¿Que es Sysmon?
System Monitor ( Sysmon ) es un servicio del sistema de Windows y un controlador de dispositivo que, una vez instalado en un sistema, permanece residente en todos los reinicios del sistema para monitorear y registrar la actividad del sistema en el registro de eventos de Windows. Proporciona información detallada sobre creaciones de procesos, conexiones de red y cambios en el tiempo de creación de archivos. Al recopilar los eventos que genera utilizando Windows Event Collection o los agentes SIEM y luego analizarlos, puede identificar actividades maliciosas o anómalas y comprender cómo operan los intrusos y el malware en su red.
Para descargar Sysmon accedemos a la pagina oficial de Microsft https://docs.microsoft.com/es-es/sysinternals/downloads/sysmon
Agregamos el fichero sysmon.xml de configuración en la carpeta (Configuración obtenida de: https://github.com/Hestat/ossec-sysmon)
<Sysmon schemaversion="4.30">
<HashAlgorithms>sha256</HashAlgorithms>
<!-- This now also determines the file names of the files preserved (String) -->
<CheckRevocation />
<DnsLookup>False</DnsLookup>
<!-- Disables lookup behavior, default is True (Boolean) -->
<ArchiveDirectory>Java</ArchiveDirectory>
<!-- Sets the name of the directory in the C:\ root where preserved files will be saved (String)-->
<EventFiltering>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 1 == Process Creation. -->
<ProcessCreate onmatch="include">
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">sethc.exe</ParentImage>
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">utilman.exe</ParentImage>
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">osk.exe</ParentImage>
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">Magnify.exe</ParentImage>
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">DisplaySwitch.exe</ParentImage>
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">Narrator.exe</ParentImage>
<ParentImage name="technique_id=T1015,technique_name=Accessibility Features" condition="image">AtBroker.exe</ParentImage>
<OriginalFileName name="technique_id=T1138,technique_name=Application Shimming" condition="is">sdbinst.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1197,technique_name=BITS Jobs" condition="is">bitsadmin.exe</OriginalFileName>
<Rule name="Eventviewer Bypass UAC" groupRelation="and">
<ParentImage name="technique_id=T1088,technique_name=Bypass User Account Control" condition="image">eventvwr.exe</ParentImage>
<Image condition="is not">c:\windows\system32\mmc.exe</Image>
</Rule>
<ParentImage name="technique_id=T1088,technique_name=Bypass User Account Control" condition="image">fodhelper.exe</ParentImage>
<CommandLine name="technique_id=T1027,technique_name=Obfuscated Files or Information" condition="contains">ˆ</CommandLine>
<ParentCommandLine name="technique_id=T1204,technique_name=User Execution" condition="is">C:\Windows\explorer.exe</ParentCommandLine>
<Rule name="Fltmc" groupRelation="and">
<OriginalFileName name="technique_id=T1054,technique_name=Indicator Blocking" condition="is">fltMC.exe</OriginalFileName>
<CommandLine name="technique_id=T1054,technique_name=Indicator Blocking" condition="contains">unload;detach</CommandLine>
</Rule>
<Rule groupRelation="or">
<OriginalFileName name="technique_id=T1063,technique_name=Security Software Discovery" condition="is">fltMC.exe</OriginalFileName>
<CommandLine name="technique_id=T1063,technique_name=Security Software Discovery" condition="contains">misc::mflt</CommandLine>
</Rule>
<Rule name="InstallUtil" groupRelation="and">
<OriginalFileName name="technique_id=T1118,technique_name=InstallUtil" condition="is">InstallUtil.exe</OriginalFileName>
<CommandLine name="technique_id=T1118,technique_name=InstallUtil" condition="contains all">/logfile=;/LogToConsole=false;/U</CommandLine>
</Rule>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="is">whoami.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="is">ipconfig.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">tasklist.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">taskmgr.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="contains any">systeminfo.exe;sysinfo.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1049,technique_name=System Network Connections Discovery" condition="is">netstat.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="image">qprocess.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="is">nslookup.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1018,technique_name=Remote System Discovery" condition="contains any">net.exe;net1.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="is">quser.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">query.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="is">tracert.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1083,technique_name=File and Directory Discovery" condition="is">tree.com</OriginalFileName>
<OriginalFileName name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="is">route.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1134,technique_name=Access Token Manipulation" condition="is">runas.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1112,technique_name=Modify Registry" condition="is">reg.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1112,technique_name=Modify Registry" condition="is">regedit.exe</OriginalFileName>
<OriginalFileName condition="is">taskkill.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1063,technique_name=Security Software Discovery" condition="is">netsh.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1087,technique_name=Account Discovery" condition="is">klist.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1070,technique_name=Indicator Removal on Host" condition="is">wevtutil.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1053,technique_name=Scheduled Task" condition="is">taskeng.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1117,technique_name=Regsvr32" condition="is">regsvr32.exe</OriginalFileName>
<ParentImage name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="image">wmiprvse.exe</ParentImage>
<OriginalFileName name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="is">wmiprvse.exe</OriginalFileName>
<OriginalFileName condition="is">hh.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1059,technique_name=Command-Line Interface" condition="is">cmd.exe</OriginalFileName>
<ParentImage name="technique_id=T1059,technique_name=Command-Line Interface" condition="image">cmd.exe</ParentImage>
<Image name="technique_id=T1086,technique_name=PowerShell" condition="image">powershell.exe</Image>
<ParentImage name="technique_id=T1086,technique_name=PowerShell" condition="image">powershell.exe</ParentImage>
<ParentImage name="technique_id=T1086,technique_name=PowerShell" condition="image">powershell_ise.exe</ParentImage>
<OriginalFileName name="technique_id=T1202,technique_name=Indirect Command Execution" condition="is">bash.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1073,technique_name=DLL Side-Loading" condition="is">odbcconf.exe</OriginalFileName>
<Image name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">pcalua.exe</Image>
<OriginalFileName name="technique_id=T1202,technique_name=Indirect Command Execution" condition="is">cscript.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1202,technique_name=Indirect Command Execution" condition="is">wscript.exe</OriginalFileName>
<ParentImage name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">pcalua.exe</ParentImage>
<ParentImage name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">cscript.exe</ParentImage>
<ParentImage name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">wscript.exe</ParentImage>
<ParentImage name="technique_id=T1170,technique_name=Mshta" condition="image">mshta.exe</ParentImage>
<ParentImage name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">control.exe</ParentImage>
<OriginalFileName name="technique_id=T1170,technique_name=Mshta" condition="is">mshta.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1158,technique_name=Hidden Files and DirectoriesHidden Files and Directories" condition="is">attrib.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1087,technique_name=Account Discovery" condition="is">cmdkey.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="contains any">nbtstat.exe;nbtinfo.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">qwinsta.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">rwinsta.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1053,technique_name=Scheduled Tasks" condition="contains any">schtasks.exe;sctasks.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">replace.exe</OriginalFileName>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">jjs.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">appcmd.exe</Image>
<OriginalFileName name="technique_id=T1031,technique_name=Modify Existing Service" condition="is">sc.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1202,technique_name=Indirect Command Execution" condition="is">certutil.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1081,technique_name=Credentials in Files" condition="is">findstr.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1081,technique_name=Credentials in Files" condition="is">where.exe</OriginalFileName>
<Image name="technique_id=T1222,technique_name=File Permissions Modification" condition="image">forfiles.exe</Image>
<OriginalFileName name="technique_id=T1222,technique_name=File Permissions Modification" condition="contains any">icacls.exe;cacls.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1074,technique_name=Data Staged" condition="is">xcopy.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1074,technique_name=Data Staged" condition="is">robocopy.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1222,technique_name=File Permissions Modification" condition="is">takeown.exe</OriginalFileName>
<OriginalFileName name="technique_id=T,technique_name=" condition="is">makecab.exe</OriginalFileName>
<OriginalFileName name="technique_id=T,technique_name=" condition="is">wusa.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1490,technique_name=Inhibit System Recovery" condition="is">vassadmin.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="contains any">nltest.exe;nltestk.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1202,technique_name=Indirect Command Execution" condition="is">winrs.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1088,technique_name=Bypass User Account Control" condition="is">computerdefaults.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1088,technique_name=Bypass User Account Control" condition="is">dism.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1088,technique_name=Bypass User Account Control" condition="is">fodhelper.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1078,technique_name=Valid Accounts" condition="is">djoin.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1040,technique_name=Network Sniffing" condition="is">PktMon.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="is">mofcomp.exe</OriginalFileName>
<Image name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="begin with">C:\WINDOWS\system32\wbem\scrcons.exe</Image>
<OriginalFileName name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="is">ScrCons</OriginalFileName>
<Rule name="Extensible Storage Engine Utilities" groupRelation="and">
<OriginalFileName name="technique_id=T1003,technique_name=Credential Dumping" condition="is">esentutl.exe</OriginalFileName>
<CommandLine name="technique_id=T1003,technique_name=Credential Dumping" condition="contains all">/y;/vss/d</CommandLine>
</Rule>
<Rule name="Domain Name" groupRelation="and">
<OriginalFileName name="technique_id=1482,technique_name=Domain Trust Discovery" condition="is">nltestrk.exe</OriginalFileName>
<CommandLine name="technique_id=T1482,technique_name=Domain Trust Discovery" condition="contains">/domain_trusts</CommandLine>
</Rule>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">ATBroker.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">csc.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">dfsvc.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1035,technique_name=Service Execution" condition="is">dnscmd.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1096,technique_name=NTFS File Attributes" condition="is">esentutl.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1105,technique_name=Remote File Copy" condition="is">expand</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">extexport.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1096,technique_name=NTFS File Attributes" condition="is">extrac32.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1105,technique_name=Remote File Copy" condition="is">IEExec.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">ilasm.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">InfDefaultInstall.EXE</OriginalFileName>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">jsc.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">vbc.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">Microsoft.Workflow.Compiler.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">msconfig.EXE</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">Msdt.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">msiexec.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">odbcconf.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">PresentationHost.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1105,technique_name=Remote File Copy" condition="is">Print.Exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">rasdlui.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">RegisterCimProvider2.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">RegisterCimProvider.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1003,technique_name=Credential Dumping" condition="is">RpcPing.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">ScriptRunner.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1003,technique_name=Credential Dumping" condition="is">TTTracer.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">verclsid.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">wab.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1088,technique_name=Bypass User Account Control" condition="is">WSReset.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1088,technique_name=Bypass User Account Control" condition="is">xwizard.exe</OriginalFileName>
<Rule name="Mavinject" groupRelation="and">
<OriginalFileName name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="contains any">Mavinject.exe;mavinject64.exe</OriginalFileName>
<CommandLine name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="contains">/INJECTRUNNING</CommandLine>
</Rule>
<Rule name="Mavinject" groupRelation="and">
<OriginalFileName name="technique_id=T1191,technique_name=CMSTP" condition="is">CMSTP.exe</OriginalFileName>
<CommandLine name="technique_id=T1191,technique_name=CMSTP" condition="contains all">/ni;/s</CommandLine>
</Rule>
<OriginalFileName name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">MSBuild.exe</OriginalFileName>
<ParentImage name="technique_id=T1137,technique_name=Office Application Startup" condition="image">excel.exe</ParentImage>
<ParentImage name="technique_id=T1137,technique_name=Office Application Startup" condition="image">winword.exe</ParentImage>
<ParentImage name="technique_id=T1137,technique_name=Office Application Startup" condition="image">powerpnt.exe</ParentImage>
