program Files\AccessData\FTK Imager\FTK Imager.exe" C:\Program Files\AccessData\FTK Imager\FTK Imager.exe
* 860 588 fontdrvhost.ex 0xad818761f140 5 - 1 False 2023-05-21 22:27:33.000000 N/A \Device\HarddiskVolume3\Windows\System32\fontdrvhost.exe - -
5896 8844 oneetx.exe 0xad8189b41080 5 - 1 True 2023-05-21 22:30:56.000000 N/A \Device\HarddiskVolume3\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe - -
* 7732 5896 rundll32.exe 0xad818d1912c0 1 - 1 True 2023-05-21 22:31:53.000000 N/A \Device\HarddiskVolume3\Windows\SysWOW64\rundll32.exe - -
El proceso tun2socks.exe (PID 1234) es hijo del proceso Outline.exe (PID 6724).
#5 Respuesta: 77.91.124.20
What is the attacker's IP address?Obtención de la evidencia
En la pregunta anterior, verificamos que el proceso utilizado por el atacante para conectarse mediante VPN es oneetx.exe. Para comprobar las conexiones, ejecutamos el siguiente comando:
vol -f MemoryDump.mem windows.netscan.NetScan | grep oneetx.exeOutput
0xad818de4aa20.0TCPv4 10.0.85.2DB scan55462fin77.91.124.20 80 CLOSED 5896 oneetx.exe 2023-05-21 23:01:22.000000
0xad818e4a6900 UDPv4 0.0.0.0 0 * 0 5480 oneetx.exe 2023-05-21 22:39:47.000000
0xad818e4a6900 UDPv6 :: 0 * 0 5480 oneetx.exe 2023-05-21 22:39:47.000000
0xad818e4a9650 UDPv4 0.0.0.0 0 * 0 5480 oneetx.exe 2023-05-21 22:39:47.000000 Como podemos observar, el proceso oneetx.exe tiene una conexión cerrada desde la dirección IP 77.91.124.20.
#6 Respuesta: RedLine Stealer
Obtención de la evidencia
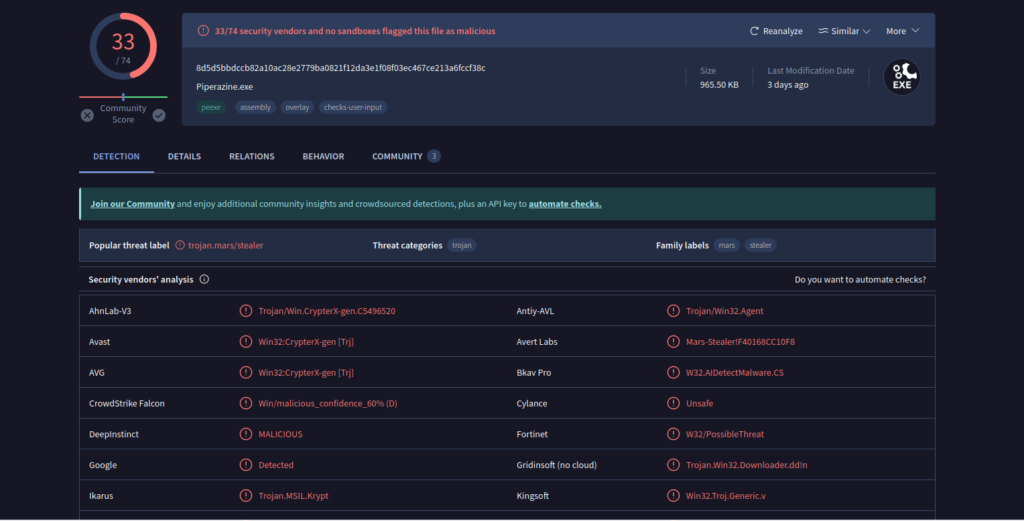
En la pregunta #1, pudimos comprobar que se trataba de un malware Trojan.Mars/Stealer.
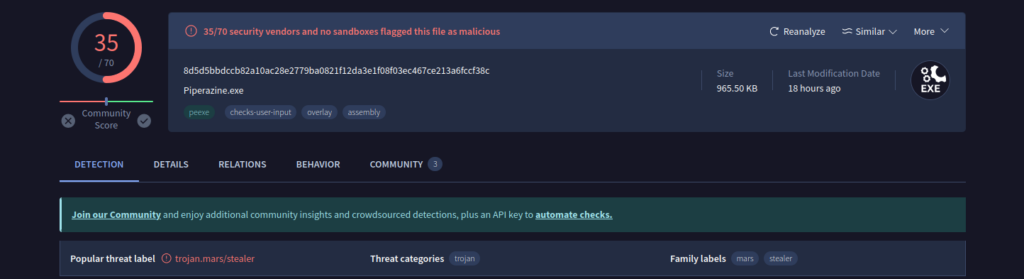
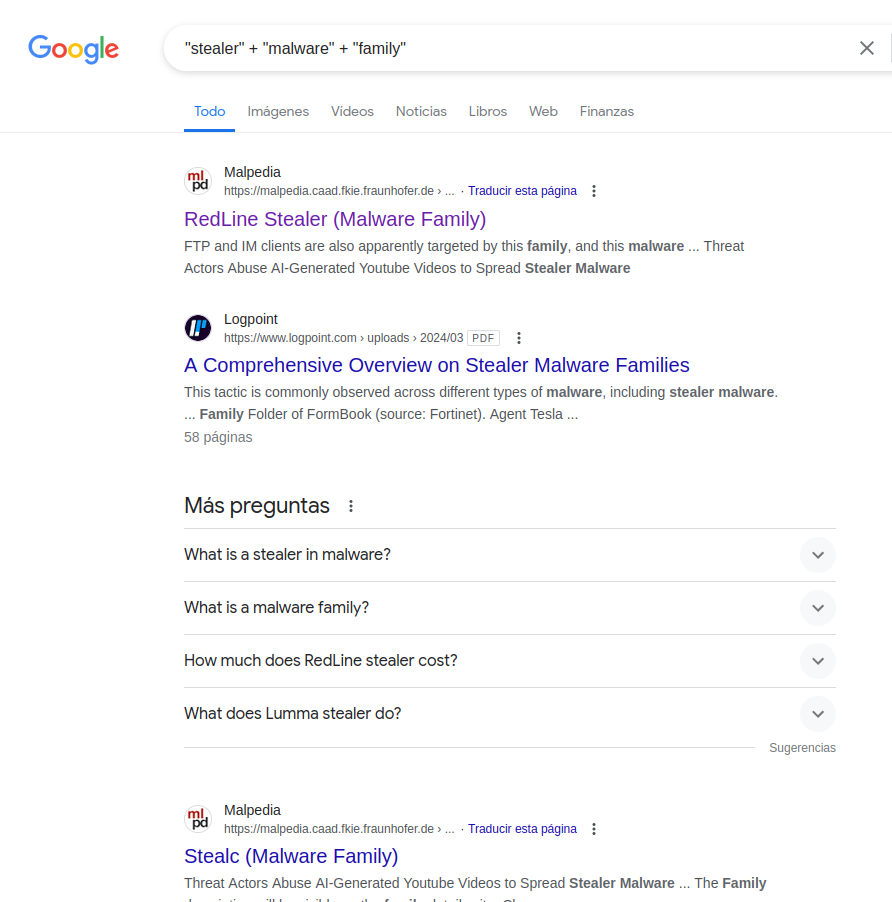
Buscando en internet por «stealer» + «malware» + «family», pude encontrar información sobre el nombre de la familia.
#7 Respuesta: http://77.91.124.20/store/games/index.php
What is the full URL of the PHP file that the attacker visited?Obtención de la evidencia
Para determinar el URL completo del archivo PHP visitado por el atacante, se ejecutó el comando strings en el volcado de memoria:
strings MemoryDump.mem | grep http | grep phpOutput:
.phphttp
nf!.http://209.11.244.51/p.php?n=
zalivi.phphttp://%s%s?searchp
https:\/\/new.f0c4.gq\/proc.php?
php http/(
=http://gbfhju.com/r.php></
https://thl9.tk/office-dream.php',
https://msn.com https://msn.com https://hbx.media.net/cksync.php?type=nms&cs=3&ovsid=2159D74C474D6B9A2450C45B46E76A80&gdpr=0&gdpr_consent=
