Instructions:
- Uncompress the lab (pass: cyberdefenders.org)
Scenario:
A large multinational corporation heavily relies on the 3CX software for phone communication, making it a critical component of their business operations. After a recent update to the 3CX Desktop App, antivirus alerts flag sporadic instances of the software being wiped from some workstations while others remain unaffected. Dismissing this as a false positive, the IT team overlooks the alerts, only to notice degraded performance and strange network traffic to unknown servers. Employees report issues with the 3CX app, and the IT security team identifies unusual communication patterns linked to recent software updates.
As the threat intelligence analyst, it’s your responsibility to examine this possible supply chain attack. Your objectives are to uncover how the attackers compromised the 3CX app, identify the potential threat actor involved, and assess the overall extent of the incident.
Tools:
#1 Respuesta: 2
Understanding the scope of the attack and identifying which versions exhibit malicious behavior is crucial for making informed decisions if these compromised versions are present in the organization. How many versions of 3CX running on Windows have been flagged as malware?
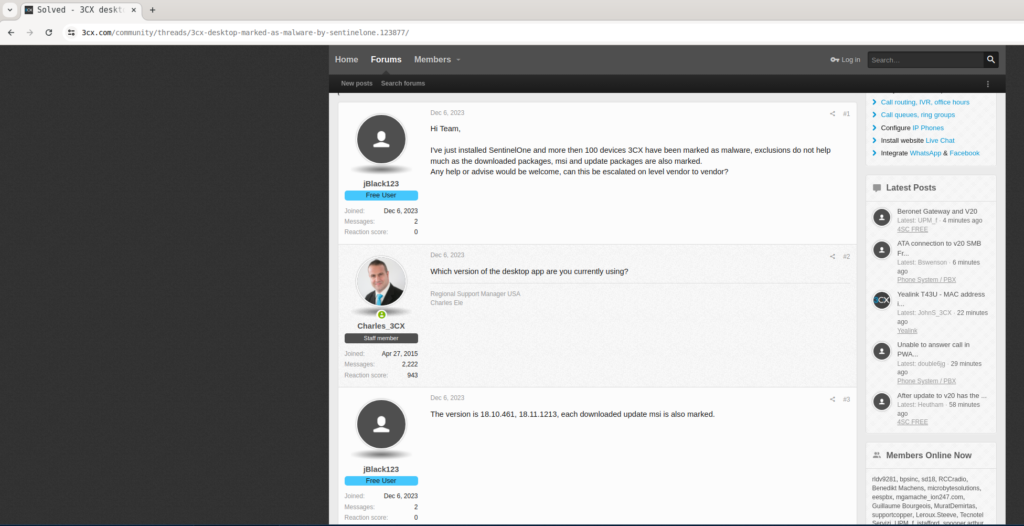
Realizamos una búsqueda avanzada en Google utilizando el siguiente término: site:https://www.3cx.com/community "3CX" + "malware", lo que nos llevó a una entrada en el foro oficial de 3CX (Solved – 3CX desktop marked as Malware by SentinelOne) . En dicha entrada, se menciona específicamente lo siguiente:
"The version is 18.10.461, 18.11.1213, each downloaded update msi is also marked."A partir de esta información, concluimos que dos versiones de 3CX han sido identificadas como maliciosas: 18.10.461 y 18.11.1213.