<ParentImage name="technique_id=T1137,technique_name=Office Application Startup" condition="image">outlook.exe</ParentImage>
<ParentImage name="technique_id=T1137,technique_name=Office Application Startup" condition="image">msaccess.exe</ParentImage>
<ParentImage name="technique_id=T1137,technique_name=Office Application Startup" condition="image">mspub.exe</ParentImage>
<OriginalFileName name="technique_id=T1121,technique_name=Regsvcs/Regasm" condition="contains any">regsvcs.exe;regasm.exe</OriginalFileName>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">SyncAppvPublishingServer.exe</Image>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">PsList.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1007,technique_name=System Service Discovery" condition="is">PsService.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1035,technique_name=Service Execution" condition="is">PsExec.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1035,technique_name=Service Execution" condition="is">PsExec.c</OriginalFileName>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="is">PsGetSID.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1089,technique_name=Disabling Security Tools" condition="is">PsKill.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1089,technique_name=Disabling Security Tools" condition="is">PKill.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1003,technique_name=Credential Dumping" condition="contains">ProcDump</OriginalFileName>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="is">PsLoggedOn.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1105,technique_name=Remote File Copy" condition="image">PsFile.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1088,technique_name=Bypass User Account Control" condition="contains">ShellRunas</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">PipeList.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1083,technique_name=File and Directory Discovery" condition="is">AccessChk.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1083,technique_name=File and Directory Discovery" condition="is">AccessEnum.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="is">LogonSessions.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1005,technique_name=Data from Local System" condition="is">PsLogList.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1057,technique_name=Process Discovery" condition="is">PsInfo.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1007,technique_name=System Service Discovery" condition="contains">LoadOrd</OriginalFileName>
<OriginalFileName name="technique_id=T1098,technique_name=Account Manipulation" condition="is">PsPasswd.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1012,technique_name=Query Registry" condition="is">ru.exe</OriginalFileName>
<OriginalFileName name="technique_id=T1012,technique_name=Query Registry" condition="contains">Regsize</OriginalFileName>
<OriginalFileName name="technique_id=T1003,technique_name=Credential Dumping" condition="is">ProcDump</OriginalFileName>
<CommandLine name="technique_id=T1003,technique_name=Credential Dumping" condition="is">-ma lsass.exe</CommandLine>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\PerfLogs\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\$Recycle.bin\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Intel\Logs\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\Default\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\Public\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\NetworkService\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Fonts\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Debug\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Media\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Help\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\addins\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\repair\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\security\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\system32\config\systemprofile\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">VolumeShadowCopy</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">\htdocs\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">\wwwroot\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">\Temp\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">\Appdata\Local\</Image>
<Rule name="Control Panel Items" groupRelation="or">
<CommandLine name="technique_id=T1196,technique_name=Control Panel Items" condition="contains all">control;/name</CommandLine>
<CommandLine name="technique_id=T1196,technique_name=Control Panel Items" condition="contains all">rundll32.exe;shell32.dll;Control_RunDLL</CommandLine>
</Rule>
<Rule name="Windows Defender tampering" groupRelation="and">
<Image name="technique_id=T1089,technique_name=Disabling Security Tools" condition="image">MpCmdRun.exe</Image>
<CommandLine name="technique_id=T1089,technique_name=Disabling Security Tools" condition="contains any">Add-MpPreference;RemoveDefinitions;DisableIOAVProtection</CommandLine>
</Rule>
<OriginalFileName name="technique_id=T1028,technique_name=Windows Remote Management" condition="is">wsmprovhost.exe</OriginalFileName>
<Image name="technique_id=T1028,technique_name=Windows Remote Management" condition="image">winrm.cmd</Image>
</ProcessCreate>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 2 == File Creation Time. -->
<FileCreateTime onmatch="include">
<Image name="technique_id=T1099,technique_name=Timestomp" condition="begin with">C:\Temp</Image>
<Image name="technique_id=T1099,technique_name=Timestomp" condition="begin with">C:\Windows\Temp</Image>
<Image name="technique_id=T1099,technique_name=Timestomp" condition="begin with">C:\Tmp</Image>
<Image name="technique_id=T1099,technique_name=Timestomp" condition="begin with">C:\Users</Image>
</FileCreateTime>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 3 == Network Connection. -->
<NetworkConnect onmatch="include">
<Image name="technique_id=T1021,technique_name=Remote Services" condition="image">vnc.exe</Image>
<Image name="technique_id=T1021,technique_name=Remote Services" condition="image">vncviewer.exe</Image>
<Image name="technique_id=T1021,technique_name=Remote Services" condition="image">vncservice.exe</Image>
<Image name="technique_id=T1035,technique_name=Service Execution" condition="image">winexesvc.exe</Image>
<Image name="technique_id=T1197,technique_name=BITS Jobs" condition="image">bitsadmin.exe</Image>
<Image name="technique_id=T1021,technique_name=Remote Services" condition="image">omniinet.exe</Image>
<Image name="technique_id=T1021,technique_name=Remote Services" condition="image">hpsmhd.exe</Image>
<Image name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="image">ipconfig.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">tasklist.exe</Image>
<Image name="technique_id=T1049,technique_name=System Network Connections Discovery" condition="image">netstat.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">qprocess.exe</Image>
<Image name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="image">nslookup.exe</Image>
<Image name="technique_id=T1018,technique_name=Remote System Discovery" condition="image">net.exe</Image>
<Image name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="image">quser.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">query.exe</Image>
<Image name="technique_id=T1134,technique_name=Access Token Manipulation" condition="image">runas.exe</Image>
<Image name="technique_id=T1112,technique_name=Modify Registry" condition="image">reg.exe</Image>
<Image name="technique_id=T1063,technique_name=Security Software Discovery" condition="image">netsh.exe</Image>
<Image condition="image">klist.exe</Image>
<Image name="technique_id=T1070,technique_name=Indicator Removal on Host" condition="image">wevtutil.exe</Image>
<Image name="technique_id=T1053,technique_name=Scheduled Task" condition="image">taskeng.exe</Image>
<Image name="technique_id=T1117,technique_name=Regsvr32" condition="image">regsvr32.exe</Image>
<Image condition="image">hh.exe</Image>
<Image name="technique_id=T1059,technique_name=Command-Line Interface" condition="image">cmd.exe</Image>
<Image name="technique_id=T1086,technique_name=PowerShell" condition="image">powershell.exe</Image>
<Image name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">bash.exe</Image>
<Image name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">pcalua.exe</Image>
<Image name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">cscript.exe</Image>
<Image name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">wscript.exe</Image>
<Image name="technique_id=T1170,technique_name=Mshta" condition="image">mshta.exe</Image>
<Image name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="image">nbtstat.exe</Image>
<Image name="technique_id=T1069,technique_name=Permission Groups Discovery" condition="image">net1.exe</Image>
<Image name="technique_id=T1018,technique_name=Remote System Discovery" condition="image">nslookup.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">qwinsta.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">rwinsta.exe</Image>
<Image condition="image">schtasks.exe</Image>
<Image condition="image">taskkill.exe</Image>
<Image name="technique_id=T1031,technique_name=Modify Existing Service" condition="image">sc.exe</Image>
<Image name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="image">nltest.exe</Image>
<Image name="technique_id=T1202,technique_name=Indirect Command Execution" condition="image">winrs.exe</Image>
<Image name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="is">dfsvc.exe</Image>
<Image name="technique_id=T1035,technique_name=Service Execution" condition="is">dnscmd.exe</Image>
<Image name="technique_id=T1096,technique_name=NTFS File Attributes" condition="is">esentutl.exe</Image>
<Image name="technique_id=T1105,technique_name=Remote File Copy" condition="is">expand.exe</Image>
<Image name="technique_id=T1105,technique_name=Remote File Copy" condition="is">extrac32.exe</Image>
<Image name="technique_id=T1105,technique_name=Remote File Copy" condition="is">IEExec.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">Msdt.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">msiexec.exe</Image>
<Image name="technique_id=T1105,technique_name=Remote File Copy" condition="is">Print.Exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">RegisterCimProvider.exe</Image>
<Image name="technique_id=T1003,technique_name=Credential Dumping" condition="is">RpcPing.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="is">ScriptRunner.exe</Image>
<Image name="technique_id=T1088,technique_name=Bypass User Account Control" condition="is">xwizard.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">Mavinject.exe</Image>
<Image name="technique_id=T1053,technique_name=Scheduled Task" condition="image">at.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">certutil.exe</Image>
<Image condition="image">cmd.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Script Proxy Execution" condition="image">cscript.exe</Image>
<Image condition="image">java.exe</Image>
<Image name="technique_id=T1170,technique_name=Mshta" condition="image">mshta.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">msiexec.exe</Image>
<Image name="technique_id=T1069,technique_name=Permission Groups Discovery" condition="image">net.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">notepad.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">powershell.exe</Image>
<Image name="technique_id=T1012,technique_name=Query Registry" condition="image">reg.exe</Image>
<Image name="technique_id=T1218,technique_name=Regsvr32" condition="image">regsvr32.exe</Image>
<Image name="technique_id=T1085,technique_name=Rundll32" condition="image">rundll32.exe</Image>
<Image name="technique_id=T1031,technique_name=Modify Existing Service" condition="image">sc.exe</Image>
<Image name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="image">wmic.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Script Proxy Execution" condition="image">wscript.exe</Image>
<Image condition="image">driverquery.exe</Image>
<Image condition="image">dsquery.exe</Image>
<Image condition="image">hh.exe</Image>
<Image condition="image">infDefaultInstall.exe</Image>
<Image condition="image">javaw.exe</Image>
<Image condition="image">javaws.exe</Image>
<Image name="technique_id=T1031,technique_name=Modify Existing Service" condition="image">mmc.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">msbuild.exe</Image>
<Image name="technique_id=T1016,technique_name=System Network Configuration Discovery" condition="image">nbtstat.exe</Image>
<Image name="technique_id=T1069,technique_name=Permission Groups Discovery" condition="image">net1.exe</Image>
<Image name="technique_id=T1018,technique_name=Remote System Discovery" condition="image">nslookup.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">qprocess.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">qwinsta.exe</Image>
<Image name="technique_id=T1121,technique_name=Regsvcs/Regasm" condition="image">regsvcs.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">rwinsta.exe</Image>
<Image name="technique_id=T1053,technique_name=Scheduled Task" condition="image">schtasks.exe</Image>
<Image name="technique_id=T1089,technique_name=Disabling Security Tools" condition="image">taskkill.exe</Image>
<Image name="technique_id=T1057,technique_name=Process Discovery" condition="image">tasklist.exe</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">replace.exe</Image>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">1080</DestinationPort>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">3128</DestinationPort>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">8080</DestinationPort>
<DestinationPort name="technique_id=T1021,technique_name=Remote Services" condition="is">22</DestinationPort>
<DestinationPort name="technique_id=T1021,technique_name=Remote Services" condition="is">23</DestinationPort>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">25</DestinationPort>
<DestinationPort name="technique_id=T1021,technique_name=Remote Services" condition="is">3389</DestinationPort>
<DestinationPort name="technique_id=T1021,technique_name=Remote Services" condition="is">5800</DestinationPort>
<DestinationPort name="technique_id=T1021,technique_name=Remote Services" condition="is">5900</DestinationPort>
<Image name="technique_id=T1035,technique_name=Service Execution" condition="image">psexec.exe</Image>
<Image name="technique_id=T1035,technique_name=Service Execution" condition="image">psexesvc.exe</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\ProgramData</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Temp</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Temp</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\PerfLogs\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\$Recycle.bin\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Intel\Logs\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\Default\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\Public\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\NetworkService\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Fonts\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Debug\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Media\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Help\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\addins\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\repair\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\security\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\system32\config\systemprofile\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">\htdocs\</Image>
