Hace tiempo que no subo nada de Azure sentinel, en esta ocasión veremos como parsear los logs de Powershell en Azure Sentinel
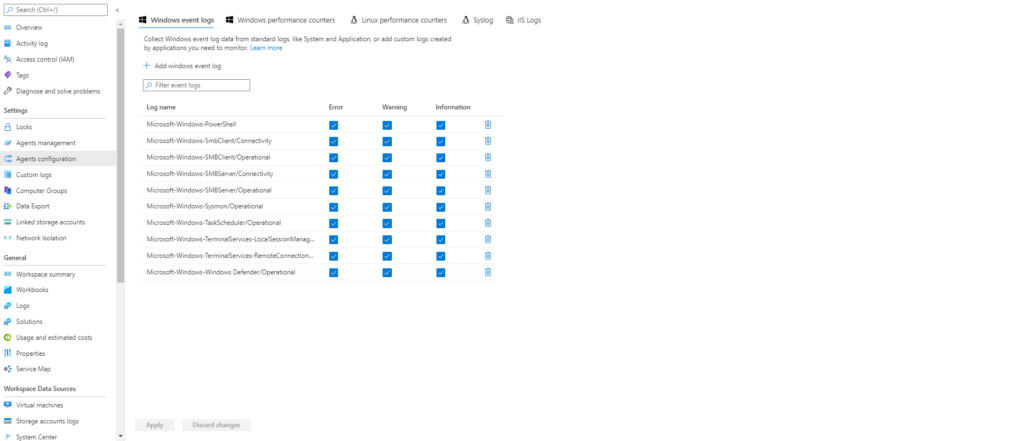
En primer lugar agregamos Azure Sentinel > Settings > Workspace Settings > y dentro de la sección de Settings presionamos sobre Agents configuration
Dentro de ahí damos a: Add windows event logs y seleccionamos Microsoft-Windows-PowerShell
Para agregar la funcion tenemos que irnos Azure Sentinel > Logs y ejecutamos la query: (powershell_parser.kql)
let EventData = Event
| where Source == "Microsoft-Windows-PowerShell"
| extend RenderedDescription = tostring(split(RenderedDescription, ":")[0])
| project TimeGenerated,
Source,
EventID,
Computer,
UserName,
EventData,
RenderedDescription
| extend EvData = parse_xml(EventData)
| extend EventDetail = EvData.DataItem.EventData.Data
| project-away EventData,
EvData;
let POWERSHELL_PIPELINE_4103=() {
let processEvents = EventData
| where EventID == 4103
| extend Lines = split(EventDetail.[0].["#text"], " ")
| extend Severity = split(Lines.[0], "=").[1]
| extend HostName = split(Lines.[1], "=").[1]
| extend HostVersion = split(Lines.[2], "=").[1]
| extend HostID = split(Lines.[3], "=").[1]
| extend HostApplication = split(Lines.[4], "=").[1]
| extend EngineVersion = split(Lines.[5], "=").[1]
| extend RunspaceID = split(Lines.[6], "=").[1]
| extend PipelineID = split(Lines.[7], "=").[1]
| extend CommandName = split(Lines.[8], "=").[1]
| extend CommandType = split(Lines.[9], "=").[1]
| extend ScriptName = split(Lines.[10], "=").[1]
| extend CommandPath = split(Lines.[11], "=").[1]
| extend SequenceNumber = split(Lines.[12], "=").[1]
| extend User = split(Lines.[13], "=").[1]
| extend ConnectedUser = split(Lines.[14], "=").[1]
| extend ShellID = split(Lines.[15], "=").[1]
| project-away EventDetail, Lines
;
processEvents;
};
let POWERSHELL_REMOTE_COMMAND_4104=() {
let processEvents = EventData
| where EventID == 4104
| extend MessageNumber = EventDetail.[0].["#text"]
| extend MessageTotal = EventDetail.[1].["#text"]
| extend ScriptBlockText = EventDetail.[2].["#text"]
| extend ScriptBlockID = EventDetail.[3].["#text"]
| extend Path = EventDetail.[4].["#text"]
| project-away EventDetail
;
processEvents;
};
(union isfuzzy=true
POWERSHELL_PIPELINE_4103,
POWERSHELL_REMOTE_COMMAND_4104
)
| extend Details = column_ifexists("Details", ""),
RuleName = column_ifexists("RuleName", ""),
PreviousCreationUtcTime=column_ifexists("PreviousCreationUtcTime", ""),
Hashes = column_ifexists("Hashes", ""),
Hash = column_ifexists("Hash", "")
| project TimeGenerated,
Source,
Computer,
UserName,
EventID,
Severity,
HostName,
HostVersion,
HostID,
HostApplication,
EngineVersion,
RunspaceID,
PipelineID,
CommandName,
CommandType,
ScriptName,
CommandPath,
SequenceNumber,
User,
ConnectedUser,
ShellID,
MessageNumber,
MessageTotal,
ScriptBlockText,
ScriptBlockID,
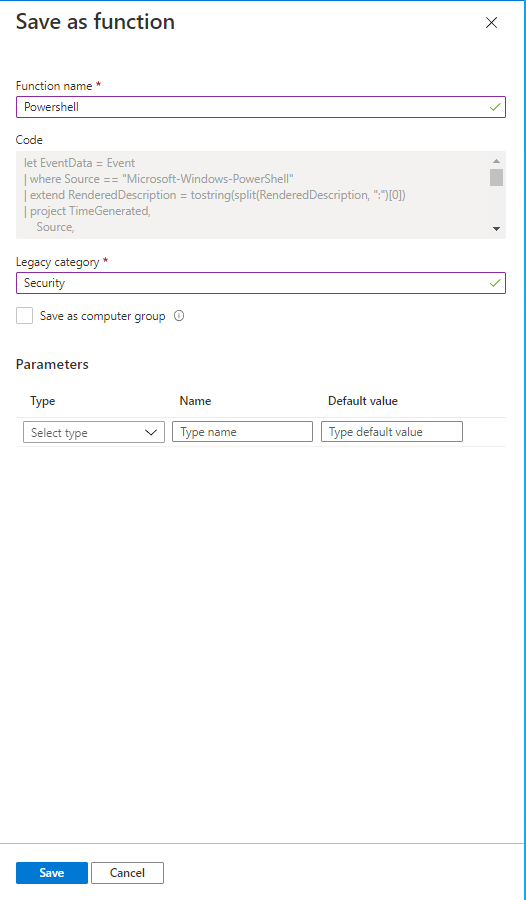
PathGuardamos como Funcion
:wq!