Arquitectura
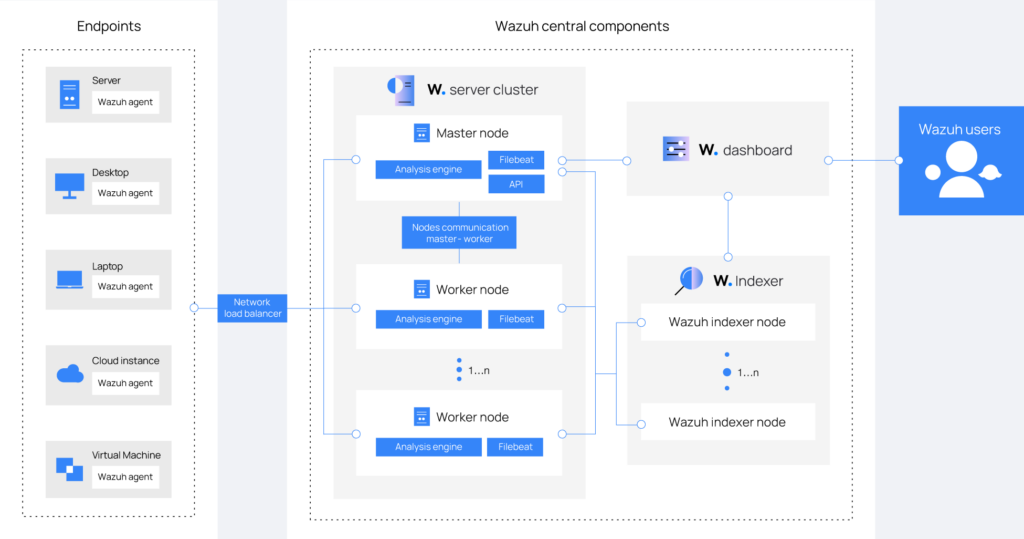
Servidores
| Servidor | IP | Rol |
|---|---|---|
| srvlwm01 | 192.168.1.100 | Wazuh Manager – Node Master |
| srvlww01 | 192.168.1.101 | Wazuh Manager – Node Worker |
| srvlww02 | 192.168.1.102 | Wazuh Manager – Node Worker |
| srvlwd01 | 192.168.1.103 | Wazuh Dashboard |
| srvlwi01 | 192.168.1.104 | Wazuh Indexer |
| srvlwi02 | 192.168.1.105 | Wazuh Indexer |
Requisitos
Sistemas Operativos Recomendados
Wazuh puede instalarse en sistemas operativos Linux de 64 bits. Las versiones soportadas son:
- Amazon Linux 2
- CentOS 7, 8
- Red Hat Enterprise Linux 7, 8, 9
- Ubuntu 16.04, 18.04, 20.04, 22.04
Requisitos de Hardware
Wazuh puede instalarse en un nodo único o en un clúster multinodo.
| Componente | RAM Mínima (GB) | CPU Mínima (Cores) | RAM Recomendada (GB) | CPU Recomendada (Cores) |
|---|---|---|---|---|
| Wazuh server | 2 | 2 | 4 | 8 |
| Wazuh indexer | 4 | 2 | 16 | 8 |
| Wazuh dashboard | 4 | 2 | 8 | 4 |
Espacio en Disco Wazuh Server
La cantidad de datos depende de las alertas generadas por segundo (APS). Aquí se detalla el espacio necesario por agente para almacenar 90 días de alertas en un servidor Wazuh, dependiendo del tipo de endpoints monitorizados.
| Endpoints Monitorizados | APS | Almacenamiento en Servidor Wazuh (GB/90 días) |
|---|---|---|
| Servidores | 0.25 | 0.1 |
| Estaciones de trabajo | 0.1 | 0.04 |
| Dispositivos de red | 0.5 | 0.2 |
Por ejemplo, para un entorno con 80 estaciones de trabajo, 10 servidores y 10 dispositivos de red, se necesitarían 6 GB de almacenamiento en el servidor Wazuh para 90 días de alertas.