<Image name="technique_id=T1036,technique_name=Masquerading" condition="contains">\wwwroot\</Image>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">SyncAppvPublishingServer.exe</Image>
<Image condition="image">tor.exe</Image>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">1723</DestinationPort>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">4500</DestinationPort>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">9001</DestinationPort>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">9030</DestinationPort>
<DestinationPort name="technique_id=T1028,technique_name=Windows Remote Management" condition="is">5986</DestinationPort>
<DestinationPort name="technique_id=T1065,technique_name=UnCommonly Used Port" condition="is">449</DestinationPort>
<DestinationPort name="technique_id=T1065,technique_name=UnCommonly Used Port" condition="is">447</DestinationPort>
<DestinationPort name="technique_id=T1065,technique_name=UnCommonly Used Port" condition="is">8082</DestinationPort>
<Image name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="image">svchost.exe</Image>
<DestinationPort name="technique_id=T1043,technique_name=Commonly Used Port" condition="is">445</DestinationPort>
</NetworkConnect>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 5 == Process Terminated. -->
<ProcessTerminate onmatch="include">
<Image condition="begin with">C:\Users</Image>
<Image condition="begin with">C:\Temp</Image>
<Image condition="begin with">C:\Windows\Temp</Image>
</ProcessTerminate>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 6 == Driver Loaded. -->
<DriverLoad onmatch="include" />
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 7 == Image Loaded. -->
<ImageLoad onmatch="include">
<Rule groupRelation="and">
<ImageLoaded name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\System32\samlib.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\System32\WinSCard.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\System32\cryptdll.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\System32\hid.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\System32\vaultcli.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\System32\wlanapi.dll</ImageLoaded>
</Rule>
<ImageLoaded name="technique_id=1137,technique_name=Office Application Startup" condition="end with">.wll</ImageLoaded>
<ImageLoaded name="technique_id=T1137,technique_name=Office Application Startup" condition="end with">.xll</ImageLoaded>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded name="technique_id=1175,technique_name=Component Object Model and Distributed COM" condition="is">C:\Windows\SysWOW64\combase.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded name="technique_id=1175,technique_name=Component Object Model and Distributed COM" condition="is">C:\Windows\SysWOW64\coml2.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded name="technique_id=1175,technique_name=Component Object Model and Distributed COM" condition="is">C:\Windows\SysWOW64\comsvcs.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and" name="technique_id=1055,technique_name=Process Injection">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="begin with">C:\Windows\assembly\</ImageLoaded>
</Rule>
<Rule groupRelation="and" name="technique_id=1055,technique_name=Process Injection">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="begin with">C:\Windows\Microsoft.NET\assembly\GAC_MSIL</ImageLoaded>
</Rule>
<Rule groupRelation="and" name="technique_id=1055,technique_name=Process Injection">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="end with">clr.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and" name="technique_id=1059.005,technique_name=Command and Scripting Interpreter VBScript">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="end with">VBE7INTL.DLL</ImageLoaded>
</Rule>
<Rule groupRelation="and" name="technique_id=1059.005,technique_name=Command and Scripting Interpreter VBScript">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="end with">VBE7.DLL</ImageLoaded>
</Rule>
<Rule groupRelation="and" name="technique_id=1059.005,technique_name=Command and Scripting Interpreter VBScript">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="end with">VBEUI.DLL</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image name="technique_id=1047,technique_name=Windows Management Instrumentation" condition="contains all">C:\Program Files;\Microsoft Office\root\Office</Image>
<ImageLoaded condition="is">C:\Windows\SysWOW64\wbem\wbemdisp.dll</ImageLoaded>
</Rule>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">system.management.automation.ni.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">system.management.automation.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">Microsoft.PowerShell.Commands.Diagnostics.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">Microsoft.PowerShell.Commands.Management.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">Microsoft.PowerShell.Commands.Utility.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">Microsoft.PowerShell.ConsoleHost.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1086,technique_name=PowerShell" condition="end with">Microsoft.PowerShell.Security.dll</ImageLoaded>
<ImageLoaded name="technique_id=1053,technique_name=Scheduled Task" condition="end with">taskschd.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1117,technique_name=Regsvr32" condition="end with">scrobj.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1073,technique_name=DLL Side-Loading" condition="contains any">admin$;c$;\\;\appdata\;\temp\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">c:\programdata\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\Media\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\addins\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\system32\config\systemprofile\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\Debug\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\Temp</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\PerfLogs\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\Help\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Intel\Logs\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Temp</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\repair\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\security\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">C:\Windows\Fonts\</ImageLoaded>
<ImageLoaded condition="begin with" name="technique_id=T1073,technique_name=DLL Side-Loading">file:</ImageLoaded>
<ImageLoaded name="technique_id=T1073,technique_name=DLL Side-Loading" condition="contains">$Recycle.bin\</ImageLoaded>
<ImageLoaded name="technique_id=T1073,technique_name=DLL Side-Loading" condition="contains">\Windows\IME\</ImageLoaded>
<ImageLoaded name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="end with">wmiutils.dll</ImageLoaded>
<ImageLoaded name="technique_id=T1204,technique_name=User Execution" condition="end with">.exe</ImageLoaded>
</ImageLoad>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 8 == CreateRemoteThread. -->
<CreateRemoteThread onmatch="include">
<Rule groupRelation="and">
<SourceImage condition="is">c:\windows\system32\csrss.exe</SourceImage>
<StartFunction condition="is">CrtlRoutine</StartFunction>
</Rule>
<StartFunction name="technique_id=T1055,technique_name=Process Injection" condition="contains">LoadLibrary</StartFunction>
<TargetImage name="technique_id=T1055,technique_name=Process Injection" condition="is">C:\Windows\System32\rundll32.exe</TargetImage>
<TargetImage name="technique_id=T1055,technique_name=Process Injection" condition="is">C:\Windows\System32\svchost.exe</TargetImage>
<TargetImage name="technique_id=T1055,technique_name=Process Injection" condition="is">C:\Windows\System32\sysmon.exe</TargetImage>
<Rule groupRelation="and">
<StartAddress name="technique_id=T1003,technique_name=Credential Dumping" condition="is">0x001A0000</StartAddress>
<TargetImage condition="is">c:\windows\system32\lsass.exe</TargetImage>
</Rule>
<StartAddress name="technique_id=T1055,technique_name=Process Injection" condition="is">0x00590000</StartAddress>
</CreateRemoteThread>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 9 == RawAccessRead. -->
<RawAccessRead onmatch="include" />
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 10 == ProcessAccess. -->
<ProcessAccess onmatch="include">
<CallTrace name="technique_id=T1003,technique_name=Credential Dumping" condition="contains">dbghelp.dll</CallTrace>
<CallTrace name="technique_id=T1003,technique_name=Credential Dumping" condition="contains">dbgore.dll</CallTrace>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\csrss.exe</TargetImage>
<GrantedAccess>0x1F1FFF</GrantedAccess>
</Rule>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\wininit.exe</TargetImage>
<GrantedAccess>0x1F1FFF</GrantedAccess>
</Rule>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\winlogon.exe</TargetImage>
<GrantedAccess>0x1F1FFF</GrantedAccess>
</Rule>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\services.exe</TargetImage>
<GrantedAccess>0x1F1FFF</GrantedAccess>
</Rule>
<GrantedAccess name="technique_id=T1093,technique_name=Process Hollowing">0x21410</GrantedAccess>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\lsass.exe</TargetImage>
<GrantedAccess>0x1FFFFF</GrantedAccess>
</Rule>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\lsass.exe</TargetImage>
<GrantedAccess>0x1F1FFF</GrantedAccess>
</Rule>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\lsass.exe</TargetImage>
<GrantedAccess>0x1010</GrantedAccess>
</Rule>
<Rule groupRelation="and">
<TargetImage name="technique_id=T1003,technique_name=Credential Dumping" condition="is">C:\Windows\system32\lsass.exe</TargetImage>
<GrantedAccess>0x143A</GrantedAccess>
</Rule>
<Rule groupRelation="and" name="technique_id=1055,technique_name=Process Injection">
<SourceImage condition="contains all">C:\Program Files;\Microsoft Office\Root\Office</SourceImage>
<CallTrace condition="contains">\Microsoft Shared\VBA</CallTrace>
</Rule>
<GrantedAccess name="technique_id=T1093,technique_name=Process Hollowing">0x0800</GrantedAccess>
<GrantedAccess name="technique_id=T1003,technique_name=Credential Dumping">0x0810</GrantedAccess>
<GrantedAccess name="technique_id=T1055,technique_name=Process Injection">0x0820</GrantedAccess>
<GrantedAccess name="technique_id=T1093,technique_name=Process Hollowing">0x800</GrantedAccess>
<GrantedAccess name="technique_id=T1003,technique_name=Credential Dumping">0x810</GrantedAccess>
<GrantedAccess name="technique_id=T1055,technique_name=Process Injection">0x820</GrantedAccess>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\PerfLogs\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\$Recycle.bin\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Intel\Logs\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\Default\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\Public\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Users\NetworkService\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Fonts\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Debug\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Media\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\Help\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\addins\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\repair\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\security\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="begin with">C:\Windows\system32\config\systemprofile\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="contains">VolumeShadowCopy</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="contains">\htdocs\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="contains">\wwwroot\</SourceImage>
<SourceImage name="technique_id=T1036,technique_name=Masquerading" condition="contains">\Temp\</SourceImage>
<Rule groupRelation="and">
<CallTrace name="technique_id=T1086,technique_name=PowerShell" condition="contains">System.Management.Automation.ni.dll</CallTrace>
<SourceImage condition="is not">C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe</SourceImage>
</Rule>
</ProcessAccess>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 11 == FileCreate. -->
<FileCreate onmatch="include">
<TargetFilename name="technique_id=T1138,technique_name=Application Shimming" condition="contains">C:\Windows\AppPatch\Custom</TargetFilename>
<TargetFilename condition="end with">.bat</TargetFilename>
<TargetFilename condition="end with">.cmd</TargetFilename>
<TargetFilename name="technique_id=T1064,technique_name=Scripting" condition="end with">.chm</TargetFilename>
<TargetFilename condition="begin with">C:\Users\Default</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="contains">AppData\Local\Microsoft\CLR_v2.0\UsageLogs\</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\cscript.exe.log</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\wscript.exe.log</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\wmic.exe.log</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\mshta.exe.log</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\svchost.exe.log</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\regsvr32.exe.log</TargetFilename>
<TargetFilename name="technique_id=1218,technique_name=Office Signed Binary Proxy Execution" condition="end with">\UsageLogs\rundll32.exe.log</TargetFilename>
<TargetFilename condition="contains">\Downloads\</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Drivers</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\SysWOW64\Drivers</TargetFilename>
<TargetFilename condition="end with">.exe</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\GroupPolicy\Machine\Scripts</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\GroupPolicy\User\Scripts</TargetFilename>
<TargetFilename name="technique_id=T1170,technique_name=Mshta" condition="end with">.hta</TargetFilename>
<TargetFilename condition="end with">.iso</TargetFilename>
<TargetFilename condition="end with">.img</TargetFilename>
<TargetFilename condition="end with">.kirbi</TargetFilename>
<TargetFilename name="technique_id=T1187,technique_name=Forced Authentication" condition="end with">.lnk</TargetFilename>
<TargetFilename name="technique_id=T1187,technique_name=Forced Authentication" condition="end with">.scf</TargetFilename>
<TargetFilename condition="end with">.application</TargetFilename>
<TargetFilename condition="end with">.appref-ms</TargetFilename>
<TargetFilename name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="end with">.*proj</TargetFilename>
<TargetFilename name="technique_id=T1127,technique_name=Trusted Developer Utilities" condition="end with">.sln</TargetFilename>
<TargetFilename condition="end with">.settingcontent-ms</TargetFilename>
<TargetFilename condition="end with">.docm</TargetFilename>
<TargetFilename condition="end with">.pptm</TargetFilename>
<TargetFilename condition="end with">.xlsm</TargetFilename>
<TargetFilename condition="end with">.xlm</TargetFilename>
<TargetFilename condition="end with">.dotm</TargetFilename>
<TargetFilename condition="end with">.xltm</TargetFilename>
<TargetFilename condition="end with">.potm</TargetFilename>
<TargetFilename condition="end with">.ppsm</TargetFilename>
<TargetFilename condition="end with">.sldm</TargetFilename>
<TargetFilename condition="end with">.xlam</TargetFilename>
<TargetFilename condition="end with">.xla</TargetFilename>
