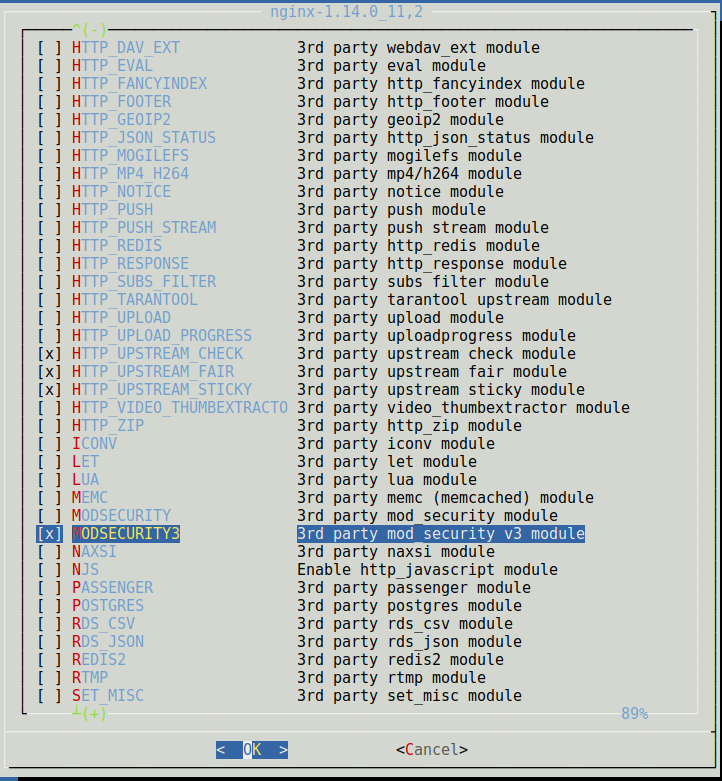
En esta entrada vamos a ver como instalar y configurar un NGINX con Modsecurity bajo FreeBSD
Antes de nada refrescamos y actualizamos los ports
portsnap fetch auto
pkg upgrade
Instalamos las librerías necesarias:
pkg install libxml2 libxslt mod_security3 python git binutils pcre GeoIP libgd openldap-client
Accedemos al port de NGINX y configuramos los modulos
cd /usr/port/www/nginx
make config
Compilamos NGINX
make install
Creamos las siguientes carpetas dentro del directorio de NGINX
mkdir /usr/local/etc/nginx/conf.d
mkdir /usr/local/etc/nginx/sites-enabled
Realizamos una copia de seguridad de nginx.conf
mv /usr/local/etc/nginx/nginx.conf /usr/local/etc/nginx/nginx.conf-bck
Agregamos la siguiente configuración al fichero nginx.conf
vi /usr/local/etc/nginx/nginx.conf
user www;
worker_processes auto;worker_rlimit_nofile 100000;
events {
#worker_connections 768;
worker_connections 4000;
use kqueue;
multi_accept on;
}http {
##
# Basic Settings
##open_file_cache max=200000 inactive=20s;
open_file_cache_valid 30s;
open_file_cache_min_uses 2;
open_file_cache_errors on;
proxy_cache_path /tmp/nginx levels=1:2 keys_zone=my_zone:10m inactive=60m;access_log off;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
types_hash_max_size 2048;
server_tokens off;# server_names_hash_bucket_size 64;
# server_name_in_redirect off;include /usr/local/etc/nginx/mime.types;
default_type application/octet-stream;##
# SSL Settings
##ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Dropping SSLv3, ref: POODLE
ssl_prefer_server_ciphers on;##
# Logging Settings
##access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;##
# Gzip Settings
##gzip on;
gzip_min_length 10240;
gzip_proxied expired no-cache no-store private auth;
gzip_types text/plain text/css text/xml text/javascript application/x-javascript application/json application/xml;
gzip_disable «msie6»;reset_timedout_connection on;
#client_body_timeout 10;
#send_timeout 2;
send_timeout 10;
#keepalive_timeout 30;
keepalive_timeout 15;
keepalive_requests 100000;# gzip_vary on;
# gzip_proxied any;
# gzip_comp_level 6;
# gzip_buffers 16 8k;
# gzip_http_version 1.1;
# gzip_types text/plain text/css application/json application/javascript text/xml application/xml application/xml+rss text/javascript;#Modsecurity
modsecurity on;
modsecurity_rules_file /usr/local/etc/modsecurity/modsecurity.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs-setup.conf;##
# Virtual Host Configs
##include /usr/local/etc/nginx/conf.d/*.conf;
include /usr/local/etc/nginx/sites-enabled/*;
}
Configuramos las reglas de Modsecurity
cd /tmp
git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git
cd owasp-modsecurity-crs/
cp crs-setup.conf.example /usr/local/etc/modsecurity/crs-setup.conf
mkdir /usr/local/etc/modsecurity/crs
cp rules/* /usr/local/etc/modsecurity/crs
Creamos un sitio para probar el funcionamiento del servidor
cat /usr/local/etc/nginx/sites-enabled/redorbita.conf
server {
listen 80 default_server;
listen [::]:80 default_server;root /usr/local/www/nginx/;
server_name _;
location / {