#2 Respuesta: 2023-03-13 06:33:26 UTC
Determining the age of the malware can help assess the extent of the compromise and track the evolution of malware families and variants. What's the UTC creation time of the .msi malware?Obtención de la evidencia
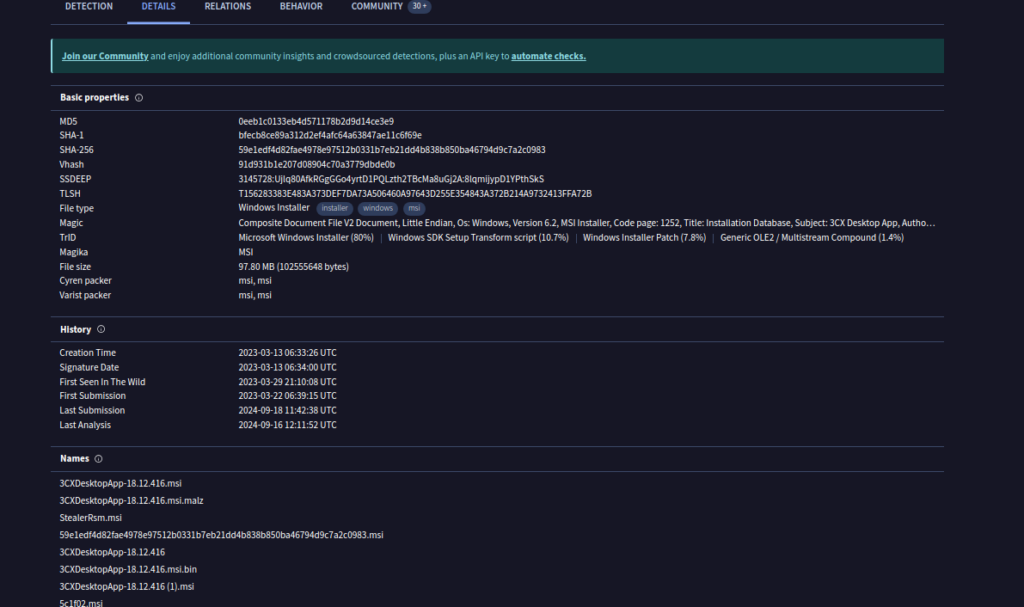
Ejecutamos el comando md5sum para obtener el hash MD5 del archivo malicioso. El comando y el resultado fueron los siguientes:
md5sum 3CXDesktopApp-18.12.416.msi
0eeb1c0133eb4d571178b2d9d14ce3e9 3CXDesktopApp-18.12.416.msiCon este hash MD5, buscamos en la base de datos de VirusTotal para rastrear el historial del archivo. A partir de la información obtenida, verificamos que el archivo malicioso fue creado el 13 de marzo de 2023 a las 06:33:26 UTC.
#3 Respuesta: ffmpeg.dll d3dcompiler_47.dll
Executable files (.exe) are frequently used as primary or secondary malware payloads, while dynamic link libraries (.dll) often load malicious code or enhance malware functionality. Analyzing files deposited by the Microsoft Software Installer (.msi) is crucial for identifying malicious files and investigating their full potential. Which malicious DLLs were dropped by the .msi file?Obtención de la evidencia
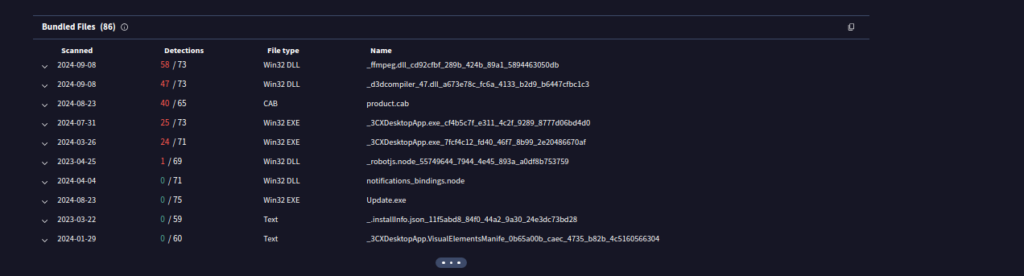
Utilizamos VirusTotal para examinar las DLL empleadas por el archivo malicioso.