<TargetFilename condition="end with">.iqy</TargetFilename>
<TargetFilename condition="end with">.slk</TargetFilename>
<TargetFilename condition="contains">\Content.Outlook\</TargetFilename>
<TargetFilename condition="end with">.rft</TargetFilename>
<TargetFilename condition="end with">.jsp</TargetFilename>
<TargetFilename condition="end with">.jspx</TargetFilename>
<TargetFilename condition="end with">.asp</TargetFilename>
<TargetFilename condition="end with">.aspx</TargetFilename>
<TargetFilename condition="end with">.php</TargetFilename>
<TargetFilename condition="end with">.war</TargetFilename>
<TargetFilename condition="end with">.ace</TargetFilename>
<TargetFilename name="technique_id=T1086,technique_name=PowerShell" condition="begin with">C:\Windows\System32\WindowsPowerShell</TargetFilename>
<TargetFilename name="technique_id=T1086,technique_name=PowerShell" condition="begin with">C:\Windows\SysWOW64\WindowsPowerShell</TargetFilename>
<TargetFilename name="technique_id=T1086,technique_name=PowerShell" condition="end with">.ps1</TargetFilename>
<TargetFilename name="technique_id=T1086,technique_name=PowerShell" condition="end with">.ps2</TargetFilename>
<TargetFilename condition="end with">.py</TargetFilename>
<TargetFilename condition="end with">.pyc</TargetFilename>
<TargetFilename condition="end with">.pyw</TargetFilename>
<Image condition="image">rundll32.exe</Image>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\Tasks\</TargetFilename>
<TargetFilename condition="contains">\Start Menu</TargetFilename>
<TargetFilename condition="contains">\Startup</TargetFilename>
<TargetFilename condition="end with">.sys</TargetFilename>
<TargetFilename condition="contains">\*lsass*.dmp\</TargetFilename>
<Image condition="image">taskmgr.exe</Image>
<TargetFilename condition="end with">.url</TargetFilename>
<TargetFilename condition="end with">.vb</TargetFilename>
<TargetFilename condition="end with">.vbe</TargetFilename>
<TargetFilename condition="end with">.vbs</TargetFilename>
<TargetFilename name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="begin with">C:\Windows\System32\Wbem</TargetFilename>
<TargetFilename name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="begin with">C:\Windows\SysWOW64\Wbem</TargetFilename>
<Image name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="begin with">C:\WINDOWS\system32\wbem\scrcons.exe</Image>
<TargetFilename name="technique_id=T1044,technique_name=File System Permissions Weakness" condition="begin with">C:\Windows\Temp\</TargetFilename>
<TargetFilename name="technique_id=T1047,technique_name=File System Permissions Weakness" condition="begin with">C:\Temp\</TargetFilename>
<TargetFilename name="technique_id=T1047,technique_name=File System Permissions Weakness" condition="begin with">C:\PerfLogs\</TargetFilename>
<TargetFilename name="technique_id=T1047,technique_name=File System Permissions Weakness" condition="begin with">C:\Users\Public\</TargetFilename>
<TargetFilename name="technique_id=T1047,technique_name=File System Permissions Weakness" condition="contains">\AppData\Temp\</TargetFilename>
</FileCreate>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 12,13,14 == RegObject added/deleted, RegValue Set, RegObject Renamed. -->
<RegistryEvent onmatch="include">
<TargetObject name="technique_id=T1015,technique_name=Accessibility Features" condition="is">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject name="technique_id=T1138,technique_name=Application Shimming" condition="contains">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\InstalledSDB</TargetObject>
<TargetObject name="technique_id=T1138,technique_name=Application Shimming" condition="contains">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Custom</TargetObject>
<TargetObject name="technique_id=T1131,technique_name=Authentication Package" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa</TargetObject>
<TargetObject name="technique_id=T1060,technique_name=Registry Run Keys / Start Folder" condition="contains">\CurrentVersion\Run</TargetObject>
<TargetObject condition="contains">\Group Policy\Scripts</TargetObject>
<TargetObject name="technique_id=T1037,technique_name=Logon Scripts" condition="contains">\Windows\System\Scripts</TargetObject>
<TargetObject name="technique_id=T1060,technique_name=Registry Run Keys / Start Folder" condition="contains">\Policies\Explorer\Run</TargetObject>
<TargetObject condition="end with">\ServiceDll</TargetObject>
<TargetObject condition="end with">\ImagePath</TargetObject>
<TargetObject condition="end with">\Start</TargetObject>
<TargetObject name="technique_id=T1004,technique_name=Winlogon Helper DLL" condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify</TargetObject>
<TargetObject name="technique_id=T1004,technique_name=Winlogon Helper DLL" condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit</TargetObject>
<TargetObject name="technique_id=T1004,technique_name=Winlogon Helper DLL" condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32</TargetObject>
<TargetObject name="technique_id=T1060,technique_name=Registry Run Keys / Start Folder" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\BootExecute</TargetObject>
<TargetObject name="technique_id=T1042,technique_name=Change Default File Association" condition="contains">\Explorer\FileExts</TargetObject>
<TargetObject condition="contains">\shell\install\command</TargetObject>
<TargetObject condition="contains">\shell\open\command</TargetObject>
<TargetObject condition="contains">\shell\open\ddeexec</TargetObject>
<TargetObject name="technique_id=T1060,technique_name=Registry Run Keys / Start Folder" condition="contains">Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders\Startup</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="contains">\mscfile\shell\open\command</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="contains">ms-settings\shell\open\command</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="contains">Classes\exefile\shell\runas\command\isolatedCommand</TargetObject>
<TargetObject name="technique_id=T1122,technique_name=Component Object Model Hijacking" condition="contains">Software\Classes\CLSID</TargetObject>
<TargetObject name="technique_id=T1098,technique_name=Account Manipulation" condition="contains">\services\Netlogon\Parameters\DisablePasswordChange</TargetObject>
<TargetObject name="technique_id=T1103,technique_name=Appinit DLLs" condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\Appinit_Dlls</TargetObject>
<TargetObject name="technique_id=T1103,technique_name=Appinit DLLs" condition="begin with">HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Windows\Appinit_Dlls</TargetObject>
<TargetObject name="technique_id=T1103,technique_name=Appinit DLLs" condition="is">REGISTRY\MACHINE\SYSTEM\ControlSet001\Services\DNS\Parameters\ServerLevelPluginDll</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions</TargetObject>
<TargetObject name="technique_id=T1183,technique_name=Image File Execution Options Injection" condition="begin with">HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject name="technique_id=T1183,technique_name=Image File Execution Options Injection" condition="begin with">HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject condition="contains">\Internet Explorer\Toolbar</TargetObject>
<TargetObject condition="contains">\Internet Explorer\Extensions</TargetObject>
<TargetObject condition="contains">\Browser Helper Objects</TargetObject>
<TargetObject name="technique_id=T1013,technique_name=Forced Authentication" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Print\Monitors</TargetObject>
<TargetObject name="technique_id=T1128,technique_name=Netsh Helper DLL" condition="contains">SOFTWARE\Microsoft\Netsh</TargetObject>
<TargetObject condition="end with">\UrlUpdateInfo</TargetObject>
<TargetObject condition="contains">\Security\Trusted Documents\TrustRecords</TargetObject>
<TargetObject condition="contains">\Microsoft\Office\Outlook\Addins</TargetObject>
<TargetObject condition="contains">\Software\Microsoft\VSTO\Security\Inclusion</TargetObject>
<TargetObject condition="contains">\Software\Microsoft\VSTO\SolutionMetadata</TargetObject>
<TargetObject name="technique_id=T1076,technique_name=Remote Desktop Protocol" condition="is">HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services</TargetObject>
<TargetObject name="technique_id=T1101,technique_name=Security Support Provider" condition="contains">SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LSASS.exe</TargetObject>
<TargetObject name="technique_id=T1198,technique_name=SIP and Trust Provider Hijacking" condition="begin with">HKLM\SOFTWARE\Microsoft\Cryptography\OID</TargetObject>
<TargetObject name="technique_id=T1198,technique_name=SIP and Trust Provider Hijacking" condition="begin with">HKLM\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID</TargetObject>
<TargetObject name="technique_id=T1198,technique_name=SIP and Trust Provider Hijacking" condition="begin with">HKLM\SOFTWARE\Microsoft\Cryptography\Providers\Trust</TargetObject>
<TargetObject name="technique_id=T1198,technique_name=SIP and Trust Provider Hijacking" condition="begin with">HKLM\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust</TargetObject>
<TargetObject name="technique_id=T1035,technique_name=Service Execution" condition="end with">\PsExec\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1105,technique_name=Remote File Copy" condition="end with">\PsFile\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="end with">\PsGetSID\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1057,technique_name=Process Discovery" condition="end with">\PsInfo\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="end with">\PsKill\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1057,technique_name=Process Discovery" condition="end with">\PsList\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="end with">\PsLoggedOn\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1035,technique_name=Service Execution" condition="end with">\PsLogList\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1098,technique_name=Account Manipulation" condition="end with">\PsPasswd\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1035,technique_name=Service Execution" condition="end with">\PsService\EulaAccepted</TargetObject>
<TargetObject name="undefined" condition="end with">\PsShutDown\EulaAccepted</TargetObject>
<TargetObject name="undefined" condition="end with">\PsSuspend\EulaAccepted</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="contains">SYSTEM\CurrentControlSet\services\SysmonDrv</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="contains">SYSTEM\CurrentControlSet\services\Sysmon</TargetObject>
<TargetObject name="technique_id=T1060,technique_name=Registry Run Keys / Start Folder" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\InitialProgram</TargetObject>
<TargetObject name="technique_id=T1209,technique_name=Time Providers" condition="contains">HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\W32Time\TimeProviders</TargetObject>
<TargetObject name="technique_id=T1218,technique_name=Signed Binary Proxy Execution" condition="begin with">HKLM\Software\Microsoft\WAB\DLLPath</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths</TargetObject>
<TargetObject name="technique_id=T1182,technique_name=AppCert DLLs" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\AppCertDlls</TargetObject>
<TargetObject name="technique_id=T1122,technique_name=Component Object Model Hijacking" condition="end with">\InprocServer32\(Default)</TargetObject>
<TargetObject name="technique_id=T1122,technique_name=Component Object Model Hijacking" condition="contains all">Classes\CLSID\;TreatAs</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Provider</TargetObject>
<TargetObject condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa</TargetObject>
<TargetObject name="technique_id=T1003,technique_name=Credential Dumping" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SecurityProviders</TargetObject>
<TargetObject name="technique_id=T1003,technique_name=Credential Dumping" condition="contains">\Control\SecurityProviders\WDigest</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiVirus</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableBehaviorMonitoring</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableOnAccessProtection</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableScanOnRealtimeEnable</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Spynet\SpyNetReporting</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Policies\Microsoft\Windows Defender</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\FirewallOverride</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT</TargetObject>
<TargetObject condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Safeboot</TargetObject>
<TargetObject condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\Winlogon</TargetObject>
<TargetObject condition="end with">\FriendlyName</TargetObject>
<TargetObject condition="is">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\InProgress\(Default)</TargetObject>
<Rule groupRelation="and">
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System</TargetObject>
<Image condition="is not">C:\Windows\System32\svchost.exe</Image>
</Rule>
<TargetObject condition="begin with">HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles</TargetObject>
<TargetObject name="technique_id=T1130,technique_name=Install Root Certificate" condition="begin with">HKLM\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates</TargetObject>
<TargetObject name="technique_id=T1130,technique_name=Install Root Certificate" condition="contains">\Microsoft\SystemCertificates\Root\Certificates</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\AllAlertsDisabled</TargetObject>
<TargetObject name="technique_id=T1089,technique_name=Disabling Security Tools" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\DisableMonitoring</TargetObject>
<TargetObject condition="contains">\Classes\AllFilesystemObjects</TargetObject>
<TargetObject condition="contains">\Classes\Directory</TargetObject>
<TargetObject condition="contains">\Classes\Drive</TargetObject>
<TargetObject condition="contains">\Classes\Folder</TargetObject>
<TargetObject condition="contains">\ContextMenuHandlers</TargetObject>
<TargetObject condition="contains">\CurrentVersion\Shell</TargetObject>
<TargetObject condition="begin with">HKLM\Software\Microsoft\Windows\CurrentVersion\explorer\ShellExecuteHooks</TargetObject>
<TargetObject condition="begin with">HKLM\Software\Microsoft\Windows\CurrentVersion\explorer\ShellServiceObjectDelayLoad</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="begin with">HKCU\Software\Classes\AppX82a6gwre4fdg3bt635tn5ctqjf8msdd2\Shell\open\command</TargetObject>
<TargetObject condition="contains">{AB8902B4-09CA-4bb6-B78D-A8F59079A8D5}</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="begin with">HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="begin with">HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\LocalAccountTokenFilterPolicy</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\UacDisableNotify</TargetObject>
<TargetObject name="technique_id=T1088,technique_name=Bypass User Account Control" condition="begin with">HKLM\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify</TargetObject>
<TargetObject condition="is">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Setup\ServiceStartup</TargetObject>
<TargetObject condition="begin with">HKLM\SYSTEM\CurrentControlSet\Services\WinSock</TargetObject>
