Seguimos configurando nuestra infraestructura SIRP Open source (https://red-orbita.com/?p=8726) En esta ocasión veremos como integrar Kaspersky Security Center para la detección de amenazas con Wazuh y Thehive
Antes de nada, tenemos que ir a la consola de Kaspersky Security Center > Configurar las notificaciones y la exportación de eventos > Configuración exportación a SIEM (Mas información)
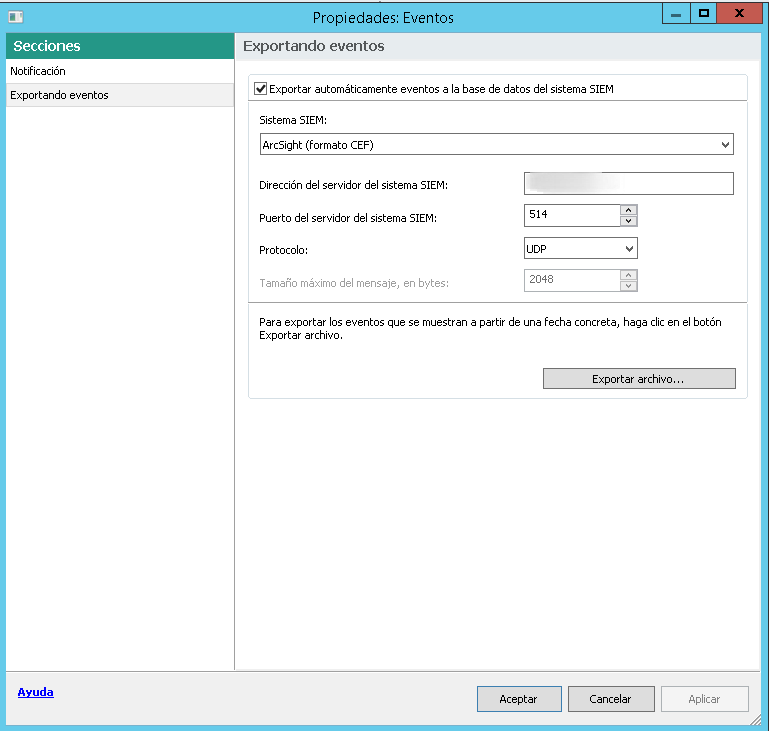
Seleccionamos ArcSiht (Formato CEF), Configuramos la dirección ip de nuestro servidor Wazuh Manager y presionamos Aceptar
Una vez configurado el envió de los logs tenemos que acceder a nuestro servidor Wazuh Manager en el cual vamos a generar un Decoder, para ello editamos /var/ossec/etc/decoders/local_decoder.xml
En este archivo agregamos la siguiente configuración
<!-- Kaspersky Decoder. -->
<decoder name="Kaspersky">
<prematch>^CEF:0\|KasperskyLab\|SecurityCenter</prematch>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>dhost=(\S+)</regex>
<order>dhost</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>dst=(\d+.\d+.\d+.\d+:\d+)|dst=(\d+.\d+.\d+.\d+)</regex>
<order>dstip</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>TCP from (\d+.\d+.\d+.\d+:\d+)|TCP from (\d+.\d+.\d+.\d+)</regex>
<order>srcip</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>TCP de (\d+.\d+.\d+.\d+:\d+)|TCP de (\d+.\d+.\d+.\d+)</regex>
<order>srcip</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>local port (\d+)</regex>
<order>dstport</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>duser=(\S+)</regex>
<order>duser</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Usuario: (\S+)</regex>
<order>duser</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>filePath=(\.+) (\w+=)|filePath=(\.+)</regex>
<order>Kaspersky.url</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>msg=(\.+) File:</regex>
<order>Kaspersky.description.task</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>GNRL_EV_VIRUS_FOUND_AND_BLOCKED\|(\.+)\|</regex>
<order>Kaspersky.description</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>GNRL_EV_VIRUS_FOUND\|(\.+)\|</regex>
<order>Kaspersky.description</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>GNRL_EV_SUSPICIOUS_OBJECT_FOUND\|(\.+)\|</regex>
<order>Kaspersky.description</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>GNRL_EV_WEB_URL_BLOCKED\|(\.+)\|</regex>
<order>Kaspersky.description</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>GNRL_EV_OBJECT_DELETED\|(\.+)\|</regex>
