En esta ocasión nos pasamos al bando azul y vamos a intentar resolver el primer reto que tenemos de Splunk en https://cyberdefenders.org llamado: Boss Of The SOC v1
En primer lugar tenemos que descargar la maquina virtual que nos proporcionan y acceder mediante nuestro navegador web http://x.x.x.x:8000
Descripción de los diferentes escenarios
Scenario 1 (APT):
The focus of this hands on lab will be an APT scenario and a ransomware scenario. You assume the persona of Alice Bluebird, the analyst who has recently been hired to protect and defend Wayne Enterprises against various forms of cyberattack.
In this scenario, reports of the below graphic come in from your user community when they visit the Wayne Enterprises website, and some of the reports reference «P01s0n1vy.» In case you are unaware, P01s0n1vy is an APT group that has targeted Wayne Enterprises. Your goal, as Alice, is to investigate the defacement, with an eye towards reconstructing the attack via the Lockheed Martin Kill Chain.
Scenario 2 (Ransomeware):
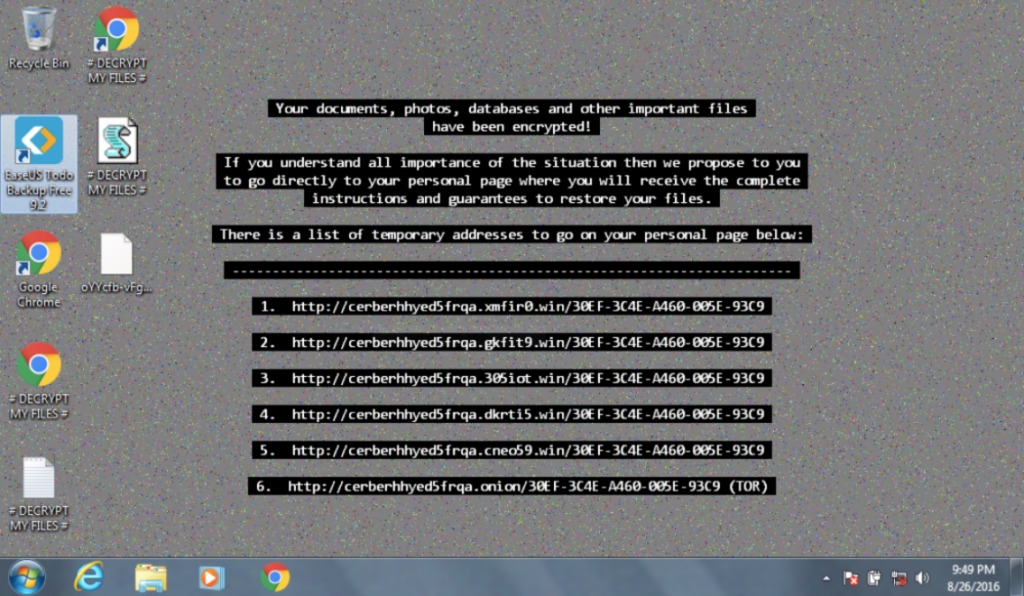
In the second scenario, one of your users is greeted by this image on a Windows desktop that is claiming that files on the system have been encrypted and payment must be made to get the files back. It appears that a machine has been infected with Cerber ransomware at Wayne Enterprises and your goal is to investigate the ransomware with an eye towards reconstructing the attack.
Sin mas preámbulos comenzamos, la primera pregunta como podemos ver es simplemente de rigor.
1# Respuesta: splunk
This is a simple question to get you familiar with submitting answers. What is the name of the company that makes the software that you are using for this competition? Just a six-letter word with no punctuation.2# Respuesta 40.80.148.42
What is the likely IP address of someone from the Po1s0n1vy group scanning imreallynotbatman.com for web application vulnerabilities?Obtención de la evidencia:
Buscamos todas las direcciones orígenes que han realizado una consulta a imreallynotbatman.com
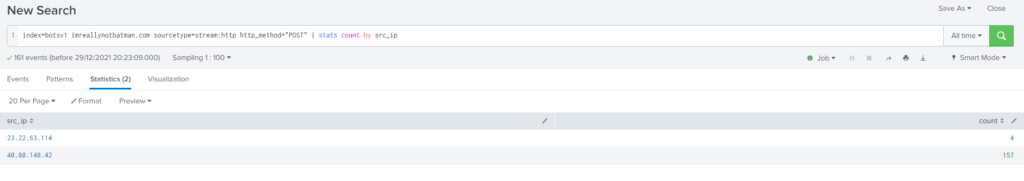
Query
index=botsv1 imreallynotbatman.com sourcetype="stream:http" http_method="POST"
| stats count by src_ipComo podemos observar, tenemos muchas consultas por parte de la dirección ip: 40.80.148.42, para confirmar si se trata de nuestro atacante vemos que tipo de consultas está realizando.
Según detectamos parece ser que se trata de un escáner utilizando Acunetix
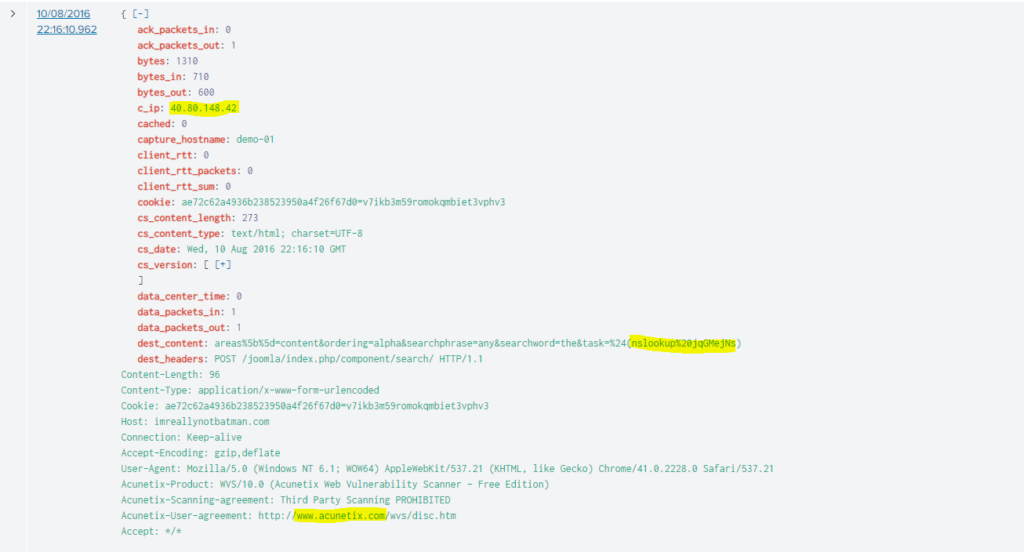
#3 Respuesta: Acunetix
What company created the web vulnerability scanner used by Po1s0n1vy? Type the company name. (For example, "Microsoft" or "Oracle")
Obtención de la evidencia:
Como vimos en la imagen anterior el software que están empleando para realizar el escaneo es Acunetix
Query
index=botsv1 imreallynotbatman.com sourcetype="stream:http" http_method="POST" c_ip="40.80.148.42" | stats count by src_headers| sort -count
| head 3#4 Respuesta: jomla
What content management system is imreallynotbatman.com likely using? (Please do not include punctuation such as . , ! ? in your answer. We are looking for alpha characters only.)Obtención de la evidencia:
para obtener el gestor de la web que aloja imreallynotbatman.com vamos a listar la url utilizando: stats count by
Tal y como podemos comprobar la web utiliza Joomla.