<TargetObject condition="end with">\ProxyServer</TargetObject>
<TargetObject name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="contains">SYSTEM\CurrentControlSet\Control\CrashControl</TargetObject>
</RegistryEvent>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 15 == FileStream Created. -->
<FileCreateStreamHash onmatch="include">
<TargetFilename condition="contains">Temp\7z</TargetFilename>
<TargetFilename condition="end with">.bat</TargetFilename>
<TargetFilename condition="end with">.cmd</TargetFilename>
<TargetFilename condition="end with">Temp\debug.bin</TargetFilename>
<TargetFilename condition="contains">Downloads</TargetFilename>
<TargetFilename condition="end with">.exe</TargetFilename>
<TargetFilename condition="end with">.hta</TargetFilename>
<TargetFilename condition="end with">.lnk</TargetFilename>
<TargetFilename condition="contains">Content.Outlook</TargetFilename>
<TargetFilename name="technique_id=T1086,technique_name=PowerShell" condition="end with">.ps1</TargetFilename>
<TargetFilename name="technique_id=T1086,technique_name=PowerShell" condition="end with">.ps2</TargetFilename>
<TargetFilename condition="end with">.reg</TargetFilename>
<TargetFilename condition="end with">.vb</TargetFilename>
<TargetFilename condition="end with">.vbe</TargetFilename>
<TargetFilename condition="end with">.vbs</TargetFilename>
</FileCreateStreamHash>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 17,18 == PipeEvent. Log Named pipe created & Named pipe connected -->
<PipeEvent onmatch="exclude">
<Image condition="is">"C:\Program Files\Microsoft Monitoring Agent\Agent\MonitoringHost.exe"</Image>
<Image condition="is">Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe</Image>
<Image condition="is">Program Files (x86)\Citrix\ICA Client\Receiver\Receiver.exe</Image>
<Image condition="is">Program Files (x86)\Citrix\ICA Client\wfcrun32.exe</Image>
<Image condition="is">Program Files (x86)\Citrix\ICA Client\concentr.exe</Image>
<PipeName condition="begin with">\Vivisimo Velocity</PipeName>
<PipeName condition="is">\SQLLocal\MSSQLSERVER</PipeName>
<PipeName condition="is">\SQLLocal\INSTANCE01</PipeName>
<PipeName condition="is">\SQLLocal\SQLEXPRESS</PipeName>
<PipeName condition="is">\SQLLocal\COMMVAULT</PipeName>
<PipeName condition="is">\SQLLocal\RTCLOCAL</PipeName>
<PipeName condition="is">\SQLLocal\RTC</PipeName>
<PipeName condition="is">\SQLLocal\TMSM</PipeName>
<Image condition="is">Program Files (x86)\Microsoft SQL Server\110\DTS\binn\dtexec.exe</Image>
<Image condition="end with">PostgreSQL\9.6\bin\postgres.exe</Image>
<PipeName condition="contains">\pgsignal_</PipeName>
<Image condition="is">Program Files\Qlik\Sense\Engine\Engine.exe</Image>
<Image condition="end with">Program Files\SplunkUniversalForwarder\bin\splunkd.exe</Image>
<Image condition="end with">Program Files\SplunkUniversalForwarder\bin\splunk.exe</Image>
<Image condition="end with">Program Files\SplunkUniversalForwarder\bin\splunk-MonitorNoHandle.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\CMAgent\OfcCMAgent.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\ofcservice.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\Web\Service\DbServer.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\verconn.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\WEB_OSCE\WEB\CGI\cgiOnClose.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\WEB_OSCE\WEB\CGI\cgiRqHotFix.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\LWCS\LWCSService.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\WSS\iCRCService.exe</Image>
<Image condition="end with">Program Files\Trend\SPROTECT\x64\tsc.exe</Image>
<Image condition="end with">Program Files\Trend\SPROTECT\x64\tsc64.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\osceintegrationservice.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\OfcLogReceiverSvc.exe</Image>
<PipeName condition="is">\Trend Micro OSCE Command Handler Manager</PipeName>
<PipeName condition="is">\Trend Micro OSCE Command Handler2 Manager</PipeName>
<PipeName condition="is">\Trend Micro Endpoint Encryption ToolBox Command Handler Manager</PipeName>
<PipeName condition="is">\OfcServerNamePipe</PipeName>
<PipeName condition="is">\ntapvsrq</PipeName>
<PipeName condition="is">\srvsvc</PipeName>
<PipeName condition="is">\wkssvc</PipeName>
<PipeName condition="is">\lsass</PipeName>
<PipeName condition="is">\winreg</PipeName>
<PipeName condition="is">\spoolss</PipeName>
<PipeName condition="contains">Anonymous Pipe</PipeName>
<Image condition="is">c:\windows\system32\inetsrv\w3wp.exe</Image>
</PipeEvent>
</RuleGroup>
<RuleGroup name="" groupRelation="or">
<!-- Event ID 19,20,21, == WmiEvent. Log all WmiEventFilter, WmiEventConsumer, WmiEventConsumerToFilter activity-->
<WmiEvent onmatch="include">
<Operation name="technique_id=T1047,technique_name=Windows Management Instrumentation" condition="is">Created</Operation>
</WmiEvent>
</RuleGroup>
<RuleGroup groupRelation="or">
<ProcessCreate onmatch="exclude">
<Rule groupRelation="and">
<Image condition="end with">AcroRd32.exe</Image>
<CommandLine condition="contains any">/CR;channel=</CommandLine>
</Rule>
<Rule groupRelation="or">
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\AcroCEF\AcroCEF.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\LogTransport2.exe</Image>
</Rule>
<Image condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\ACC\Creative Cloud.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\ACC\Creative Cloud.exe</ParentImage>
<ParentImage condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\CCXProcess\CCXProcess.exe</ParentImage>
<ParentImage condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\CoreSync\CoreSync.exe</ParentImage>
<Image condition="end with">C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\armsvc.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\AdobeCollabSync.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\Adobe Desktop Common\HEX\Adobe CEF Helper.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AdobeGCClient.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\P6\adobe_licutil.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\P7\adobe_licutil.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\P7\adobe_licutil.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\UWA\updaterstartuputility.exe</Image>
<ParentImage condition="is">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\UWA\updaterstartuputility.exe</ParentImage>
<ParentCommandLine condition="is">"C:\Program Files\Microsoft Monitoring Agent\Agent\MonitoringHost.exe" -Embedding</ParentCommandLine>
<CommandLine condition="is">C:\Windows\system32\cscript.exe" /nologo "MonitorKnowledgeDiscovery.vbs</CommandLine>
<ParentImage condition="end with">C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnagent.exe</ParentImage>
<CommandLine condition="begin with">C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe</CommandLine>
<Image condition="is">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe</Image>
<Image condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe</Image>
<Image condition="is">C:\Windows\Microsoft.Net\Framework64\v3.0\WPF\PresentationFontCache.exe</Image>
<Image condition="is">C:\Windows\Microsoft.Net\Framework64\v3.0\WPF\PresentationFontCache.exe</Image>
<ParentCommandLine condition="contains">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngentask.exe</ParentCommandLine>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngentask.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngentask.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngentask.exe</ParentImage>
<Image condition="begin with">C:\Program Files\NVIDIA Corporation\</Image>
<Image condition="begin with">C:\Program Files\Realtek\</Image>
<ParentImage condition="end with">C:\Program Files\Realtek\Audio\HDA\RtkAudioService64.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Dropbox\Update\DropboxUpdate.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Dropbox\Update\DropboxUpdate.exe</ParentImage>
<Image condition="is">C:\Program Files\ESET\ESET Nod32 Antivirus\ekrn.exe</Image>
<CommandLine condition="begin with">"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=</CommandLine>
<CommandLine condition="begin with">"C:\Program Files\Google\Chrome\Application\chrome.exe" --type=</CommandLine>
<Image condition="begin with">C:\Program Files (x86)\Google\Update\</Image>
<ParentImage condition="begin with">C:\Program Files (x86)\Google\Update\</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\pfwsmgr.exe</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\respesvc64.exe</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\pfwsmgr.exe</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\ResPesvc64.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\RES Software\Workspace Manager\respesvc.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\Ivanti\Workspace Control\ResPesvc.exe</ParentImage>
<Image condition="is">C:\Program Files\Malwarebytes\Anti-Malware\mbam.exe</Image>
<Image condition="is">C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe</Image>
<Image condition="is">C:\Program Files\Malwarebytes\Anti-Malware\mbamtray.exe</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe</Image>
<ParentImage condition="end with">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe</ParentImage>
<Image condition="is">C:\Program Files (x86)\Microsoft Office\Office16\MSOSYNC.EXE</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE</Image>
<CommandLine condition="begin with">"C:\Program Files\Mozilla Firefox\plugin-container.exe" --channel</CommandLine>
<CommandLine condition="begin with">"C:\Program Files (x86)\Mozilla Firefox\plugin-container.exe" --channel</CommandLine>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Intelligence\swi_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Control\swc_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos System Protection\ssp.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Remote Management System\RouterNT.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\AutoUpdate\ALsvc.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\SAVAdminService.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Remote Management System\ManagementAgentNT.exe</Image>
<Image condition="begin with">C:\Program Files\SplunkUniversalForwarder\bin\</Image>
<ParentImage condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunk.exe</ParentImage>
<Image condition="begin with">D:\Program Files\SplunkUniversalForwarder\bin\</Image>
<ParentImage condition="is">D:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">D:\Program Files\SplunkUniversalForwarder\bin\splunk.exe</ParentImage>
<Image condition="begin with">C:\Program Files\Splunk\bin\</Image>
<ParentImage condition="is">C:\Program Files\Splunk\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\Splunk\bin\splunk.exe</ParentImage>
<Image condition="begin with">D:\Program Files\Splunk\bin\</Image>
<ParentImage condition="is">D:\Program Files\Splunk\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">D:\Program Files\Splunk\bin\splunk.exe</ParentImage>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k appmodel -s StateRepository</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k appmodel</CommandLine>
<CommandLine condition="is">C:\WINDOWS\system32\svchost.exe -k appmodel -p -s tiledatamodelsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k camera -s FrameServer</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k dcomlaunch -s LSM</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k dcomlaunch -s PlugPlay</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k defragsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k devicesflow -s DevicesFlowUserSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k imgsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s EventSystem</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s bthserv</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s nsi</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s w32Time</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceAndNoImpersonation</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s Dhcp</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s EventLog</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s TimeBrokerSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s WFDSConMgrSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceAndNoImpersonation -s SensrSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNoNetwork</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -p -s WPDBusEnum</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -p -s fhsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s DeviceAssociationService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s NcbService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s SensorService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s TabletInputService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s UmRdpService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s WPDBusEnum</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s WdiSystemHost</CommandLine>
<CommandLine condition="is">C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted</CommandLine>
<CommandLine condition="is">C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wlidsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -p -s ncaSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s BDESVC</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s BITS</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s CertPropSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s DsmSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s Gpsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s ProfSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s SENS</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s SessionEnv</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s Themes</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s Winmgmt</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -p -s DoSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s Dnscache</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s LanmanWorkstation</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s NlaSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s TermService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkServiceNetworkRestricted</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k rPCSS</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k secsvcs</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k swprv</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k unistackSvcGroup</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k utcsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k wbioSvcGroup</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k werSvcGroup</CommandLine>
<CommandLine condition="is">C:\WINDOWS\System32\svchost.exe -k wsappx -p -s ClipSVC</CommandLine>
<CommandLine condition="is">C:\WINDOWS\system32\svchost.exe -k wsappx -p -s AppXSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k wsappx -s ClipSVC</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k wsappx</CommandLine>
<ParentCommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs</ParentCommandLine>
<ParentCommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted</ParentCommandLine>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\ds_monitor.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\dsa.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\dsuam.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\Notifier.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\lib\Patch.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\BM\TMBMSRV.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\OfficeScan Client\TmopExtIns32.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\OfficeScan Client\TmExtIns.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\OfficeScan Client\TmListen.exe</Image>
<Image condition="begin with">C:\Program Files\Windows Defender\</Image>
<Image condition="is">C:\Windows\system32\MpSigStub.exe</Image>
<Image condition="begin with">C:\Windows\SoftwareDistribution\Download\Install\AM_</Image>
<Image condition="is">C:\Program Files\Microsoft Security Client\MpCmdRun.exe</Image>
<CommandLine condition="begin with">C:\Windows\system32\DllHost.exe /Processid</CommandLine>
<CommandLine condition="is">C:\Windows\system32\SearchIndexer.exe /Embedding</CommandLine>
<Image condition="end with">C:\Windows\System32\CompatTelRunner.exe</Image>
<Image condition="is">C:\Windows\System32\MusNotification.exe</Image>
<Image condition="is">C:\Windows\System32\MusNotificationUx.exe</Image>
<Image condition="is">C:\Windows\System32\audiodg.exe</Image>
<Image condition="is">C:\Windows\System32\conhost.exe</Image>
<Image condition="is">C:\Windows\System32\powercfg.exe</Image>
<Image condition="is">C:\Windows\System32\wbem\WmiApSrv.exe</Image>
<Image condition="is">C:\Windows\System32\wermgr.exe</Image>
<Image condition="is">C:\Windows\SysWOW64\wermgr.exe</Image>
<Image condition="is">C:\Windows\system32\sppsvc.exe</Image>
<IntegrityLevel condition="is">AppContainer</IntegrityLevel>
<ParentCommandLine condition="begin with">%%SystemRoot%%\system32\csrss.exe ObjectDirectory=\Windows</ParentCommandLine>
<ParentImage condition="is">C:\Windows\system32\SearchIndexer.exe</ParentImage>
</ProcessCreate>
</RuleGroup>
<RuleGroup groupRelation="or">
<FileCreateTime onmatch="exclude">
<Image condition="end with">AppData\Local\Google\Chrome\Application\chrome.exe</Image>
<Image condition="end with">Root\VFS\ProgramFilesX86\Google\Chrome\Application\chrome.exe</Image>
<Image condition="image">OneDrive.exe</Image>
<Image condition="contains">setup</Image>
</FileCreateTime>
</RuleGroup>
<RuleGroup groupRelation="or">
<NetworkConnect onmatch="exclude">
<Image condition="end with">AppData\Roaming\Dropbox\bin\Dropbox.exe</Image>
<Image condition="is">C:\Program Files\ESET\ESET Nod32 Antivirus\ekrn.exe</Image>
<Image condition="image">OneDrive.exe</Image>
<Image condition="image">OneDriveStandaloneUpdater.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Intelligence\swi_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\AutoUpdate\ALsvc.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Remote Management System\RouterNT.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Control\swc_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Intelligence\swi_service.exe</Image>
<Image condition="is">C:\Program Files\Sophos\Sophos Network Threat Protection\bin\SntpService.exe</Image>
<Image condition="image">Spotify.exe</Image>
<Image condition="is">C:\Program files (x86)\Trend Micro\OfficeScan Client\tmlisten.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\BM\TMBMSRV.exe</Image>
<DestinationHostname condition="end with">microsoft.com</DestinationHostname>
<DestinationHostname condition="end with">microsoft.com.akadns.net</DestinationHostname>
<DestinationHostname condition="end with">microsoft.com.nsatc.net</DestinationHostname>
</NetworkConnect>
</RuleGroup>
<RuleGroup groupRelation="or">
<DriverLoad onmatch="exclude">
<Signature condition="begin with">Intel </Signature>
<Signature condition="contains">microsoft</Signature>
<Signature condition="contains">windows</Signature>
</DriverLoad>
</RuleGroup>
<RuleGroup groupRelation="or">
<CreateRemoteThread onmatch="exclude">
<SourceImage condition="is">C:\Windows\System32\svchost.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\wininit.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\csrss.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\services.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\winlogon.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\audiodg.exe</SourceImage>
<StartModule condition="is">C:\windows\system32\kernel32.dll</StartModule>
<TargetImage condition="end with">Google\Chrome\Application\chrome.exe</TargetImage>
<SourceImage condition="is">C:\Windows\System32\wbem\WmiPrvSE.exe</SourceImage>
</CreateRemoteThread>
</RuleGroup>
<RuleGroup groupRelation="or">
<ProcessAccess onmatch="exclude">
<SourceImage condition="is">C:\Windows\CarbonBlack\cb.exe</SourceImage>
<SourceImage condition="contains all">C:\Program Files\Cisco\AMP\;sfc.exe</SourceImage>
<SourceImage condition="is">c:\Program Files\Couchbase\Server\bin\sigar_port.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\cpushld.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\cpushld.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Ivanti\Workspace Control\cpushld.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\RES Software\Workspace Manager\cpushld.exe</SourceImage>
<SourceImage condition="end with">wmiprvse.exe</SourceImage>
<SourceImage condition="end with">GoogleUpdate.exe</SourceImage>
<SourceImage condition="end with">LTSVC.exe</SourceImage>
<SourceImage condition="end with">taskmgr.exe</SourceImage>
<SourceImage condition="end with">VBoxService.exe</SourceImage>
<SourceImage condition="end with">vmtoolsd.exe</SourceImage>
<SourceImage condition="end with">\Citrix\System32\wfshell.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\lsm.exe</SourceImage>
<SourceImage condition="end with">Microsoft.Identity.AadConnect.Health.AadSync.Host.exe</SourceImage>
<SourceImage condition="begin with">C:\Program Files (x86)\Symantec\Symantec Endpoint Protection</SourceImage>
<GrantedAccess>0x1000</GrantedAccess>
<GrantedAccess>0x1400</GrantedAccess>
<GrantedAccess>0x101400</GrantedAccess>
<GrantedAccess>0x101000</GrantedAccess>
<SourceImage condition="is">C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\McAfee\Agent\x86\macompatsvc.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Microsoft Security Client\MsMpEng.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Windows Defender\MsMpEng.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Mobatek\MobaXterm\MobaXterm.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Razer Chroma SDK\bin\RzSDKService.exe</SourceImage>
<SourceImage condition="is">C:\WINDOWS\CCM\CcmExec.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Splunk\bin\splunkd.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\VMware\VMWare Player\vmware-authd.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\VMware\VMware Workstation\vmware-authd.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\WinZip\FAHWindow64.exe</SourceImage>
</ProcessAccess>
</RuleGroup>
<RuleGroup groupRelation="or">
<FileCreate onmatch="exclude">
<Image condition="is">C:\Program Files (x86)\Dell\CommandUpdate\InvColPC.exe</Image>
<Image condition="is">C:\Windows\system32\igfxCUIService.exe</Image>
<Image condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe</Image>
<Image condition="is">C:\Windows\System32\smss.exe</Image>
<Image condition="is">C:\Windows\system32\CompatTelRunner.exe</Image>
<Image condition="is">C:\Windows\system32\wbem\WMIADAP.EXE</Image>
<TargetFilename condition="begin with">C:\Windows\System32\DriverStore\Temp\</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\wbem\Performance\</TargetFilename>
<TargetFilename condition="end with">WRITABLE.TST</TargetFilename>
<TargetFilename condition="contains">\AppData\Roaming\Microsoft\Windows\Recent\</TargetFilename>
<TargetFilename condition="begin with">C:\$WINDOWS.~BT\Sources\SafeOS\SafeOS.Mount\</TargetFilename>
<Image condition="begin with">C:\WINDOWS\winsxs\amd64_microsoft-windows</Image>
<Image condition="is">c:\Program Files\Microsoft Security Client\MsMpEng.exe</Image>
<Image condition="is">c:\windows\system32\provtool.exe</Image>
<Image condition="is">C:\WINDOWS\CCM\CcmExec.exe</Image>
<TargetFilename condition="begin with">C:\Windows\CCM</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\PLA\FabricTraces</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Server\ServerRoleUsageCollector</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Server\ServerCeipAssistant</TargetFilename>
<Image condition="is">C:\WINDOWS\system32\svchost.exe</Image>
</FileCreate>
</RuleGroup>
<RuleGroup groupRelation="or">
<RegistryEvent onmatch="exclude">
<Image condition="is">C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\aciseposture.exe</Image>
<Image condition="is">C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnagent.exe</Image>
<TargetObject condition="end with">Toolbar\WebBrowser</TargetObject>
<TargetObject condition="end with">Toolbar\WebBrowser\ITBar7Height</TargetObject>
<TargetObject condition="end with">Toolbar\ShellBrowser\ITBar7Layout</TargetObject>
<TargetObject condition="end with">Internet Explorer\Toolbar\Locked</TargetObject>
<TargetObject condition="end with">ShellBrowser</TargetObject>
<Image condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files\RES Software\Workspace Manager\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Encryption Agent\MfeEpeHost.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\mfeatp.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe</Image>
<Image condition="is">C:\Program Files\Common Files\McAfee\Engine\AMCoreUpdater\amupdate.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\masvc.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\x86\mfemactl.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\x86\McScript_InUse.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\x86\macompatsvc.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Security\Threat Prevention\mfeensppl.exe</Image>
<Image condition="begin with">C:\Program Files\Common Files\McAfee\Engine\scanners</Image>
<Image condition="is">C:\Program Files\Common Files\McAfee\AVSolution\mcshield.exe</Image>
<Image condition="is">C:\Program Files (x86)\Webroot\WRSA.exe</Image>
<Image condition="is">C:\Program Files\WIDCOMM\Bluetooth Software\btwdins.exe</Image>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Audit</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Audit\AuditPolicy</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Audit\PerUserAuditing\System</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\SspiCache</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Domains</TargetObject>
<TargetObject condition="end with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Audit</TargetObject>
<TargetObject condition="contains">\OpenWithProgids</TargetObject>
<TargetObject condition="end with">\OpenWithList</TargetObject>
<TargetObject condition="end with">\UserChoice</TargetObject>
<TargetObject condition="end with">\UserChoice\ProgId</TargetObject>
<TargetObject condition="end with">\UserChoice\Hash</TargetObject>
<TargetObject condition="end with">\OpenWithList\MRUList</TargetObject>
<TargetObject condition="end with">} 0xFFFF</TargetObject>
<Image condition="end with">Office\root\integration\integrator.exe</Image>
<Image condition="image">C:\WINDOWS\system32\backgroundTaskHost.exe</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe</Image>
<Image condition="is">C:\Program Files\Windows Defender\MsMpEng.exe</Image>
<Image condition="is">C:\Windows\SystemApps\Microsoft.Windows.Cortana_cw5n1h2txyewy\SearchUI.exe</Image>
<Image condition="is">C:\Program Files\Microsoft Application Virtualization\Client\AppVClient.exe</Image>
<TargetObject condition="end with">\CurrentVersion\Run</TargetObject>
<TargetObject condition="end with">\CurrentVersion\RunOnce</TargetObject>
<TargetObject condition="end with">\CurrentVersion\App Paths</TargetObject>
<TargetObject condition="end with">\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject condition="end with">\CurrentVersion\Shell Extensions\Cached</TargetObject>
<TargetObject condition="end with">\CurrentVersion\Shell Extensions\Approved</TargetObject>
<TargetObject condition="end with">}\PreviousPolicyAreas</TargetObject>
<TargetObject condition="contains">\Control\WMI\Autologger\</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Services\UsoSvc\Start</TargetObject>
<TargetObject condition="end with">\Lsa\OfflineJoin\CurrentValue</TargetObject>
<TargetObject condition="end with">\Components\TrustedInstaller\Events</TargetObject>
<TargetObject condition="end with">\Components\TrustedInstaller</TargetObject>
<TargetObject condition="end with">\Components\Wlansvc</TargetObject>
<TargetObject condition="end with">\Components\Wlansvc\Events</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\</TargetObject>
<TargetObject condition="end with">\Directory\shellex</TargetObject>
<TargetObject condition="end with">\Directory\shellex\DragDropHandlers</TargetObject>
<TargetObject condition="end with">\Drive\shellex</TargetObject>
<TargetObject condition="end with">\Drive\shellex\DragDropHandlers</TargetObject>
<TargetObject condition="contains">_Classes\AppX</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Publishers\</TargetObject>
<TargetObject condition="is">HKLM\SOFTWARE\Policies\Microsoft\SystemCertificates\Root\Certificates</TargetObject>
<Image condition="is">C:\Windows\SystemApps\Microsoft.Windows.Cortana_cw5n1h2txyewy\SearchUI.exe</Image>
<Image condition="begin with">C:\$WINDOWS.~BT\</Image>
<TargetObject condition="end with">\services\clr_optimization_v2.0.50727_32\Start</TargetObject>
<TargetObject condition="end with">\services\clr_optimization_v2.0.50727_64\Start</TargetObject>
<TargetObject condition="end with">\services\clr_optimization_v4.0.30319_32\Start</TargetObject>
<TargetObject condition="end with">\services\clr_optimization_v4.0.30319_64\Start</TargetObject>
<TargetObject condition="end with">\services\DeviceAssociationService\Start</TargetObject>
<TargetObject condition="end with">\services\BITS\Start</TargetObject>
<TargetObject condition="end with">\services\TrustedInstaller\Start</TargetObject>
<TargetObject condition="end with">\services\tunnel\Start</TargetObject>
<TargetObject condition="end with">\services\UsoSvc\Start</TargetObject>
</RegistryEvent>
</RuleGroup>
<RuleGroup groupRelation="or">
<PipeEvent onmatch="include">
<PipeName name="technique_id=T1077,technique_name=Windows Admin Shares" condition="begin with">\atsvc</PipeName>
<PipeName name="technique_id=T1077,technique_name=Windows Admin Shares" condition="begin with">\msagent_</PipeName>
<PipeName name="technique_id=T1077,technique_name=Windows Admin Shares" condition="begin with">\msf-pipe</PipeName>
<PipeName name="technique_id=T1077,technique_name=Windows Admin Shares" condition="begin with">\PSEXESVC</PipeName>
<PipeName name="technique_id=T1049,technique_name=System Network Connections Discovery" condition="begin with">\srvsvc</PipeName>
<PipeName name="technique_id=T1033,technique_name=System Owner/User Discovery" condition="begin with">\winreg</PipeName>
</PipeEvent>
</RuleGroup>
<RuleGroup groupRelation="or">
<DnsQuery onmatch="exclude">
<QueryName condition="end with">.1rx.io</QueryName>
<QueryName condition="end with">.2mdn.net</QueryName>
<QueryName condition="end with">.adadvisor.net</QueryName>
<QueryName condition="end with">.adap.tv</QueryName>
<QueryName condition="end with">.addthis.com</QueryName>
<QueryName condition="end with">.adform.net</QueryName>
<QueryName condition="end with">.adnxs.com</QueryName>
<QueryName condition="end with">.adroll.com</QueryName>