, "http://9ygw2.com/iz5/yaca.php
://spr-updates.ddns.net/spr_updates.php"-q-nhttp://spr-updates.ddns.net/spr_updates.php-o
https://www.ludashi.com/cms/server/monitor.php?id=
o.ru/index.php", falsemyhttps.se
php http/(
/gate.php|http://
.php[]http:/y
http://dongtaiwang.com/loc/phome.php?v=
http://dongtaiwang.com/loc/phome.php?v=
=http://gbfhju.com/r.php></
http://skdjui.com/r.php>
https://thl9.tk/office-dream.php',
n/x-httpd-php.
m/new.phphttp://blacktraff
http://77.91.124.20/store/games/index.php
php http/(
2src="http://%s/js.php?affid
x-httpd-php .jp
.php http/1.1
lehttp://9bgnq.com/iz5/yaca.php
http://skdjui.com/r.php>
.php[]http:/y
http://dongtaiwang.com/loc/phome.php?v=
http://dongtaiwang.com/loc/phome.php?v=
2src="http://%s/js.php?affid
http://77.91.124.20/store/games/index.php
http://77.91.124.20/store/games/index.php
/gate.php|http://
.php http/1.1
.phphttp://lskdfjlerjvm.com/arm3
=http://gbfhju.com/r.php></
http://skdjui.com/r.php>
66.246.38.\system32\config\samto: haxorklog.sys\win.comntdetect.comwww.prodexteam.netcorpse@mailserver.ruget /aserver.php?id=%s¶m=%u http/1.1software\microsoft\windows nt\currentversion\winlogon\notify\pdxsoftware\microsoft\windows\currentversion\app paths\7-zipcfg.exesoftware\microsoft\windows\currentversion\app paths\winrar.exe
http://yuoiop.info/rd/rd.phphttp://nanoatom.info/rd/rd.php{8d5849a2-93f3-429d-ff34-260a2068897c}Entre las múltiples líneas de salida, se identificó una entrada que coincide con la dirección IP del atacante:
http://77.91.124.20/store/games/index.phpEsta URL corresponde al archivo PHP que utilizo el atacante
#8 Respuesta: C:\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe
What is the full path of the malicious executable?Obtención de la evidencia
En la pregunta anterior, verificamos que el proceso utilizado por el atacante para conectarse mediante VPN es oneetx.exe. filtramos por el proceso malicioso oneetx.exe
vol -f MemoryDump.mem windows.pstree | grep oneetx.exeOutput
*** 5480: 100.0448 oneetx.exeB scan0xad818d3d6080 6 - 1 True 2023-05-21 23:03:00.000000 N/A \Device\HarddiskVolume3\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe - -
5896 8844 oneetx.exe 0xad8189b41080 5 - 1 True 2023-05-21 22:30:56.000000 N/A \Device\HarddiskVolume3\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe - -Como podemos observar en la salida, la ruta del ejecutable es «\Device\HarddiskVolume3\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe».
:wq!