<order>Kaspersky.description</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>GNRL_EV_PASSWD_ARCHIVE_FOUND\|(\.+)\|</regex>
<order>Kaspersky.description</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Ruta: (\.+)\\r\\n</regex>
<order>Kaspersky.path</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Detectado: (\.+)\\r\\n</regex>
<order>Kaspersky.object</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Objeto: (\.+) rt=</regex>
<order>Kaspersky.object</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Path: (\.+)\\r\\n</regex>
<order>Kaspersky.path</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>r\\nApplication: (\.+)\\r\\n</regex>
<order>Kaspersky.application</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>r\\nAplicación: (\.+)\\r\\n</regex>
<order>Kaspersky.application</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>nName: (\.+)\\r\\n</regex>
<order>Kaspersky.application.name</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>\\Name: (\.+)\\r</regex>
<order>Kaspersky.application.name</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Deleted: (\.+)\\r\\n</regex>
<order>Kaspersky.applocation.delete</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>level:(\.+)\\r\\n</regex>
<order>Kaspersky.level</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>Hash: (\.+)\\r\\n</regex>
<order>Kaspersky.hash</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>SHA256: (\w+)</regex>
<order>Kaspersky.hash.sha256</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>MD5: (\w+)</regex>
<order>Kaspersky.hash.md5</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>filePath=(\.+) (\w+=)|(\$s)</regex>
<order>Kaspersky.filePath</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>\\Description: (\w+)</regex>
<order>Kaspersky.attack.status</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs1=(\S+)</regex>
<order>Kaspersky.cs1</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs1Label=(\S+)</regex>
<order>Kaspersky.cs1Label</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs4=(\S+)</regex>
<order>Kaspersky.cs4</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs4Label=(\S+)</regex>
<order>Kaspersky.cs4Label</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs6Label=(\S+)</regex>
<order>Kaspersky.cs6Label</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs6=(\S+)</regex>
<order>Kaspersky.cs6</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs7=(\S+)</regex>