<QueryName condition="end with">.adrta.com</QueryName>
<QueryName condition="end with">.adsafeprotected.com</QueryName>
<QueryName condition="end with">.adsrvr.org</QueryName>
<QueryName condition="end with">.advertising.com</QueryName>
<QueryName condition="end with">.amazon-adsystem.com</QueryName>
<QueryName condition="end with">.amazon-adsystem.com</QueryName>
<QueryName condition="end with">.analytics.yahoo.com</QueryName>
<QueryName condition="end with">.aol.com</QueryName>
<QueryName condition="end with">.betrad.com</QueryName>
<QueryName condition="end with">.bidswitch.net</QueryName>
<QueryName condition="end with">.casalemedia.com</QueryName>
<QueryName condition="end with">.chartbeat.net</QueryName>
<QueryName condition="end with">.cnn.com</QueryName>
<QueryName condition="end with">.convertro.com</QueryName>
<QueryName condition="end with">.criteo.com</QueryName>
<QueryName condition="end with">.criteo.net</QueryName>
<QueryName condition="end with">.crwdcntrl.net</QueryName>
<QueryName condition="end with">.demdex.net</QueryName>
<QueryName condition="end with">.domdex.com</QueryName>
<QueryName condition="end with">.dotomi.com</QueryName>
<QueryName condition="end with">.doubleclick.net</QueryName>
<QueryName condition="end with">.doubleverify.com</QueryName>
<QueryName condition="end with">.emxdgt.com</QueryName>
<QueryName condition="end with">.exelator.com</QueryName>
<QueryName condition="end with">.google-analytics.com</QueryName>
<QueryName condition="end with">.googleadservices.com</QueryName>
<QueryName condition="end with">.googlesyndication.com</QueryName>
<QueryName condition="end with">.googletagmanager.com</QueryName>
<QueryName condition="end with">.googlevideo.com</QueryName>
<QueryName condition="end with">.gstatic.com</QueryName>
<QueryName condition="end with">.gvt1.com</QueryName>
<QueryName condition="end with">.gvt2.com</QueryName>
<QueryName condition="end with">.ib-ibi.com</QueryName>
<QueryName condition="end with">.jivox.com</QueryName>
<QueryName condition="end with">.mathtag.com</QueryName>
<QueryName condition="end with">.moatads.com</QueryName>
<QueryName condition="end with">.moatpixel.com</QueryName>
<QueryName condition="end with">.mookie1.com</QueryName>
<QueryName condition="end with">.myvisualiq.net</QueryName>
<QueryName condition="end with">.netmng.com</QueryName>
<QueryName condition="end with">.nexac.com</QueryName>
<QueryName condition="end with">.openx.net</QueryName>
<QueryName condition="end with">.optimizely.com</QueryName>
<QueryName condition="end with">.outbrain.com</QueryName>
<QueryName condition="end with">.pardot.com</QueryName>
<QueryName condition="end with">.phx.gbl</QueryName>
<QueryName condition="end with">.pinterest.com</QueryName>
<QueryName condition="end with">.pubmatic.com</QueryName>
<QueryName condition="end with">.quantcount.com</QueryName>
<QueryName condition="end with">.quantserve.com</QueryName>
<QueryName condition="end with">.revsci.net</QueryName>
<QueryName condition="end with">.rfihub.net</QueryName>
<QueryName condition="end with">.rlcdn.com</QueryName>
<QueryName condition="end with">.rubiconproject.com</QueryName>
<QueryName condition="end with">.scdn.co</QueryName>
<QueryName condition="end with">.scorecardresearch.com</QueryName>
<QueryName condition="end with">.serving-sys.com</QueryName>
<QueryName condition="end with">.sharethrough.com</QueryName>
<QueryName condition="end with">.simpli.fi</QueryName>
<QueryName condition="end with">.sitescout.com</QueryName>
<QueryName condition="end with">.smartadserver.com</QueryName>
<QueryName condition="end with">.snapads.com</QueryName>
<QueryName condition="end with">.spotxchange.com</QueryName>
<QueryName condition="end with">.taboola.com</QueryName>
<QueryName condition="end with">.taboola.map.fastly.net</QueryName>
<QueryName condition="end with">.tapad.com</QueryName>
<QueryName condition="end with">.tidaltv.com</QueryName>
<QueryName condition="end with">.trafficmanager.net</QueryName>
<QueryName condition="end with">.tremorhub.com</QueryName>
<QueryName condition="end with">.tribalfusion.com</QueryName>
<QueryName condition="end with">.turn.com</QueryName>
<QueryName condition="end with">.twimg.com</QueryName>
<QueryName condition="end with">.tynt.com</QueryName>
<QueryName condition="end with">.w55c.net</QueryName>
<QueryName condition="end with">.ytimg.com</QueryName>
<QueryName condition="end with">.zorosrv.com</QueryName>
<QueryName condition="is">1rx.io</QueryName>
<QueryName condition="is">adservice.google.com</QueryName>
<QueryName condition="is">ampcid.google.com</QueryName>
<QueryName condition="is">clientservices.googleapis.com</QueryName>
<QueryName condition="is">googleadapis.l.google.com</QueryName>
<QueryName condition="is">imasdk.googleapis.com</QueryName>
<QueryName condition="is">l.google.com</QueryName>
<QueryName condition="is">ml314.com</QueryName>
<QueryName condition="is">mtalk.google.com</QueryName>
<QueryName condition="is">update.googleapis.com</QueryName>
<QueryName condition="is">www.googletagservices.com</QueryName>
<QueryName condition="end with">.mozaws.net</QueryName>
<QueryName condition="end with">.mozilla.com</QueryName>
<QueryName condition="end with">.mozilla.net</QueryName>
<QueryName condition="end with">.mozilla.org</QueryName>
<QueryName condition="is">clients1.google.com</QueryName>
<QueryName condition="is">clients2.google.com</QueryName>
<QueryName condition="is">clients3.google.com</QueryName>
<QueryName condition="is">clients4.google.com</QueryName>
<QueryName condition="is">clients5.google.com</QueryName>
<QueryName condition="is">clients6.google.com</QueryName>
<QueryName condition="is">safebrowsing.googleapis.com</QueryName>
<QueryName condition="end with">.akadns.net</QueryName>
<QueryName condition="end with">.netflix.com</QueryName>
<QueryName condition="end with">aspnetcdn.com</QueryName>
<QueryName condition="is">ajax.googleapis.com</QueryName>
<QueryName condition="is">cdnjs.cloudflare.com</QueryName>
<QueryName condition="is">fonts.googleapis.com</QueryName>
<QueryName condition="end with">.typekit.net</QueryName>
<QueryName condition="is">cdnjs.cloudflare.com</QueryName>
<QueryName condition="end with">.stackassets.com</QueryName>
<QueryName condition="end with">.steamcontent.com</QueryName>
<QueryName condition="end with">.arpa.</QueryName>
<QueryName condition="end with">.arpa</QueryName>
<QueryName condition="end with">.msftncsi.com</QueryName>
<QueryName condition="end with">.localmachine</QueryName>
<QueryName condition="is">localhost</QueryName>
<Rule groupRelation="and">
<Image condition="is">C:\ProgramData\LogiShrd\LogiOptions\Software\Current\updater.exe</Image>
<QueryName condition="end with">.logitech.com</QueryName>
</Rule>
<Image condition="is">C:\Program Files\Windows Defender Advanced Threat Protection\MsSense.exe</Image>
<QueryName condition="end with">-pushp.svc.ms</QueryName>
<QueryName condition="end with">.b-msedge.net</QueryName>
<QueryName condition="end with">.bing.com</QueryName>
<QueryName condition="end with">.hotmail.com</QueryName>
<QueryName condition="end with">.live.com</QueryName>
<QueryName condition="end with">.live.net</QueryName>
<QueryName condition="end with">.s-microsoft.com</QueryName>
<QueryName condition="end with">.microsoft.com</QueryName>
<QueryName condition="end with">.microsoftonline.com</QueryName>
<QueryName condition="end with">.microsoftstore.com</QueryName>
<QueryName condition="end with">.ms-acdc.office.com</QueryName>
<QueryName condition="end with">.msedge.net</QueryName>
<QueryName condition="end with">.msn.com</QueryName>
<QueryName condition="end with">.msocdn.com</QueryName>
<QueryName condition="end with">.skype.com</QueryName>
<QueryName condition="end with">.skype.net</QueryName>
<QueryName condition="end with">.windows.com</QueryName>
<QueryName condition="end with">.windows.net.nsatc.net</QueryName>
<QueryName condition="end with">.windowsupdate.com</QueryName>
<QueryName condition="end with">.xboxlive.com</QueryName>
<QueryName condition="is">login.windows.net</QueryName>
<QueryName condition="end with">.activedirectory.windowsazure.com</QueryName>
<QueryName condition="end with">.aria.microsoft.com</QueryName>
<QueryName condition="end with">.msauth.net</QueryName>
<QueryName condition="end with">.msftauth.net</QueryName>
<QueryName condition="end with">.opinsights.azure.com</QueryName>
<QueryName condition="is">management.azure.com</QueryName>
<QueryName condition="is">outlook.office365.com</QueryName>
<QueryName condition="is">portal.azure.com</QueryName>
<QueryName condition="is">substrate.office.com</QueryName>
<QueryName condition="is">osi.office.net</QueryName>
<QueryName condition="end with">.digicert.com</QueryName>
<QueryName condition="end with">.globalsign.com</QueryName>
<QueryName condition="end with">.globalsign.net</QueryName>
<QueryName condition="is">msocsp.com</QueryName>
<QueryName condition="is">ocsp.msocsp.com</QueryName>
<QueryName condition="end with">pki.goog</QueryName>
<QueryName condition="is">ocsp.godaddy.com</QueryName>
<QueryName condition="end with">amazontrust.com</QueryName>
<QueryName condition="is">ocsp.sectigo.com</QueryName>
<QueryName condition="is">pki-goog.l.google.com</QueryName>
<QueryName condition="end with">.usertrust.com</QueryName>
<QueryName condition="is">ocsp.comodoca.com</QueryName>
<QueryName condition="is">ocsp.verisign.com</QueryName>
<QueryName condition="is">ocsp.entrust.net</QueryName>
<QueryName condition="end with">ocsp.identrust.com</QueryName>
<QueryName condition="is">status.rapidssl.com</QueryName>
<QueryName condition="is">status.thawte.com</QueryName>
<QueryName condition="is">ocsp.int-x3.letsencrypt.org</QueryName>
<QueryName condition="is">subca.ocsp-certum.com</QueryName>
<QueryName condition="is">cscasha2.ocsp-certum.com</QueryName>
<QueryName condition="is">crl.verisign.com</QueryName>
<Image condition="contains all">C:\Program Files\SentinelOne\Sentinel Agent;\SentinelAgent.exe</Image>
<QueryName condition="end with">.spotify.com</QueryName>
<QueryName condition="end with">.spotify.map.fastly.net</QueryName>
</DnsQuery>
</RuleGroup>
<RuleGroup groupRelation="or">
<FileDelete onmatch="include">
<TargetFilename condition="contains all">C:\Program Files\Microsoft SQL Server;\Shared\ErrorDumps</TargetFilename>
<TargetFilename condition="contains all">C:\Program Files\Microsoft SQL Server;\DataDumps</TargetFilename>
<TargetFilename condition="contains all">C:\Program Files (X86)\Microsoft SQL Server\;Shared\ErrorDumps</TargetFilename>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Program Files\Qualys\QualysAgent</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="contains">\Downloads\</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="contains">\Appdata\Local\Temp\</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="contains">\Appdata\Local\Microsoft\Windows\INetCache\Content.Outlook\</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Intel</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Mozilla</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\chocolatey\logs</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\DeviceSync</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\PlayReady</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\User Account Pictures</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Crypto\DSS\MachineKeys</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\NetFramework\BreadcrumbStore</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Office\Heartbeat</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Windows\WER\ReportQueue</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Windows\WER\Temp</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Windows\WER\Temp</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Windows\WER\Temp</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Windows\WER\Temp</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\ProgramData\Microsoft\Windows\WER\Temp</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Intel</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Mozilla</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\chocolatey\logs</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\DeviceSync</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\PlayReady</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\User Account Pictures</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\Crypto\DSS\MachineKeys</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\Crypto\RSA\MachineKeys</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\NetFramework\BreadcrumbStore</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\Office\Heartbeat</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\Windows\WER\ReportArchive</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\Windows\WER\ReportQueue</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Users\All Users\Microsoft\Windows\WER\Temp</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\Tasks</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\tracing</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\Registration\CRMLog</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\System32\Tasks</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\System32\Microsoft\Crypto\RSA\MachineKeys</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\System32\spool\drivers\color</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
<Rule groupRelation="and">
<TargetFilename condition="begin with">C:\Windows\SysWOW64\Tasks</TargetFilename>
<TargetFilename condition="contains any">.com;.bat;.exe;.reg;.ps1;.vbs;.vba;.lnk;.doc;.xls;.hta;.bin;.7z;.dll;.xla;.cmd;.sh;.lnk;.pptm;.scr;.msi;.sct</TargetFilename>
</Rule>
</FileDelete>
</RuleGroup>
<RuleGroup groupRelation="or">
<FileDelete onmatch="exclude">
<Image condition="contains all">\appdata\local\google\chrome\user data\swreporter\;software_reporter_tool.exe</Image>
<Image condition="is">C:\Program Files (x86)\Google\Chrome\Application\chrome.exe</Image>
<User condition="contains any">NETWORK SERVICE; LOCAL SERVICE</User>
</FileDelete>
</RuleGroup>
</EventFiltering>
</Sysmon>iniciamos sysmon
Sysmon64.exe -accepteula -i sysmon.xmlNos tendría que salir registros en Applications and Services Logs/Microsoft/Windows/Sysmon/Operational
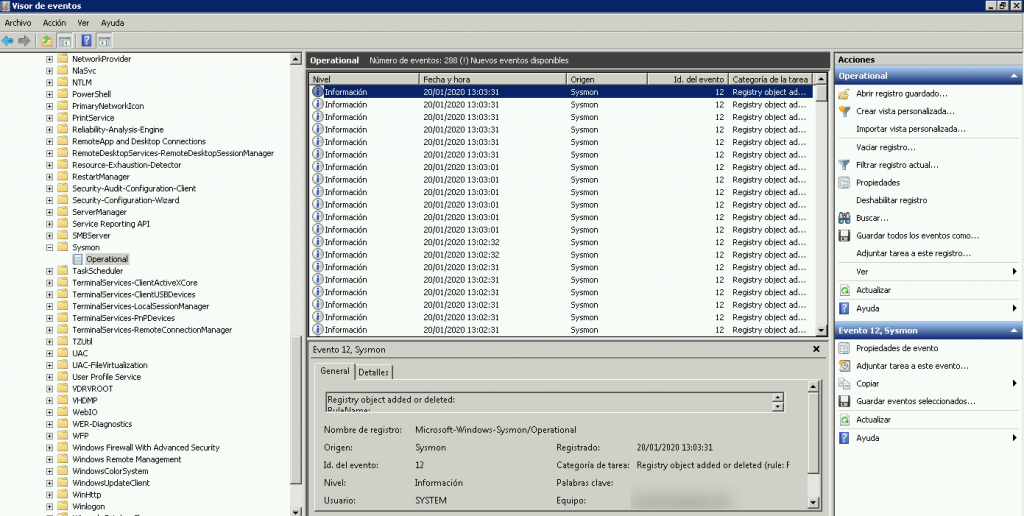
Es necesario indicarle en el agente de wazuh que monitorice los eventos de Sysmon, para ello agregamos las siguientes lineas en C:\Program Files (x86)\ossec-agent\ossec.conf
<localfile>
<location>Microsoft-Windows-Sysmon/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-Windows Defender/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-WMI-Activity/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-TerminalServices-LocalSessionManager/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-SMBServer/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-SMBServer/Connectivity</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-SMBClient/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-SmbClient/Connectivity</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational</location>
<log_format>eventchannel</log_format>
</localfile>
<localfile>
<location>Microsoft-Windows-TaskScheduler/Operational</location>
<log_format>eventchannel</log_format>
</localfile>Es necesario agregar una nueva regla local_rules.xmlen el administrador de Wazuh para que coincida con el evento Sysmon generado por la ejecución de Powershell. Esta regla permitirá que el administrador active una alerta cada vez que reciba este tipo de evento.