Espacio en Disco Wazuh indexer
La cantidad de datos necesarios depende de las alertas generadas por segundo (APS). Esta tabla detalla el espacio estimado en disco necesario por agente para almacenar 90 días de alertas en un servidor Wazuh Indexer, según el tipo de endpoints monitoreados.
Endpoints Monitoreados
| Endpoints Monitorizados | APS | Almacenamiento en Servidor Wazuh (GB/90 días) |
|---|---|---|
| Servidores | 0.25 | 3.7 |
| Estaciones de trabajo | 0.1 | 1.5 |
| Dispositivos de red | 0.5 | 7.4 |
Instalación de Wazuh
Paso 1: Preparar el Entorno
- NOTA: He realizado la preparación del entorno desde el servidor con IP 192.168.1.100, que desempeña el rol de Master.
Instalamos curl y descargamos el script de instalación
apt install curl
curl -sO https://packages.wazuh.com/4.8/wazuh-install.sh
curl -sO https://packages.wazuh.com/4.8/config.yml
Paso 2: Configurar el Archivo config.yml
Configuramos los nodos en el archivo config.yml:
nodes:
indexer:
- name: srvlwi01
ip: "192.168.1.104"
- name: srvlwi02
ip: "192.168.1.105"
server:
- name: srvlwm01
ip: "192.168.1.100"
node_type: master
- name: srvlww01
ip: "192.168.1.101"
node_type: worker
- name: srvlww02
ip: "192.168.1.102"
node_type: worker
dashboard:
- name: srvlwd01
ip: "192.168.1.103"
Generamos los archivos de configuración:
sudo bash wazuh-install.sh --generate-config-files -i
Transferimos los archivos a todos nuestros servidores:
for ip in 192.168.1.101 192.168.1.102 192.168.1.103 192.168.1.104 192.168.1.105; do
scp * $ip:/tmp
done
Paso 3: Instalación de Wazuh Indexer
Configurar Variables de JAVA
Antes de proceder con la instalación de Wazuh Indexer, es esencial configurar las variables de entorno de JAVA. Me encontré con problemas al iniciar la parte de seguridad debido a que estas variables no estaban configuradas correctamente.
export OPENSEARCH_JAVA_HOME=/usr/share/wazuh-indexer/jdk
export JAVA_HOME=/usr/share/wazuh-indexer/jdk
export PATH=$OPENSEARCH_JAVA_HOME/bin:$PATH
export PATH=$JAVA_HOME/bin:$PATH
Instalamos Wazuh Indexer en los servidores srvlwi01 y srvlwi02:
sudo bash wazuh-install.sh --wazuh-indexer srvlwi01 -i
La salida debería ser similar a:
13/06/2024 10:02:14 INFO: Starting Wazuh installation assistant. Wazuh version: 4.7.5
13/06/2024 10:02:14 INFO: Verbose logging redirected to /var/log/wazuh-install.log
13/06/2024 10:02:18 WARNING: Hardware and system checks ignored.
13/06/2024 10:02:26 INFO: Wazuh repository added.
13/06/2024 10:02:27 INFO: --- Wazuh indexer ---
13/06/2024 10:02:27 INFO: Starting Wazuh indexer installation.
13/06/2024 10:04:06 INFO: Wazuh indexer installation finished.
13/06/2024 10:04:06 INFO: Wazuh indexer post-install configuration finished.
13/06/2024 10:04:06 INFO: Starting service wazuh-indexer.
13/06/2024 10:05:36 INFO: wazuh-indexer service started.
13/06/2024 10:05:36 INFO: Initializing Wazuh indexer cluster security settings.
13/06/2024 10:05:37 INFO: Wazuh indexer cluster initialized.