<order>dstport</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs7Label=(\S+)</regex>
<order>Kaspersky.cs7Label</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs9=(\S+)</regex>
<order>Kaspersky.cs9</order>
</decoder>
<decoder name="Kaspersky-fields">
<parent>Kaspersky</parent>
<regex>cs10=(\.+) cs10Label=</regex>
<order>Kaspersky.cs10</order>
</decoder>
Comprobamos el correcto funcionamiento mediante ossec-logtest
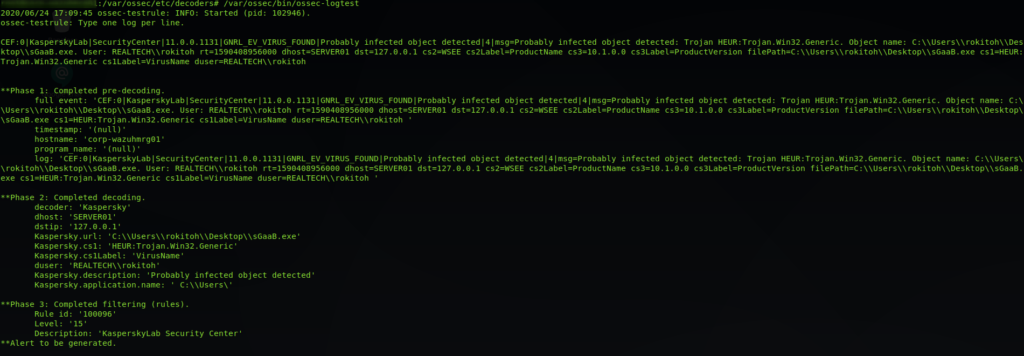
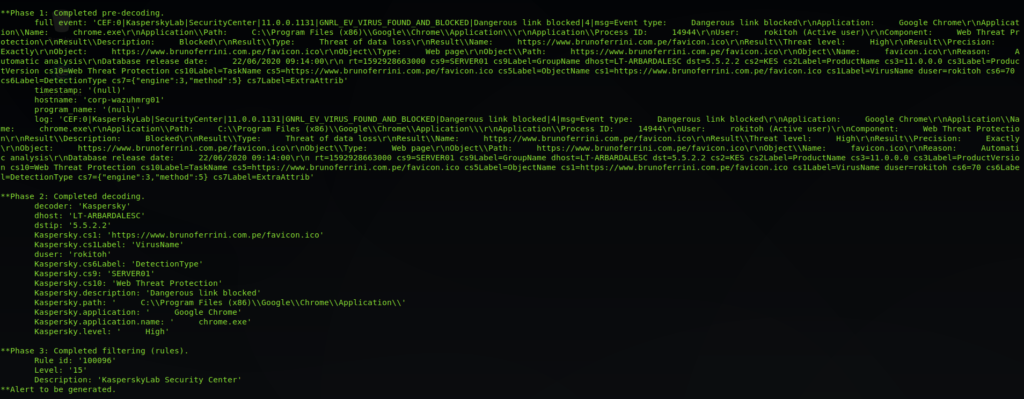
Tras configurar el Decoder procedemos a agregar las siguientes reglas
*/ rules in localrules.xml for Kaspersky*/
<group name="KasperskyLab,">
<rule id="100090" level="0">
<match>KasperskyLab</match>
<decoded_as>Kaspersky</decoded_as>
<description>$(data.Kaspersky.description)</description>
</rule>
<rule id="100092" level="3">
<if_sid>100090</if_sid>
<match>attack</match>
<description>Attack detected</description>
<group>syslog,attack,kaspersky,</group>
</rule>
<rule id="100093" level="3">
<if_sid>100090</if_sid>
<match>detected</match>
<description>Object detected</description>
<group>syslog,detected_attack,kaspersky,</group>
</rule>
<rule id="100095" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_ATTACK_DETECTED</match>
<description>Attack detected</description>
<group>syslog,detected_attack,kaspersky,</group>
</rule>
<rule id="100096" level="15">
<if_sid>100090</if_sid>
<match>GNRL_EV_VIRUS_FOUND</match>
<description>Virus found</description>
<group>syslog,virus_found,attack,kaspersky,</group>
</rule>
<rule id="100097" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_SUSPICIOUS_OBJECT_FOUND</match>
<description>Suspicious object found</description>
<group>syslog,suspicius_object_found,kaspersky,</group>
</rule>
<rule id="100098" level="10">
<if_sid>100090</if_sid>
<match>GNRL_EV_WEB_URL_BLOCKED</match>
<description>URL Web Blocked</description>
<group>syslog,url_blocked,kaspersky,</group>
</rule>
<rule id="100099" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_OBJECT_DELETED</match>
<description>Object was deleted</description>
<group>syslog,object_deleted,kaspersky,</group>
</rule>
<rule id="100100" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_PASSWD_ARCHIVE_FOUND</match>
<description>Password-protected archive was found</description>
<group>syslog,passwod_arhive_found,kaspersky,</group>
</rule>
</group>
*/ rules in localrules.xml for Kaspersky*/
<group name="KasperskyLab,">
<rule id="100090" level="0">
<match>KasperskyLab</match>
<decoded_as>Kaspersky</decoded_as>