Para ello agregamos la siguiente configuración en: /var/ossec/etc/rules/local_rules.xml
*/ rules in localrules.xml for Sysmon*/
<group name="sysmon,sysmon_process-anomalies,">
<rule id="255000" level="12">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">\\powershell.exe||\\.ps1||\\.ps2</field>
<description>Sysmon - Event 1: Powershell or Script Execution: $(win.eventdata.image)</description>
</rule>
<rule id="255001" level="0">
<field name="win.eventdata.Image">\\rundll32.exe</field>
<description>Sysmon - rundll32.exe</description>
</rule>
<rule id="255002" level="12">
<if_sid>255001</if_sid>
<field name="win.eventdata.ImageLoaded">\\vaultcli.dll</field>
<description>Possible Mimikatz Running In-Memory Detection</description>
</rule>
<rule id="255003" level="12">
<if_sid>255001</if_sid>
<field name="win.eventdata.ImageLoaded">\\wlanapi.dll</field>
<description>Possible Mimikatz In-Memory Detection</description>
</rule>
<rule id="255004" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.parentImage">\\mshta.exe</field>
<description>Sysmon - mshta.exe</description>
</rule>
<rule id="255005" level="12">
<if_sid>255004</if_sid>
<field name="win.eventdata.Image">\\cmd.exe||\\powershell.exe||\\wscript.exe||\\cscript.exe||\\sh.exe||\\bash.exe||\\reg.exe||\\regsvr32.exe||\\BITSADMIN*</field>
<description>Detection a Windows command line executable started from MSHTA</description>
</rule>
<rule id="255006" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.ParentImage">\\WINWORD.EXE||\\EXCEL.EXE||\\POWERPNT.exe||\\MSPUB.exe||\\VISIO.exe</field>
<description>Sysmon - MS Word - Ms EXCEL run</description>
</rule>
<rule id="255007" level="12">
<if_sid>255006</if_sid>
<field name="win.eventdata.Image">\\cmd.exe</field>
<description>Possible Office Macro Started : $(win.eventdata.image)</description>
</rule>
<rule id="255008" level="12">
<if_sid>255006</if_sid>
<field name="win.eventdata.Image">\\cmd.exe||\\powershell.exe||\\wscript.exe||\\cscript.exe||\\sh.exe||\\bash.exe||\\scrcons.exe||\\schtasks.exe||\\regsvr32.exe||\\hh.exe</field>
<description>Microsoft Office Product Spawning Windows Shell</description>
</rule>
<rule id="255009" level="0">
<if_group>sysmon_event8</if_group>
<field name="win.eventdata.TargetImage">\\lsass.exe</field>
<description>sysmon</description>
</rule>
<rule id="255010" level="12">
<if_sid>255009</if_sid>
<field name="win.eventdata.startModule">null</field>
<description>Password Dumper Remote Thread in LSASS</description>
</rule>
<rule id="255011" level="12">
<if_sid>255000</if_sid>
<field name="win.eventdata.commandline">DownloadString||downloadfile</field>
<description>PowerShell scripts that download content from the Internet</description>
</rule>
<rule id="255016" level="12">
<if_sid>255000</if_sid>
<field name="win.eventdata.commandline">EncodedCommand||-w hidden||-window hidden||-windowstyle hidden||-enc||-noni||noninteractive</field>
<description>Detects suspicious PowerShell invocation command parameters</description>
</rule>
<rule id="255017" level="0">
<if_group>sysmon_event3</if_group>
<field name="win.eventdata.image">rundll32.exe</field>
<description>Rundll32 Internet Connection</description>
</rule>
<rule id="255018" level="12">
<if_sid>255017</if_sid>
<match>!192.</match>
<description>Detects a rundll32 that communicates with public IP addresses</description>
</rule>
<rule id="255020" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">certutil.exe</field>
<description>Detetcs a suspicious Microsoft certutil execution with sub commands</description>
</rule>
<rule id="255021" level="12">
<if_sid>255020</if_sid>
<field name="win.eventdata.commandline">URL||decode||decodehex||urlcache||ping</field>
<description>Detetcs a suspicious Microsoft certutil execution with sub commands</description>
</rule>
<rule id="255023" level="12">
<if_sid>255000</if_sid>
<field name="win.eventdata.currentDirectory">AppData</field>
<description>Detects a suspicious command line execution that includes an URL and AppData</description>
</rule>
<rule id="255024" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.parentImage">\\System32\\control.exe</field>
<description>Detects suspicious Rundll32 execution from control.exe as used by Equation Group and Exploit Kits</description>
</rule>
<rule id="255025" level="12">
<if_sid>255024</if_sid>
<field name="win.eventdata.commandline">\\rundll32.exe</field>
<description>Detects suspicious Rundll32 execution from control.exe as used by Equation Group and Exploit Kits</description>
</rule>
<rule id="255026" level="12">
<if_group>sysmon_event6</if_group>
<field name="win.eventdata.imageLoaded">\\Temp</field>
<description>Detects a driver load from a temporary directory</description>
</rule>
<rule id="255027" level="12">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">C:\\PerfLogs\\||C:\$Recycle.bin\\||C:\\Intel\\Logs\\||C:\\Users\\Default\\||C:\\Users\\Public\\||C:\\Users\\NetworkService\\||C:\\Windows\\Fonts\\C:\\Windows\\Debug\\||C:\\Windows\\Media\\||C:\\Windows\\Help\\||C:\\Windows\\addins\\||C:\\Windows\\repair\\||C:\\Windows\\security\\||\\RSA\\MachineKeys\\||C:\\Windows\\system32\\config\\systemprofile</field>
<description>Detects process starts of binaries from a suspicious folder</description>
</rule>
<rule id="255028" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.parentImage">\\mmc.exe</field>
<description>Processes started by MMC could by a sign of lateral movement using MMC application COM object</description>
</rule>
<rule id="255029" level="12">
<if_sid>255028</if_sid>
<field name="win.eventdata.image">\\cmd.exe</field>
<description>Processes started by MMC could by a sign of lateral movement using MMC application COM object</description>
</rule>
<!-- https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/-->
<rule id="255030" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.parentImage">\\net.exe||\\net1.exe</field>
<description>Detects execution of Net.exe, whether suspicious or benign.</description>
</rule>
<rule id="255031" level="12">
<if_sid>255030</if_sid>
<field name="win.eventdata.commandline">group||localgroup||user||view||share||accounts||use</field>
<description>Detects execution of Net.exe, whether suspicious or benign</description>
</rule>
<rule id="255032" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.parentImage">\\wscript.exe||\\cscript.exe</field>
<description>Sysmon - wscript/cscript.exe</description>
</rule>
<rule id="255033" level="12">
<if_sid>255032</if_sid>
<field name="win.eventdata.Image">\\powershell.exe</field>
<description>Detects suspicious powershell invocations from interpreters or unusual programs</description>
</rule>
<rule id="255034" level="12">
<if_sid>255030</if_sid>
<field name="win.eventdata.commandline">net group "domain admins" /domain||net localgroup administrators||net1 group "domain admins" /domain||net1 localgroup administrators</field>
<description>Detects suspicious command line activity on Windows systems</description>
</rule>
<rule id="255035" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">\\regsvr32.exe</field>
<description>Detects various anomalies in relation to regsvr32.exe</description>
</rule>
<rule id="255036" level="12">
<if_sid>255035</if_sid>
<field name="win.eventdata.commandline">\\Temp</field>
<description>Detects various anomalies in relation to regsvr32.exe</description>
</rule>
<rule id="255037" level="12">
<if_sid>255035</if_sid>
<field name="win.eventdata.parentImage">powershell.exe</field>
<description>Detects various anomalies in relation to regsvr32.exe</description>
</rule>
<rule id="255038" level="12">
<if_sid>255035</if_sid>
<field name="win.eventdata.commandline">scrobj.dll</field>
<description>Detects various anomalies in relation to regsvr32.exe</description>
</rule>
<rule id="255039" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">\\schtasks.exe</field>
<description>Detects the creation of scheduled tasks in user session</description>
</rule>
<rule id="255040" level="12">
<if_sid>255039</if_sid>
<field name="win.eventdata.commandline">/create</field>
<description>Detects the creation of scheduled tasks in user session</description>
</rule>
<rule id="255041" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">\\wscript.exe||\\cscript.exe</field>
<description>Detects various anomalies in relation to wscriptcscript</description>
</rule>
<rule id="255042" level="12">
<if_sid>255041</if_sid>
<field name="win.eventdata.commandline">jse||vbe||js||vba</field>
<description>Detects suspicious file execution by wscript and cscript</description>
</rule>
<rule id="255043" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.parentImage">\\svchost.exe</field>
<description>Suspicious Svchost Process</description>
</rule>
<rule id="255044" level="12">
<if_sid>255041</if_sid>
<field name="win.eventdata.image">\\services.exe</field>
<description>Detects a suspicious scvhost process start</description>
</rule>
<rule id="255045" level="12">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.commandline">vssadmin.exe Delete Shadows||vssadmin create shadow||GLOBALROOT||vssadmin delete shadows||reg SAVE HKLM\\SYSTEM||\\windows\\ntds\\ntds.dit</field>
<description>Detects suspicious commands that could be related to activity that uses volume shadow copy</description>
</rule>
<rule id="255046" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">\\wmic.exe</field>
<description>Detects WMI executing suspicious commands</description>
</rule>
<rule id="255047" level="12">
<if_sid>255046</if_sid>
<field name="win.eventdata.commandline">process call create||AntiVirusProduct get||FirewallProduct get||shadowcopy delete</field>
<description>Detects WMI executing suspicious commands</description>
</rule>
<rule id="255048" level="12">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.commandline">transport=dt_socket,address=</field>
<description>Detects a JAVA process running with remote debugging allowing more than just localhost to connect</description>
</rule>
<rule id="255049" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.ParentImage">\\WINWORD.EXE</field>
<description>Sysmon - MS Word</description>
</rule>
<rule id="255050" level="12">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">\\csc.exe</field>
<description>Detects Winword starting uncommon sub process csc.exe as used in exploits</description>
</rule>
<rule id="255051" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.ParentImage">\\apache||\\tomcat||\\w3wp.exe||\\php-cgi.exe||\\nginx.exe||\\httpd.exe</field>
<description>Sysmon - Webshell detection</description>
</rule>
<rule id="255052" level="0">
<if_sid>255051</if_sid>
<field name="win.eventdata.commandline">whoami||net user||ping -n||systeminfo</field>
<description>Sysmon - Webshell detection</description>
</rule>
<rule id="255053" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.image">bitsadmin.exe</field>
<description>Sysmon Bitsadmin.exe detection</description>
</rule>
<rule id="255054" level="12">
<if_sid>255053</if_sid>
<field name="win.eventdata.commandline">/transfer</field>
<description>Detects usage of bitsadmin downloading a file</description>
</rule>
<rule id="254056" level="12">
<if_sid>255000</if_sid>
<field name="win.eventdata.commandline">AppData</field>
<description>Detects a suspicious command line execution that includes an URL and AppData</description>
</rule>
<rule id="255057" level="12">
<if_sid>255028</if_sid>
<field name="win.eventdata.image">\\powershell.exe</field>
<description>Processes started by MMC could by a sign of lateral movement using MMC application COM object</description>
</rule>
<rule id="255058" level="12">
<if_sid>255032</if_sid>
<field name="win.eventdata.Image">\\cmd.exe</field>
<description>Detects suspicious powershell invocations from interpreters or unusual programs</description>
</rule>
<rule id="255059" level="0">
<if_sid>184666</if_sid>
<match>MsMpEng.exe</match>
<description>Exclude</description>
</rule>
<rule id="254060" level="0">
<if_sid>254056</if_sid>
<match>WindowsVersionTempFile.txt</match>
<description>Exclude</description>
</rule>
<rule id="255061" level="0">
<if_sid>255025</if_sid>
<match>timedate.cpl</match>
<description>Exclude</description>
</rule>
<rule id="255062" level="0">
<if_sid>255033</if_sid>
<match>getfilecounts.vbs</match>
<description>Exclude</description>
</rule>
<rule id="255063" level="0">
<if_sid>255050</if_sid>
<match>xj6r_ru4.cmdline</match>
<description>Exclude</description>
</rule>
<rule id="255065" level="0">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.Image">conhost.exe</field>
<description>Mimikatz Detection Parent Image $(win.eventdata.parentimage)</description>
</rule>
<rule id="255066" level="12">
<if_sid>255065</if_sid>
<field name="win.eventdata.ParentImage">mimikatz.exe</field>
<description>Mimikatz Detection Image: $(win.eventdata.parentimage)</description>
</rule>
<rule id="255067" level="12">
<if_sid>255032</if_sid>
<field name="win.eventdata.currentDirectory">AppData</field>
<description>Detects a suspicious command line execution that includes an URL and AppData</description>
</rule>
<rule id="255068" level="12">
<if_sid>255041</if_sid>
<field name="win.eventdata.currentDirectory">AppData</field>
<description>Detects a suspicious command line execution that includes an URL and AppData</description>
</rule>
<!--
<rule id="255069" level="12">
<if_sid>255017</if_sid>
<match>!172.</match>
<description>Detects a rundll32 that communicates with public IP addresses</description>
</rule>
<rule id="255070" level="12">
<if_sid>255017</if_sid>
<match>!10.</match>
<description>Detects a rundll32 that communicates with public IP addresses</description>
</rule>
-->
<rule id="255071" level="12">
<if_group>sysmon_event1</if_group>
<field name="win.eventdata.commandline">AppData</field>
<description>Detects a suspicious command line execution that includes an URL and AppData</description>
</rule>
</group>
Una vez reiniciado el servicio de Wazuh accedemos a mediante Kibana y podemos observar las diferentes alertas que nos llegan:
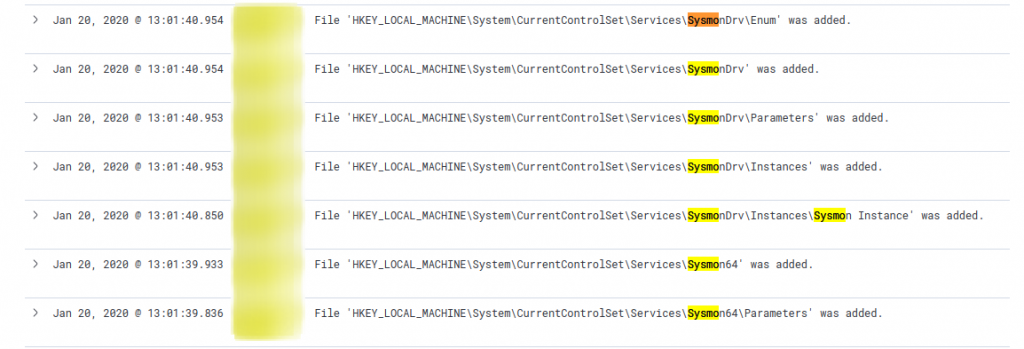
:wq!
2 comentarios en “Integrar Sysmon con Wazuh”