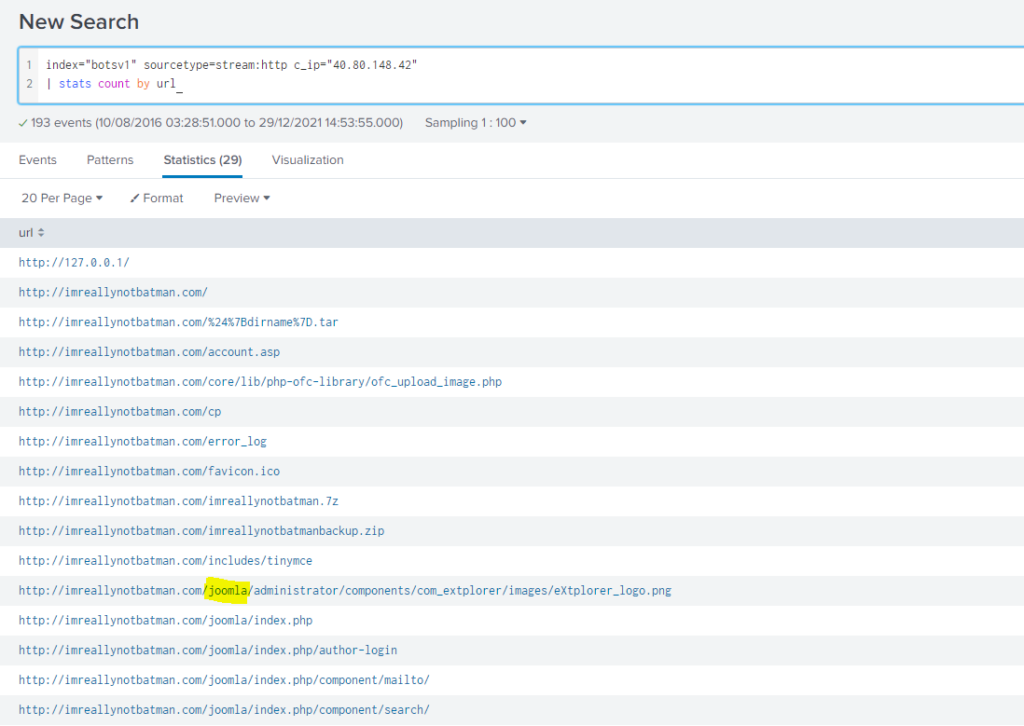
Query
index=botsv1 imreallynotbatman.com sourcetype="stream:http" http_method="POST" c_ip="40.80.148.42"
| stats count by url
#5 Respuesta: poisonivy-is-coming-for-you-batman.jpeg
What is the name of the file that defaced the imreallynotbatman.com website? Please submit only the name of the file with the extension (For example, "notepad.exe" or "favicon.ico").
Obtención de la evidencia:
Tras realizar múltiples consultas filtrando por la dirección ip 40.80.148.42 no encontramos nada. Dado que en la segunda pregunta encontramos otra dirección ip (23.22.63.114) decidimos filtrar por ella.
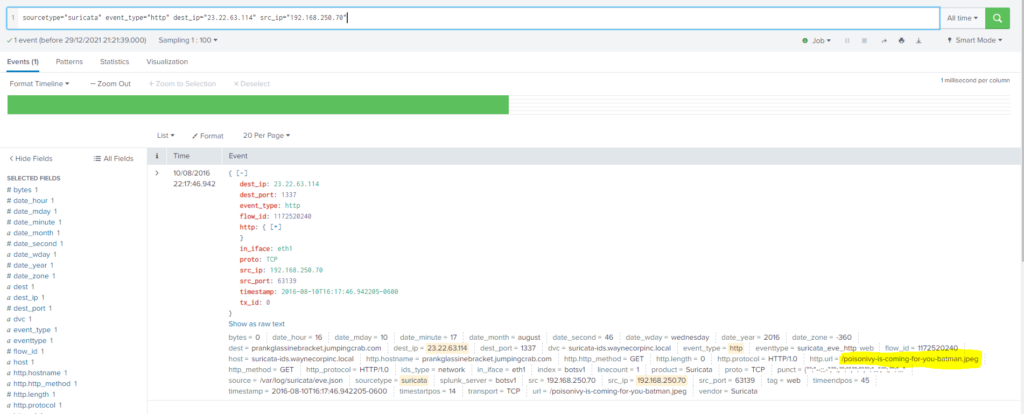
Buscando por dicha ip encontramos en los logs de suricata un registro el día 10/08/2016 a las 22:17:46.942.
Query
index=botsv1 sourcetype="suricata" src_ip="192.168.250.70" dest_ip="23.22.63.114"#6 Respuesta: prankglassinebracket.jumpingcrab.com
This attack used dynamic DNS to resolve to the malicious IP. What is the fully qualified domain name (FQDN) associated with this attack?Obtención de la evidencia:
En el registro anterior pudimos encontrar la respuesta de esta pregunta. Si apreciamos el dst o el http.hostname podemos ver el FQDN: prankglassinebracket.jumpingcrab.com
Query
index=botsv1 sourcetype="suricata" src_ip="192.168.250.70" dest_ip="23.22.63.114"#7 Respuesta: 23.22.63.114
What IP address has Po1s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
Obtención de la evidencia:
Esta respuesta la hemos podido obtener en la pregunta 5.
Query
index=botsv1 imreallynotbatman.com sourcetype="stream:http" http_method="POST"
| stats count by src_ip
#8 Respuesta: LILLIAN.ROSE@PO1S0N1VY.COM
Based on the data gathered from this attack and common open-source intelligence sources for domain names, what is the email address most likely associated with the Po1s0n1vy APT group?
Obtención de la evidencia:
Sirviéndonos de de https://www.threatcrowd.org/ y dirección ip del atacante (23.22.63.114) podemos comprobar que la dirección de correo electrónico asociada es:
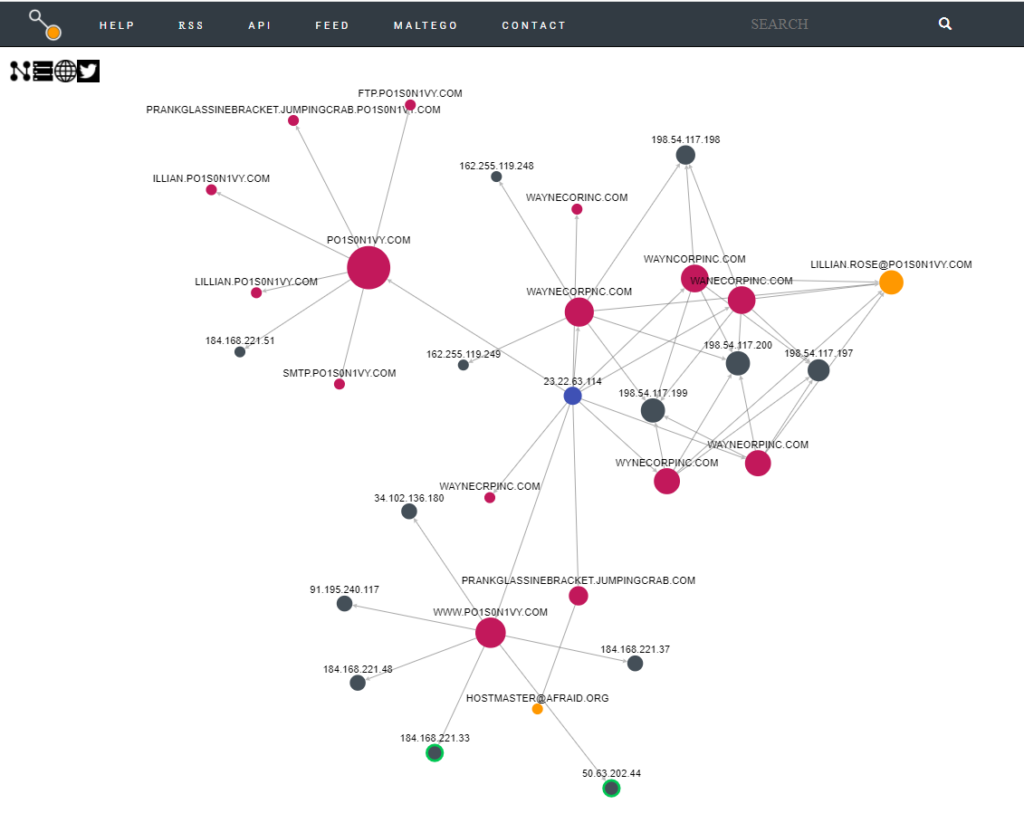
#9 Respuesta: 23.22.63.114
What IP address is likely attempting a brute force password attack against imreallynotbatman.com?
Obtención de la evidencia:
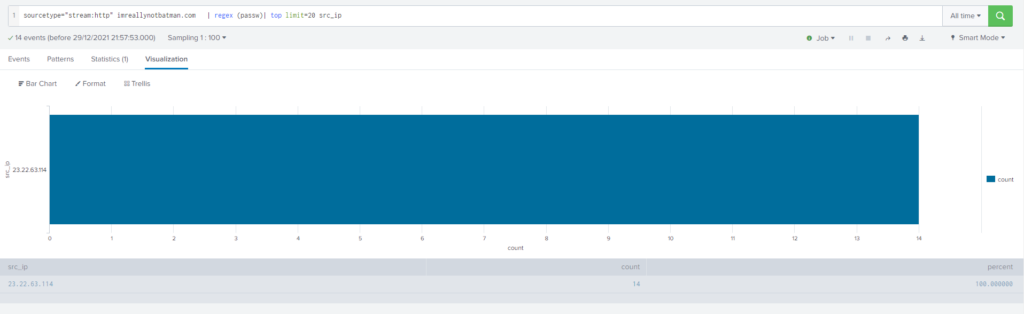
Query
sourcetype="stream:http" imreallynotbatman.com
| regex (passw)
| top limit=20 src_ip#10 Respuesta: 3791.exe
What is the name of the executable uploaded by Po1s0n1vy? Please include the file extension. (For example, "notepad.exe" or "favicon.ico")
Obtención de la evidencia:
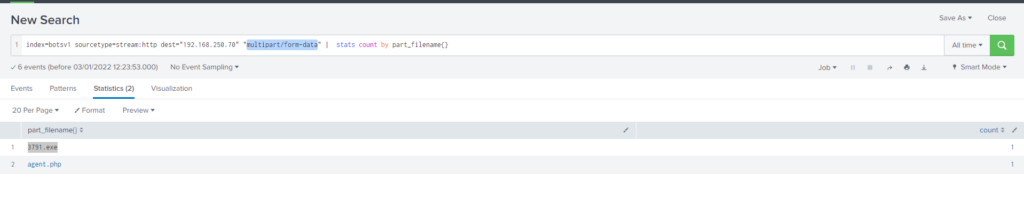
Query
index=botsv1 sourcetype=stream:http dest="192.168.250.70" "multipart/form-data" | stats count by part_filename{}Información sobre multipart/form-data
#11 Respuesta: AAE3F5A29935E6ABCC2C2754D12A9AF0
What is the MD5 hash of the executable uploaded?