13/06/2024 10:05:37 INFO: Installation finished.Iniciamos el servicio:
sudo bash wazuh-install.sh --start-cluster -i
La salida debería ser similar a:
13/06/2024 10:09:30 INFO: Starting Wazuh installation assistant. Wazuh version: 4.7.5
13/06/2024 10:09:30 INFO: Verbose logging redirected to /var/log/wazuh-install.log
13/06/2024 10:09:32 INFO: --- Removing existing Wazuh installation ---
13/06/2024 10:09:32 INFO: Removing Wazuh indexer.
13/06/2024 10:09:37 INFO: Wazuh indexer removed.
13/06/2024 10:09:38 INFO: Installation cleaned.
13/06/2024 10:09:45 WARNING: Hardware and system checks ignored.
13/06/2024 10:09:52 INFO: Wazuh repository added.
13/06/2024 10:09:53 INFO: --- Wazuh indexer ---
13/06/2024 10:09:53 INFO: Starting Wazuh indexer installation.
13/06/2024 10:11:15 INFO: Wazuh indexer installation finished.
13/06/2024 10:11:15 INFO: Wazuh indexer post-install configuration finished.
13/06/2024 10:11:15 INFO: Starting service wazuh-indexer.
13/06/2024 10:12:23 INFO: wazuh-indexer service started.
13/06/2024 10:12:23 INFO: Initializing Wazuh indexer cluster security settings.
13/06/2024 10:12:24 INFO: Wazuh indexer cluster initialized.
13/06/2024 10:12:24 INFO: Installation finished.Posibles errores:
Si OpenSearch Security no se encuentra iniciado, lo iniciamos:
sudo /usr/share/wazuh-indexer/bin/indexer-security-init.sh
La salida debería mostrar algo como:
** This tool will be deprecated in the next major release of OpenSearch **
** https://github.com/opensearch-project/security/issues/1755 **
Security Admin v7
Will connect to 192.168.1.104:9200 … done
Connected as "CN=admin,OU=Wazuh,O=Wazuh,L=California,C=US"
OpenSearch Version: 2.10.0
Contacting opensearch cluster 'opensearch' and wait for YELLOW clusterstate …
Clustername: wazuh-indexer-cluster
Clusterstate: GREEN
Number of nodes: 2
Number of data nodes: 2
.opendistro_security index does not exists, attempt to create it … done (0-all replicas)
Populate config from /etc/wazuh-indexer/opensearch-security/
Will update '/config' with /etc/wazuh-indexer/opensearch-security/config.yml
SUCC: Configuration for 'config' created or updated
Will update '/roles' with /etc/wazuh-indexer/opensearch-security/roles.yml
SUCC: Configuration for 'roles' created or updated
Will update '/rolesmapping' with /etc/wazuh-indexer/opensearch-security/roles_mapping.yml
SUCC: Configuration for 'rolesmapping' created or updated
Will update '/internalusers' with /etc/wazuh-indexer/opensearch-security/internal_users.yml
SUCC: Configuration for 'internalusers' created or updated
Will update '/actiongroups' with /etc/wazuh-indexer/opensearch-security/action_groups.yml
SUCC: Configuration for 'actiongroups' created or updated
Will update '/tenants' with /etc/wazuh-indexer/opensearch-security/tenants.yml
SUCC: Configuration for 'tenants' created or updated
Will update '/nodesdn' with /etc/wazuh-indexer/opensearch-security/nodes_dn.yml
SUCC: Configuration for 'nodesdn' created or updated
Will update '/whitelist' with /etc/wazuh-indexer/opensearch-security/whitelist.yml
SUCC: Configuration for 'whitelist' created or updated
Will update '/audit' with /etc/wazuh-indexer/opensearch-security/audit.yml
SUCC: Configuration for 'audit' created or updated
Will update '/allowlist' with /etc/wazuh-indexer/opensearch-security/allowlist.yml
SUCC: Configuration for 'allowlist' created or updated
SUCC: Expected 10 config types for node {"updated_config_types":["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"],"updated_config_size":10,"message":null} is 10 (["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"]) due to: null