A partir de esta investigación, confirmamos que las siguientes DLL maliciosas fueron depositadas por el archivo .msi:
ffmpeg.dll(_ffmpeg.dll_cd92cfbf_289b_424b_89a1_5894463050db)d3dcompiler_47.dll(_d3dcompiler_47.dll_a673e78c_fc6a_4133_b2d9_b6447cfbc1c3)
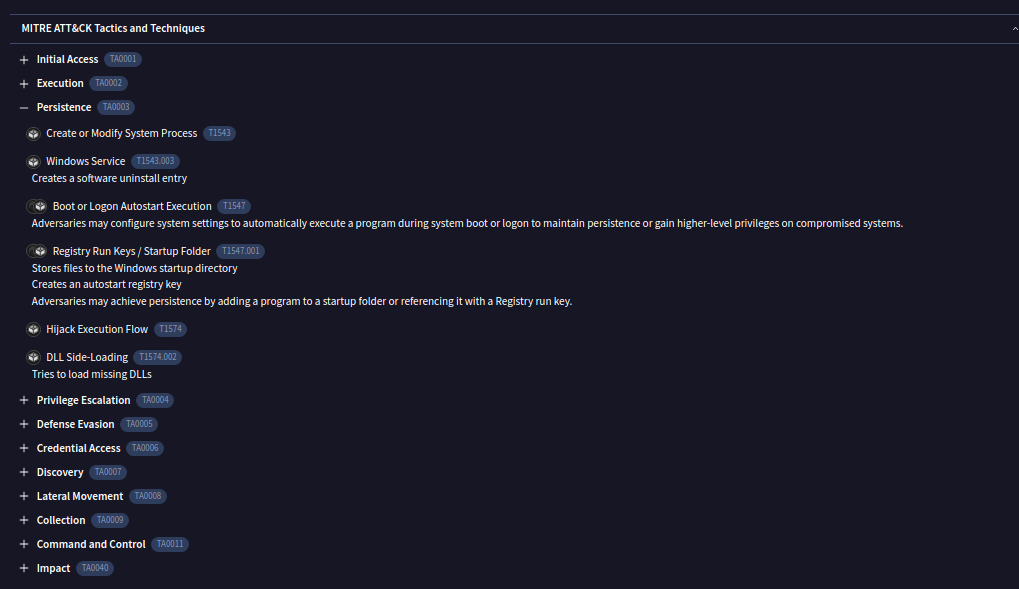
#4 Respuesta: T1574.002
Recognizing the persistence techniques used in this incident is essential for current mitigation strategies and future defense improvements. What is the MITRE sub-technique ID employed by the .msi files to load the malicious DLL?Obtención de la evidencia
Accedimos a la pestaña «Behavior» en la consola de VirusTotal.
En la sección «MITRE ATT&CK Tactics and Techniques», identificamos las técnicas empleadas por el malware, donde se mostró el uso de la sub-técnica T1574.002.
#5 Respuesta: trojan
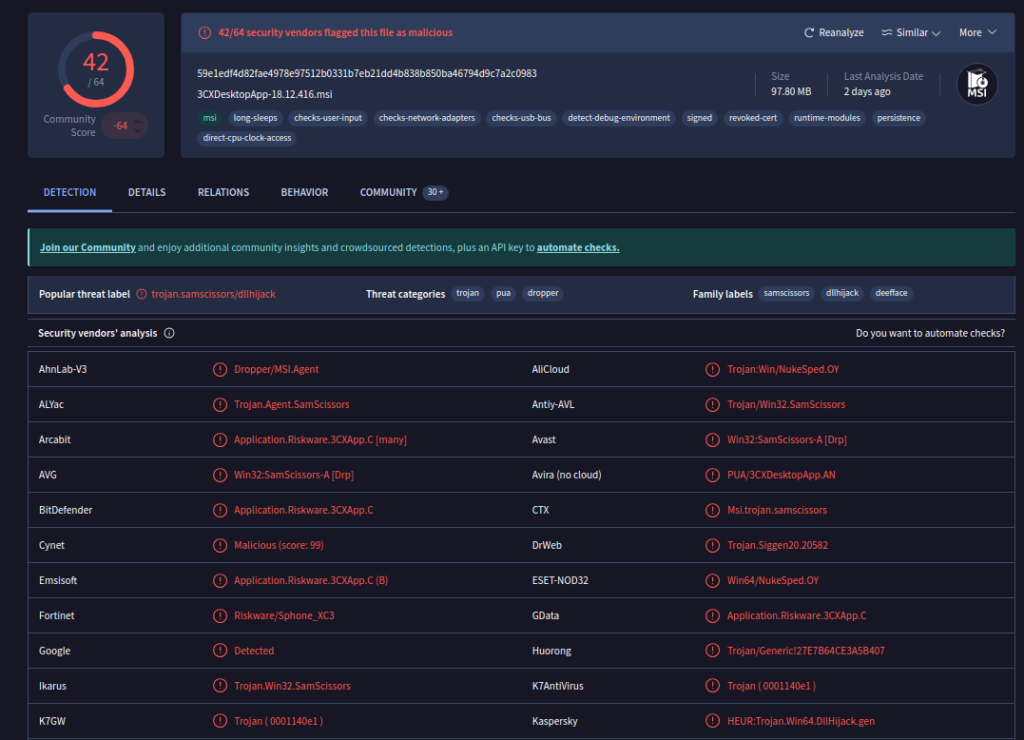
Recognizing the malware type (threat category) is essential to your investigation, as it can offer valuable insight into the possible malicious actions you'll be examining. What is the malware family of the two malicious DLLs?Obtención de la evidencia