Obtención de la evidencia:
Buscamos el archivo 3791.exe y encontramos los siguientes recursos en donde podemos obtener información
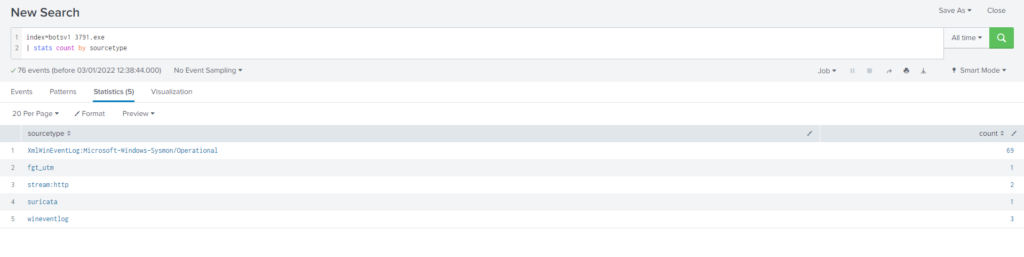
Query
index=botsv1 3791.exe
| stats count by sourcetypeDado que necesitamos obtener el hash MD5 empleamos el log del sysmon
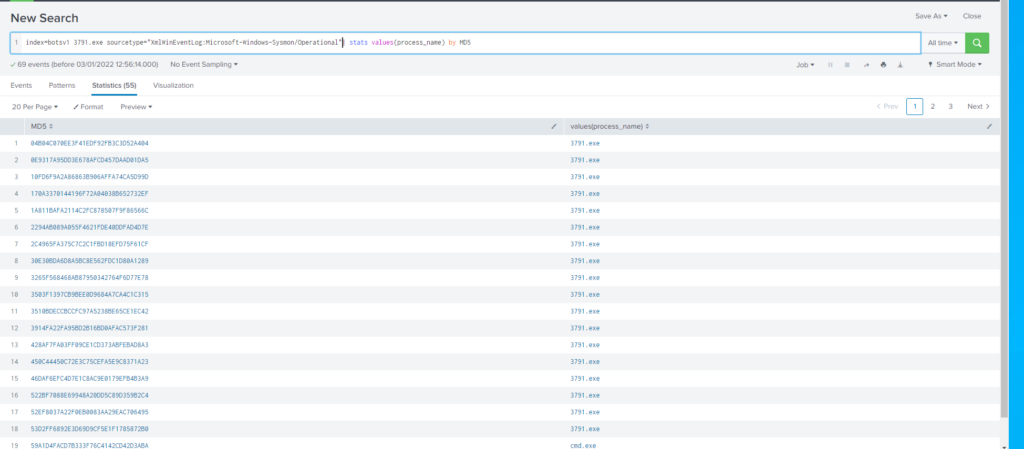
Query
index=botsv1 3791.exe sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational"
| stats values(process_name) by MD5Dado que hemos obtenido demasiados resultados filtramos un poco mas, agregando CommandLine=’3791.exe’
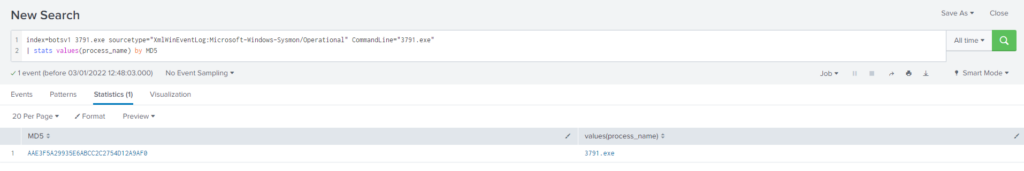
Query
index=botsv1 3791.exe sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" commandLine=" 3791.exe"
| stats values(process_name) by MD5
Información sobre Process hash Matching
- https://www.splunk.com/en_us/blog/security/supernova-redux-with-a-generous-portion-of-masquerading.html
- https://lantern.splunk.com/Security_Use_Case_Guidance/Threat_Intelligence_and_Threat_Hunting/Insider_Threat_and_Account_Compromise/Detecting_masquerading/Process_hash_matching
#12 Respuesta: 9709473AB351387AAB9E816EFF3910B9F28A7A70202E250ED46DBA8F820F34A8
GCPD reported that common TTP (Tactics, Techniques, Procedures) for the Po1s0n1vy APT group, if initial compromise fails, is to send a spear-phishing email with custom malware attached to their intended target. This malware is usually connected to Po1s0n1vy's initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.
Obtención de la evidencia:
Sirviéndonos de https://www.malwares.com/ buscamos la dirección ip que hemos detectado anteriormente (23.22.63.114)
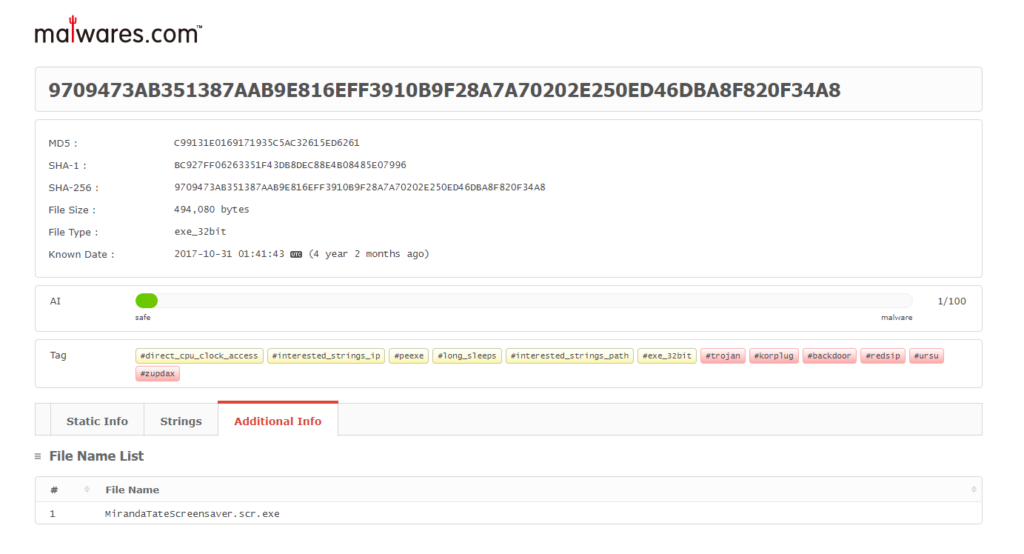
#13 Respuesta: 53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21
What is the special hex code associated with the customized malware discussed in question 12? (Hint: It's not in Splunk)
Obtención de la evidencia:
Buscamos los hash en virustotal y en la parte de community encontramos el código hexadecional
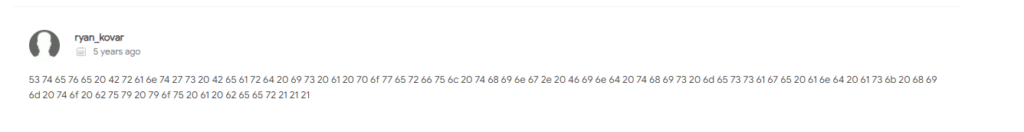
echo "53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21" | xxd -r -p
Steve Brant's Beard is a powerful thing. Find this message and ask him to buy you a beer!!!
#14 Respuesta: 31 73 74 32 66 69 6E 64 67 65 74 73 66 72 65 65 62 65 65 72
One of Po1s0n1vy's staged domains has some disjointed "unique" whois information. Concatenate the two codes together and submit them as a single answer.
