Scenario
Welcome, Defender! As an incident responder, we’re granting you access to the AWS account called «Security» as an IAM user. This account contains a copy of the logs during the time period of the incident and has the ability to assume the «Security» role in the target account so you can look around to spot the misconfigurations that allowed for this attack to happen.
Credentials
Your IAM credentials for the Security account:
- Login: https://flaws2-security.signin.aws.amazon.com/console
- Account ID: 322079859186
- Username: security
- Password: password
- Access Key: AKIAIUFNQ2WCOPTEITJQ
- Secret Key: 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
Environment
The credentials above give you access to the Security account, which can assume the role of «security» in the Target account. You also have access to an S3 bucket, named flaws2_logs, in the Security account, that contains the CloudTrail logs recorded during a successful compromise
La primera pregunta, como en casi todos los retos es de rigor.
#1 Respuesta: aws configure
What is the full AWS CLI command used to configure credentials?
Obtención de la evidencia
aws configure
AWS Access Key ID [None]: AKIAIUFNQ2WCOPTEITJQ
AWS Secret Access Key [None]: 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
Default region name [None]:
Default output format [None]:Mas información
#2 Respuesta: 2018-11-19 20:54:31 UTC
What is the 'creation' date of the bucket 'flaws2-logs'?
Mediante el comando aws s3api listamos todos los buckets
aws s3api list-buckets
{
"Buckets": [
{
"Name": "flaws2-logs",
"CreationDate": "2018-11-19T20:54:31.000Z"
}
],
"Owner": {
"DisplayName": "scott+flaws2_security",
"ID": "0ff467deaf461e549934997a2df02d29c8010173b1464262782d522bce63bf46"
}
}
Mas información
#3 Respuesta: AssumeRole
What is the name of the first generated event -according to time?
Obtención de la evidencia
Nos descargamos todo el contenido del bucket flaws2-logs a nuestro equipo.
aws s3 sync s3://flaws2-logs .
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json.gz
download: s3://flaws2-logs/AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json.gz to AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json.gzAccedemos a la carpeta y descomprimimos todos los archivos
cd AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28
gunzip *.gz
Dado que nos encontramos ante ficheros en formato json instalamos jq para poder tratarlos.
apt install jqVisualizamos uno de los archivos para buscar strings que nos sirva a filtrar la busqueda
cat 653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json | jq '.'
{
"Records": [
{
"eventVersion": "1.05",
"userIdentity": {
"type": "AWSAccount",
"principalId": "",
"accountId": "ANONYMOUS_PRINCIPAL"
},
"eventTime": "2018-11-28T23:09:36Z",
"eventSource": "s3.amazonaws.com",
"eventName": "GetObject",
"awsRegion": "us-east-1",
"sourceIPAddress": "104.102.221.250",
"userAgent": "[Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36]",
"requestParameters": {
"bucketName": "the-end-962b72bjahfm5b4wcktm8t9z4sapemjb.flaws2.cloud",
"key": "index.htm"
},
"responseElements": null,
"additionalEventData": {
"x-amz-id-2": "AeawUxLi2duvWcRYWMuVYUmtCkBuOvHaktUvODIORlnw+U6VbswU9FfeOAEDq9kguRNgMfWRmaw="
},
"requestID": "EDFBFC9CE11E755F",
"eventID": "ea33682d-0829-40c1-9820-bd721b9aede8",
"readOnly": true,
"resources": [
{
"type": "AWS::S3::Object",
"ARN": "arn:aws:s3:::the-end-962b72bjahfm5b4wcktm8t9z4sapemjb.flaws2.cloud/index.htm"
},
{
"accountId": "653711331788",
"type": "AWS::S3::Bucket",
"ARN": "arn:aws:s3:::the-end-962b72bjahfm5b4wcktm8t9z4sapemjb.flaws2.cloud"
}
],
"eventType": "AwsApiCall",
"recipientAccountId": "653711331788",
"sharedEventID": "a59b4ac8-6a51-44ff-ab76-e66f75bd95ce"
},
{
"eventVersion": "1.05",
"userIdentity": {
"type": "AWSAccount",
"principalId": "",