SUCC: Expected 10 config types for node {"updated_config_types":["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"],"updated_config_size":10,"message":null} is 10 (["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"]) due to: null
Done with success** This tool will be deprecated in the next major release of OpenSearch **
** https://github.com/opensearch-project/security/issues/1755 **
Security Admin v7
Will connect to 192.168.1.104:9200 … done
Connected as "CN=admin,OU=Wazuh,O=Wazuh,L=California,C=US"
OpenSearch Version: 2.10.0
Contacting opensearch cluster 'opensearch' and wait for YELLOW clusterstate …
Clustername: wazuh-indexer-cluster
Clusterstate: GREEN
Number of nodes: 2
Number of data nodes: 2
.opendistro_security index does not exists, attempt to create it … done (0-all replicas)
Populate config from /etc/wazuh-indexer/opensearch-security/
Will update '/config' with /etc/wazuh-indexer/opensearch-security/config.yml
SUCC: Configuration for 'config' created or updated
Will update '/roles' with /etc/wazuh-indexer/opensearch-security/roles.yml
SUCC: Configuration for 'roles' created or updated
Will update '/rolesmapping' with /etc/wazuh-indexer/opensearch-security/roles_mapping.yml
SUCC: Configuration for 'rolesmapping' created or updated
Will update '/internalusers' with /etc/wazuh-indexer/opensearch-security/internal_users.yml
SUCC: Configuration for 'internalusers' created or updated
Will update '/actiongroups' with /etc/wazuh-indexer/opensearch-security/action_groups.yml
SUCC: Configuration for 'actiongroups' created or updated
Will update '/tenants' with /etc/wazuh-indexer/opensearch-security/tenants.yml
SUCC: Configuration for 'tenants' created or updated
Will update '/nodesdn' with /etc/wazuh-indexer/opensearch-security/nodes_dn.yml
SUCC: Configuration for 'nodesdn' created or updated
Will update '/whitelist' with /etc/wazuh-indexer/opensearch-security/whitelist.yml
SUCC: Configuration for 'whitelist' created or updated
Will update '/audit' with /etc/wazuh-indexer/opensearch-security/audit.yml
SUCC: Configuration for 'audit' created or updated
Will update '/allowlist' with /etc/wazuh-indexer/opensearch-security/allowlist.yml
SUCC: Configuration for 'allowlist' created or updated
SUCC: Expected 10 config types for node {"updated_config_types":["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"],"updated_config_size":10,"message":null} is 10 (["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"]) due to: null
SUCC: Expected 10 config types for node {"updated_config_types":["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"],"updated_config_size":10,"message":null} is 10 (["allowlist","tenants","rolesmapping","nodesdn","audit","roles","whitelist","internalusers","actiongroups","config"]) due to: null
Done with successPaso 4: Configurar Permisos y Memoria
Ajustamos los permisos y la configuración de memoria:
Permisos
sudo chown -R wazuh-indexer:wazuh-indexer /etc/wazuh-indexer
sudo chown -R wazuh-indexer:wazuh-indexer /var/lib/wazuh-indexerMemoria
vi /etc/wazuh-indexer/jvm.options
-Xms4g
-Xmx4gIntentamos iniciar nuevamente el servicio:
sudo bash wazuh-install.sh --start-cluster -i
Verificamos que el servicio haya iniciado correctamente:
sudo systemctl status wazuh-indexer
La salida debería ser similar a la siguiente:
● wazuh-indexer.service - Wazuh-indexer
Loaded: loaded (/lib/systemd/system/wazuh-indexer.service; enabled; preset: enabled)