Esta pregunta no la entendía muy bien por lo tanto accedí a las ayudas:
hint #1
Use a service like www.robtex.com to determine other domains that are or have been associated with the attacker infrastructure (IP address).hint #2
Use a high quality whois site like www.domaintools.com to perform whois lookups against these domains until you see a hex code where you were expecting text. Warning not all whois sites show you all fields!
Obtención de la evidencia:
No he podido resolver esta pregunta, he sacado los dominios asociados a la dirección ip con www.robtex.com y https://www.threatcrowd.org/ y he realizado whois mediante https://whois.domaintools.com/ a los diferentes dominios sin encontrar una posible solución.
Si cualquier persona sabe como resolverlo no dudéis en indicarlo Jajajaja
ACTUALIZACIÓN
Mediante la web https://www.whoxy.com/whois-history/demo.php conseguí obtener la respuesta a la pregunta.
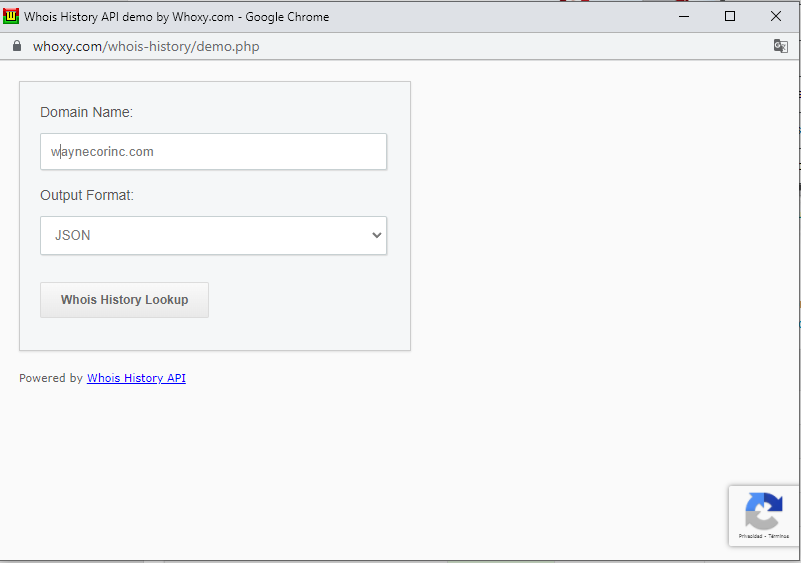
Obtenemos el history del dominio:
{
"status": 1,
"api_query": "whois_history",
"total_records_found": 7,
"whois_records": [
{
"num": 1,
"domain_name": "waynecorinc.com",
"query_time": "2016-08-11 14:15:25",
"create_date": "2016-08-09",
"update_date": "2016-08-09",
"expiry_date": "2017-08-09",
"registrant_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC",
"mailing_address": "TOXICODENR INC|1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "75803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian@po1s0n1vy.com",
"phone_number": "17357647667"
},
"administrative_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC",
"mailing_address": "TOXICODENR INC|1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "75803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian@po1s0n1vy.com",
"phone_number": "17357647667"
},
"technical_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC",
"mailing_address": "TOXICODENR INC|1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "75803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian@po1s0n1vy.com",
"phone_number": "17357647667"
},
"billing_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC",
"mailing_address": "TOXICODENR INC|1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "75803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian@po1s0n1vy.com",
"phone_number": "17357647667"
},
"name_servers": [
"dns1.registrar-servers.com",
"dns2.registrar-servers.com"
],
"domain_status": [
"clientTransferProhibited"
]
},
{
"num": 2,
"domain_name": "waynecorinc.com",
"query_time": "2017-08-03 16:46:53",
"create_date": "2016-08-09",
"update_date": "2017-07-10",
"expiry_date": "2018-08-09",
"domain_registrar": {
"iana_id": 48,
"registrar_name": "eNom, Inc.",
"whois_server": "whois.enom.com",
"website_url": "http://www.enom.com",
"registrar_status": "Accredited"
},
"registrant_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"administrative_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "31 73 74 32 66 69 6E 64 67 65 74 73 66 72 65 65 62 65 65 72",
"mailing_address": "66 72 6F 6D 72 79 61 6E 66 69 6E 64 68 69 6D 74 6F 67 65 74",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"technical_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"name_servers": [
"dns1.registrar",
"dns2.registrar"
],
"domain_status": [
"clientTransferProhibited"
]
},
{
"num": 3,
"domain_name": "waynecorinc.com",
"query_time": "2017-08-03 16:46:53",
"create_date": "2016-08-09",
"update_date": "2017-07-10",
"expiry_date": "2018-08-09",
"domain_registrar": {
"iana_id": 48,
"registrar_name": "eNom, Inc.",
"whois_server": "whois.enom.com",
"website_url": "http://www.enom.com",
"registrar_status": "Accredited"
},
"registrant_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"administrative_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "31 73 74 32 66 69 6E 64 67 65 74 73 66 72 65 65 62 65 65 72",
"mailing_address": "66 72 6F 6D 72 79 61 6E 66 69 6E 64 68 69 6D 74 6F 67 65 74",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"technical_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"name_servers": [
"dns1.registrar",
"dns2.registrar"
],
"domain_status": [
"clientTransferProhibited"
]
},
{
"num": 4,
"domain_name": "waynecorinc.com",
"query_time": "2017-10-25 18:36:28",
"create_date": "2016-08-09",
"update_date": "2017-07-10",
"expiry_date": "2018-08-09",
"domain_registrar": {
"iana_id": 48,
"registrar_name": "eNom, Inc.",
"whois_server": "whois.enom.com",
"website_url": "http://www.enom.com",
"registrar_status": "Accredited"
},
"registrant_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"administrative_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "31 73 74 32 66 69 6E 64 67 65 74 73 66 72 65 65 62 65 65 72",
"mailing_address": "66 72 6F 6D 72 79 61 6E 66 69 6E 64 68 69 6D 74 6F 67 65 74",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"technical_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"name_servers": [
"dns1.registrar",
"dns2.registrar"
],
"domain_status": [
"clientTransferProhibited"
]
},
{
"num": 5,
"domain_name": "waynecorinc.com",
"query_time": "2018-08-08 21:46:20",
"create_date": "2016-08-09",
"update_date": "2018-07-17",
"expiry_date": "2019-08-09",
"domain_registrar": {
"iana_id": 1068,
"registrar_name": "NameCheap, Inc.",
"whois_server": "whois.namecheap.com",
"website_url": "http://www.namecheap.com",
"registrar_status": "Accredited"
},
"registrant_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"administrative_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "31 73 74 32 66 69 6E 64 67 65 74 73 66 72 65 65 62 65 65 72",
"mailing_address": "66 72 6F 6D 72 79 61 6E 66 69 6E 64 68 69 6D 74 6F 67 65 74",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"technical_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC.",