"accountId": "ANONYMOUS_PRINCIPAL"
},
"eventTime": "2018-11-28T23:09:36Z",
"eventSource": "s3.amazonaws.com",
"eventName": "GetObject",
"awsRegion": "us-east-1",
"sourceIPAddress": "104.102.221.250",
"userAgent": "[Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36]",
"requestParameters": {
"bucketName": "the-end-962b72bjahfm5b4wcktm8t9z4sapemjb.flaws2.cloud",
"key": "favicon.ico"
},
"responseElements": null,
"additionalEventData": {
"x-amz-id-2": "tLMpJDK15z1teLvIzReA3N4IMnNATUrOrGfoPS0kxZ27SPTRVbxUtdmmucw3XfEW5XzIzUkrCiU="
},
"requestID": "9880010F3D39F3AC",
"eventID": "dee6f6a3-f18a-40db-a6fd-b96d05502266",
"readOnly": true,
"resources": [
{
"type": "AWS::S3::Object",
"ARN": "arn:aws:s3:::the-end-962b72bjahfm5b4wcktm8t9z4sapemjb.flaws2.cloud/favicon.ico"
},
{
"accountId": "653711331788",
"type": "AWS::S3::Bucket",
"ARN": "arn:aws:s3:::the-end-962b72bjahfm5b4wcktm8t9z4sapemjb.flaws2.cloud"
}
],
"eventType": "AwsApiCall",
"recipientAccountId": "653711331788",
"sharedEventID": "f8c6cdc8-6ec1-4e14-9a0e-f300b16e282e"
}
]
}
Creamos un script que mediante un bucle busque en todos los archivos y filtre por el parámetro EventTime
cat script.sh
#!/bin/bash
FILES="*.json"
for f in $FILES
do
echo "Processing: $f"
cat "$f" | jq '.' | grep eventTime
done
Ejecutamos el script
./script.sh
Processing: 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json
"eventTime": "2018-11-28T22:31:59Z",
"eventTime": "2018-11-28T22:31:59Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json
"eventTime": "2018-11-28T23:03:12Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json
"eventTime": "2018-11-28T23:02:56Z",
"eventTime": "2018-11-28T23:03:08Z",
"eventTime": "2018-11-28T23:03:11Z",
"eventTime": "2018-11-28T23:03:20Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json
"eventTime": "2018-11-28T23:03:50Z",
"eventTime": "2018-11-28T23:03:12Z",
"eventTime": "2018-11-28T23:03:20Z",
"eventTime": "2018-11-28T23:03:13Z",
"eventTime": "2018-11-28T23:05:53Z",
"eventTime": "2018-11-28T23:03:35Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json
"eventTime": "2018-11-28T23:06:17Z",
"eventTime": "2018-11-28T23:06:33Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json
"eventTime": "2018-11-28T23:02:56Z",
"eventTime": "2018-11-28T23:02:56Z",
"eventTime": "2018-11-28T23:02:56Z",
"eventTime": "2018-11-28T23:02:57Z",
"eventTime": "2018-11-28T23:03:08Z",
"eventTime": "2018-11-28T23:03:08Z",
"eventTime": "2018-11-28T23:03:08Z",
"eventTime": "2018-11-28T23:03:08Z",
"eventTime": "2018-11-28T23:03:11Z",
"eventTime": "2018-11-28T23:03:13Z",
"eventTime": "2018-11-28T23:03:14Z",
"eventTime": "2018-11-28T23:03:17Z",
"eventTime": "2018-11-28T23:03:18Z",
"eventTime": "2018-11-28T23:04:54Z",
"eventTime": "2018-11-28T23:05:10Z",
"eventTime": "2018-11-28T23:05:12Z",
"eventTime": "2018-11-28T23:05:12Z",
"eventTime": "2018-11-28T23:07:08Z",
"eventTime": "2018-11-28T23:07:08Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json
"eventTime": "2018-11-28T23:09:28Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json
"eventTime": "2018-11-28T23:09:36Z",
"eventTime": "2018-11-28T23:09:36Z",
Como podemos observar el primer evento que tenemos se encuentra en el fichero 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json. Al procesar el fichero podemos que el nombre del evento es: AssumeRole
"eventTime": "2018-11-28T22:31:59Z",
"eventSource": "sts.amazonaws.com",
"eventName": "AssumeRole",
"awsRegion": "us-east-1",
"sourceIPAddress": "ecs-tasks.amazonaws.com",
"userAgent": "ecs-tasks.amazonaws.com",
"requestParameters": {
"roleSessionName": "d190d14a-2404-45d6-9113-4eda22d7f2c7",
"roleArn": "arn:aws:iam::653711331788:role/ecsTaskExecutionRole"
},
Mas información
#4 Respuesta: 34.234.236.212
What source IP address generated the event dated 2018-11-28 at 23:03:20 UTC?