<description>$(data.Kaspersky.description)</description>
</rule>
<rule id="100092" level="3">
<if_sid>100090</if_sid>
<match>attack</match>
<description>Attack detected</description>
<group>syslog,attack,kaspersky,</group>
</rule>
<rule id="100093" level="3">
<if_sid>100090</if_sid>
<match>detected</match>
<description>Object detected</description>
<group>syslog,detected_attack,kaspersky,</group>
</rule>
<rule id="100095" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_ATTACK_DETECTED</match>
<description>Attack detected</description>
<group>syslog,detected_attack,kaspersky,</group>
</rule>
<rule id="100096" level="15">
<if_sid>100090</if_sid>
<match>GNRL_EV_VIRUS_FOUND</match>
<description>Virus found</description>
<group>syslog,virus_found,attack,kaspersky,</group>
</rule>
<rule id="100097" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_SUSPICIOUS_OBJECT_FOUND</match>
<description>Suspicious object found</description>
<group>syslog,suspicius_object_found,kaspersky,</group>
</rule>
<rule id="100098" level="10">
<if_sid>100090</if_sid>
<match>GNRL_EV_WEB_URL_BLOCKED</match>
<description>URL Web Blocked</description>
<group>syslog,url_blocked,kaspersky,</group>
</rule>
<rule id="100099" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_OBJECT_DELETED</match>
<description>Object was deleted</description>
<group>syslog,object_deleted,kaspersky,</group>
</rule>
<rule id="100100" level="12">
<if_sid>100090</if_sid>
<match>GNRL_EV_PASSWD_ARCHIVE_FOUND</match>
<description>Password-protected archive was found</description>
<group>syslog,passwod_arhive_found,kaspersky,</group>
</rule>Reiniciamos el servicio de wazuh manager
systemctl restart wazuh-manager.serviceForzamos una alerta ejecutando algún tipo de software malicioso en un servidor de pruebas. Accedemos mediante nuestro navegador a Kibana y comprobamos si esta funcionando correctamente nuestro Decoder y las reglas realizadas
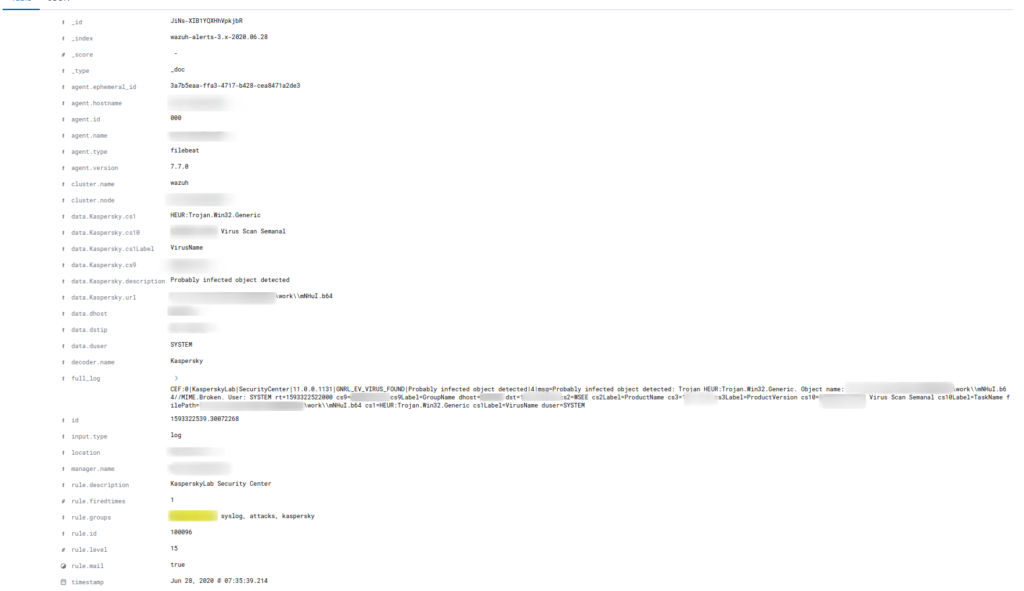
En la próxima entrada veremos como integrar estas alertas con Thehive
:wq!
Hola, tengo una consulta, hice la configuracion tanto en wazuh en centos 7 y el kaspersky windows server, todo exactamente como esta pero no me funciona, incluso el comando /var/ossec/bin/ossec-logtest no me da salida, incluso forzando una salida no obtengo nada y por supuesto en wazuh no obtengo ninguna respuesta, solo tengo salidas de la proteccion por defecto de windows pero ningun log de kaspersky.
Gracias
El ultimo fragmento está incompleto, podrías compartirlo
gracias