"mailing_address": "1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "65803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian.rose@po1s0n1vy.com",
"phone_number": "+1.7357647667"
},
"billing_contact": {
"full_name": "LILLIAN ROSE",
"company_name": "TOXICODENDRON INC",
"mailing_address": "TOXICODENR INC|1 EDGE FORREST LANE",
"city_name": "SPRINGFIELD",
"state_name": "MO",
"zip_code": "75803",
"country_name": "United States",
"country_code": "US",
"email_address": "lillian@po1s0n1vy.com",
"phone_number": "17357647667"
},
"name_servers": [
"dns1.registrar-servers.com",
"dns2.registrar-servers.com"
],
"domain_status": [
"clientTransferProhibited"
]
},
{
"num": 6,
"domain_name": "waynecorinc.com",
"query_time": "2019-03-22 14:33:38",
"create_date": "2016-08-09",
"update_date": "2018-07-17",
"expiry_date": "2019-08-09",
"domain_registrar": {
"iana_id": 1068,
"registrar_name": "NameCheap, Inc.",
"whois_server": "whois.namecheap.com",
"website_url": "http://www.namecheap.com",
"registrar_status": "Accredited"
},
"registrant_contact": {
"full_name": "WhoisGuard Protected",
"mailing_address": "P.O. Box 0823-03411",
"city_name": "Panama",
"state_name": "Panama",
"country_name": "Panama",
"country_code": "PA",
"email_address": "3a5625ebe1e64e2e9219faabbe026e9b.protect@whoisguard.com",
"phone_number": "+507.8365503",
"fax_number": "+51.17057182"
},
"administrative_contact": {
"full_name": "WhoisGuard Protected",
"mailing_address": "P.O. Box 0823-03411",
"city_name": "Panama",
"state_name": "Panama",
"country_name": "Panama",
"country_code": "PA",
"email_address": "3a5625ebe1e64e2e9219faabbe026e9b.protect@whoisguard.com",
"phone_number": "+507.8365503",
"fax_number": "+51.17057182"
},
"technical_contact": {
"full_name": "WhoisGuard Protected",
"mailing_address": "P.O. Box 0823-03411",
"city_name": "Panama",
"state_name": "Panama",
"country_name": "Panama",
"country_code": "PA",
"email_address": "3a5625ebe1e64e2e9219faabbe026e9b.protect@whoisguard.com",
"phone_number": "+507.8365503",
"fax_number": "+51.17057182"
},
"name_servers": [
"dns1.registrar-servers.com",
"dns2.registrar-servers.com"
],
"domain_status": [
"clientTransferProhibited"
]
},
{
"num": 7,
"domain_name": "waynecorinc.com",
"query_time": "2020-08-31 19:10:13",
"create_date": "2016-08-09",
"update_date": "2019-08-08",
"expiry_date": "2020-08-09",
"domain_registrar": {
"iana_id": 1068,
"registrar_name": "NameCheap, Inc.",
"whois_server": "whois.namecheap.com",
"website_url": "http://www.namecheap.com",
"registrar_status": "Accredited"
},
"registrant_contact": {
"full_name": "REACTIVATION PERIOD",
"company_name": "NAMECHEAP",
"mailing_address": "11400 W. OLYMPIC BLVD, SUITE 200",
"city_name": "LOS ANGELES",
"state_name": "CA",
"zip_code": "90064",
"country_name": "United States",
"country_code": "US",
"email_address": "reactivation-pending@namecheap.com",
"phone_number": "+1.6613102107",
"fax_number": "+1.6613102107"
},
"administrative_contact": {
"full_name": "REACTIVATION PERIOD",
"company_name": "NAMECHEAP",
"mailing_address": "11400 W. OLYMPIC BLVD, SUITE 200",
"city_name": "LOS ANGELES",
"state_name": "CA",
"zip_code": "90064",
"country_name": "United States",
"country_code": "US",
"email_address": "reactivation-pending@namecheap.com",
"phone_number": "+1.6613102107",
"fax_number": "+1.6613102107"
},
"technical_contact": {
"full_name": "REACTIVATION PERIOD",
"company_name": "NAMECHEAP",
"mailing_address": "11400 W. OLYMPIC BLVD, SUITE 200",
"city_name": "LOS ANGELES",
"state_name": "CA",
"zip_code": "90064",
"country_name": "United States",
"country_code": "US",
"email_address": "reactivation-pending@namecheap.com",
"phone_number": "+1.6613102107",
"fax_number": "+1.6613102107"
},
"name_servers": [
"dns101.registrar-servers.com",
"dns102.registrar-servers.com"
],
"domain_status": [
"clientTransferProhibited"
]
}
],
"api_execution_time": 0.01
}#15 Respuesta: 12345678
What was the first brute force password used?
Obtención de la evidencia:
Buscamos si encontramos alguna cadena de conexión con el string password o passwd
index=botsv1 sourcetype="stream:http" http_method=POST *passwd*
Ajustamos mas la búsqueda filtrando por form_data
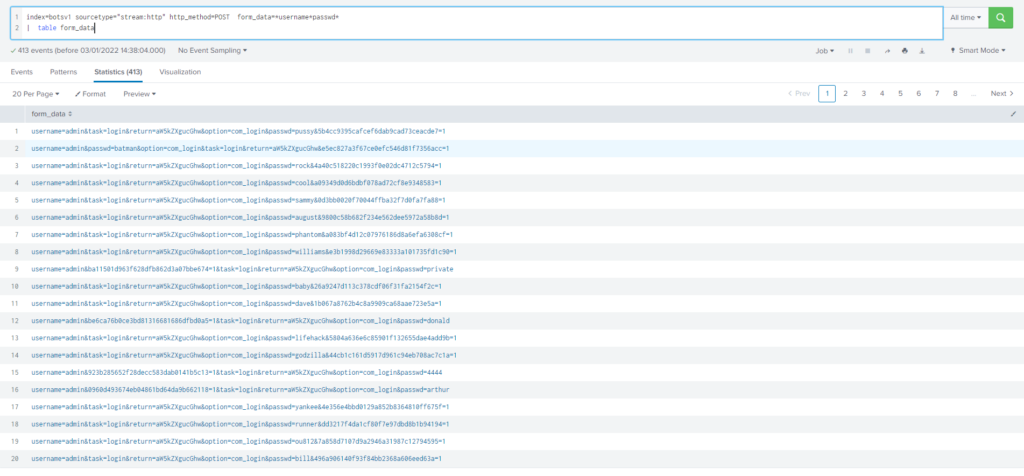
Query
index=botsv1 sourcetype="stream:http" http_method=POST *passwd*
| table form_dataComo podemos ver tenemos demasiados registros y no se ven muy fácilmente, por lo tanto vamos a parsear los datos y ordenar por el primer registro en adelante.
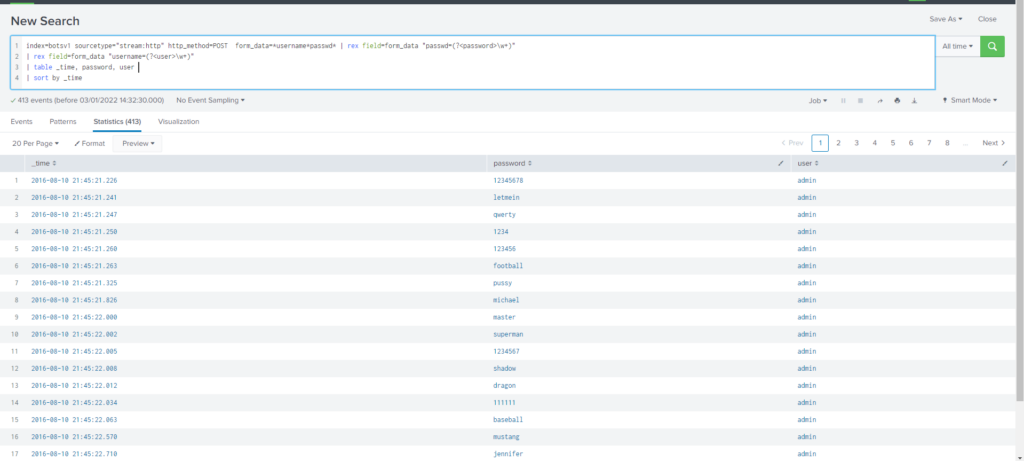
Query
index="botsv1" sourcetype="stream:http" http_method="POST" form_data=*username*passwd*
| rex field=form_data "passwd=(?<password>\w+)"
| table _time, password, user
| sort by _timeAccedemos al listado de canciones comendadas por Coldplay: https://en.wikipedia.org/wiki/List_of_songs_recorded_by_Coldplay
Nos descargamos la lista y mediante grep filtramos las canciones que tiene 6 caracteres
grep -E '^[[:alpha:]]{6}$' songs
Aliens
Broken
Church
Clocks
Murder
Oceans
Shiver
Sparks
Voodoo
YellowEl filtrado de estos parámetros se debería realizar mediante lookup pero mi conocimiento en splunk a fecha de hoy es algo bajo, por lo tanto y debido a que el numero de canciones con 6 caracteres es realmente bajo he decidido realizar una búsqueda filtrando os strings. Como podemos ver nos quedan dos: Voodoo y Yellow
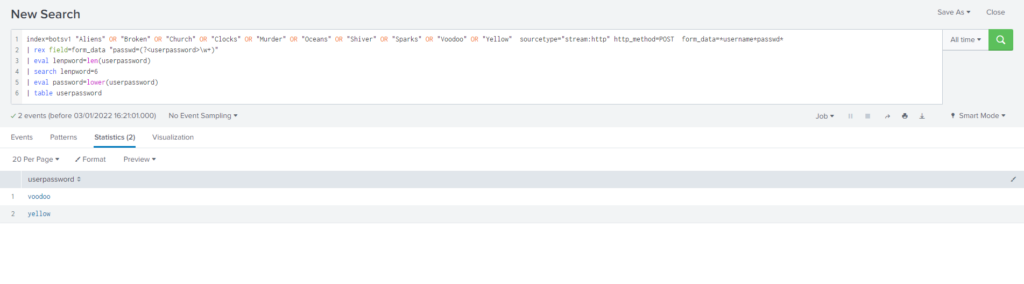
Query
index="botsv1" "Aliens" OR "Broken" OR "Church" OR "Clocks" OR "Murder" OR "Oceans" OR "Shiver" OR "Sparks" OR "Voodoo" OR "Yellow" sourcetype="stream:http" http_method="POST" form_data=*username*passwd*
| rex field=form_data "passwd=(?<userpassword>\w+)"
| eval lenpword=len(userpassword)
| search lenpword=6
| eval password=lower(userpassword)
| table userpassword#17 Respuesta: batman
What was the correct password for admin access to the content management system running "imreallynotbatman.com"?