A través de la consola de VirusTotal, en la ventana principal, se verificó que el tipo de malware es un Trojan.
Información adicional proporcionada por la plataforma:
- Popular threat label: trojan.samscissors/dllhijack
- Threat categories: trojan, PUA (Potentially Unwanted Application), dropper
- Family labels: samscissors, dllhijack, deefface
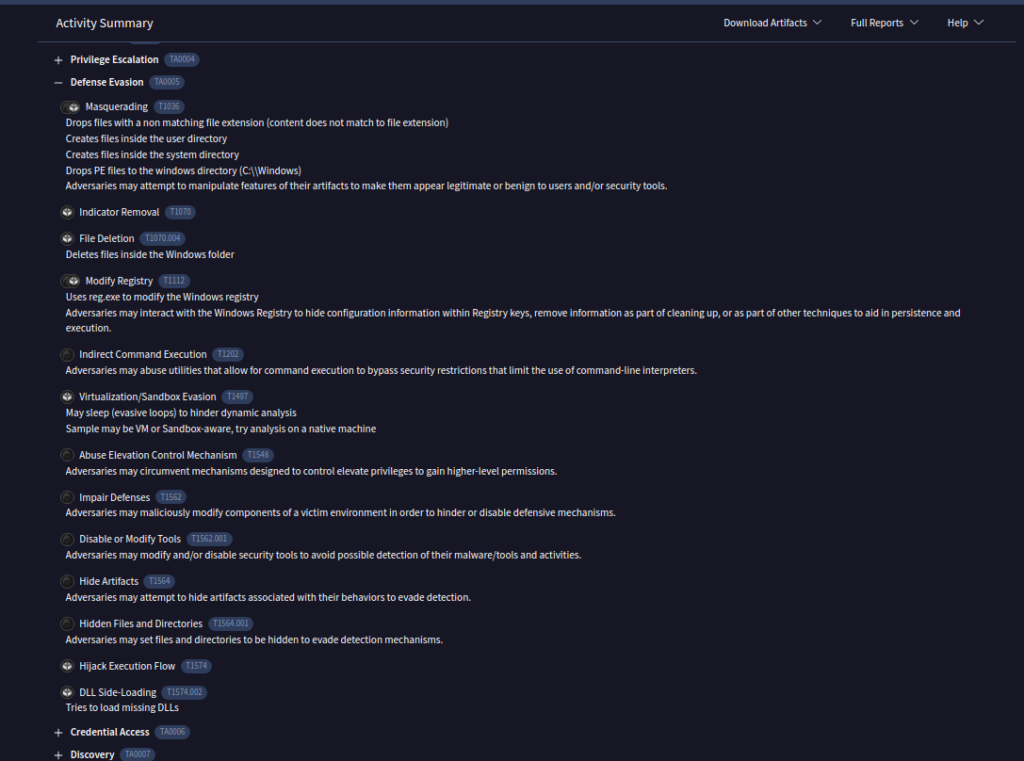
#6 Respuesta: T1497
As a threat intelligence analyst conducting dynamic analysis, it's vital to understand how malware can evade detection in virtualized environments or analysis systems. This knowledge will help you effectively mitigate or address these evasive tactics. What is the MITRE ID for the virtualization/sandbox evasion techniques used by the two malicious DLLs?Obtención de la evidencia
En la consola de VirusTotal, nos dirigimos a la sección MITRE ATT&CK Tactics and Techniques > Defense Evasion.