Active: active (running) since Thu 2024-06-13 10:12:23 UTC; 5min ago
Docs: https://documentation.wazuh.com
Main PID: 3203 (java)
Tasks: 52 (limit: 1100)
Memory: 746.8M
CPU: 1min 18.120s
CGroup: /system.slice/wazuh-indexer.service
└─3203 /usr/share/wazuh-indexer/jdk/bin/java -Xshare:auto -Dopensearch.networkaddress.cache.ttl=60 -Dopensearch.networkaddress.cache.negative.ttl=10 -XX:+AlwaysPreTouch -Xss1m -Djava.awt.headless=true -Dfile.encoding=UTF-8 -Djna.nosys=true -XX:-OmitStackTraceInFastThr>
Jun 13 10:11:17 srvlwi02 systemd[1]: Starting wazuh-indexer.service - Wazuh-indexer…
Jun 13 10:11:22 srvlwi02 systemd-entrypoint[3203]: WARNING: A terminally deprecated method in java.lang.System has been called
Jun 13 10:11:22 srvlwi02 systemd-entrypoint[3203]: WARNING: System::setSecurityManager has been called by org.opensearch.bootstrap.OpenSearch (file:/usr/share/wazuh-indexer/lib/opensearch-2.8.0.jar)
Jun 13 10:11:22 srvlwi02 systemd-entrypoint[3203]: WARNING: Please consider reporting this to the maintainers of org.opensearch.bootstrap.OpenSearch
Jun 13 10:11:22 srvlwi02 systemd-entrypoint[3203]: WARNING: System::setSecurityManager will be removed in a future release
Jun 13 10:11:26 srvlwi02 systemd-entrypoint[3203]: WARNING: A terminally deprecated method in java.lang.System has been called
Jun 13 10:11:26 srvlwi02 systemd-entrypoint[3203]: WARNING: System::setSecurityManager has been called by org.opensearch.bootstrap.Security (file:/usr/share/wazuh-indexer/lib/opensearch-2.8.0.jar)
Jun 13 10:11:26 srvlwi02 systemd-entrypoint[3203]: WARNING: Please consider reporting this to the maintainers of org.opensearch.bootstrap.Security
Jun 13 10:11:26 srvlwi02 systemd-entrypoint[3203]: WARNING: System::setSecurityManager will be removed in a future release
Jun 13 10:12:23 srvlwi02 systemd[1]: Started wazuh-indexer.service - Wazuh-indexer.
Comprobamos que el puerto de OpenSearch esté activo:
lsof -i | grep 9200
La salida debería ser similar a:
java 3203 wazuh-indexer 577u IPv6 24150 0t0 TCP 192.168.1.105:9200 (LISTEN)
Verificamos que el servicio de OpenSearch funcione correctamente realizando una consulta:
sudo tar -axf wazuh-install-files.tar wazuh-install-files/wazuh-passwords.txt -O | grep -P "'admin'" -A 1
La salida debería mostrar algo como:
indexer_username: 'admin'
indexer_password: 'rV**********************************************'
Luego, ejecutamos la siguiente consulta:
curl -k -u admin:rV********************************************** https://192.168.1.104:9200
La respuesta debería ser algo similar a:
{
"name" : "srvlwi01",
"cluster_name" : "wazuh-indexer-cluster",
"cluster_uuid" : "q4mM1RlUTIS_hXiWFShO6A",
"version" : {
"number" : "7.10.2",
"build_type" : "rpm",
"build_hash" : "eee49cb340edc6c4d489bcd9324dda571fc8dc03",
"build_date" : "2023-09-20T23:54:29.889267151Z",
"build_snapshot" : false,
"lucene_version" : "9.7.0",
"minimum_wire_compatibility_version" : "7.10.0",
"minimum_index_compatibility_version" : "7.0.0"
},
"tagline" : "The OpenSearch Project: https://opensearch.org/"
}
Paso 5: Instalación de Wazuh Manager
Instalamos Wazuh Manager en el nodo master y los workers:
sudo bash wazuh-install.sh --wazuh-server srvlwm01 -i
La respuesta debería ser algo similar a:
14/06/2024 07:35:07 INFO: Starting Wazuh installation assistant. Wazuh version: 4.8.0
14/06/2024 07:35:07 INFO: Verbose logging redirected to /var/log/wazuh-install.log
14/06/2024 07:35:08 WARNING: Hardware and system checks ignored.