Obtención de la evidencia:
Como en la pregunta #15 buscamos los logins realizados contra imreallynotbatman.com pero en este caso comprobamos que el numero de la contraseña sea superior a 1.
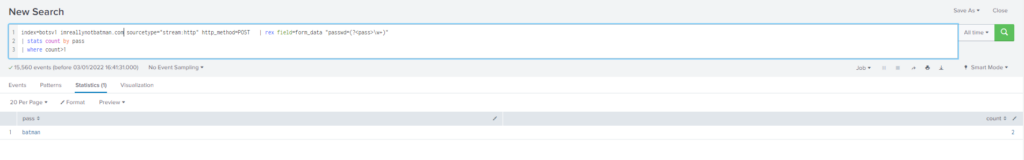
Query
index="botsv1" imreallynotbatman.com sourcetype="stream:http" http_method="POST"
| rex field=form_data "passwd=(?<pass>\w+)"
| stats count by pass
| where count>1#18 Respuesta: 6
What was the average password length used in the password brute-forcing attempt? (Round to a closest whole integer. For example "5" not "5.23213")
Obtención de la evidencia:
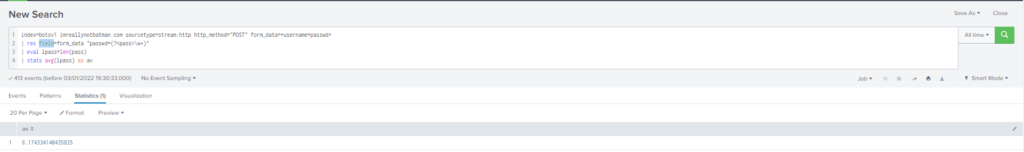
Query
index="botsv1" imreallynotbatman.com sourcetype="stream:http" http_method="POST" form_data=*username*passwd*
| rex field=form_data "passwd=(?<pass>\w+)"
| eval lpass=len(pass)
| stats avg(lpass) as avMas información sobre Evaluation functions:
https://docs.splunk.com/Documentation/Splunk/latest/SearchReference/CommonEvalFunctions
#19 Respuesta: 92.17
How many seconds elapsed between the brute force password scan identified the correct password and the compromised login? Round to 2 decimal places.
Obtención de la evidencia:
Buscamos consultas que coincida con la contraseña obtenida anteriormente (batman)
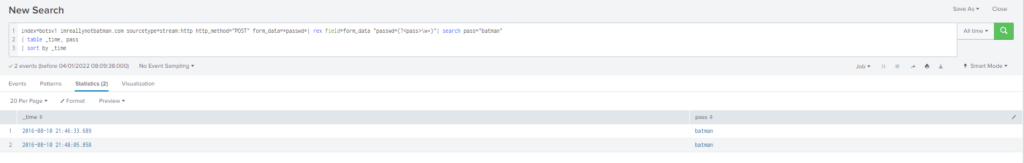
En un principio utilice transaction y imprimí la tabla duration pero me mostraba 92.16 el cual me indicaba que era incorrecta la respuesta.
index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*passwd*| rex field=form_data "passwd=(?<pass>\w+)"| search pass="batman"
| transaction pass
| table duration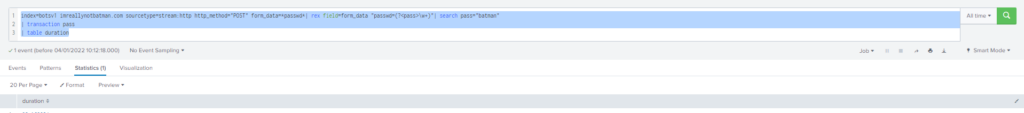
Por lo tanto, utilizamos: transaction y eval duration = round(X,2).
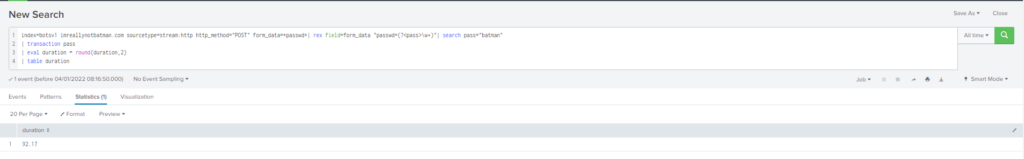
Query
index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*passwd*| rex field=form_data "passwd=(?<pass>\w+)"| search pass="batman"
| transaction pass
| eval duration = round(duration,2)
| table duration
Mas información sobre transaction y duration
- https://community.splunk.com/t5/Splunk-Search/Transaction-and-Duration/m-p/158289
- https://docs.splunk.com/Documentation/Splunk/8.2.4/SearchReference/Transaction
#20 Respuesta: 412
How many unique passwords were attempted in the brute force attempt?
Obtención de la evidencia:
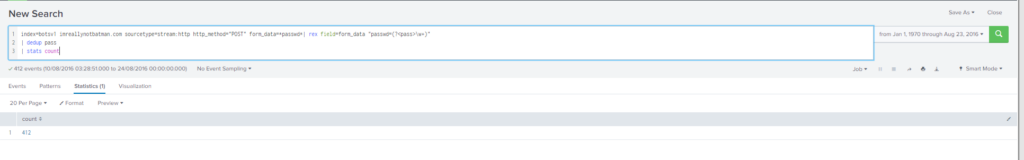
Query
index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*passwd*| rex field=form_data "passwd=(?<pass>\w+)"
| dedup pass
| stats countMas información sobre Depdup
- https://docs.splunk.com/Documentation/SCS/current/SearchReference/DedupCommandExamples
- https://mindmajix.com/splunk-dedup
#21 Respuesta: 192.168.250.100
What was the most likely IP address of we8105desk in 24AUG2016?
Obtención de la evidencia:
Filtramos por la fecha indicada (24AUG2016) y mostramos los registros que tenemos con la ip origen que tengan mas de 1 registro sobre we8105desk.
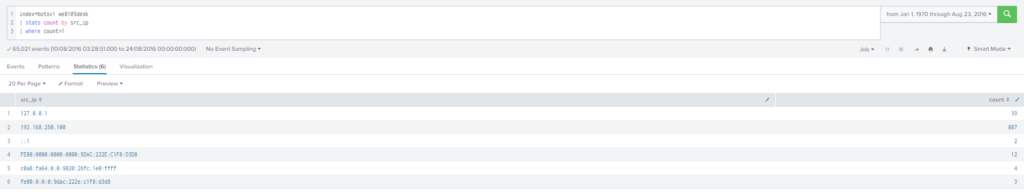
Query
index=botsv1 we8105desk | stats count by src_ip
| where count>1#22 Respuesta: 2816763
Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer. (No punctuation, just 7 integers.)Obtención de la evidencia:
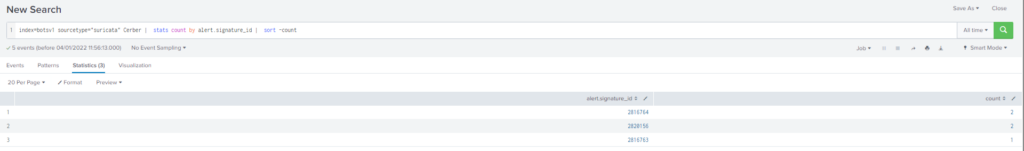
Query
index=botsv1 sourcetype="suricata" Cerber | stats count by alert.signature_id | sort -count#23 Respuesta: cerberhhyed5frqa.xmfir0.win
What fully qualified domain name (FQDN) makes the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Obtención de la evidencia:
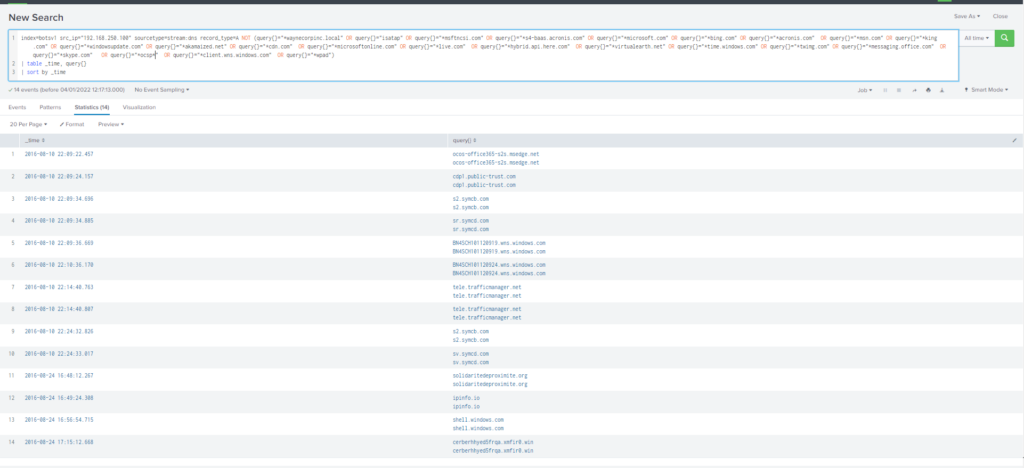
Query
index=botsv1 src_ip="192.168.250.100" sourcetype=stream:dns record_type=A NOT (query{}="*waynecorpinc.local" OR query{}="isatap" OR query{}="*msftncsi.com" OR query{}="*s4-baas.acronis.com" OR query{}="*microsoft.com" OR query{}="*bing.com" OR query{}="*acronis.com" OR query{}="*msn.com" OR query{}="*king.com" OR query{}="*windowsupdate.com" OR query{}="*akamaized.net" OR query{}="*cdn.com" OR query{}="*microsoftonline.com" OR query{}="*live.com" OR query{}="*hybrid.api.here.com" OR query{}="*virtualearth.net" OR query{}="*time.windows.com" OR query{}="*twimg.com" OR query{}="*messaging.office.com" OR query{}="*skype.com" OR query{}="*ocsp*" OR query{}="*client.wns.windows.com" OR query{}="*wpad")
| table _time, query{}
| sort by _time#24 Respuesta: solidaritedeproximite.org
What was the first suspicious domain visited by we8105desk in 24AUG2016?