Confirmamos que el identificador correspondiente a la técnica de evasión de virtualización/sandbox es T1497.
Información adicional:
Técnicas empleadas:
- Virtualization/Sandbox Evasion
- T1497
- May sleep (evasive loops) to hinder dynamic analysis
- Sample may be VM or Sandbox-aware, try analysis on a native machine
#7 Respuesta: Vmware
When conducting malware analysis and reverse engineering, understanding anti-analysis techniques is vital to avoid wasting time. Which hypervisor is targeted by the anti-analysis techniques in the ffmpeg.dll file?
Obtención de la evidencia
La técnica de anti-análisis utilizada por el malware 3CX se identifica como T1497 en el marco MITRE ATT&CK, que se centra en la evasión de virtualización y sandbox.
Según podemos observar otros malwares como «S0268 Bisonal» se ejecuta en Vmware
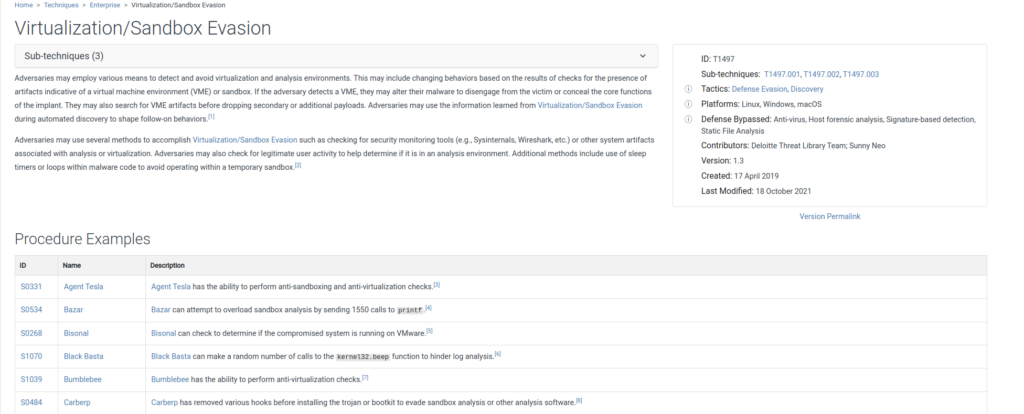
De la misma forma, Según el análisis de la documentación de InfoSec Institute, el malware emplea diversas técnicas para detectar si se está ejecutando en un entorno virtualizado o de análisis.
#8 Respuesta: RC4
Identifying the cryptographic method used in malware is crucial for understanding the techniques employed to bypass defense mechanisms and execute its functions fully. What encryption algorithm is used by the ffmpeg.dll file?Obtención de la evidencia
En el análisis publicado en el blog de Huntress (enlace), se menciona que:
After retrieving d3dcompiler_47.dll, the ffmpeg.dll binary locates and unravels this secondary payload by decrypting an RC4 stream with the key 3jB(2bsG#@c7. According to other threat intelligence, this static key is known to be attributed to DPRK threat actors.