################################## ModSecurity ############################################################modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-901-INITIALIZATION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-903.9003-NEXTCLOUD-EXCLUSION-RULES.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-903.9004-DOKUWIKI-EXCLUSION-RULES.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-903.9005-CPANEL-EXCLUSION-RULES.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-905-COMMON-EXCEPTIONS.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-910-IP-REPUTATION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-911-METHOD-ENFORCEMENT.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-912-DOS-PROTECTION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-913-SCANNER-DETECTION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-914-FILE-DETECTION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-920-PROTOCOL-ENFORCEMENT.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-921-PROTOCOL-ATTACK.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-930-APPLICATION-ATTACK-LFI.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-931-APPLICATION-ATTACK-RFI.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-932-APPLICATION-ATTACK-RCE.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-933-APPLICATION-ATTACK-PHP.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-941-APPLICATION-ATTACK-XSS.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-942-APPLICATION-ATTACK-SQLI.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-944-APPLICATION-ATTACK-JAVA.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/REQUEST-949-BLOCKING-EVALUATION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-950-DATA-LEAKAGES.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-951-DATA-LEAKAGES-SQL.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-952-DATA-LEAKAGES-JAVA.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-953-DATA-LEAKAGES-PHP.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-954-DATA-LEAKAGES-IIS.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-959-BLOCKING-EVALUATION.conf;
modsecurity_rules_file /usr/local/etc/modsecurity/crs/RESPONSE-980-CORRELATION.conf;##########################################################################################################
}
}
Al chequear la configuración vamos a ver diversos errores en las reglas de modsecurity la cual tenemos que eliminar:
/usr/local/sbin/nginx -t
nginx: [emerg] «modsecurity_rules_file» directive Rules error. File: /usr/local/etc/modsecurity/crs/REQUEST-912-DOS-PROTECTION.conf. Line: 187. Column: 29. Expecting an action, got: ,\ in /usr/local/etc/nginx/sites-enabled/redorbita.conf:69
nginx: configuration file /usr/local/etc/nginx/nginx.conf test failed/usr/local/sbin/nginx -t
nginx: [emerg] «modsecurity_rules_file» directive Rules error. File: /usr/local/etc/modsecurity/crs/REQUEST-912-DOS-PROTECTION.conf. Line: 188. Column: 29. Expecting an action, got: ,\ in /usr/local/etc/nginx/sites-enabled/redorbita.conf:69/usr/local/sbin/nginx -t
nginx: [emerg] «modsecurity_rules_file» directive Rules error. File: /usr/local/etc/modsecurity/crs/REQUEST-914-FILE-DETECTION.conf. Line: 70. Column: 85. Expecting a variable, got: : S}: %{MATCHED_VARS}’,\ in /usr/local/etc/nginx/sites-enabled/redorbita.conf:71/usr/local/sbin/nginx -t
nginx: [emerg] «modsecurity_rules_file» directive Rules error. File: /usr/local/etc/modsecurity/crs/REQUEST-914-FILE-DETECTION.conf. Line: 121. Column: 85. Expecting a variable, got: : S}: %{MATCHED_VARS}’,\ in /usr/local/etc/nginx/sites-enabled/redorbita.conf:71
Tras eliminar las reglas erroneas chequeamos y reiniciamos:
/usr/local/sbin/nginx -t
nginx: the configuration file /usr/local/etc/nginx/nginx.conf syntax is ok
nginx: configuration file /usr/local/etc/nginx/nginx.conf test is successfulservice nginx restart
Accedemos mediante nuestro navegador
:wq!