Obtención de la evidencia:
Al igual que en la pregunta #23 vamos faltando los dominios a los que se consulto, nos vamos al día 24AUG2016 y encontramos las siguientes consultas:
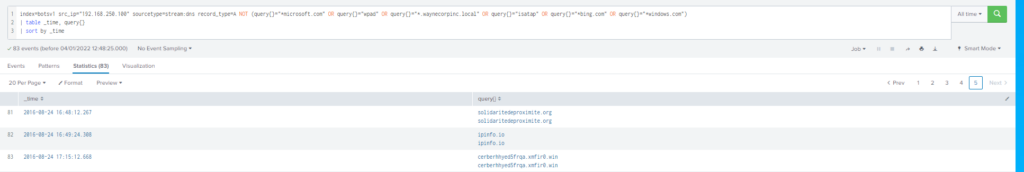
Como podemos ver a las 2016-08-24 16:48:12.267 se accede a solidaritedeproximite.org y después a las 2016-08-24 17:15:12.668 tenemos una consulta a: cerberhhyed5frqa.xmfir0.win
Query:
index=botsv1 src_ip="192.168.250.100" sourcetype=stream:dns record_type=A NOT (query{}="*microsoft.com" OR query{}="wpad" OR query{}="*.waynecorpinc.local" OR query{}="isatap" OR query{}="*bing.com" OR query{}="*windows.com")
| table _time, query{}
| sort by _timeMas información sobre sourcetype=stream:dns
#25 Respuesta: 4490
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length in characters of the value of this field?
Obtención de la evidencia:
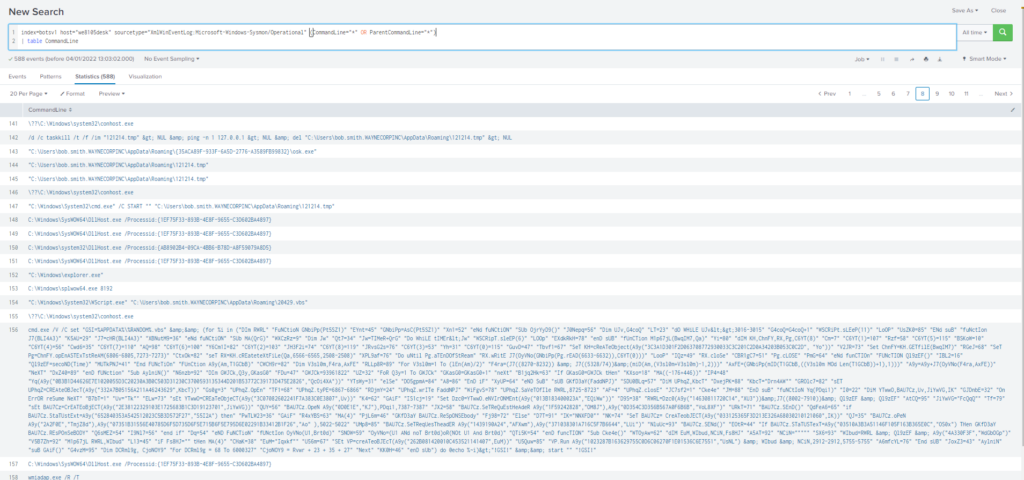
Query
index=botsv1 host="we8105desk" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" (CommandLine="*" OR ParentCommandLine="*")
| table CommandLine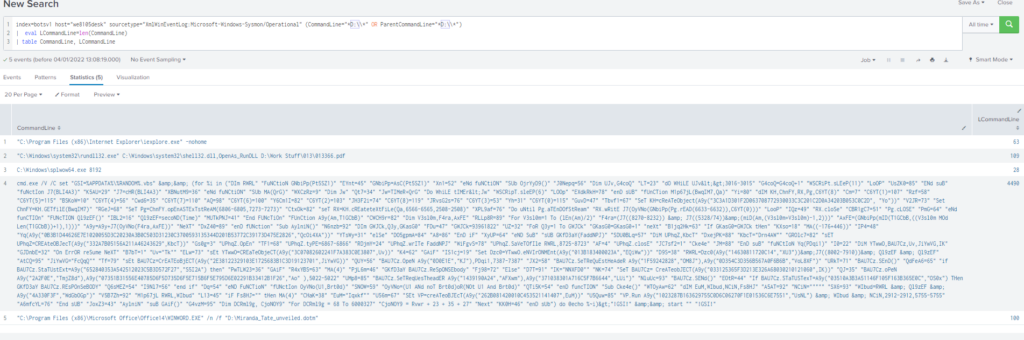
Query
index=botsv1 host="we8105desk" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" (CommandLine="*D:\\*" OR ParentCommandLine="*D:\\*")
| eval LCommandLine=len(CommandLine)
| table CommandLine, LCommandLine#26 Respuesta: MIRANDA_PRI
What is the name of the USB key inserted by Bob Smith?
Obtención de la evidencia:
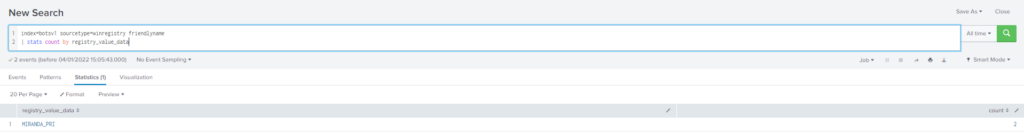
Query
index=botsv1 sourcetype=winregistry friendlyname
| stats count by registry_value_dataMas información
Removable devices connected to a machine
USB and Removable Media Detection
#27 Respuesta: 192.168.250.20
Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IP address of the file server?
Obtención de la evidencia:
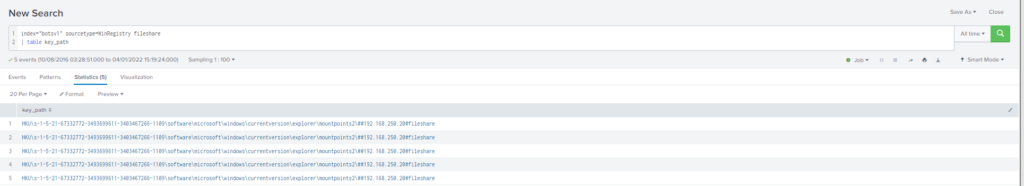
Mas información
#28 Respuesta: 257
How many distinct PDFs did the ransomware encrypt on the remote file server?