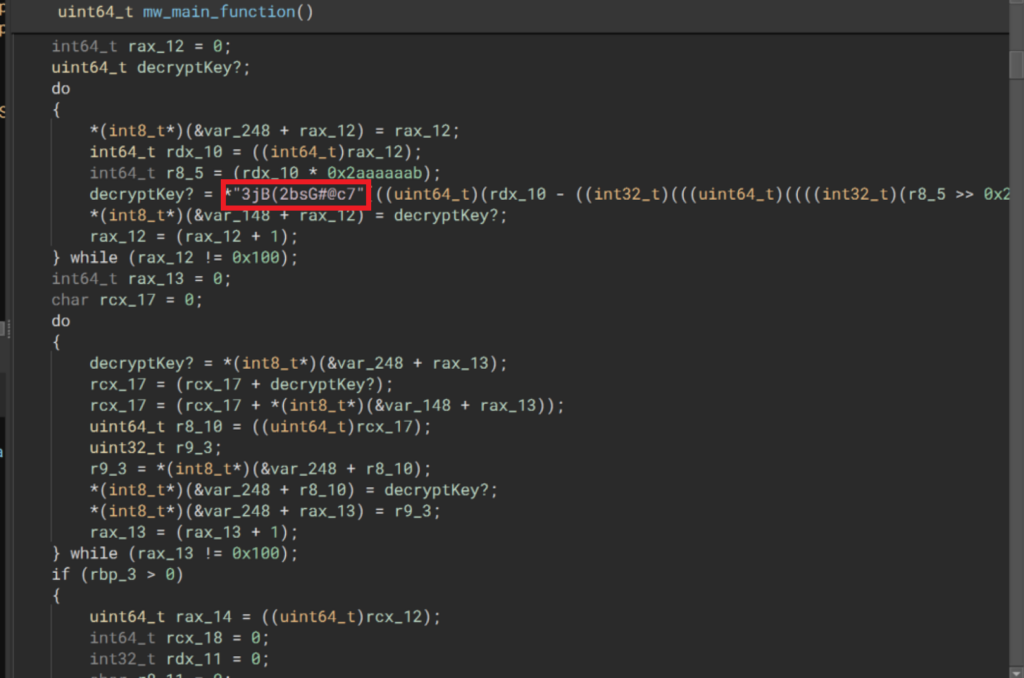
De manera similar, el blog de Forescout Vedere Labs (enlace) analiza lo siguiente:
Forescout Vedere Labs analyzed an MSI installer obtained directly from the vendor’s website that includes both the malicious DLLs and the 3CXDesktopApp executable. The initial attack is a DLL sideloading with multiple components involved. The 3CXDesktopApp package contains the following files of interest:
- exe – 3CXDesktopApp application, which serves as a shellcode loader
- dll – A malicious loader DLL used to load and execute malicious shellcode from d3dcompiler_47.dll
- dll – A DLL with an appended payload
As in a regular update, the MSI installer launches the executable Update.exe, which in turn launches 3CXDesktopApp.exe. 3CXDesktopApp.exe loads ffmpeg.dll and then hollows out a portion of the 3CXDeskttopApp.exe binary to inject code from d3dcompiler_47.dll.
After the contents of d3dcompiler_47.dll have been read into the heap space, the code decrypts the malicious shellcode appended in the file, using RC4 and the key 3jB(2bsG#@c7 – as shown below.
#8 Respuesta: Lazarus
As an analyst, you've recognized some TTPs involved in the incident, but identifying the APT group responsible will help you search for their usual TTPs and uncover other potential malicious activities. Which group is responsible for this attack?Obtención de la evidencia
En la pregunta anterior (#7), el análisis del blog de Forescout Vedere Labs (enlace) indica que:
The trojanized version of 3CXDesktopApp was observed as the first stage in a multi-step attack, which indicates that the threat is sophisticated. The threat actors behind the attack have also acquired a code signing certificate from 3CX that they have used to sign the malicious binaries. This further complicates the situation by making victims trust the malicious executable and by making it harder for security tools to detect the threat.
Based on the malicious code being used, the current campaign has been linked to North Korean APT Lazarus Group. Lazarus Group has been active since 2009 and was responsible for attacks such as the 2009 Sony breach and WannaCry. The group is also known as Labyrinth Chollima, Hidden Cobra, Guardians of Peace, ZINC and Nickel Academy.
:wq!