14/06/2024 07:35:17 INFO: Wazuh repository added.
14/06/2024 07:35:18 INFO: --- Wazuh server ---
14/06/2024 07:35:18 INFO: Starting the Wazuh manager installation.
14/06/2024 07:36:53 INFO: Wazuh manager installation finished.
14/06/2024 07:36:54 INFO: Wazuh manager vulnerability detection configuration finished.
14/06/2024 07:36:54 INFO: Starting service wazuh-manager.
14/06/2024 07:37:18 INFO: wazuh-manager service started.
14/06/2024 07:37:18 INFO: Starting Filebeat installation.
14/06/2024 07:37:24 INFO: Filebeat installation finished.
14/06/2024 07:37:25 INFO: Filebeat post-install configuration finished.
14/06/2024 07:37:57 INFO: Starting service filebeat.
14/06/2024 07:37:59 INFO: filebeat service started.
14/06/2024 07:37:59 INFO: Installation finished.Verificamos la instalación:
/var/ossec/bin/cluster_control -l
La respuesta debería ser algo similar a:
NAME TYPE VERSION ADDRESS
srvlwm01 master 4.8.0 192.168.1.100
srvlww01 worker 4.8.0 192.168.1.101
srvlww02 worker 4.8.0 192.168.1.102Paso 6: Instalación del Dashboard
Instalamos Wazuh Dashboard:
sudo bash wazuh-install.sh --wazuh-dashboard srvlwd01 -i
La respuesta debería ser algo similar a:
14/06/2024 08:52:07 INFO: Starting Wazuh installation assistant. Wazuh version: 4.8.0
14/06/2024 08:52:07 INFO: Verbose logging redirected to /var/log/wazuh-install.log
14/06/2024 08:52:09 WARNING: Hardware and system checks ignored.
14/06/2024 08:52:14 INFO: --- Dependencies ----
14/06/2024 08:52:14 INFO: Installing gawk.
14/06/2024 08:52:17 INFO: Wazuh web interface port will be 443.
14/06/2024 08:52:22 INFO: --- Dependencies ----
14/06/2024 08:52:22 INFO: Installing apt-transport-https.
14/06/2024 08:52:23 INFO: Installing software-properties-common.
14/06/2024 08:52:38 INFO: Installing gnupg.
14/06/2024 08:52:46 INFO: Wazuh repository added.
14/06/2024 08:52:47 INFO: --- Wazuh dashboard ----
14/06/2024 08:52:47 INFO: Starting Wazuh dashboard installation.
14/06/2024 08:53:43 INFO: Wazuh dashboard installation finished.
14/06/2024 08:53:43 INFO: Wazuh dashboard post-install configuration finished.
14/06/2024 08:53:43 INFO: Starting service wazuh-dashboard.
14/06/2024 08:53:44 INFO: wazuh-dashboard service started.
14/06/2024 08:54:14 INFO: Initializing Wazuh dashboard web application.
14/06/2024 08:54:15 INFO: Wazuh dashboard web application initialized.
14/06/2024 08:54:15 INFO: --- Summary ---
14/06/2024 08:54:15 INFO: You can access the web interface https://192.168.1.103:443
User: admin
Password: ****************************************************
14/06/2024 08:54:15 INFO: --- Dependencies ----
14/06/2024 08:54:15 INFO: Removing gawk.
14/06/2024 08:54:17 INFO: Installation finished.
Accedemos al dashboard mediante la URL proporcionada:
https://192.168.1.103:443
Usuario: admin
Contraseña: [proporcionada durante la instalación]
En la próxima entrada, veremos cómo configurar el balanceador de carga e instalar un agente.
:wq!
ahora pega el dfir iris en vez del thehive por el paso a pago, yo ya me habia acostumbrado a thehive 🙁 , aun estoy en el laboratorio para implementar iris