Obtención de la evidencia:
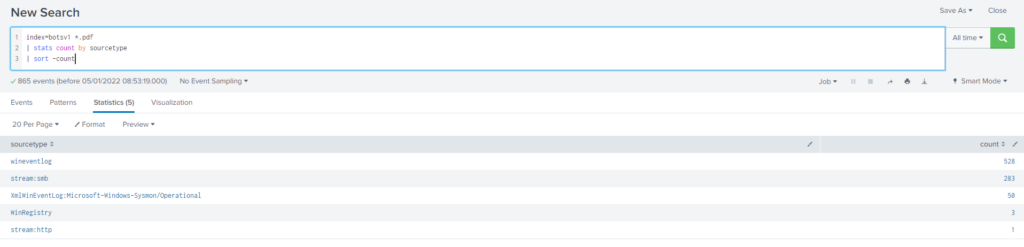
Query
index="botsv1" *.pdf
| stats count by sourcetype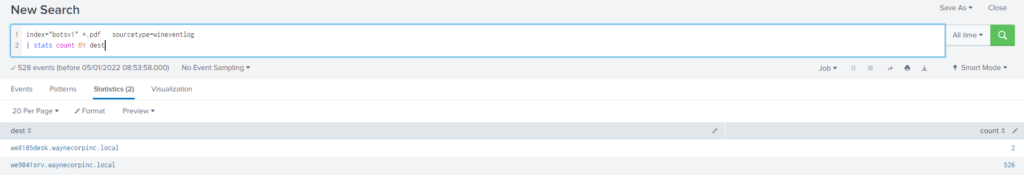
Query
index="botsv1" *.pdf sourcetype=wineventlog
| stats count BY dest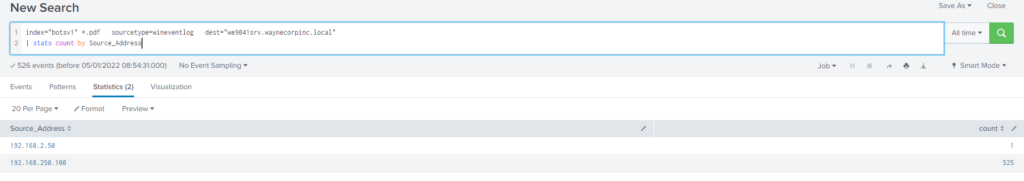
Query
index=botsv1 *.pdf sourcetype=wineventlog dest="we9041srv.waynecorpinc.local"
| stats count by Source_Address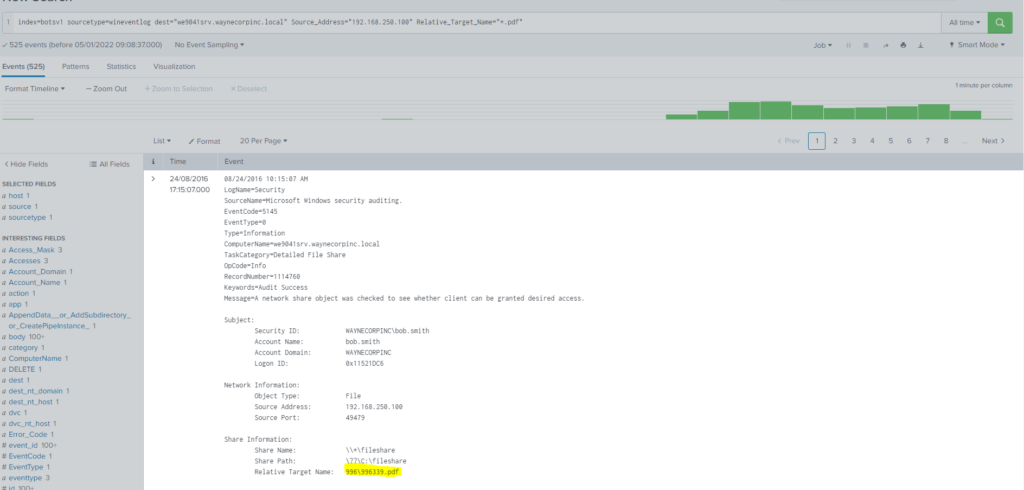
Query
index=botsv1 sourcetype=wineventlog dest="we9041srv.waynecorpinc.local" Source_Address="192.168.250.100" Relative_Target_Name="*.pdf"Me costo sacar el numero totales de registros que había, dado que mediante «stats count by» no me lo mostraba. Buscando por internet en el community de Splunk vi varias publicaciones que utilizaban la opción stats dc()
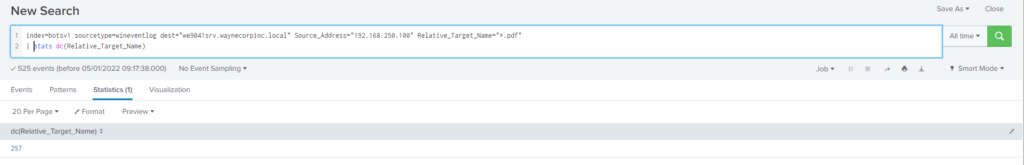
Query
index=botsv1 sourcetype=wineventlog dest="we9041srv.waynecorpinc.local" Source_Address="192.168.250.100" Relative_Target_Name="*.pdf"
| stats dc(Relative_Target_Name)Mas información
- https://community.splunk.com/t5/Splunk-Search/Why-does-count-and-dc-behave-differently/m-p/470611
- https://docs.splunk.com/Documentation/Splunk/latest/SearchReference/stats
#29 Respuesta: 3968
The VBScript found in question 25 launches 121214.tmp. What is the ParentProcessId of this initial launch?
Obtención de la evidencia:
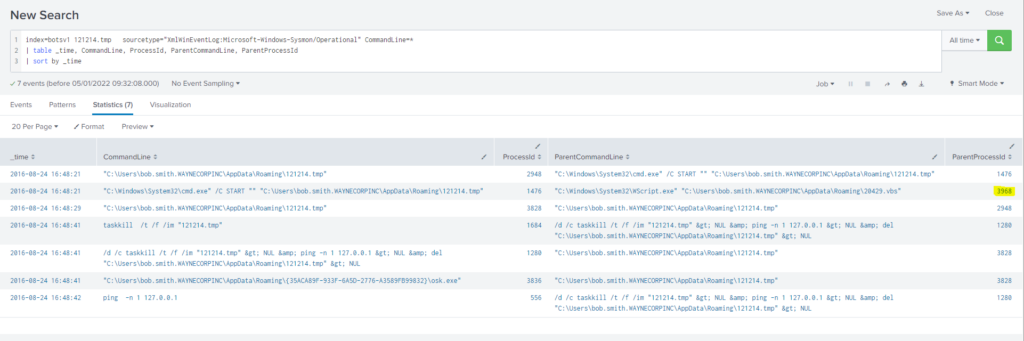
Query
index=botsv1 121214.tmp sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine=*
| table _time, CommandLine, ProcessId, ParentCommandLine, ParentProcessId
| sort by _time#30 Respuesta: 406
The Cerber ransomware encrypts files located in Bob Smith's Windows profile. How many .txt files does it encrypt?
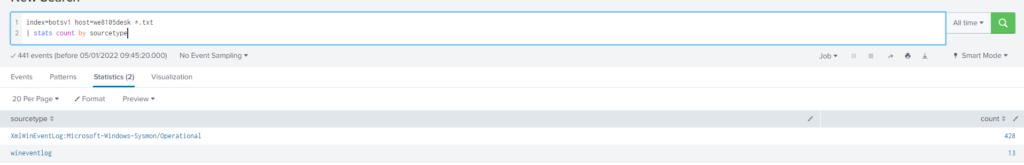
Query
index=botsv1 host=we8105desk *.txt
| stats count by sourcetype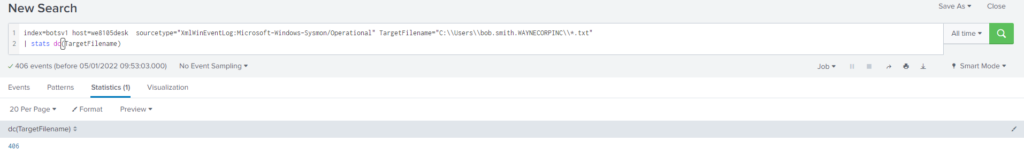
Query
index=botsv1 host=we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" TargetFilename="C:\\Users\\bob.smith.WAYNECORPINC\\*.txt"
| stats dc(TargetFilename)#31 Respuesta: mhtr.jpg
The malware downloads a file that contains the Cerber ransomware crypto code. What is the name of that file?
Obtención de la evidencia:
En la pregunta #24 vimos los dominios que eran sospechosos, utilizando dichos dominios sospechosos filtramos en busca de url’s
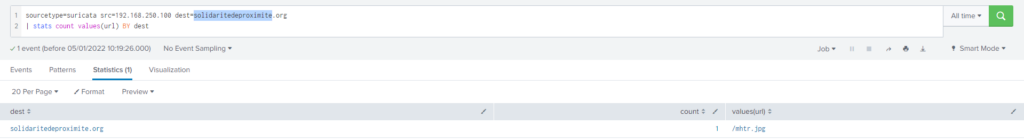
Query
sourcetype=suricata src=192.168.250.100 dest=solidaritedeproximite.org
| stats count values(url) BY destMas información
#32 Respuesta: Steganography
Now that you know the name of the ransomware's encryptor file, what obfuscation technique does it likely use?
Obtención de la evidencia:


Pretty! This was a really wonderful article. Many thanks
for providing this information.