Obtención de la evidencia
Mediante el mismo script filtramos por la fecha y hora que nos indican.
#!/bin/bash
FILES="*.json"
for f in $FILES
do
echo "Processing: $f"
cat "$f" | jq '.' | grep 2018-11-28T23:03:20
doneEncontramos dos ficheros
./script.sh
Processing: 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json
"eventTime": "2018-11-28T23:03:20Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json
"eventTime": "2018-11-28T23:03:20Z",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.jsonFiltramos en ambos ficheros por la IP y encontramos 104.102.221.250 y 34.234.236.212. Debido a que el formato de la respuesta es: XX.XXX.XXX.XXX podemos deducir que se trata de 34.234.236.212
cat 653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json | jq '.' | grep IP
"accountId": "ANONYMOUS_PRINCIPAL"
"sourceIPAddress": "104.102.221.250",
"accountId": "ANONYMOUS_PRINCIPAL"
"sourceIPAddress": "104.102.221.250",
"accountId": "ANONYMOUS_PRINCIPAL"
"sourceIPAddress": "104.102.221.250",
"sourceIPAddress": "apigateway.amazonaws.com",
cat 653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json | jq '.' | grep IP
"sourceIPAddress": "34.234.236.212",
"sourceIPAddress": "lambda.amazonaws.com",
"sourceIPAddress": "34.234.236.212",
"sourceIPAddress": "34.234.236.212",
"sourceIPAddress": "104.102.221.250",
"sourceIPAddress": "34.234.236.212",
#5 Respuesta: 104.102.221.25
Which IP address does not belong to Amazon AWS infrastructure?
Obtención de la evidencia
Nuevamente mediante nuestro script filtramos por el parámetro sourceIPAddress
cat script.sh
#!/bin/bash
FILES="*.json"
for f in $FILES
do
echo "Processing: $f"
cat "$f" | jq '.' | grep sourceIPAddress | sort -u
done
Como en la anterior pregunta únicamente encontramos las direcciones IP’s 104.102.221.250 y 34.234.236.212
./script.sh
Processing: 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json
"sourceIPAddress": "ecs-tasks.amazonaws.com",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json
"sourceIPAddress": "34.234.236.212",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json
"sourceIPAddress": "104.102.221.250",
"sourceIPAddress": "apigateway.amazonaws.com",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json
"sourceIPAddress": "104.102.221.250",
"sourceIPAddress": "34.234.236.212",
"sourceIPAddress": "lambda.amazonaws.com",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json
"sourceIPAddress": "104.102.221.250",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json
"sourceIPAddress": "104.102.221.250",
"sourceIPAddress": "apigateway.amazonaws.com",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json
"sourceIPAddress": "104.102.221.250",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json
"sourceIPAddress": "104.102.221.250"Comprobamos mediante https://ipdata.co/ que la dirección ip 34.234.236.212 pertenece a Amazon y 104.102.221.25 a Akamai
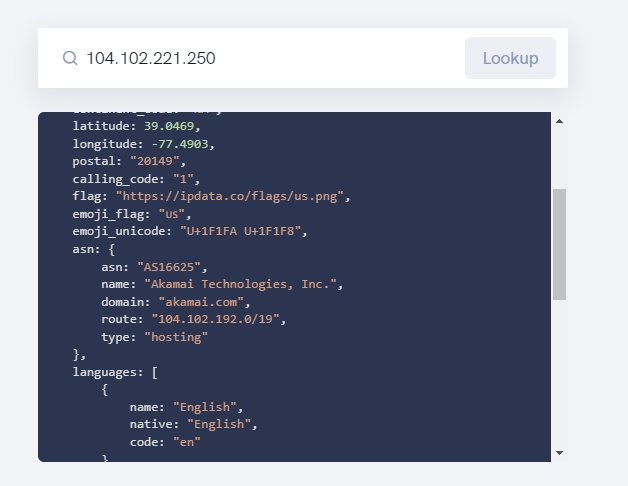
#6 Respuesta: level3
Which user issued the 'ListBuckets' request?
Obtención de la evidencia
Si…otra vez el mismo script filtramos por ListBuckets
#!/bin/bash
FILES="*.json"
for f in $FILES
do
echo "Processing: $f"
cat "$f" | jq '.' | grep ListBuckets
done
Encontramos un fichero
./script.sh
Processing: 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json
"eventName": "ListBuckets",
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json
Abrimos el fichero y observamos que nuestro usuario se trata de: level3
cat 653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json | jq '.'
{
"Records": [
{
"eventVersion": "1.05",
"userIdentity": {
"type": "AssumedRole",
"principalId": "AROAJQMBDNUMIKLZKMF64:d190d14a-2404-45d6-9113-4eda22d7f2c7",
"arn": "arn:aws:sts::653711331788:assumed-role/level3/d190d14a-2404-45d6-9113-4eda22d7f2c7",
"accountId": "653711331788",
"accessKeyId": "ASIAZQNB3KHGNXWXBSJS",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false",
"creationDate": "2018-11-28T22:31:59Z"
},
"sessionIssuer": {
"type": "Role",
"principalId": "AROAJQMBDNUMIKLZKMF64",
"arn": "arn:aws:iam::653711331788:role/level3",
"accountId": "653711331788",
"userName": "level3"
}
}
},
"eventTime": "2018-11-28T23:09:28Z",
"eventSource": "s3.amazonaws.com",
"eventName": "ListBuckets",
"awsRegion": "us-east-1",
"sourceIPAddress": "104.102.221.250",
"userAgent": "[aws-cli/1.16.19 Python/2.7.10 Darwin/17.7.0 botocore/1.12.9]",
"requestParameters": null,
"responseElements": null,
"requestID": "4698593B9338B27F",
"eventID": "65e111a0-83ae-4ba8-9673-16291a804873",
"eventType": "AwsApiCall",
"recipientAccountId": "653711331788"
}
]
}
#7 Respuesta: CreateLogStream
What was the first request issued by the user 'level1'?
Obtención de la evidencia
Una vez mas con el mismo script pero filtrando por el string level1
cat script.sh
#!/bin/bash
FILES="*.json"
for f in $FILES
do
echo "Processing: $f"
cat "$f" | jq '.' | grep '"userName": "level1"' | sort -u
done
Encontramos 4 ficheros
./script.sh
Processing: 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json
"userName": "level1"
Processing: 653711331788_CloudTrail_us-east-1_20181128T2305Z_zKlMhON7EpHala9u.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_7J9NEIxrjJsrlXSd.json
"userName": "level1"
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_A1lhv3sWzzRIBFVk.json
"userName": "level1"
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jJW5HfNtz7kOnvcP.json
"userName": "level1"
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_jQajCuiobojD8I4y.json
Processing: 653711331788_CloudTrail_us-east-1_20181128T2310Z_rp9i9zxR2Vcpqfnz.json
Verificando la fecha y la hora de las solicitudes emitidas por el usuario level1 vemos que su primera solicitud se trata de CreateLogStream
cat 653711331788_CloudTrail_us-east-1_20181128T2305Z_83VTWZ8Z0kiEC7Lq.json | jq '.'
{
"Records": [
{
"eventVersion": "1.04",
"userIdentity": {
"type": "AssumedRole",
"principalId": "AROAIBATWWYQXZTTALNCE:level1",
"arn": "arn:aws:sts::653711331788:assumed-role/level1/level1",
"accountId": "653711331788",
"accessKeyId": "ASIAZQNB3KHGIGYQXVVG",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false",
"creationDate": "2018-11-28T23:03:12Z"
},
"sessionIssuer": {
"type": "Role",
"principalId": "AROAIBATWWYQXZTTALNCE",
"arn": "arn:aws:iam::653711331788:role/service-role/level1",
"accountId": "653711331788",
"userName": "level1"
}
}
},
"eventTime": "2018-11-28T23:03:12Z",
"eventSource": "logs.amazonaws.com",
"eventName": "CreateLogStream",
"awsRegion": "us-east-1",
"sourceIPAddress": "34.234.236.212",
"userAgent": "awslambda-worker",
"errorCode": "AccessDenied",
"errorMessage": "User: arn:aws:sts::653711331788:assumed-role/level1/level1 is not authorized to perform: logs:CreateLogStream on resource: arn:aws:logs:us-east-1:653711331788:log-group:/aws/lambda/level1:log-stream:2018/11/28/[$LATEST]2d75b45ba94f495598fd2fed9f3ca60e",
"requestParameters": null,
"responseElements": null,
"requestID": "c80afb02-f361-11e8-b660-f9fa07f60344",
"eventID": "77b02a51-70c8-465b-94df-579c1fe42a5c",
"eventType": "AwsApiCall",
"recipientAccountId": "653711331788"
}
]
}
:wq!
